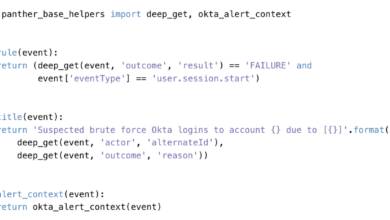
It is no secret that secrets scanning is important
It is no secret that secrets scanning is important; in today’s digital landscape, where data breaches are headline news, protecting sensitive information is paramount. Think about it – your passwords, API keys, database credentials – all are juicy targets for malicious actors. Secrets scanning acts as your digital bodyguard, tirelessly searching your code and systems for these hidden vulnerabilities before they can be exploited.
This proactive approach to security is not just a good idea; it’s a necessity.
This post dives deep into the world of secrets scanning, exploring its importance, various methods, available tools, and future trends. We’ll uncover how secrets scanning helps prevent costly data breaches and strengthens your overall security posture. Get ready to learn how to safeguard your valuable data!
The Importance of Secrets Scanning
In today’s interconnected world, where applications and services are increasingly reliant on cloud infrastructure and third-party integrations, the risk of data breaches is ever-present. Neglecting secrets scanning leaves your organization vulnerable to significant financial losses, reputational damage, and legal repercussions. Proactive secrets scanning is no longer a luxury; it’s a critical component of a robust security posture.The potential consequences of neglecting secrets scanning are far-reaching and severe.
A single exposed credential can grant attackers access to your entire system, allowing them to steal sensitive data, disrupt operations, or even hold your business hostage through ransomware attacks. The cost of remediation following a breach, including legal fees, regulatory fines, and the damage to your brand’s reputation, can easily outweigh the cost of implementing a comprehensive secrets scanning program.
Sensitive Data Requiring Protection
Many types of sensitive data require the protection afforded by secrets scanning. This includes, but is not limited to, database credentials (usernames and passwords), API keys, cryptographic keys (encryption and decryption keys), SSH keys, certificates, and tokens used for authentication and authorization. Furthermore, hardcoded passwords within source code, configuration files containing sensitive information, and even internal documents containing confidential data should be considered within the scope of secrets scanning.
The breadth of data requiring protection highlights the necessity of a robust and comprehensive approach.
Types of Secrets Detectable by Secrets Scanning
Secrets scanning tools are designed to detect a wide range of sensitive information. These tools can identify credentials embedded in code repositories, configuration files, and cloud environments. They can also detect hardcoded secrets, leaked credentials, and secrets stored in insecure locations such as plain text files or unencrypted databases. Modern secrets scanning solutions utilize various techniques, including pattern matching, machine learning, and context analysis, to identify a broad spectrum of potential vulnerabilities.
This comprehensive approach helps ensure that even sophisticated attempts at obfuscation are detected.
Hypothetical Data Breach Scenario
Imagine a software development team at a fictional company, “InnovateTech,” is working on a new mobile banking application. They inadvertently commit a configuration file containing the production database credentials to their public GitHub repository. Without a secrets scanning solution in place, these credentials remain exposed for several days. A malicious actor discovers the credentials and gains unauthorized access to InnovateTech’s database.
The attacker exfiltrates customer financial information, leading to a massive data breach. This breach results in significant financial losses due to regulatory fines, legal fees associated with class-action lawsuits, and the loss of customer trust. InnovateTech’s reputation is severely damaged, potentially leading to a decline in market share and long-term financial instability. This hypothetical scenario underscores the critical importance of implementing a comprehensive secrets scanning program to prevent such devastating consequences.
Methods and Techniques in Secrets Scanning
Secrets scanning is crucial for protecting sensitive information, but the methods employed can vary significantly in their approach and effectiveness. Understanding these different techniques is key to building a robust security posture. This section explores the core methods, best practices, and integration strategies for secrets scanning.
Secrets scanning primarily relies on two fundamental approaches: static and dynamic analysis. Static analysis examines the codebase without actually executing it, searching for patterns and hardcoded secrets directly within the source code, configuration files, and build artifacts. Dynamic analysis, on the other hand, involves monitoring the application’s runtime behavior to detect secrets that might be exposed during execution, perhaps through logging or temporary files.
Each method offers unique advantages and limitations.
Static vs. Dynamic Analysis
Static analysis excels at identifying secrets embedded directly within code or configuration files. It’s generally faster and easier to implement than dynamic analysis, making it ideal for early-stage detection in the SDLC. However, it may miss secrets that are dynamically generated during runtime or those present only in specific execution contexts. Dynamic analysis, conversely, can uncover secrets revealed during application operation, even if they aren’t explicitly present in the source code.
This is particularly useful for catching secrets inadvertently leaked through logs or temporary files. However, dynamic analysis requires more sophisticated tools and infrastructure, and can be more resource-intensive. A comprehensive secrets scanning strategy often leverages both approaches for maximum effectiveness.
Best Practices for Implementing an Effective Secrets Scanning Strategy
A successful secrets scanning program requires more than just choosing the right tools. A holistic strategy encompassing various stages of the SDLC is essential. Key best practices include:
- Prioritize critical systems: Focus initial scanning efforts on systems handling sensitive data, such as databases and payment gateways.
- Integrate into CI/CD: Automate secrets scanning as part of your continuous integration and continuous delivery pipeline to catch vulnerabilities early.
- Regularly update scanning tools: Threat actors constantly evolve their techniques, so keeping your tools up-to-date is crucial for staying ahead.
- Establish clear remediation processes: Define clear steps for addressing identified vulnerabilities, assigning ownership, and tracking resolution.
- Use multiple scanning tools: Different tools employ different detection methods, so using a combination can improve overall coverage.
The Role of Regular Vulnerability Assessments
Regular vulnerability assessments are indispensable components of a comprehensive secrets scanning program. They provide a periodic overview of the security posture of your systems, highlighting potential vulnerabilities, including those related to secrets exposure. These assessments, often performed through penetration testing or automated vulnerability scanners, supplement the continuous monitoring provided by integrated secrets scanning tools. The combination of continuous scanning and periodic assessments offers a layered defense against secrets leaks.
Integrating Secrets Scanning into the SDLC
A step-by-step approach to integrating secrets scanning into the SDLC ensures consistent protection throughout the software development lifecycle.
- Selection of Tools: Choose appropriate static and dynamic analysis tools based on your technology stack and budget.
- Integration into CI/CD: Integrate the chosen tools into your CI/CD pipeline, triggering scans automatically during build and deployment phases.
- Configuration and Customization: Configure the tools to scan relevant code repositories, configuration files, and runtime environments. Customize rules to filter out false positives.
- Alerting and Reporting: Set up alerts for critical vulnerabilities and establish reporting mechanisms to track and manage findings.
- Remediation Workflow: Define a clear process for addressing identified vulnerabilities, including assigning responsibility, setting deadlines, and verifying fixes.
- Continuous Monitoring: Continuously monitor the effectiveness of the implemented strategy and adapt as needed, keeping in mind evolving threats and vulnerabilities.
Tools and Technologies for Secrets Scanning: It Is No Secret That Secrets Scanning Is Important
Secrets scanning is crucial for maintaining the security of your applications and infrastructure. The right tools can significantly reduce the risk of data breaches and unauthorized access. Choosing the appropriate tool depends on your specific needs, budget, and technical expertise. This section explores several popular options and their capabilities.
Popular Secrets Scanning Tools
Selecting the right secrets scanning tool involves careful consideration of various factors. The following table compares three popular options, highlighting their strengths and weaknesses. Remember that the best tool will vary based on your specific context and requirements.
| Tool | Features | Strengths | Weaknesses |
|---|---|---|---|
| GitLeaks | Scans Git repositories for leaked secrets; supports various secret types (API keys, passwords, tokens); integrates with CI/CD pipelines. | Open-source, easy to use, fast scanning, good community support. | Limited to Git repositories; may produce false positives; lacks advanced features found in commercial tools. |
| Secret Scanner (Snyk) | Comprehensive secrets detection across various codebases and infrastructure; integrates with various platforms; offers remediation guidance. | High accuracy, wide range of integrations, excellent remediation capabilities. | Commercial product (subscription required); can be more complex to set up than open-source alternatives. |
| AWS Secrets Manager | Secure storage and retrieval of secrets; integrates with other AWS services; offers rotation and access control features. | Tight integration within the AWS ecosystem; robust security features; simplifies secret management. | Primarily for managing secrets within the AWS environment; not a standalone secrets scanning tool for broader codebases. |
Open-Source vs. Commercial Secrets Scanning Tools
The choice between open-source and commercial secrets scanning tools involves a trade-off between cost, features, and support. Open-source tools like GitLeaks offer a cost-effective solution, particularly for smaller projects or those with limited budgets. However, they may lack the advanced features, comprehensive support, and regular updates of commercial offerings. Commercial tools, while more expensive, often provide more accurate detection, better integrations, and dedicated support teams.
The decision ultimately hinges on your organization’s specific security needs and resources. For example, a large enterprise with stringent security requirements and a substantial budget might prefer a commercial solution like Snyk, while a smaller startup might find an open-source tool like GitLeaks sufficient.
Configuring Secret Scanner (Snyk)
This example demonstrates configuring Snyk Secret Scanner for a Node.js application hosted on GitHub. First, you’ll need a Snyk account and to integrate Snyk with your GitHub repository. This usually involves connecting Snyk to your GitHub account via OAuth. Once connected, Snyk will automatically scan your repository for secrets. You can configure scan settings, such as specifying the branches to scan and defining custom rules for specific secret patterns.
Snyk provides detailed documentation and tutorials to guide you through the setup process. For more granular control, you can integrate Snyk into your CI/CD pipeline to automate the scanning process and receive alerts on newly detected secrets. The exact steps will vary depending on your CI/CD system (e.g., Jenkins, GitLab CI), but generally involve setting up a Snyk CLI command within your pipeline.
Remember to regularly review Snyk’s findings and address any detected vulnerabilities promptly.
Addressing Secrets Scanning Challenges
Implementing secrets scanning, while crucial for security, isn’t without its hurdles. Successfully integrating this practice requires careful planning and a proactive approach to address the inherent challenges. Ignoring these difficulties can lead to ineffective scanning, wasted resources, and ultimately, increased vulnerability.
False positives, integration complexities, and developer resistance are common obstacles. Addressing these challenges requires a multi-faceted strategy encompassing improved tooling, enhanced developer education, and a broader security framework.
False Positives and Minimizing Disruptions
False positives, where the scanner flags harmless data as secrets, are a significant problem. They lead to wasted developer time investigating non-issues and can desensitize teams to legitimate alerts. Minimizing false positives requires careful configuration of the scanning tools, focusing on context-aware analysis, and leveraging regular expressions to fine-tune detection rules. For instance, a scanner might incorrectly identify a base64-encoded string as a secret when it’s actually part of a legitimate application payload.
Implementing custom rules or utilizing exclusion lists for known false positive patterns can significantly reduce this noise. Furthermore, regular reviews of scan results and adjustments to the scanning configuration are essential for maintaining accuracy. This iterative process of refinement is crucial for optimizing the scanning process and ensuring its effectiveness.
Educating Developers on Secure Coding Practices
Developers are often the primary source of secrets introduced into code. They might inadvertently hardcode API keys, database credentials, or other sensitive information. To mitigate this, comprehensive training on secure coding practices is vital. This training should cover topics such as the importance of using secrets management tools, avoiding hardcoding sensitive data, and leveraging environment variables for configuration.
Regular code reviews, where experienced developers can identify potential security vulnerabilities, are also crucial. Encouraging the use of linters and static analysis tools that automatically detect potential secrets within code can proactively prevent many issues before they even reach production. The goal is to instill a security-conscious mindset from the outset of the development lifecycle.
Integrating Secrets Scanning with Other Security Measures
Secrets scanning shouldn’t operate in isolation. Effective security requires a layered approach. Integrating secrets scanning with other security measures, such as vulnerability scanners, penetration testing, and software composition analysis (SCA), provides a comprehensive view of the security posture. This integrated approach enables a more holistic understanding of potential risks and facilitates a more effective response. For example, findings from a vulnerability scanner might highlight a weakness that allows attackers to access secrets, even if those secrets weren’t directly identified by the secrets scanner.
Similarly, SCA can help identify vulnerabilities in third-party libraries that might expose secrets. By correlating findings across different security tools, organizations can gain a more complete and accurate picture of their security risks.
Future Trends in Secrets Scanning
Secrets scanning is rapidly evolving, driven by the ever-increasing sophistication of cyberattacks and the expanding attack surface of modern applications. The future of this crucial security practice promises significant advancements, fueled by innovative technologies and a deeper understanding of attacker tactics. We’re moving beyond simple matching towards more intelligent and proactive security measures.The integration of AI and machine learning is poised to revolutionize secrets scanning.
Current methods often rely on pattern matching and regular expressions, which can be easily circumvented by attackers employing obfuscation techniques. AI, however, can learn to identify secrets even when disguised or encoded, significantly improving detection rates and reducing false positives.
AI and Machine Learning Enhancements, It is no secret that secrets scanning is important
AI and machine learning algorithms can analyze vast amounts of code and configuration data to identify patterns indicative of leaked secrets. This goes beyond simple string matching; machine learning models can learn to recognize subtle indicators of compromised credentials, API keys, and other sensitive information, even in encrypted or obfuscated form. For example, an AI model could learn to identify a pattern of characters frequently associated with specific types of secrets, even if the exact characters change.
This capability allows for the detection of novel obfuscation techniques that would bypass traditional methods. Furthermore, AI can dynamically adapt to new attack vectors and emerging obfuscation strategies, ensuring ongoing effectiveness against evolving threats. This adaptive learning is a key advantage over static rule-based systems.
Future Challenges and Opportunities
While the future of secrets scanning is bright, several challenges remain. The increasing complexity of software development, including the rise of serverless architectures and cloud-native applications, presents a significant challenge to comprehensive secrets scanning. The sheer volume of data generated by modern applications also requires highly efficient and scalable scanning solutions. However, these challenges also represent opportunities.
The development of more efficient and sophisticated algorithms, coupled with advancements in cloud-based security infrastructure, can pave the way for seamless integration of secrets scanning into the entire software development lifecycle. The opportunity lies in creating tools that are not only highly effective but also easy to integrate into existing workflows, reducing friction and encouraging wider adoption.
A Seamlessly Integrated Future
Imagine a future where secrets scanning is not an afterthought but an integral part of every development stage. Developers write code, and automated secrets scanning tools instantly flag potential vulnerabilities. Integration with continuous integration/continuous delivery (CI/CD) pipelines ensures that no code containing exposed secrets ever reaches production. This proactive approach significantly reduces the risk of data breaches and minimizes the time and resources spent on remediation.
Such a scenario would involve real-time analysis of code repositories, infrastructure-as-code configurations, and runtime environments. Automated remediation workflows would be triggered upon detection of a secret, and the entire process would be transparent and easily auditable. This level of integration would be achieved through the development of sophisticated APIs and plugins for popular IDEs, CI/CD platforms, and cloud environments.
Companies like GitHub, GitLab, and AWS are already moving in this direction, integrating security tools directly into their platforms. This future scenario represents a paradigm shift from reactive security to proactive risk mitigation.
Illustrative Examples of Secrets Scanning in Action
Secrets scanning isn’t just a theoretical concept; it’s a crucial practice that actively protects organizations from significant data breaches. Real-world examples demonstrate its effectiveness in preventing disastrous outcomes and safeguarding sensitive information. Let’s examine how secrets scanning has proven its worth in practical applications.A Real-World Example of Secrets Scanning Preventing a Breach
Preventing a Data Breach at a Fintech Startup
A fast-growing fintech startup integrated secrets scanning into its CI/CD pipeline. During a routine code review, the scanner flagged an AWS access key embedded directly within a configuration file committed to their Git repository. This key provided full access to the company’s cloud infrastructure, including customer databases and financial transactions. Had this key fallen into the wrong hands, the consequences could have been catastrophic, including potential financial losses, regulatory fines, and irreparable damage to the company’s reputation.
The security team was immediately alerted, the compromised file was removed, the access key was revoked and regenerated, and the developers received training on secure coding practices and secret management. This proactive measure prevented a potential breach that could have cost the company millions of dollars and severely damaged its credibility.
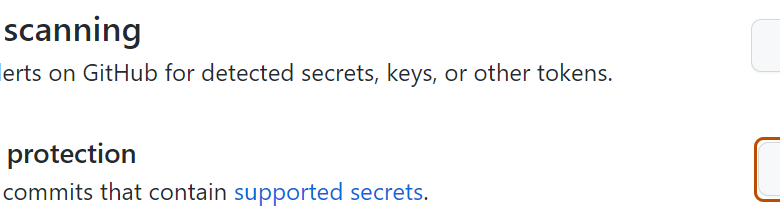
A Hypothetical Visualization of Secrets Scanning
Imagine a vibrant image depicting a codebase represented by a complex network of interconnected nodes and lines, each node a file or function. The nodes are colored a soft blue, representing the clean, secure code. Suddenly, a bright red node appears, pulsating ominously. This node represents a file containing a secret – perhaps a database password – embedded within its code.
Around the red node, several smaller, yellow nodes representing the lines of code containing the secret highlight the location of the vulnerability. Thin, green lines connect the red node to other nodes, visually indicating how the compromised secret could potentially allow access to other parts of the system. The image is overlaid with a magnifying glass icon, symbolizing the secrets scanning tool actively identifying and highlighting the compromised section of the code.
The background is a dark gray, emphasizing the potential danger lurking within the seemingly secure codebase.
Secrets Scanning Integration within a CI/CD Pipeline
Secrets scanning seamlessly integrates into a CI/CD pipeline to provide continuous security verification. The process involves these key steps: First, developers commit code to a version control system like Git. Next, the CI/CD pipeline triggers upon code changes, automatically initiating the secrets scanning process. The scanning tool analyzes the codebase for hardcoded secrets, API keys, passwords, and other sensitive information.
If a secret is detected, the pipeline immediately stops, alerting the development team to the vulnerability. This prevents the compromised code from being built, tested, or deployed to production environments. The output includes a detailed report specifying the location of the secret, its type, and the severity of the risk. Once the issue is resolved, the pipeline resumes, ensuring only secure code reaches production.
This automated approach enhances security and significantly reduces the risk of breaches.
Final Review
Ultimately, secrets scanning isn’t just about finding hidden secrets; it’s about building a robust security culture. By integrating secrets scanning into your development lifecycle and embracing best practices, you significantly reduce your attack surface and protect your organization from devastating consequences. Remember, proactive security is always better than reactive damage control. So, take the plunge, implement secrets scanning, and sleep soundly knowing your secrets are safe.
Questions Often Asked
What happens if a secret is found during a scan?
The process depends on the tool and your setup. Usually, you’ll receive an alert, detailing the location and type of secret. You then take corrective action, such as rotating credentials or fixing the code.
Is secrets scanning suitable for small projects?
Absolutely! Even small projects can benefit from secrets scanning. While the scale might be smaller, the potential impact of a breach remains significant.
How often should I run secrets scans?
Frequency depends on your development cycle and risk tolerance. Daily or weekly scans are common, especially during active development. Integrating scans into your CI/CD pipeline is ideal.
Can secrets scanning detect all types of secrets?
While secrets scanning is highly effective, it’s not foolproof. Sophisticated attackers might employ techniques to evade detection. It’s crucial to combine secrets scanning with other security measures for comprehensive protection.