Keeping Our Customers Safe with MITRE ATT&CK
Keeping our customers safe with the mitre attck framework – Keeping our customers safe with the MITRE ATT&CK framework is more critical than ever. In today’s digital landscape, cybersecurity isn’t just a buzzword; it’s the bedrock of trust. A single data breach can shatter years of hard work and damage a company’s reputation irreparably. This framework, a powerful tool for understanding and mitigating cyber threats, helps us proactively defend against attacks, protecting our customers’ sensitive information and ensuring their peace of mind.
We’ll delve into how we utilize the MITRE ATT&CK framework to build a robust, layered security system, identifying vulnerabilities before they can be exploited.
We’ll explore the framework’s structure, examining key tactics and techniques used by attackers. This will allow us to implement proactive security measures targeting specific vulnerabilities. We’ll cover everything from securing Personally Identifiable Information (PII) and financial data to creating comprehensive incident response plans and implementing robust employee training programs. Think of it as building a fortress, layer by layer, to protect our most valuable asset: our customers’ trust.
The Importance of Customer Safety in a Digital World
In today’s hyper-connected world, businesses rely heavily on digital platforms to interact with customers. This reliance, while offering immense opportunities, introduces significant cybersecurity risks. Protecting customer data is no longer a luxury; it’s a fundamental necessity for maintaining trust, complying with regulations, and ensuring the long-term viability of any organization. Neglecting cybersecurity can lead to devastating consequences, far beyond simple financial losses.The potential ramifications of inadequate customer data security are profound and multifaceted.
Data breaches can result in significant financial penalties due to regulatory fines (like GDPR or CCPA violations), legal battles from affected customers, and the substantial cost of remediation efforts. Beyond the financial impact, reputational damage can be irreparable, leading to loss of customer trust, decreased brand loyalty, and difficulty attracting new business. The erosion of public confidence can be slow and insidious, but ultimately devastating.
Examples of Cybersecurity Breaches and Their Impact
Several high-profile data breaches have vividly demonstrated the severe consequences of neglecting customer data security. For instance, the 2017 Equifax breach exposed the personal information of nearly 150 million individuals, resulting in billions of dollars in fines and legal settlements. This breach severely damaged Equifax’s reputation and underscored the importance of robust security measures. Similarly, the Yahoo data breaches, spanning several years, exposed billions of user accounts, highlighting the long-term vulnerability of neglecting proactive security strategies.
These incidents showcase the far-reaching and long-lasting effects of inadequate security, extending beyond immediate financial losses to include lasting reputational harm and loss of customer trust.
Introducing the MITRE ATT&CK Framework
The MITRE ATT&CK framework provides a powerful and widely adopted methodology for understanding and mitigating cybersecurity threats. It offers a structured, comprehensive knowledge base of adversary tactics and techniques, enabling organizations to proactively identify vulnerabilities and improve their security posture. By mapping potential attack paths and understanding the techniques used by malicious actors, businesses can develop more effective defense strategies and protect their customers’ data more effectively.
The framework’s versatility allows for adaptation to various industries and threat landscapes, making it an invaluable tool for organizations of all sizes. Using ATT&CK allows for a proactive, rather than reactive, approach to security, significantly reducing the risk of breaches and their associated consequences.
Understanding the MITRE ATT&CK Framework: Keeping Our Customers Safe With The Mitre Attck Framework
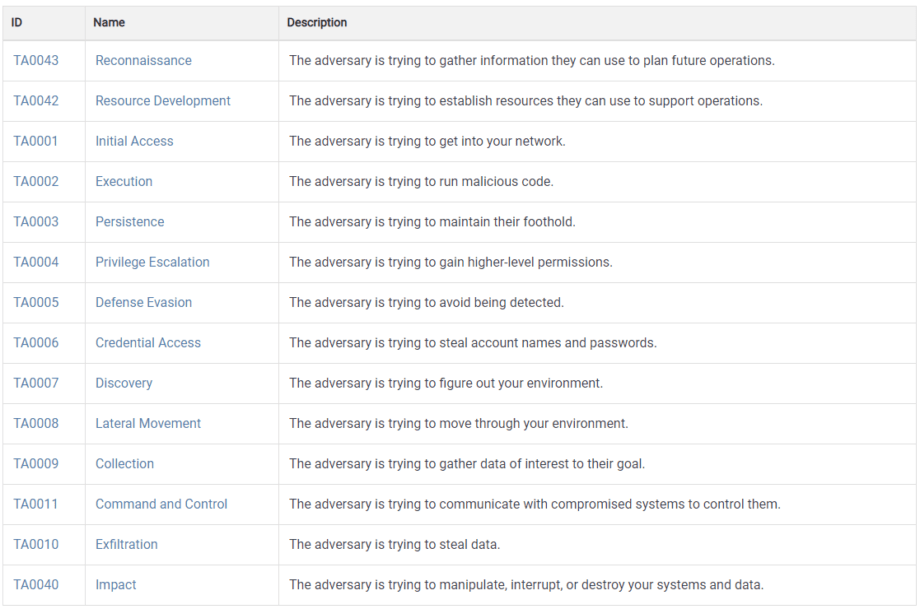
The MITRE ATT&CK framework is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations. It provides a standardized language and model for understanding and defending against cyberattacks, making it an invaluable tool for organizations committed to protecting their customers’ data. Its strength lies in its comprehensive nature, allowing security professionals to anticipate and mitigate threats more effectively.The framework organizes known adversary behaviors into a matrix of tactics and techniques.
Tactics represent high-level adversary goals (e.g., reconnaissance, initial access), while techniques describe specific actions taken to achieve those goals (e.g., phishing, exploiting vulnerabilities). This structured approach allows security teams to map observed attacker activity to the framework, facilitating threat detection, prevention, and response. Understanding this structure is crucial for building robust cybersecurity defenses.
MITRE ATT&CK Tactics and Techniques Relevant to Customer Data Protection
Several tactics and techniques within the MITRE ATT&CK framework are particularly relevant to protecting customer data. Focusing on these key areas allows organizations to prioritize their security efforts and allocate resources effectively. Understanding the adversary’s likely methods is the first step towards neutralizing them.
Stages of a Cyberattack According to MITRE ATT&CK
The MITRE ATT&CK framework models the lifecycle of a cyberattack across various stages. Understanding these stages is essential for proactive threat detection and response. Each stage represents a potential point of vulnerability, and a strong defense requires addressing each phase effectively.
| Technique | Tactic | Potential Impact on Customer Safety | Mitigation Strategies |
|---|---|---|---|
| Phishing | Initial Access | Compromise of user credentials, leading to data breaches and identity theft. | Security awareness training, multi-factor authentication, email filtering. |
| Exploiting Software Vulnerabilities | Initial Access | Unauthorized access to systems and data, potentially leading to data exfiltration or ransomware attacks. | Regular software patching, vulnerability scanning, intrusion detection systems. |
| Credential Access | Execution | Gaining access to sensitive accounts, enabling further lateral movement and data theft. | Strong password policies, privileged access management, monitoring for suspicious login attempts. |
| Data Exfiltration | Exfiltration | Theft of sensitive customer data, leading to financial loss, reputational damage, and legal repercussions. | Data loss prevention (DLP) tools, network monitoring, secure data storage and access controls. |
Applying the MITRE ATT&CK Framework to Customer Safety
The MITRE ATT&CK framework isn’t just a theoretical model; it’s a powerful tool for proactively safeguarding our customers in the ever-evolving landscape of cyber threats. By understanding the tactics and techniques used by adversaries, we can anticipate their actions and build robust defenses. This allows us to move beyond reactive security measures and instead implement a proactive strategy that minimizes risk and maximizes customer protection.Proactive Vulnerability Identification using the MITRE ATT&CK Framework involves systematically mapping our systems and processes against the framework’s tactics and techniques.
This allows us to identify gaps in our security posture before attackers exploit them. For example, by examining the “Initial Access” tactic, we can assess our vulnerability to phishing attacks, exploiting software vulnerabilities, or compromised credentials. Identifying these weaknesses allows for targeted mitigation strategies.
Mitigating Risks Associated with Specific ATT&CK Techniques
Effective risk mitigation requires a tailored approach for each identified weakness. The framework provides a structured way to analyze and address these weaknesses. Consider the “Credential Access” technique. Implementing multi-factor authentication (MFA) across all systems significantly reduces the risk of attackers gaining unauthorized access through stolen or compromised credentials. Similarly, for the “Execution” technique, focusing on application whitelisting and regular software patching minimizes the likelihood of malicious code execution.
A comprehensive vulnerability scanning program, regularly updated with the latest threat intelligence, further enhances our proactive defense.
Implementing Security Controls Based on the MITRE ATT&CK Framework: A Step-by-Step Procedure
Implementing security controls based on the ATT&CK framework follows a methodical approach.
- Identify Potential Attack Paths: Begin by mapping your organization’s infrastructure and processes against the ATT&CK matrix. Identify the techniques most likely to be used against your specific environment. Consider factors such as industry, customer base, and critical assets.
- Prioritize Risks: Based on the likelihood and impact of potential attacks, prioritize the identified techniques. Focus on mitigating the most critical risks first.
- Develop Mitigation Strategies: For each prioritized technique, develop specific mitigation strategies. This may involve implementing new security controls, enhancing existing controls, or improving security awareness training.
- Implement and Test Controls: Implement the chosen mitigation strategies and rigorously test their effectiveness. This may involve penetration testing, vulnerability scanning, or tabletop exercises.
- Monitor and Adapt: Continuously monitor the effectiveness of implemented controls and adapt your strategy as new threats emerge or vulnerabilities are discovered. The MITRE ATT&CK framework is constantly updated, so staying current is vital.
Examples of Security Controls for Each Stage of the Cyberattack Lifecycle
The MITRE ATT&CK framework organizes attacks into phases, from initial access to impact. Effective security requires addressing each stage.
| Cyberattack Lifecycle Stage | ATT&CK Tactics | Example Security Controls |
|---|---|---|
| Reconnaissance | Discovery | Network segmentation, intrusion detection systems (IDS), security information and event management (SIEM) |
| Initial Access | Initial Access | Multi-factor authentication (MFA), strong password policies, endpoint detection and response (EDR), vulnerability management |
| Execution | Execution | Application whitelisting, regular software patching, sandboxing, data loss prevention (DLP) |
| Persistence | Persistence | Regular security audits, access control lists (ACLs), privileged access management (PAM) |
| Privilege Escalation | Privilege Escalation | Principle of least privilege, regular security audits, strong access control policies |
| Defense Evasion | Defense Evasion | Advanced threat protection (ATP), sandboxing, threat intelligence feeds |
| Credential Access | Credential Access | MFA, password managers, regular password changes, security awareness training |
| Discovery | Discovery | Regular vulnerability assessments, network segmentation, security monitoring |
| Lateral Movement | Lateral Movement | Network segmentation, micro-segmentation, endpoint detection and response (EDR) |
| Collection | Collection | Data loss prevention (DLP), encryption, access control |
| Command and Control | Command and Control | Network monitoring, firewall rules, intrusion prevention systems (IPS) |
| Exfiltration | Exfiltration | Data loss prevention (DLP), network monitoring, encryption |
| Impact | Impact | Business continuity and disaster recovery planning, incident response plan |
Specific Customer Data Protection Measures
Protecting customer data is paramount, not just for legal compliance but also for maintaining trust and loyalty. A robust data protection strategy involves multiple layers of security, encompassing technical safeguards, employee training, and stringent policies. This section delves into specific measures for safeguarding sensitive customer information.
Securing Personally Identifiable Information (PII)
PII, including names, addresses, email addresses, and phone numbers, requires stringent protection. Implementing robust access controls, limiting data access to only authorized personnel on a need-to-know basis, is crucial. Regular data audits should be conducted to identify and rectify any unauthorized access or data breaches. Data encryption both in transit and at rest is essential to protect PII from unauthorized access even if a breach occurs.
Furthermore, implementing strong password policies and multi-factor authentication (MFA) adds an extra layer of security. Data minimization, only collecting the necessary PII, and data retention policies, specifying how long data is stored and when it should be deleted, are also vital.
Protecting Customer Financial Data and Payment Information
Protecting financial data, such as credit card numbers and bank account details, necessitates even more stringent measures. Compliance with industry standards like PCI DSS (Payment Card Industry Data Security Standard) is mandatory for businesses processing payment card information. This involves implementing strong security controls around the payment gateway, using secure payment processing methods (like tokenization), and regularly updating security software.
Data encryption, both at rest and in transit, is crucial, and regular vulnerability scans and penetration testing help identify and address security weaknesses. The use of secure servers and firewalls further enhances protection against unauthorized access.
Security Awareness Training Program for Employees
A comprehensive security awareness training program is essential for educating employees about data protection best practices. This program should cover topics such as phishing scams, social engineering attacks, password security, and the importance of data confidentiality. Regular training sessions, including interactive modules and simulated phishing attacks, help employees recognize and respond to potential threats. Employees should be clearly informed about the company’s data protection policies and procedures, and their responsibilities in upholding them.
The training should also emphasize the consequences of data breaches and the importance of reporting suspicious activity immediately.
Data Encryption Methods
Several encryption methods exist, each with varying levels of security and complexity. Symmetric encryption, using the same key for encryption and decryption, is faster but requires secure key exchange. Examples include AES (Advanced Encryption Standard) and DES (Data Encryption Standard), with AES being significantly more secure. Asymmetric encryption, using separate keys for encryption and decryption (public and private keys), is slower but offers better key management.
RSA (Rivest-Shamir-Adleman) is a widely used asymmetric encryption algorithm. Hybrid encryption methods, combining symmetric and asymmetric encryption, offer a balance of speed and security. For example, a session key is generated using symmetric encryption, and this key is then encrypted using the recipient’s public key in asymmetric encryption. The choice of encryption method depends on the sensitivity of the data and the specific security requirements.
Stronger encryption methods offer greater protection against unauthorized access, even if the encrypted data is compromised.
Incident Response and Recovery
A robust incident response plan is crucial for minimizing the impact of a security breach on your customers and your business. Leveraging the MITRE ATT&CK framework allows for a proactive and structured approach, enabling quicker identification, containment, and recovery. This framework provides a common language and understanding of adversary tactics and techniques, which are essential for effective incident response.
Our incident response plan is built upon the MITRE ATT&CK framework, allowing us to categorize observed behaviors, prioritize responses, and effectively track progress. By mapping observed activities to specific ATT&CK techniques, we can better understand the attacker’s goals and the scope of the compromise. This structured approach significantly improves our efficiency and effectiveness in mitigating the impact of security incidents.
Incident Containment and Eradication Procedures
Containing and eradicating a security breach affecting customer data requires swift and decisive action. Our procedures involve isolating affected systems, preventing further data exfiltration, and systematically removing malicious code. This process follows a well-defined protocol that utilizes the MITRE ATT&CK framework to identify the specific techniques used by the attacker, guiding our remediation efforts. For example, if we detect the use of lateral movement techniques (e.g., Pass-the-Hash), our response will focus on securing accounts and network access points.
If data exfiltration is identified (e.g., using data staging techniques), we will prioritize securing the data stores and analyzing network traffic for indicators of compromise. The entire process is meticulously documented to ensure accountability and facilitate future improvements to our security posture.
Customer Communication During a Security Incident
Open and transparent communication with customers is paramount during a security incident. Our communication strategy prioritizes providing timely and accurate information about the incident, its impact on customer data, and the steps we’re taking to address the situation. We maintain a dedicated communication channel to keep customers informed of our progress. This might include email updates, website postings, and even phone calls, depending on the severity and scope of the incident.
We’ve prepared pre-written templates for different scenarios to ensure consistent messaging and avoid delays in communication. For example, in a situation where a data breach has exposed customer PII (Personally Identifiable Information), we’ll follow legal and regulatory requirements for notification, while simultaneously providing customers with advice on steps they can take to protect themselves, such as credit monitoring services.
This proactive approach builds trust and minimizes negative impact.
Incident Response Process Flowchart
Our incident response process is visualized in a flowchart. The flowchart starts with the initial detection of a security incident, which might be triggered by an intrusion detection system, a security information and event management (SIEM) system, or a user report. Next, the incident is triaged to assess its severity and impact. This triage involves mapping the observed behaviors to MITRE ATT&CK tactics and techniques.
Then, containment actions are implemented to isolate affected systems and prevent further damage. Eradication follows, which involves removing malware and restoring systems to a secure state. Recovery involves restoring data from backups and validating the integrity of systems. Finally, a post-incident review is conducted to identify lessons learned and improve our security posture. The entire process is documented meticulously, providing a detailed record of actions taken and their outcomes.
This record is crucial for continuous improvement and for demonstrating compliance with regulatory requirements.
Continuous Monitoring and Improvement
Maintaining robust customer safety in the digital realm isn’t a one-time fix; it’s an ongoing process requiring continuous vigilance and adaptation. Think of it like regular health checkups – preventative measures are far more effective and less costly than emergency room visits. Continuous monitoring and improvement are crucial for proactively identifying and mitigating emerging threats, ensuring your security controls remain effective, and ultimately protecting your customers.Regularly evaluating the effectiveness of your security controls is paramount.
A static security posture is a vulnerable one. The threat landscape is constantly evolving, with new attack vectors and sophisticated techniques emerging regularly. What worked yesterday might not be sufficient today. A proactive approach is essential to stay ahead of the curve.
Methods for Evaluating Security Control Effectiveness
Effective evaluation requires a multi-faceted approach. This includes regular vulnerability scans to identify weaknesses in your systems, penetration testing to simulate real-world attacks, and security audits to assess compliance with relevant standards and best practices. Log analysis plays a vital role, providing valuable insights into system activity and potential threats. Security Information and Event Management (SIEM) systems are invaluable for this purpose, aggregating and analyzing security data from various sources.
Finally, regular employee training and security awareness programs are crucial for mitigating human error, a major contributor to security breaches.
Metrics for Tracking Security Initiative Success
Tracking key metrics allows for objective assessment of your security posture and the effectiveness of implemented initiatives. These metrics can be both quantitative and qualitative. Quantitative metrics might include the number of vulnerabilities identified and remediated, the mean time to detect (MTTD) and mean time to respond (MTTR) to security incidents, and the reduction in successful phishing attempts.
Qualitative metrics could involve evaluating the effectiveness of employee training programs through phishing simulations or assessing the overall maturity of your security program using a recognized framework like the NIST Cybersecurity Framework. Tracking these metrics over time provides valuable insights into trends and areas needing improvement. For example, a consistent increase in MTTD might indicate a need for improved threat detection capabilities.
Proactive Threat Identification and Response System
A proactive system for identifying and addressing emerging threats should incorporate several key components. This includes utilizing threat intelligence feeds to stay informed about the latest threats and vulnerabilities, leveraging automated security tools such as intrusion detection and prevention systems (IDS/IPS), and establishing clear incident response plans. Regular security awareness training for employees is essential to enhance their ability to identify and report suspicious activities.
Furthermore, participating in industry threat intelligence sharing communities allows for collaborative threat mitigation and response. For instance, proactive monitoring of dark web forums for mentions of your organization’s brand or data leaks can provide early warning of potential attacks. Similarly, analyzing network traffic for unusual patterns or anomalies can indicate compromised systems or ongoing attacks. By combining these methods, a robust proactive system can be established to minimize the impact of emerging threats.
Visual Representation of Security Measures

A layered security approach is crucial for protecting customer data in today’s digital landscape. Visualizing this approach as a series of concentric circles, each representing a different security layer, helps understand how these layers work together to defend against attacks mapped to the MITRE ATT&CK framework. Each layer adds an additional barrier, making it harder for attackers to breach the system and access sensitive information.
A successful attack often requires bypassing multiple layers, highlighting the importance of a robust, multi-layered defense.
Layered Security Model, Keeping our customers safe with the mitre attck framework
We can visualize our security posture as a series of concentric circles, each representing a different layer of defense. The innermost circle represents the most sensitive data, while the outermost layers provide initial protection.
The outermost layer, the perimeter security, focuses on preventing unauthorized access to the network. This includes firewalls, intrusion detection/prevention systems (IDS/IPS), and secure web gateways. These tools monitor network traffic, blocking malicious activity and preventing initial access attempts, mitigating tactics such as initial access and execution within the MITRE ATT&CK framework.
The next layer focuses on network security, encompassing measures like segmentation, micro-segmentation, and data loss prevention (DLP) tools. This layer aims to limit the impact of a breach by containing the attacker within a specific network segment. This helps prevent lateral movement, a key tactic in many attacks, reducing the attacker’s ability to spread through the network and access more sensitive data, thereby addressing techniques like lateral movement and privilege escalation within the MITRE ATT&CK framework.
The third layer focuses on endpoint security. This includes measures like endpoint detection and response (EDR) software, antivirus, and strong endpoint access controls. These tools monitor individual devices for malicious activity, preventing malware execution and data exfiltration, countering tactics such as command and control and exfiltration.
The innermost layer focuses on data security. This includes data encryption, access control lists, and regular data backups. This layer ensures that even if an attacker gains access to the system, the data itself remains protected, mitigating the impact of data breaches and limiting the success of tactics like data exfiltration.
Impact of a Successful Attack on Customer Data
Imagine a scenario where an attacker successfully exploits a vulnerability in a web application (initial access). This vulnerability, perhaps an unpatched software flaw, allows the attacker to gain initial access to the network. They then use this access to move laterally (lateral movement) through the network, leveraging compromised credentials or exploiting weak security configurations. This lateral movement might involve accessing a database server (data access) holding customer data.
Once access is obtained, the attacker exfiltrates sensitive data (exfiltration) using techniques like encoding the data and sending it through covert channels, or simply downloading it directly. The consequences can be devastating, including significant financial losses due to regulatory fines, reputational damage, loss of customer trust, and potential legal action. The chain of events, from initial compromise to data exfiltration, can unfold rapidly, emphasizing the need for proactive security measures and swift incident response.
The impact extends beyond the immediate loss of data, encompassing the long-term costs associated with remediation, legal fees, and the restoration of customer confidence. This illustrates the real-world consequences of failing to adequately protect customer data, and the importance of a robust and layered security approach, directly addressing many techniques within the MITRE ATT&CK framework.
Concluding Remarks
Ultimately, keeping our customers safe with the MITRE ATT&CK framework is a continuous journey, not a destination. It requires constant vigilance, adaptation to emerging threats, and a commitment to ongoing improvement. By leveraging this powerful framework and implementing the strategies discussed, we aim to not only protect our customers’ data but also foster a culture of security that prioritizes trust and transparency.
Our commitment to proactive security and robust incident response ensures that we are prepared for any eventuality, always striving to maintain the highest level of customer data protection.
Detailed FAQs
What is the MITRE ATT&CK framework in simple terms?
It’s a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations. We use it to understand how attackers operate and build defenses against them.
How often should we update our security measures based on the MITRE ATT&CK framework?
Regularly! The threat landscape is constantly evolving, so we need to adapt our defenses frequently. We conduct regular assessments and updates based on new MITRE ATT&CK updates and emerging threats.
What happens if a security breach occurs despite our efforts?
We have a comprehensive incident response plan in place to contain, eradicate, and recover from any breach. Transparency with our customers is paramount during such events.
How does the MITRE ATT&CK framework help with employee training?
It provides a framework for understanding common attack vectors and allows us to tailor our training programs to address specific threats relevant to our environment and employees’ roles.