Killnet Targeting Healthcare Apps on Microsoft Azure
Killnet targeting healthcare apps hosted on Microsoft Azure is a serious threat. This notorious cybercrime group employs sophisticated tactics, leveraging vulnerabilities in Azure’s infrastructure and the applications themselves to disrupt critical healthcare services. Their attacks, often involving devastating distributed denial-of-service (DDoS) assaults, can severely impact patient care, from delaying appointments to blocking access to crucial medical records. The potential consequences are far-reaching, affecting not only individual patients but also the broader healthcare system’s stability and public trust.
Killnet’s methods are constantly evolving, making it crucial to understand their attack vectors and the vulnerabilities they exploit. This includes examining their use of various DDoS attack types, the specific techniques used to compromise application functionality, and the potential for data breaches. Understanding Microsoft Azure’s security measures and the strategies employed to mitigate these attacks is equally important.
This analysis delves into the multifaceted nature of this threat, exploring the impact on healthcare services, the technological defenses in place, and the legal and ethical implications of such cyberattacks.
Killnet’s Tactics and Methods Against Healthcare Apps: Killnet Targeting Healthcare Apps Hosted On Microsoft Azure
Killnet, a prominent pro-Russian cybercrime group, has demonstrated a willingness to target critical infrastructure, including healthcare applications hosted on Microsoft Azure. Their attacks are characterized by a combination of sophisticated techniques and a focus on disrupting services rather than simply stealing data. Understanding their methods is crucial for bolstering the security posture of healthcare organizations reliant on cloud-based systems.
Killnet’s Attack Vectors Against Azure-Hosted Applications
Killnet leverages several attack vectors to target Azure-hosted healthcare applications. These commonly include exploiting known vulnerabilities in web applications, utilizing botnets for Distributed Denial-of-Service (DDoS) attacks, and attempting to compromise user accounts through phishing or credential stuffing. The group often focuses on applications with publicly accessible interfaces, making them easier targets. They may also explore less-common attack surfaces, such as misconfigured cloud storage or improperly secured APIs.
Vulnerabilities Exploited in Healthcare Applications
Healthcare applications, often built with legacy systems and facing tight deadlines for implementation, can be particularly vulnerable to Killnet’s tactics. Common vulnerabilities exploited include SQL injection flaws, cross-site scripting (XSS) vulnerabilities, and insecure authentication mechanisms. These vulnerabilities can allow attackers to gain unauthorized access to sensitive patient data or disrupt application functionality. For example, an SQL injection vulnerability could allow Killnet to manipulate database queries, potentially deleting or altering patient records.
A successful XSS attack could allow them to inject malicious JavaScript code, redirecting users to phishing sites or compromising their sessions.
Killnet’s Use of DDoS Attacks in Targeting Healthcare Services
DDoS attacks are a cornerstone of Killnet’s strategy against healthcare services. By overwhelming the target application with a flood of traffic from numerous sources, they aim to render the service unavailable to legitimate users. This can have severe consequences in healthcare, delaying or preventing access to critical services such as electronic health records, telehealth platforms, and appointment scheduling systems. The sheer volume of traffic generated by these attacks can cripple even well-protected systems.
Techniques Used to Disrupt Healthcare App Functionality
Killnet employs a variety of techniques to disrupt healthcare app functionality. Beyond simple volumetric DDoS attacks, they may utilize application-layer attacks, targeting specific application functions to maximize disruption. This might involve flooding the application with malformed requests or exploiting known vulnerabilities to exhaust system resources. They may also use sophisticated techniques like slowloris attacks, which slowly consume server resources without generating large amounts of traffic, making detection more difficult.
The goal is not necessarily data exfiltration, but rather to cause maximum operational disruption.
Comparison of DDoS Attack Types Used by Killnet
| Attack Type | Description | Impact on Healthcare | Mitigation Strategies |
|---|---|---|---|
| Volumetric DDoS | Floods the target with massive amounts of traffic from multiple sources. | Complete unavailability of services, impacting patient care, administrative tasks, and research. | Implement robust DDoS mitigation solutions, including cloud-based protection and traffic scrubbing. |
| Protocol DDoS | Exploits vulnerabilities in network protocols to exhaust server resources. | Disruption of specific services or functionalities, leading to delays and potential errors. | Utilize intrusion detection and prevention systems (IDPS), and regularly update network devices. |
| Application-Layer DDoS | Targets specific application functionalities with malformed requests. | Slowdowns and service interruptions affecting specific application features, like appointment scheduling or electronic health records access. | Implement web application firewalls (WAFs), robust input validation, and rate limiting. |
| Slowloris | Slowly consumes server resources with a low volume of requests. | Gradual degradation of service performance, eventually leading to complete unavailability. | Employ advanced monitoring and detection systems capable of identifying slowloris attacks. |
Impact on Healthcare Services and Patients

Killnet’s attacks targeting healthcare applications hosted on Microsoft Azure represent a significant threat to the smooth functioning of healthcare services and, ultimately, the well-being of patients. The potential consequences extend far beyond simple service disruptions; they can lead to serious medical errors, compromised patient safety, and substantial financial losses for healthcare providers.Disruptions caused by these attacks can have cascading effects across various aspects of patient care.
The interconnected nature of modern healthcare systems means that a seemingly isolated attack on one application can trigger a ripple effect, impacting numerous other services and departments.
Killnet’s attacks on healthcare apps hosted on Microsoft Azure highlight the vulnerability of critical systems. Building robust, secure applications is crucial, and that’s where exploring development options like those discussed in this article on domino app dev the low code and pro code future becomes incredibly important. Understanding these modern approaches could help developers create more resilient healthcare applications, better protected from threats like those posed by Killnet.
Consequences of Disrupted Appointment Scheduling
The inability to access appointment scheduling applications directly impacts patient access to care. Delayed or missed appointments can lead to worsening health conditions, particularly for patients with chronic illnesses requiring regular monitoring or treatment. Furthermore, administrative staff spend significant time and resources attempting to reschedule appointments and manage the resulting backlog, diverting resources from direct patient care. This can lead to increased wait times for patients, potentially exacerbating anxiety and frustration.
Consider a situation where a large oncology clinic experiences a complete outage of its scheduling system for 24 hours. Hundreds of appointments would be affected, leading to significant patient inconvenience and potential delays in critical cancer treatments.
Effects of Impaired Access to Patient Records
Access to accurate and up-to-date patient records is crucial for providing safe and effective care. Attacks that compromise access to electronic health records (EHRs) can severely hinder a clinician’s ability to make informed decisions. Imagine a scenario where a doctor needs to access a patient’s allergy history during an emergency situation but cannot access the EHR due to a denial-of-service attack.
This could have life-threatening consequences. The resulting delays in treatment can lead to adverse health outcomes and increase the risk of medical errors. Furthermore, the inability to share records between healthcare providers involved in a patient’s care can fragment care and lead to inconsistencies in treatment.
Real-World Examples of Similar Attacks
While Killnet’s specific attacks on Azure-hosted healthcare apps may not yet have widely publicized, large-scale consequences, we can learn from past attacks on healthcare systems. The 2017 WannaCry ransomware attack crippled hospitals worldwide, demonstrating the vulnerability of healthcare systems to cyberattacks and the devastating consequences of data breaches and system outages. Hospitals were forced to divert ambulances, postpone surgeries, and turn away patients.
This resulted in significant patient harm and substantial financial losses. The NotPetya attack in 2017 also significantly impacted healthcare organizations globally, causing widespread disruption and demonstrating the far-reaching consequences of such attacks.
Financial Losses from Service Disruptions
The financial implications of Killnet’s attacks on healthcare apps are substantial. Direct costs include lost revenue from cancelled appointments, the expense of restoring systems, and the cost of hiring cybersecurity experts to mitigate the attack. Indirect costs include lost productivity, reputational damage, and potential legal liabilities. For example, a large hospital system experiencing a week-long outage of its EHR system could face millions of dollars in lost revenue and recovery costs.
These costs are ultimately passed on to patients through higher healthcare premiums and reduced access to care.
Long-Term Effects on Patient Trust and Healthcare Infrastructure
Repeated attacks on healthcare systems erode public trust in the ability of healthcare providers to protect sensitive patient data and ensure the reliable delivery of care. This loss of trust can lead to decreased patient utilization of services, further exacerbating existing healthcare access challenges. Moreover, the need for increased cybersecurity measures and the cost of recovery from attacks places a significant strain on already stretched healthcare budgets, diverting resources from other critical areas like staffing and equipment upgrades.
The long-term impact on healthcare infrastructure could involve increased investment in robust cybersecurity systems, potentially at the expense of other essential services. This necessitates a proactive approach to cybersecurity, including regular security assessments, employee training, and the implementation of advanced security technologies.
Microsoft Azure’s Security Measures and Response
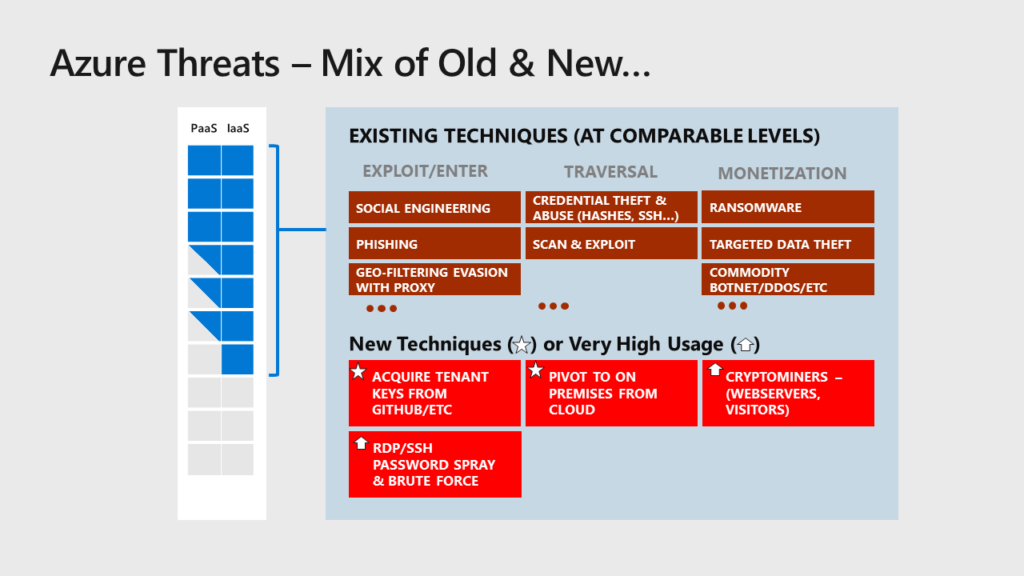
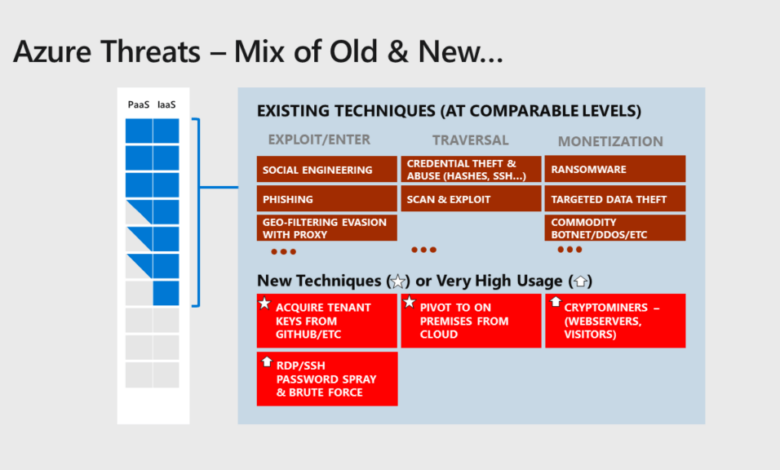
Microsoft Azure, like other major cloud providers, offers a robust suite of security features designed to mitigate various threats, including DDoS attacks like those launched by Killnet. Understanding these features and Azure’s response mechanisms is crucial for healthcare organizations relying on its services. This section will delve into the specifics of Azure’s security posture and its approach to incident management in the face of sophisticated cyberattacks.Azure’s security capabilities are multifaceted, encompassing preventative measures, detection systems, and response protocols.
A layered approach is employed, combining network security, platform security, and application-level security to create a comprehensive defense strategy.
Azure’s DDoS Protection
Azure offers various DDoS protection services, ranging from basic protection integrated into the platform to more advanced, dedicated services. The basic protection leverages Azure’s global network infrastructure to automatically mitigate low-level attacks. For higher-threat scenarios, Azure DDoS Protection Standard and Premium provide more sophisticated mitigation capabilities, including advanced analytics and custom configurations tailored to specific application needs. These services utilize machine learning algorithms to identify and respond to attacks in real-time, effectively absorbing malicious traffic and minimizing service disruption.
For example, Azure DDoS Protection Standard can automatically detect and mitigate attacks based on pre-defined thresholds, while Premium allows for more granular control and customized rules.
Azure’s Incident Response Mechanisms
Azure’s incident response is a collaborative effort involving automated systems and human expertise. Automated systems continuously monitor for suspicious activity, alerting security teams to potential threats. These alerts trigger predefined workflows, which may include automated mitigation actions or escalation to human responders. Azure’s Security Center provides a centralized dashboard for monitoring security alerts, investigating incidents, and managing responses.
Microsoft’s security experts are also available to assist customers in responding to major incidents, providing guidance and support throughout the process. The response process often involves isolating affected systems, analyzing the attack, implementing remediation measures, and restoring services. Post-incident analysis is crucial to identifying vulnerabilities and improving future defenses.
Azure Security Best Practices for Healthcare Applications
Implementing robust security measures is paramount for healthcare applications hosted on Azure. Best practices include utilizing Azure’s built-in security features, regularly patching systems and applications, implementing multi-factor authentication (MFA) for all user accounts, and leveraging Azure’s role-based access control (RBAC) to limit user privileges. Regular security assessments and penetration testing can identify vulnerabilities before they can be exploited.
Data encryption both in transit and at rest is essential to protect sensitive patient information. Compliance with relevant regulations, such as HIPAA in the US, is also a critical aspect of secure healthcare application deployment. For instance, implementing Azure Information Protection can help classify and protect sensitive data based on predefined policies.
Comparison of Azure Security with Other Cloud Providers
Azure’s security features are comparable to those offered by other major cloud providers like AWS and Google Cloud Platform (GCP). All three offer robust DDoS protection, advanced threat detection systems, and comprehensive security tools. However, the specific features and their implementation may differ slightly. The choice of cloud provider often depends on specific organizational needs, existing infrastructure, and compliance requirements.
A thorough evaluation of each provider’s security offerings is crucial before making a decision. For example, AWS offers Shield, GCP offers Cloud Armor, and Azure offers Azure DDoS Protection, each with its own strengths and weaknesses.
Hypothetical Incident Response Plan: Killnet Attack on Azure-Hosted Healthcare App
Let’s consider a scenario where a Killnet DDoS attack targets a healthcare application hosted on Azure. The incident response plan would involve the following steps:
- Detection and Alerting: Azure’s monitoring systems detect unusual network traffic patterns consistent with a DDoS attack.
- Mitigation: Azure DDoS Protection automatically mitigates the attack, leveraging its global network infrastructure and machine learning capabilities.
- Incident Investigation: Security teams analyze the attack’s characteristics, identifying the attack vector and its source.
- Containment: Affected systems are isolated to prevent further damage or data breaches.
- Remediation: Vulnerabilities are addressed, and security configurations are strengthened to prevent future attacks. This might involve updating security policies or adjusting DDoS mitigation settings.
- Recovery: Services are restored, and data integrity is verified.
- Post-Incident Analysis: A detailed analysis of the attack is conducted to identify areas for improvement in security posture.
This plan would leverage Azure’s built-in security features and incident response capabilities, while also incorporating best practices for handling cyberattacks. Regular testing and refinement of the plan are essential to ensure its effectiveness.
Mitigation and Prevention Strategies
The recent Killnet attacks highlight the critical need for robust security measures within the healthcare sector, especially for applications hosted on cloud platforms like Microsoft Azure. Strengthening defenses requires a multi-faceted approach, focusing on identifying vulnerabilities, implementing best practices, and proactively enhancing security posture. This section details key strategies for mitigation and prevention.
Key Vulnerabilities in Healthcare Applications, Killnet targeting healthcare apps hosted on microsoft azure
Healthcare applications often contain vulnerabilities stemming from legacy systems, outdated software, and insufficient security protocols. Common weaknesses include SQL injection vulnerabilities, allowing attackers to manipulate database queries; cross-site scripting (XSS) flaws, enabling attackers to inject malicious scripts into websites; and insecure authentication mechanisms, allowing unauthorized access. Furthermore, insufficient input validation can lead to buffer overflows and other exploitation opportunities.
These vulnerabilities are often exacerbated by a lack of regular security updates and patching.
Best Practices for Securing Healthcare Applications on Azure
Securing healthcare applications hosted on Azure requires leveraging the platform’s built-in security features and implementing robust application-level security controls. This includes utilizing Azure’s security center for threat detection and response, implementing multi-factor authentication (MFA) for all user accounts, and regularly patching applications and underlying infrastructure. Employing a principle of least privilege, granting users only the necessary access rights, minimizes the impact of compromised accounts.
Regular security assessments and penetration testing are also crucial to identify and remediate vulnerabilities before attackers can exploit them. Azure’s built-in tools, such as Azure Firewall and Web Application Firewall (WAF), should be properly configured to filter malicious traffic and protect against common attacks.
Recommended Security Measures to Prevent Future Attacks
A comprehensive security strategy should incorporate several key measures. This includes implementing a robust intrusion detection and prevention system (IDPS) to monitor network traffic for suspicious activity. Regular vulnerability scanning and penetration testing should be performed to identify and address security weaknesses. Employing a secure development lifecycle (SDLC) that integrates security practices throughout the software development process is essential.
This includes conducting code reviews, performing security testing, and implementing secure coding practices to prevent vulnerabilities from being introduced in the first place. Finally, implementing a comprehensive incident response plan ensures a coordinated and effective response to security incidents.
Examples of Proactive Security Measures
Proactive security measures go beyond reactive patching and involve anticipating potential threats. Implementing a zero-trust security model, where every user and device is verified before access is granted, regardless of network location, significantly reduces the attack surface. Regular security awareness training for staff can help prevent phishing attacks and other social engineering attempts. Utilizing advanced threat protection tools, such as those offered by Azure Sentinel, allows for real-time threat detection and automated response.
Implementing data loss prevention (DLP) measures prevents sensitive patient data from leaving the organization’s control.
Regular Security Audits and Penetration Testing Enhance Resilience
Regular security audits provide an independent assessment of an organization’s security posture. These audits identify vulnerabilities and weaknesses that may have been missed during internal assessments. Penetration testing simulates real-world attacks to identify exploitable vulnerabilities and assess the effectiveness of security controls. Combining both regular audits and penetration testing provides a comprehensive approach to identifying and mitigating security risks, significantly enhancing the resilience of healthcare applications against attacks like those launched by Killnet.
The frequency of these activities should be based on risk assessment, with higher-risk applications receiving more frequent attention.
Legal and Ethical Considerations
Killnet’s attacks on healthcare providers raise serious legal and ethical concerns, extending beyond the immediate disruption of services. The targeting of vulnerable systems handling sensitive patient data carries significant ramifications under both domestic and international law, demanding a comprehensive understanding of the legal landscape and ethical implications.
Legal Ramifications of Killnet’s Actions
Killnet’s actions against healthcare providers constitute a range of potential legal offenses, varying depending on the jurisdiction and specific nature of the attack. These could include violations of computer fraud and abuse statutes, data breach notification laws, and potentially even charges related to terrorism or endangering public safety if the attacks result in significant harm or loss of life.
The scale and international nature of Killnet’s operations further complicate legal pursuit, requiring international cooperation and the careful consideration of extradition treaties. For example, a successful denial-of-service attack causing the death of a patient waiting for critical care could lead to manslaughter charges in addition to cybercrime offenses.
Ethical Implications of Targeting Healthcare Systems
Targeting healthcare systems is ethically reprehensible. These systems are crucial for maintaining public health and well-being, and attacks on them directly endanger vulnerable patients who rely on these services for life-sustaining treatment or critical care. The deliberate disruption of healthcare services, regardless of the attacker’s motivations, demonstrates a profound disregard for human life and basic ethical principles. The lack of consideration for the potential consequences on patients, staff, and the wider community highlights the severe moral failing inherent in such attacks.
The ethical implications extend beyond the immediate impact, encompassing long-term damage to public trust in healthcare institutions and the potential chilling effect on innovation and investment in the sector.
Relevant International Laws and Regulations
Several international laws and regulations address cyberattacks, particularly those targeting critical infrastructure like healthcare. The Budapest Convention on Cybercrime, for instance, provides a framework for international cooperation in investigating and prosecuting cybercrimes. Furthermore, the Council of Europe Convention 108 (and its updated version, 108bis) on data protection offers guidelines for the handling of personal data, emphasizing the need for robust security measures to prevent breaches.
While these conventions provide a foundation, the enforcement and application often depend on individual nation-states’ laws and legal systems. The challenge lies in effectively coordinating international responses to prosecute actors operating across borders, like Killnet.
Responsibilities of Healthcare Providers in Protecting Patient Data and Systems
Healthcare providers bear a significant responsibility to protect patient data and systems from cyberattacks. This includes implementing robust security measures such as multi-factor authentication, regular security audits, and employee training on cybersecurity best practices. Compliance with regulations like HIPAA in the United States and GDPR in Europe is crucial. Furthermore, providers should develop incident response plans to effectively manage and mitigate the impact of cyberattacks.
Failure to meet these responsibilities can lead to legal liabilities, reputational damage, and financial penalties. A failure to adequately protect patient data can result in significant fines and legal action from regulatory bodies and individuals whose data has been compromised.
Potential Legal Actions Against Killnet and Its Members
Various legal actions can be pursued against Killnet and its members. These include civil lawsuits for damages caused by the attacks, criminal prosecutions under national and international laws, and asset seizure to compensate victims. International cooperation will be essential in identifying and prosecuting members located in different countries. The challenges lie in tracing the perpetrators, gathering evidence across jurisdictions, and overcoming jurisdictional limitations.
However, successful prosecutions could serve as a significant deterrent against future attacks. Examples include pursuing charges under the Computer Fraud and Abuse Act (CFAA) in the US, or similar legislation in other countries, for unauthorized access and damage to computer systems.
Final Summary
The targeting of healthcare applications by Killnet on Microsoft Azure highlights the critical need for robust cybersecurity measures within the healthcare sector. While Azure offers a range of security features, proactive measures such as regular security audits, penetration testing, and the implementation of best practices are crucial for mitigating the risk of successful attacks. The potential consequences—from disrupted patient care and financial losses to damage to public trust—underscore the importance of a multi-layered approach to cybersecurity that addresses both technological vulnerabilities and the legal and ethical implications of such attacks.
The fight against these malicious actors requires continuous vigilance and adaptation.
Common Queries
What specific types of healthcare apps are most vulnerable to Killnet attacks?
Apps with weak authentication, outdated software, and insufficient DDoS protection are prime targets. Those handling sensitive patient data are particularly vulnerable.
How can healthcare providers improve their resilience against Killnet attacks?
Implementing multi-factor authentication, regularly patching software, utilizing cloud-based DDoS mitigation services, and conducting regular security audits are key.
What is the role of international cooperation in combating Killnet?
International collaboration is vital for sharing threat intelligence, coordinating responses, and pursuing legal action against Killnet members across borders.
What are the long-term implications of successful Killnet attacks on patient trust?
Successful attacks can erode public trust in healthcare providers and systems, leading to hesitancy in seeking care and potentially delaying diagnosis and treatment.