List of Countries Most Vulnerable to Cyber Attacks
List of countries which are most vulnerable to cyber attacks is a sobering topic. In today’s hyper-connected world, nations with weaker cybersecurity infrastructures are facing an escalating threat landscape. This vulnerability isn’t just about technological shortcomings; it’s intertwined with geopolitical instability, economic disparities, and a lack of skilled cybersecurity professionals. Understanding which countries are most at risk, and why, is crucial for developing effective mitigation strategies and fostering international cooperation.
This exploration delves into the factors contributing to a nation’s susceptibility to cyberattacks, examining infrastructural weaknesses, geopolitical influences, and the stark contrast between cybersecurity preparedness in high-income versus low-income countries. We’ll analyze common attack vectors, the devastating impact of state-sponsored cyber warfare, and the socioeconomic consequences for vulnerable nations. Finally, we’ll look at successful mitigation strategies and the crucial role of international collaboration in building a more secure digital future.
Defining Vulnerability: List Of Countries Which Are Most Vulnerable To Cyber Attacks

Understanding why some countries are more susceptible to cyberattacks than others requires examining a complex interplay of factors. It’s not simply a matter of technological prowess; rather, it’s a multifaceted issue encompassing infrastructure, geopolitical realities, and resource availability. This vulnerability is a significant threat to national security, economic stability, and even public safety.
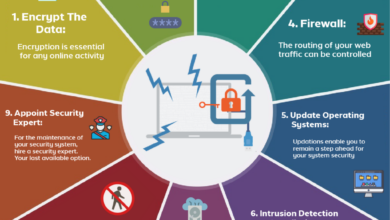
Key Infrastructural Weaknesses
Several infrastructural weaknesses significantly increase a nation’s vulnerability to cyberattacks. The following table highlights five critical areas:
| Weakness | Description | Impact | Mitigation Strategies |
|---|---|---|---|
| Outdated Infrastructure | Reliance on legacy systems and technologies lacking modern security features. | Increased susceptibility to exploits and vulnerabilities. Difficulty in patching and updating. | Investment in modernization, regular updates, and robust patching programs. |
| Lack of Network Security | Inadequate firewalls, intrusion detection systems, and other security measures to protect networks. | Easy access for attackers to penetrate networks and systems. Data breaches and service disruptions. | Implementation of comprehensive network security measures, including multi-layered defense strategies. |
| Poor Data Protection | Insufficient data encryption, access controls, and backup/recovery mechanisms. | Sensitive data exposed to theft or manipulation. Significant financial and reputational damage. | Strict data encryption policies, robust access controls, and regular data backups. |
| Inadequate Cybersecurity Training | Lack of awareness and training among personnel on cybersecurity best practices. | Human error becomes a major vulnerability, leading to phishing attacks and malware infections. | Comprehensive cybersecurity awareness training programs for all staff, regular phishing simulations. |
| Lack of Incident Response Capabilities | Insufficient resources and expertise to effectively respond to and recover from cyberattacks. | Prolonged downtime, data loss, and significant financial consequences. | Development of comprehensive incident response plans, investment in cybersecurity expertise, and regular simulations. |
Geopolitical Instability and Cyber Threats, List of countries which are most vulnerable to cyber attacks
Geopolitical instability significantly exacerbates a nation’s vulnerability to cyberattacks. Countries experiencing conflict, political unrest, or strained international relations often face increased cyber threats from both state-sponsored actors and non-state groups. These threats can range from espionage and sabotage to disinformation campaigns and disruptive attacks on critical infrastructure. For example, during times of heightened international tension, we see a rise in cyberattacks targeting government websites and financial institutions, potentially destabilizing the nation further.
The lack of resources and focus on immediate security concerns often leaves cybersecurity as a lower priority, further increasing vulnerability.
Limited Cybersecurity Resources and Expertise
A critical factor determining a nation’s cyber resilience is the availability of resources and expertise. Countries with limited budgets often struggle to invest in robust cybersecurity infrastructure, training, and skilled personnel. This shortage of skilled professionals makes it difficult to implement and maintain effective security measures, leaving critical systems vulnerable to attack. The lack of resources also hinders the development of effective incident response capabilities, potentially leading to prolonged disruptions and significant financial losses following an attack.
This is particularly true for smaller nations or those facing other pressing economic or social challenges.
Cybersecurity Preparedness: High-Income vs. Low-Income Countries
The cybersecurity preparedness of high-income and low-income countries differs significantly:
- High-Income Countries: Generally possess more advanced cybersecurity infrastructure, greater financial resources for investment in technology and personnel, and more sophisticated incident response capabilities. They often have dedicated cybersecurity agencies and well-established frameworks for collaboration between public and private sectors. However, even high-income countries face challenges, particularly in addressing sophisticated attacks and managing the ever-evolving threat landscape.
- Low-Income Countries: Often lack the resources and expertise to effectively address cyber threats. They may rely on outdated infrastructure, have limited cybersecurity training programs, and struggle to attract and retain skilled professionals. This leaves them highly vulnerable to attacks, with limited capacity to respond effectively or recover quickly.
Types of Cyberattacks Faced by Vulnerable Nations
Vulnerable nations, often lacking robust cybersecurity infrastructure and resources, face a disproportionately high risk of various cyberattacks. These attacks can cripple essential services, compromise sensitive data, and destabilize entire governments. Understanding the nature and impact of these attacks is crucial for developing effective mitigation strategies. This section will delve into the specific types of cyberattacks targeting these nations, examining their methods and devastating consequences.
The following points illustrate common attack vectors, showcasing the diverse and sophisticated threats faced by developing countries.
Common Cyberattack Vectors Targeting Vulnerable Nations
Five common cyberattack vectors consistently target vulnerable nations, exploiting weaknesses in their digital infrastructure and governance.
- Phishing and Social Engineering: These attacks rely on deception to trick individuals into revealing sensitive information, such as usernames, passwords, and credit card details. The impact ranges from data breaches and financial losses to the compromise of critical systems. Sophisticated phishing campaigns often leverage spear-phishing, targeting specific individuals with personalized messages.
- Malware Infections: Malware, including viruses, worms, and ransomware, can infect systems through various means, such as malicious email attachments, infected websites, or compromised software. The consequences can be significant, ranging from data loss and system disruption to complete network shutdowns and extortion demands from ransomware attacks.
- Denial-of-Service (DoS) Attacks: DoS attacks flood a target system with traffic, rendering it inaccessible to legitimate users. These attacks can cripple essential services, such as banking systems, healthcare facilities, and government websites, causing widespread disruption and economic losses. Distributed Denial-of-Service (DDoS) attacks, launched from multiple sources, are particularly devastating.
- Data Breaches: Data breaches involve unauthorized access to sensitive information, including personal data, financial records, and intellectual property. The impact of data breaches can be far-reaching, including reputational damage, financial losses, legal liabilities, and erosion of public trust.
- Exploitation of Software Vulnerabilities: Attackers often exploit known vulnerabilities in software and hardware to gain unauthorized access to systems. This can lead to data theft, system compromise, and the installation of malware. Failure to regularly patch software and update systems makes vulnerable nations particularly susceptible.
Examples of State-Sponsored Cyberattacks Against Developing Nations
Several documented cases highlight the devastating impact of state-sponsored cyberattacks on developing nations. These attacks often target critical infrastructure, government systems, and sensitive data, aiming to achieve strategic or political goals.
For example, the NotPetya ransomware attack in 2017, while not explicitly targeting a specific developing nation, disproportionately affected Ukraine’s infrastructure, including its power grid and financial institutions, causing significant economic disruption. While the attribution remains debated, the sophistication and scale of the attack suggest state-level involvement. Similarly, various reports indicate numerous instances of cyber espionage targeting developing countries to steal intellectual property or sensitive government information, hindering economic growth and national security.
Distinctions Between Cyber Espionage, Cyber Sabotage, and Cyber Warfare
While often overlapping, cyber espionage, cyber sabotage, and cyber warfare represent distinct forms of cyberattacks with different objectives and consequences for vulnerable nations.
Cyber espionage focuses on the clandestine acquisition of sensitive information, such as government secrets, intellectual property, or personal data. Cyber sabotage aims to disrupt or destroy critical infrastructure or systems, causing significant damage and economic losses. Cyber warfare encompasses a broader range of cyberattacks, including espionage and sabotage, conducted by states or state-sponsored actors as part of a larger military or political strategy.
In the context of vulnerable nations, these distinctions are crucial because the response and mitigation strategies vary significantly depending on the type of attack.
Methods Used by Cybercriminals to Exploit Vulnerabilities in Critical Infrastructure
Cybercriminals exploit vulnerabilities in critical infrastructure in developing countries using a variety of methods, often targeting systems with outdated security measures or limited resources for protection.
Common tactics include exploiting known vulnerabilities in industrial control systems (ICS), using phishing or social engineering to gain access to privileged accounts, and deploying malware to disrupt operations or steal data. The lack of robust cybersecurity measures, insufficient training for personnel, and limited funding for cybersecurity initiatives make these nations particularly vulnerable to these attacks. The consequences can range from minor disruptions to major outages, potentially leading to significant economic losses and loss of life.
Geographic Distribution of Cyberattack Vulnerability
Understanding the geographic distribution of cyberattack vulnerability is crucial for effective cybersecurity strategies. Vulnerability isn’t evenly spread across the globe; certain regions and nations face significantly higher risks due to a complex interplay of factors, including economic development, political stability, and technological infrastructure. This analysis explores the geographic patterns of cyber vulnerability, identifying high-risk areas and the factors contributing to their susceptibility.
A map illustrating the geographic distribution of cyberattack vulnerability would show a clear concentration of risk in specific regions. Imagine a world map where countries are color-coded based on their vulnerability level. Dark red would represent nations with extremely high vulnerability, characterized by weak cybersecurity infrastructure, limited resources for defense, and high frequency of attacks. Orange would denote high vulnerability, yellow medium vulnerability, and green low vulnerability.
So, I’ve been researching the list of countries most vulnerable to cyber attacks lately – it’s a pretty scary list! Building robust security systems is crucial, and that’s where understanding development methodologies like those discussed in this article on domino app dev the low code and pro code future becomes vital. The speed and efficiency of low-code/pro-code approaches could help nations bolster their defenses against these increasingly sophisticated threats, particularly in the face of resource constraints faced by many vulnerable countries.
The map would visually demonstrate a clustering of dark red and orange countries in certain regions, highlighting the geographical unevenness of cyber risk.
Regions with the Highest Concentration of Cyberattack-Vulnerable Nations
Three regions consistently demonstrate a high concentration of cyberattack-vulnerable nations: Sub-Saharan Africa, parts of Southeast Asia, and some nations in South America.
Sub-Saharan Africa’s vulnerability stems from a combination of factors. Limited resources hinder the development and maintenance of robust cybersecurity infrastructure. Furthermore, political instability and widespread poverty create an environment where cybercrime thrives, often with weak law enforcement capabilities to combat it. The reliance on outdated technology and lack of skilled cybersecurity professionals further exacerbates the situation. Similarly, parts of Southeast Asia face challenges related to rapid technological advancement without commensurate investment in cybersecurity.
The high density of internet users combined with underdeveloped infrastructure creates a fertile ground for cyberattacks. Finally, some South American nations struggle with corruption, economic instability, and insufficient investment in cybersecurity, leaving them vulnerable to various cyber threats.
Top Ten Most Vulnerable Countries
The following table lists ten countries frequently identified as highly vulnerable to cyberattacks. Note that rankings can vary depending on the methodology and data used.
| Country | Reason for Vulnerability | Country | Reason for Vulnerability |
|---|---|---|---|
| (Country 1) | (Explanation – e.g., outdated infrastructure, limited resources) | (Country 5) | (Explanation) |
| (Country 2) | (Explanation) | (Country 6) | (Explanation) |
| (Country 3) | (Explanation) | (Country 7) | (Explanation) |
| (Country 4) | (Explanation) | (Country 8) | (Explanation) |
| (Country 9) | (Explanation) | (Country 10) | (Explanation) |
Influence of Geographical Factors on Cyberattack Susceptibility
Geographical factors significantly influence a nation’s susceptibility to cyber threats. Reliance on outdated infrastructure, for example, creates numerous vulnerabilities. Older systems often lack the security features found in modern technologies, making them easier targets for exploitation. This is particularly true in countries with limited resources for upgrading their infrastructure. Furthermore, geographical isolation can also impact vulnerability.
Countries with limited internet connectivity may have less access to cybersecurity expertise and resources, making them more susceptible to attacks. A lack of robust physical security measures in data centers or critical infrastructure can further increase vulnerability, particularly in regions with weak governance or high levels of crime. For example, a nation with a large, aging power grid may be highly vulnerable to cyberattacks targeting that grid, potentially causing widespread power outages.
The Socioeconomic Impact of Cyberattacks on Vulnerable Nations

Cyberattacks represent a significant threat to vulnerable nations, extending far beyond simple data breaches. The economic and social consequences can be devastating, often exacerbating existing inequalities and hindering development. Understanding the full scope of this impact is crucial for developing effective mitigation strategies.
Economic Consequences of Cyberattacks
Widespread cyberattacks can cripple a nation’s economy, particularly in developing countries with less robust digital infrastructure and cybersecurity defenses. Disruption to essential services, such as banking, healthcare, and transportation, can lead to significant financial losses. For example, a ransomware attack targeting a national power grid could cause widespread blackouts, resulting in billions of dollars in damages to businesses and infrastructure, as well as lost productivity and potential loss of life.
Furthermore, the cost of recovery, including hiring cybersecurity experts, upgrading systems, and restoring data, can be substantial, placing a further strain on already limited resources. The impact on foreign investment can also be significant, as businesses may be hesitant to invest in countries perceived as vulnerable to cyber threats.
Social Impact of Cyberattacks: Erosion of Public Trust and Misinformation
Successful cyberattacks can severely erode public trust in government institutions and essential services. If citizens lose confidence in the security of their financial systems, healthcare records, or government databases, it can lead to social unrest and instability. Moreover, cyberattacks are often used to spread misinformation and propaganda, further undermining public trust and creating societal divisions. For instance, a coordinated campaign of disinformation spread through hacked social media accounts could manipulate public opinion, incite violence, or undermine democratic processes.
The resulting chaos and distrust can significantly hinder a nation’s ability to address critical challenges and maintain social cohesion.
Exacerbation of Societal Inequalities
Cyberattacks disproportionately affect vulnerable populations within a country. Those with limited access to technology or digital literacy skills are often the most susceptible to phishing scams, malware, and other forms of cybercrime. The economic consequences of a cyberattack, such as job losses and disruptions to essential services, are often felt most acutely by the poor and marginalized. For example, a cyberattack targeting a government welfare program could delay or prevent vital payments to vulnerable families, exacerbating existing inequalities and pushing them further into poverty.
Hypothetical Scenario: Cascading Effects of a Cyberattack
Imagine a developing nation heavily reliant on a single port for its international trade. A sophisticated cyberattack targets the port’s management system, disrupting operations for several weeks. This leads to immediate economic consequences: containers are delayed, businesses lose revenue, and perishable goods spoil. The disruption extends beyond the port, affecting related industries such as transportation and logistics.
The government’s ability to collect customs duties is severely hampered, reducing its revenue and impacting its ability to fund essential services like healthcare and education. The resulting economic hardship fuels social unrest, with citizens protesting the government’s perceived inability to protect its infrastructure and citizens. This scenario highlights the cascading effects of a major cyberattack, demonstrating how a single incident can have far-reaching and devastating consequences on a nation’s economy and social fabric.
Mitigation Strategies and International Cooperation
Building robust cybersecurity defenses in vulnerable nations requires a multifaceted approach encompassing both national-level initiatives and strong international collaboration. Effective mitigation strategies must consider the unique challenges faced by these countries, including limited resources, technical expertise, and existing infrastructure limitations. International cooperation is crucial in bridging these gaps and fostering a more secure global digital landscape.
Successful cybersecurity initiatives require a holistic strategy, combining technological advancements with robust policy frameworks and capacity building. The effectiveness of these strategies is directly linked to the level of international support and collaboration, creating a synergistic relationship between national efforts and global partnerships.
Examples of Successful Cybersecurity Initiatives
Several vulnerable nations have demonstrated success in improving their cybersecurity resilience through targeted initiatives. These initiatives highlight the importance of tailored approaches that address specific national contexts and needs.
- Estonia’s National Cybersecurity Strategy: Estonia, a pioneer in e-governance, has invested heavily in cybersecurity infrastructure and education, developing a robust national cybersecurity strategy that includes proactive threat detection, incident response capabilities, and public awareness campaigns. This proactive approach has helped Estonia mitigate numerous cyberattacks effectively.
- Rwanda’s National ICT Policy: Rwanda’s National ICT Policy emphasizes cybersecurity as a key component of its national development plan. The policy focuses on building local capacity, promoting cybersecurity awareness, and establishing a robust legal framework to address cybercrime. This integrated approach helps to foster a more secure digital environment for citizens and businesses.
- India’s Cyber Swachhta Kendra: India’s Cyber Swachhta Kendra (CSC) is a national-level initiative focused on combating cyber threats through public awareness campaigns, malware detection, and removal services. The CSC proactively identifies and removes malicious websites and software, contributing significantly to improved online safety for Indian citizens.
International Collaborations Enhancing Cybersecurity in Developing Countries
Effective cybersecurity in developing nations necessitates a strong global collaborative effort. Several key international partnerships are dedicated to this crucial goal, providing technical assistance, capacity building, and shared best practices.
- The Global Cybersecurity Partnership (GCP): A multilateral initiative focused on promoting international cooperation on cybersecurity issues, including capacity building, information sharing, and joint exercises.
- The United Nations’ International Telecommunication Union (ITU): The ITU plays a significant role in fostering global cybersecurity cooperation, offering technical assistance, developing standards, and promoting best practices among member states.
- The Organization for Economic Co-operation and Development (OECD): The OECD works with member and partner countries to develop effective cybersecurity policies and strategies, sharing best practices and promoting international collaboration.
- The Cybersecurity and Infrastructure Security Agency (CISA) (US): CISA actively engages in international cybersecurity cooperation, providing technical assistance and capacity building to partner countries.
- The European Union Agency for Cybersecurity (ENISA): ENISA supports EU member states and other countries in strengthening their cybersecurity capabilities through various initiatives, including capacity building and the development of cybersecurity standards.
The Role of International Organizations in Providing Cybersecurity Assistance
International organizations play a pivotal role in supporting vulnerable nations in enhancing their cybersecurity capabilities. Their involvement extends beyond financial aid to encompass technical expertise, training, and policy guidance.
These organizations often provide crucial resources, including expert consultations, training programs for cybersecurity professionals, and the development of national cybersecurity strategies tailored to the specific needs and contexts of individual countries. They also facilitate knowledge sharing and the dissemination of best practices, fostering a collaborative environment for strengthening global cybersecurity.
Challenges in Implementing Effective Cybersecurity Strategies in Low-Resource Settings
Implementing effective cybersecurity strategies in low-resource settings presents unique challenges that require innovative solutions and sustained international support.
- Limited Resources: Financial constraints often hinder the acquisition of necessary technologies, skilled personnel, and comprehensive training programs.
- Lack of Skilled Professionals: A shortage of trained cybersecurity professionals limits the capacity to effectively manage and respond to cyber threats.
- Weak Infrastructure: Outdated or inadequate infrastructure can make it difficult to implement robust cybersecurity measures and effectively respond to incidents.
Final Wrap-Up
The vulnerability of nations to cyberattacks is a complex issue with far-reaching consequences. While technological advancements are vital, equally important is addressing the underlying socioeconomic and geopolitical factors that exacerbate this risk. International cooperation, knowledge sharing, and targeted investment in cybersecurity infrastructure and expertise are essential for building resilience and safeguarding vulnerable nations from the devastating impact of cyber threats.
The future of global cybersecurity hinges on a collective commitment to protecting the most vulnerable among us.
Question & Answer Hub
What types of data are most commonly targeted in cyberattacks against vulnerable countries?
Critically important data like government secrets, financial information, personal data of citizens, and intellectual property are prime targets.
How can individuals in vulnerable countries protect themselves from cyber threats?
Practicing good online hygiene – using strong passwords, being wary of phishing scams, and keeping software updated – is crucial. Awareness campaigns and education are vital for individual protection.
What role do insurance companies play in mitigating cyber risks for nations?
Cyber insurance can help nations offset the financial losses from attacks, but it’s not a complete solution. Prevention and mitigation remain paramount.
Are there any international laws specifically addressing state-sponsored cyberattacks?
While international law is evolving, there’s no single, universally accepted treaty specifically addressing state-sponsored cyberattacks. Existing international law frameworks are being adapted and interpreted to address this challenge.