
Log Formatting Best Practices for Improved Security
Log formatting best practices for improved security aren’t just about neatness; they’re the bedrock of a robust security posture. Poorly formatted logs are like a blurry security camera – you might see something amiss, but crucial details are lost, leaving you vulnerable. Imagine trying to solve a complex puzzle with missing pieces – that’s what poorly structured logs create.
This post dives deep into crafting secure, insightful logs that empower you to detect threats, respond swiftly, and ultimately, keep your systems safe.
We’ll explore the essential components of a secure log entry, from timestamps and severity levels to source identification and detailed event descriptions. We’ll also discuss the benefits of structured logging formats like JSON and XML, which provide a far more efficient and manageable way to handle vast amounts of log data compared to unstructured text. Think of it as upgrading from a disorganized shoebox of receipts to a meticulously organized accounting system – it’s a game-changer for security analysis.
Introduction to Log Formatting and Security: Log Formatting Best Practices For Improved Security
Proper log formatting is crucial for maintaining robust system security. Well-structured logs act as a detailed audit trail, allowing security teams to quickly identify, analyze, and respond to security incidents. Conversely, poorly formatted logs hinder effective security monitoring and incident response, increasing the risk of successful attacks and data breaches. The clarity and completeness of your logs directly impact your organization’s ability to protect itself.Poorly formatted logs significantly increase vulnerability to attacks by obscuring crucial information needed for threat detection and analysis.
Imagine trying to solve a complex puzzle with missing pieces – that’s essentially what happens when critical data points are absent or illegible in log files. This lack of clarity makes it difficult to pinpoint the source of an attack, trace its progression, and effectively mitigate its impact. The delay in identifying and responding to threats can lead to prolonged system compromise and significant financial losses.
Examples of Security Breaches Exacerbated by Inadequate Log Formatting, Log formatting best practices for improved security
Inadequate log formatting has been a contributing factor in numerous high-profile security breaches. For instance, a poorly designed logging system might fail to record the source IP address of a malicious actor, making it impossible to trace the attack back to its origin. Similarly, logs lacking timestamps can hinder the reconstruction of the attack timeline, making it difficult to determine the extent of the damage and implement effective countermeasures.
In other cases, insufficient logging of user activity might mask insider threats, allowing malicious insiders to compromise systems undetected. The lack of detailed information in logs often forces security teams to rely on guesswork and incomplete data, leading to inefficient incident response and prolonged system downtime. A hypothetical scenario might involve a system where only the user ID is logged, but not the specific actions taken by the user.
This lack of detail could easily mask a compromised account being used for malicious purposes. The absence of granular details within log entries significantly hampers effective security analysis and remediation efforts.
Key Elements of Secure Log Formatting
Effective log formatting is crucial for security monitoring and incident response. Poorly formatted logs make it incredibly difficult to identify threats, track down the source of problems, and ultimately secure your systems. By incorporating key elements into every log entry, you significantly improve your ability to analyze security events and react quickly and effectively.
Secure log entries need to provide sufficient context to understand the event. This means including not just what happened, but also who, when, where, and how. This information is essential for correlating events, identifying patterns, and building a comprehensive picture of your system’s security posture. Insufficient information leads to ambiguity and slows down investigation times, potentially leaving your systems vulnerable longer.
Essential Components of Secure Log Entries
To effectively analyze security events, each log entry should include specific, vital pieces of information. These elements enable accurate correlation and faster incident response.
| Timestamp | Severity Level | Source | Event Description |
|---|---|---|---|
| 2024-10-27T10:30:45Z | ERROR | Web Server – apache2 | Unauthorized access attempt from IP address 192.168.1.
100. User agent Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Trident/5.0). |
This example demonstrates a well-formatted log entry. The timestamp provides precise timing, the severity level indicates the urgency, the source identifies the system affected, and the description details the event. This level of detail is critical for efficient analysis.
Structured Logging Formats
Using structured logging formats like JSON or XML offers significant advantages over unstructured text logs. These formats provide a standardized, machine-readable way to represent log data.
Unstructured text logs often require complex parsing and regular expressions to extract relevant information. This is time-consuming, error-prone, and difficult to scale. In contrast, structured formats allow for easy parsing and querying using tools like Elasticsearch or Splunk, greatly enhancing the efficiency of log analysis. For example, a JSON log entry allows you to directly access specific fields, such as the timestamp or source IP address, without needing to parse the entire log line.
Consider a scenario where you need to find all failed login attempts from a specific IP address within a particular time frame. With unstructured logs, this would involve complex parsing and filtering. However, with a structured format like JSON, you can easily query the log data based on specific fields, significantly reducing the time and effort required. This enhanced efficiency is invaluable in security monitoring, where rapid response is crucial.
Data Minimization and Log Rotation Strategies
Effective log management is crucial for maintaining security and ensuring efficient system operations. A key aspect of this involves carefully balancing the need for comprehensive auditing with the practical limitations of storage space and processing power. This is where data minimization and log rotation strategies come into play. They allow us to keep essential security information while mitigating the risks associated with excessive log data.Data minimization, in the context of log management, means collecting and retaining only the necessary log data.
This principle helps reduce the attack surface by minimizing the amount of sensitive information stored, thus limiting the potential damage from a data breach. Less data also translates to faster searches, improved performance of log analysis tools, and lower storage costs. This approach is aligned with best practices for data privacy and regulatory compliance, such as GDPR and CCPA.
Log Rotation Schedules
Implementing a robust log rotation schedule is paramount. This schedule should consider several factors, including the type of logs (e.g., system, application, security), the volume of log data generated, and the legal or regulatory requirements for data retention. A sample schedule might involve daily rotation for high-volume logs like web server access logs, weekly rotation for less voluminous application logs, and monthly rotation for system logs that change less frequently.
The specific retention period for each log type should be determined based on the organization’s security policies and risk assessment. For example, security logs related to authentication attempts might be retained for a longer period (e.g., 90 days or more) compared to application logs related to routine operations (e.g., 30 days). This allows for thorough investigation of security incidents while avoiding unnecessary storage of less critical information.
Secure Archiving and Deletion of Old Log Files
Once logs reach the end of their retention period, secure archiving and deletion are essential. Archiving should involve copying the logs to a secure, offsite location, ideally using encryption during both transfer and storage. This ensures data availability for potential audits or investigations while minimizing the risk of data loss or unauthorized access. Methods like using a secure cloud storage service with robust access controls or dedicated archive servers with strong encryption are highly recommended.After archiving, the old log files should be securely deleted from the primary storage location.
Simply deleting files might not be sufficient; secure deletion methods that overwrite the data multiple times are necessary to prevent data recovery using specialized tools. Many operating systems offer secure delete utilities, or third-party tools can be used. Regularly reviewing and updating the log rotation and deletion procedures ensures that the organization maintains a secure and efficient log management system.
Furthermore, implementing a documented procedure ensures consistency and accountability in the process. The procedure should clearly Artikel the responsibilities, the steps involved, and the tools utilized, ensuring that all team members are aware of the process and can perform it consistently.
Handling Sensitive Information in Logs
Protecting sensitive data within log files is paramount for maintaining security and compliance. Failing to properly handle such information can lead to severe breaches, exposing your organization to significant legal and financial risks. This section will delve into the best practices for mitigating these risks.Log files often contain a wealth of information, much of which is not necessary for troubleshooting or security analysis.
Including unnecessary details increases the attack surface, making it easier for malicious actors to gain access to sensitive data. Careful consideration of what information is logged and how it’s handled is crucial.
Common Types of Sensitive Data Requiring Redaction
Sensitive data should be masked or redacted to prevent unauthorized access. Common examples include personally identifiable information (PII), financial details, intellectual property, and API keys. PII, in particular, requires stringent protection under various regulations like GDPR and CCPA. Examples of PII include names, addresses, email addresses, phone numbers, social security numbers, and credit card information. Financial details might encompass account numbers, transaction amounts, and payment processing data.
Intellectual property, including source code, algorithms, and trade secrets, must be shielded from disclosure. API keys, used for authentication and authorization, should never be directly logged. Failing to protect this data exposes your organization to significant risks.
Best Practices for Handling Personally Identifiable Information (PII)
Securely handling PII within log entries involves a multi-layered approach. Firstly, minimize the collection of PII. Only log the absolute minimum necessary for diagnostic purposes. Secondly, employ data masking techniques to replace sensitive elements with pseudonyms or randomized values. For instance, a credit card number could be masked to show only the last four digits, while the rest are replaced with Xs.
Thirdly, encrypt log files at rest and in transit to prevent unauthorized access. Fourthly, access to log files should be strictly controlled, limited only to authorized personnel with a legitimate need to access this data. Regular security audits and penetration testing can help identify vulnerabilities and ensure the effectiveness of implemented security measures. Finally, adhere to relevant data privacy regulations and industry best practices.
Anonymizing Sensitive Data While Preserving Diagnostic Value
The challenge lies in balancing security with the diagnostic value of logs. A well-designed anonymization strategy achieves this. One approach is tokenization, where sensitive data is replaced with unique, non-reversible tokens. A lookup table can be maintained separately, linking tokens to the original data, but this table must be highly secured. Another method involves data generalization, replacing specific values with broader categories.
For example, instead of logging a user’s exact age, you could log their age range (e.g., 25-34). Hashing is another technique, though it’s typically one-way and doesn’t allow for reconstruction of the original data. However, hashing can be used to detect if the same sensitive data appears multiple times in the logs, even if the actual data is masked.
The choice of anonymization technique depends on the specific data and the required level of security and diagnostic detail. Regular review and updates of the anonymization strategy are crucial to ensure its continued effectiveness.
Log Aggregation and Centralized Monitoring
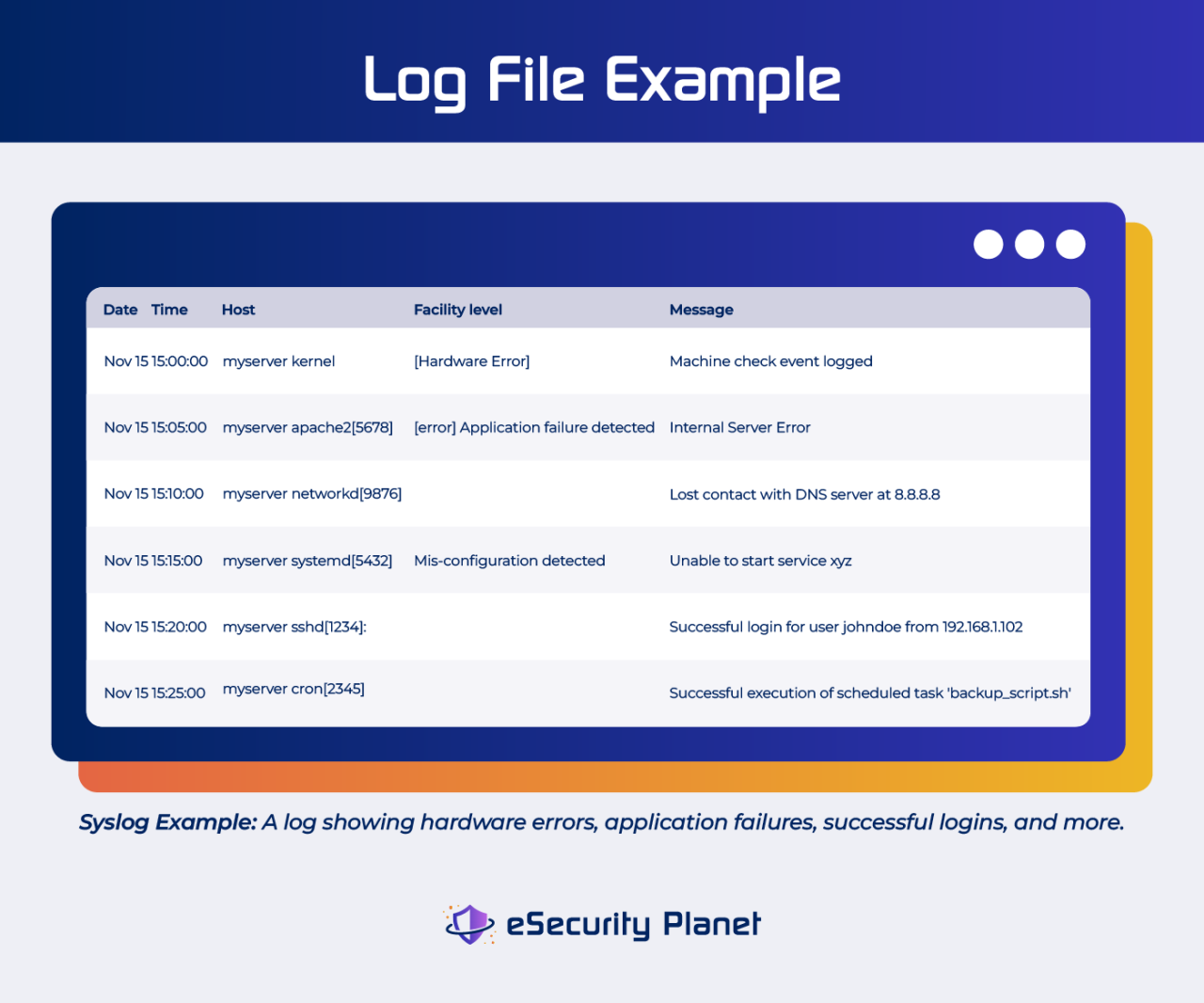
Centralized log management is no longer a luxury; it’s a necessity for effective security monitoring and incident response. By consolidating logs from various sources into a single, easily searchable repository, organizations gain significant advantages in their ability to detect threats, investigate security incidents, and maintain compliance. This approach offers a comprehensive view of security events across the entire infrastructure, making it far easier to identify patterns and anomalies that might otherwise go unnoticed.The benefits of a centralized approach are numerous and impactful.
It streamlines security monitoring, improves threat detection capabilities, simplifies compliance auditing, and allows for efficient resource allocation. The ability to correlate events across different systems provides a holistic understanding of security posture, leading to faster response times and more effective mitigation strategies. Ultimately, this translates to reduced risk and improved overall security.
Setting Up a Centralized Logging Infrastructure
Establishing a centralized logging infrastructure involves a structured approach. First, identify all sources of logs within your environment – servers, applications, network devices, and security tools. Next, choose a suitable log aggregation tool (discussed in the following section). Then, configure each log source to forward its logs to the central aggregation system, ensuring proper formatting and security during transmission (e.g., using TLS encryption).
The central system will then collect, index, and store the logs, making them readily accessible for analysis and reporting. Finally, establish a robust monitoring system to alert security personnel of critical events. This entire process requires careful planning and consideration of network bandwidth, storage capacity, and the security implications of centralizing sensitive data.
Log Aggregation Tools and Their Security Implications
Several tools are available for log aggregation, each with its own strengths and weaknesses regarding security. Elasticsearch, Logstash, and Kibana (ELK stack) are a popular open-source solution offering powerful search and visualization capabilities. However, proper security configuration is crucial, including access control, encryption, and regular updates to mitigate vulnerabilities. Splunk is a commercial solution providing robust features but requires a significant investment.
Its security features are generally strong, but the cost and potential vendor lock-in should be considered. Graylog is another open-source option that offers a user-friendly interface and scalability. Security considerations for Graylog include similar aspects to ELK, such as access control and encryption. The choice of tool depends on factors like budget, technical expertise, and specific security requirements.
Regardless of the tool selected, careful attention to security best practices during implementation and ongoing maintenance is paramount.
Log Analysis and Threat Detection

Properly formatted logs are the bedrock of effective threat detection and incident response. Without well-structured, consistent logging, identifying malicious activity becomes a tedious, error-prone process akin to searching for a needle in a haystack. Clear, concise logs, on the other hand, allow security analysts to quickly pinpoint suspicious events, understand the context of attacks, and respond efficiently. This ultimately minimizes downtime, reduces the impact of security breaches, and strengthens overall security posture.Well-structured logs dramatically improve the speed and accuracy of threat detection.
Instead of sifting through cryptic, inconsistent entries, analysts can leverage the power of log analysis tools to identify patterns and anomalies indicative of malicious behavior. This efficiency translates directly into faster incident response times, limiting the potential damage caused by cyberattacks.
Examples of Security Events Easily Identified Through Well-Structured Logs
A well-structured log allows for easy identification of a range of security events. For example, a failed login attempt from an unusual geographic location, logged with the timestamp, user ID, IP address, and location details, would immediately raise suspicion. Similarly, a large volume of file access requests originating from a single IP address within a short timeframe could signal a potential data exfiltration attempt.
Unauthorized access to sensitive files or databases, properly logged with user credentials and timestamps, is another readily identifiable threat. Finally, anomalies in system resource usage, such as unusually high CPU or memory consumption from a specific process, can be indicative of malware activity. The key is the consistent and detailed logging of all relevant information.
Common Log Analysis Techniques Used to Detect Malicious Activity
Effective log analysis relies on several techniques to uncover malicious activity.
Before listing the techniques, it’s important to note that the effectiveness of each method depends heavily on the quality and consistency of the log data. Incomplete or poorly formatted logs severely limit the insights that can be gained.
- Pattern Recognition: This involves identifying recurring patterns or sequences of events that deviate from normal behavior. For instance, a series of failed login attempts followed by a successful login from a different location might indicate a compromised account. Automated tools can be invaluable here, identifying patterns that would be difficult for a human analyst to spot manually.
- Anomaly Detection: This technique focuses on identifying unusual or unexpected events. This often involves using statistical methods or machine learning algorithms to establish a baseline of normal activity and then flagging anything that significantly deviates from that baseline. For example, an unusually high number of requests to a specific server endpoint compared to the average might signal a denial-of-service attack.
- Security Information and Event Management (SIEM): SIEM systems collect and analyze logs from various sources, providing a centralized view of security events. They use correlation rules to identify relationships between seemingly disparate events, revealing complex attack patterns that might otherwise go unnoticed. A SIEM can automate the detection and response to security threats, providing real-time alerts and facilitating faster incident response.
- Intrusion Detection Systems (IDS): IDSs monitor network traffic and system activity for malicious patterns. While they don’t directly analyze logs in the same way as SIEMs, their alerts often trigger detailed log analysis to investigate the specific nature of the detected threat. Properly formatted logs are essential for understanding the context of IDS alerts and for conducting thorough incident investigations.
Compliance and Auditing Considerations
Effective log management isn’t just about security; it’s also crucial for demonstrating compliance with various regulations and maintaining a robust audit trail. Failing to meet these requirements can lead to hefty fines, reputational damage, and legal repercussions. This section explores best practices for ensuring your log management policies align with relevant standards and support thorough auditing.Proper log management is vital for demonstrating compliance with regulations like GDPR and HIPAA, which mandate the secure processing and storage of personal data.
Maintaining detailed audit trails allows for the reconstruction of events, facilitating investigations and demonstrating adherence to regulatory requirements. A well-defined log management strategy helps organizations proactively address potential compliance issues and minimize risk.
GDPR and HIPAA Compliance
Meeting GDPR and HIPAA compliance necessitates meticulous attention to data privacy and security. For GDPR, this involves ensuring logs only retain personally identifiable information (PII) for as long as necessary and employing robust access controls to restrict access to sensitive log data. HIPAA compliance requires similar vigilance, focusing on the protection of Protected Health Information (PHI). This includes implementing strong encryption for logs containing PHI and adhering to strict audit trail requirements for all log management activities.
Regular audits and penetration testing should be conducted to identify and mitigate potential vulnerabilities. A key aspect of compliance is the ability to demonstrate a clear chain of custody for all log data, proving its integrity and authenticity.
Maintaining Comprehensive Audit Trails
Comprehensive audit trails are essential for demonstrating accountability and tracing any unauthorized access or modification of log data. These trails should meticulously record all log management activities, including user actions, system modifications, and security events. Information such as timestamps, user IDs, IP addresses, and the specific actions performed should be logged. The audit trail itself must be protected from tampering and unauthorized access, often through mechanisms such as digital signatures and tamper-evident logging.
Regular review of audit trails helps detect anomalies and potential security breaches promptly. Organizations should establish clear procedures for handling and retaining audit logs, ensuring they are readily available for internal and external audits.
Compliance Checklist
This checklist provides a framework for ensuring compliance with security and auditing standards related to log management. Regularly reviewing and updating this checklist is crucial to adapt to evolving regulatory requirements and security threats.
- Data Minimization: Are logs only retaining necessary data for the shortest required period?
- Access Control: Are access controls in place to restrict access to sensitive log data based on the principle of least privilege?
- Encryption: Is sensitive data within logs encrypted both in transit and at rest?
- Audit Trail Integrity: Is the audit trail protected from tampering and unauthorized access?
- Retention Policies: Are clear and documented retention policies in place, compliant with relevant regulations?
- Regular Audits: Are regular audits conducted to verify compliance with log management policies and regulations?
- Incident Response Plan: Is there a documented incident response plan that includes procedures for handling log data in the event of a security incident?
- Documentation: Is all log management activity thoroughly documented, including policies, procedures, and audit trail information?
- Training: Are personnel adequately trained on log management best practices and compliance requirements?
- Third-Party Assessments: Are regular third-party assessments conducted to evaluate the effectiveness of log management practices?
Common Log Formatting Pitfalls and Mitigation Strategies
Effective log formatting is crucial for maintaining robust security. Failing to adhere to best practices can significantly weaken your organization’s security posture, making it easier for attackers to exploit vulnerabilities and compromise sensitive data. This section highlights common mistakes and provides mitigation strategies to improve your log management.Inconsistent log formats across different systems represent a major challenge. This lack of standardization makes log aggregation, analysis, and threat detection significantly more difficult, hindering effective security monitoring.
Furthermore, inconsistent formats can lead to missed security events and delayed responses to incidents.
Inconsistent Timestamp Formats
Using inconsistent timestamp formats across your systems creates significant problems for log analysis. Imagine trying to correlate events across multiple servers with timestamps in different formats (e.g., YYYY-MM-DD HH:mm:ss vs. MM/DD/YYYY HH:mm:ss). This makes identifying attack timelines and reconstructing attack sequences extremely difficult. A consistent, standardized timestamp format (like ISO 8601) is essential for accurate log analysis and effective security monitoring.
Failure to do so introduces significant challenges in identifying patterns and correlating events over time.
Lack of Standardized Log Levels
Utilizing inconsistent log levels across your infrastructure significantly impacts the effectiveness of your security monitoring. If some systems use verbose logging while others use minimal logging, it becomes challenging to identify critical security events amidst a sea of less important information. Adopting a standardized logging level hierarchy (e.g., DEBUG, INFO, WARNING, ERROR, CRITICAL) ensures that crucial security-related events are easily identifiable and prioritized.
Without this consistency, important alerts can be easily overlooked, leading to delayed responses and increased risk.
Insufficient Contextual Information
Logs without sufficient contextual information severely limit their usefulness in security investigations. For example, a log entry indicating a failed login attempt is far more valuable if it includes the source IP address, username attempted, and the time of the attempt. Lack of such details hinders effective threat analysis and incident response. Including relevant contextual data, such as user IDs, session IDs, and transaction IDs, is essential for comprehensive security monitoring and efficient investigation of security incidents.
Without this information, pinpointing the source of an attack or tracing the actions of a malicious actor becomes significantly more difficult.
Missing or Incomplete Event Data
Incomplete or missing event data renders logs almost useless for security analysis. A log entry that only states “Error occurred” provides little insight into the nature of the problem and is of limited value in security investigations. Detailed logs that include error codes, stack traces, and relevant system information are essential for effective troubleshooting and security monitoring. This allows for more efficient identification of vulnerabilities and patterns of malicious activity.
The lack of detailed information can hinder security investigations and prevent effective incident response.
Overly Verbose or Unnecessary Log Data
While detailed logs are important, excessively verbose logging can lead to log management challenges. Excessive log data can overwhelm storage capacity, slow down systems, and hinder efficient analysis. It’s crucial to strike a balance between sufficient detail and manageable log volume. Strategies such as filtering and aggregation can be used to manage the volume of logs effectively while retaining the essential information.
Unnecessary data increases the overhead of storage, processing, and analysis, ultimately hindering effective security monitoring.
Inadequate Log Rotation and Retention Policies
Poor log rotation and retention policies can lead to log storage exhaustion and the loss of valuable security data. Without proper management, logs can consume excessive storage space, leading to performance degradation and potential data loss. Implementing robust log rotation and retention policies, in accordance with legal and regulatory requirements, ensures that critical security information is preserved for the appropriate duration while preventing storage overflow.
Failing to manage log retention appropriately can result in the loss of crucial evidence for security investigations and compliance audits.
End of Discussion
Mastering log formatting best practices is more than just a technical skill; it’s a strategic investment in your system’s security. By implementing the strategies Artikeld above – from data minimization and secure log rotation to centralized monitoring and effective analysis – you’ll significantly enhance your ability to detect and respond to threats. Remember, well-structured logs aren’t just for compliance; they’re your first line of defense against malicious actors.
So, take control of your logs, and take control of your security.
Essential Questionnaire
What’s the difference between structured and unstructured logging?
Unstructured logging uses plain text, making analysis difficult. Structured logging (JSON, XML) uses predefined formats, making data easier to search, filter, and analyze automatically.
How often should I rotate my logs?
The optimal rotation frequency depends on your storage capacity and regulatory requirements. A common approach is daily or weekly rotation, with older logs archived securely.
What sensitive data should I redact from logs?
Redact PII (Personally Identifiable Information) like names, addresses, credit card numbers, social security numbers, and any other data that could compromise individuals’ privacy.
How can I ensure compliance with regulations like GDPR?
Implement data minimization practices, maintain detailed audit trails of log management activities, and establish clear policies for data retention and deletion, aligning with GDPR and other relevant regulations.
