Losing Control of Your IoT A Cautionary Tale
Losing control of your iot a cautionary tale – Losing Control of Your IoT: A Cautionary Tale sets the stage for a chilling exploration of our increasingly connected world. We’re surrounded by smart devices – from smart speakers and thermostats to fitness trackers and even refrigerators – promising convenience and efficiency. But this interconnectedness comes at a price: a vastly expanded attack surface for hackers. This story delves into the real-world dangers of insecure IoT devices, the methods hackers use to exploit them, and the devastating consequences that can follow.
Get ready to rethink your relationship with your smart home, your wearable tech, and everything in between.
The exponential growth of the Internet of Things (IoT) has created a landscape ripe for exploitation. More devices mean more vulnerabilities, and the interconnected nature of these devices means a single breach can have far-reaching consequences. We’ll examine common vulnerabilities, from weak passwords to outdated firmware, and explore the various attack vectors hackers employ, from malware and phishing to brute-force attacks.
We’ll look at real-world examples of compromised devices and the resulting data breaches, financial losses, and even physical harm. But it’s not all doom and gloom. We’ll also discuss practical steps you can take to protect yourself and your devices, ensuring a safer and more secure smart future.
The Rise of IoT and Increased Vulnerability

The Internet of Things (IoT) has exploded in popularity, bringing convenience and automation to our homes and workplaces. From smart thermostats to connected security systems, the number of devices constantly communicating online is growing exponentially. This rapid expansion, however, comes with a significant downside: a dramatic increase in potential security vulnerabilities. The sheer volume of devices, coupled with often-lacking security protocols, creates a vast attack surface for malicious actors.The interconnected nature of IoT devices significantly amplifies the risk.
A single compromised device can serve as a gateway to an entire network. Imagine a hacker gaining access to a smart home hub; they could potentially control all connected devices, from lights and locks to appliances and security cameras. This cascading effect can lead to significant disruptions, data breaches, and even physical harm.
Examples of Real-World Consequences of Compromised IoT Devices
The consequences of losing control of IoT devices are far-reaching and increasingly severe. Several real-world examples highlight the gravity of this issue. For instance, the Mirai botnet, a notorious example of IoT device compromise, leveraged millions of vulnerable devices like internet-connected cameras and routers to launch massive DDoS attacks, crippling major websites and services. These attacks weren’t just inconvenient; they disrupted critical infrastructure and cost businesses significant amounts of money.
Furthermore, compromised smart home devices have been used to steal personal information, spy on residents, and even to remotely control physical devices, creating significant safety concerns. In some cases, compromised medical devices have even put patients at risk, illustrating the potential for severe, even life-threatening consequences. The increasing reliance on IoT in critical infrastructure, such as power grids and transportation systems, further emphasizes the need for robust security measures.
A large-scale attack on such systems could have catastrophic consequences.
Common Vulnerabilities in IoT Devices

The seemingly boundless convenience offered by the Internet of Things (IoT) comes at a price: increased vulnerability. While the benefits are undeniable, the security weaknesses inherent in many IoT devices present significant risks to both individuals and organizations. Understanding these vulnerabilities is crucial to mitigating the potential damage.
Weak or Default Passwords
Many IoT devices ship with default or easily guessable passwords. This practice leaves devices wide open to unauthorized access. The consequences can range from minor inconveniences, such as someone changing your smart thermostat settings, to far more serious breaches. Imagine a scenario where a hacker gains control of your smart home security system using a default password. They could remotely disable alarms, unlock doors, and even monitor your activities through connected cameras.
This weakness is particularly prevalent in less expensive devices where manufacturers prioritize cost reduction over robust security measures. The lack of a strong password enforcement mechanism during setup further exacerbates the problem.
Lack of Encryption and Secure Communication Protocols
Data transmitted between IoT devices and their associated applications often lacks adequate encryption. This means sensitive information, such as personal health data from a wearable fitness tracker or industrial control data from a smart factory sensor, can be intercepted and misused. For example, consider a smart baby monitor transmitting unencrypted video feeds. A malicious actor could easily access the feed, potentially compromising the child’s privacy and safety.
Similarly, industrial control systems lacking encryption could be vulnerable to sabotage or manipulation, leading to costly downtime or even physical damage. This vulnerability underscores the critical need for robust encryption and the use of secure protocols like TLS/SSL to protect data in transit.
Insecure Software and Firmware
Many IoT devices run on outdated or poorly secured software and firmware. This makes them susceptible to known vulnerabilities that could be exploited by attackers. These vulnerabilities often go unpatched due to a lack of regular software updates or difficulties in deploying updates to widely distributed devices. For instance, a smart lock with outdated firmware could be vulnerable to a known exploit allowing remote unlocking.
Similarly, a smart refrigerator with unpatched software could be compromised, potentially allowing access to your network and other connected devices. The consequences of insecure software and firmware can be severe, ranging from data breaches and device hijacking to denial-of-service attacks and complete system compromise. The lack of consistent update mechanisms and the difficulty in applying security patches across a large, diverse range of devices contribute significantly to this ongoing problem.
Smart home devices, with their often-simplified security features, are particularly vulnerable, whereas industrial sensors, while potentially containing more sophisticated technology, often lack the resources dedicated to ongoing security maintenance. Wearables, falling somewhere in between, often prioritize ease of use over robust security, leaving them susceptible to similar vulnerabilities.
Methods of Attack and Exploitation: Losing Control Of Your Iot A Cautionary Tale
Gaining unauthorized access to your IoT devices isn’t as difficult as you might think. Hackers employ a range of sophisticated and surprisingly simple methods to compromise these often-overlooked entry points into your network and personal data. Understanding these methods is crucial to bolstering your home and business security.
The methods used to exploit IoT vulnerabilities are diverse, ranging from highly technical exploits to deceptively simple social engineering tactics. These attacks leverage weaknesses in device security, software flaws, and even human behavior to gain control. Understanding the mechanisms behind these attacks allows for the implementation of effective preventative measures.
Malware Infections
Malware, specifically designed for IoT devices, can wreak havoc. These malicious programs often exploit known vulnerabilities in firmware or operating systems to gain access and control. Mirai, a notorious example, is a botnet malware that infects poorly secured IoT devices, turning them into zombie computers used for Distributed Denial-of-Service (DDoS) attacks. Mirai’s success stemmed from its ability to easily brute-force weak default passwords common in many IoT devices.
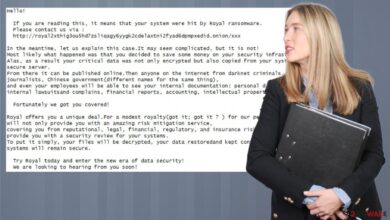
Once infected, devices are effectively hijacked, their resources consumed for malicious purposes, and potentially used to launch further attacks. Other examples include various strains of ransomware that encrypt data on compromised devices, demanding a ransom for its release. The impact ranges from minor inconveniences like disrupted device functionality to significant security breaches and financial losses.
Phishing Attacks
Phishing attacks target human vulnerabilities rather than technical weaknesses. Hackers craft convincing emails or messages appearing to be from legitimate sources, such as your internet service provider or a smart home device manufacturer. These messages often contain malicious links or attachments that, when clicked, install malware or grant access to your device. For example, an email claiming a firmware update for your smart camera could contain a malicious program that steals your login credentials or allows remote control of the device.
The effectiveness of phishing relies on social engineering, manipulating users into performing actions that compromise their security.
Brute-Force Attacks, Losing control of your iot a cautionary tale
Brute-force attacks are a more straightforward approach, relying on trial-and-error to guess passwords or access keys. This method becomes particularly effective when devices use weak or default passwords, which are sadly common in many IoT devices. Hackers use automated tools to try countless password combinations until they find the correct one, gaining access to the device. The impact of a successful brute-force attack can range from simple data theft to complete device takeover.
The sheer number of attempts can also lead to denial-of-service, rendering the device unusable.
Table of Attack Methods
| Attack Type | Target Device | Exploitation Technique | Example |
|---|---|---|---|
| Malware Infection | Smart Home Hub, Smart Camera | Exploiting software vulnerabilities, using default credentials | Mirai botnet, Ransomware |
| Phishing | Smart Thermostat, Router | Deceptive emails or messages containing malicious links or attachments | Fake firmware update email |
| Brute-Force Attack | Smart Lock, Network-Attached Storage (NAS) | Automated password guessing | Trying numerous password combinations until a match is found |
Consequences of Compromised IoT Devices
The seemingly innocuous nature of many IoT devices masks a serious threat: the potential for devastating consequences when they fall into the wrong hands. A compromised smart home, for instance, isn’t just about someone snooping on your conversations; it represents a gateway to significant personal, financial, and even physical risks. Understanding these potential ramifications is crucial for responsible IoT adoption.The consequences of a compromised IoT device can range from minor inconveniences to catastrophic events.
Data breaches are a primary concern, exposing sensitive personal information like addresses, financial details, and health records. This can lead to identity theft, financial fraud, and reputational damage. Beyond data breaches, physical harm is a very real possibility. Imagine a compromised smart lock granting access to your home, or a manipulated smart thermostat causing a dangerous temperature fluctuation.
Financial losses can also be significant, extending beyond direct theft to include expenses related to data recovery, legal fees, and the replacement of compromised devices.
Data Breaches and Identity Theft
A compromised IoT device often serves as a backdoor into a larger network, providing access to far more sensitive information than just the device itself. For example, a compromised smart baby monitor could provide access to your home network, allowing an attacker to steal data from your computer or other connected devices. This stolen information can then be used for identity theft, leading to fraudulent credit card applications, loan applications, or even the assumption of one’s identity for more sinister purposes.
The resulting financial and emotional distress can be substantial and long-lasting. The 2017 Equifax breach, while not directly related to IoT, highlights the devastating consequences of large-scale data breaches, affecting millions of individuals and costing the company billions.
Financial Loss and Extortion
The financial consequences of a compromised IoT device can be multifaceted. Direct financial loss can result from stolen funds, fraudulent transactions, and the cost of replacing compromised devices. Beyond this, indirect costs can include expenses incurred in recovering from a data breach, such as credit monitoring services, legal fees, and the time spent resolving the issue. In more extreme cases, extortion attempts are possible, with attackers demanding payment to prevent further damage or the release of sensitive information.
Consider a scenario where an attacker gains control of a smart home security system, threatening to release footage unless a ransom is paid.
Physical Harm and Safety Risks
Perhaps the most alarming consequence of compromised IoT devices is the potential for physical harm. A compromised smart lock can allow unauthorized entry into a home, leading to theft, vandalism, or even violence. Similarly, a compromised smart thermostat could be manipulated to create dangerously high or low temperatures, posing a risk to the occupants. Medical devices connected to the internet, if compromised, could malfunction with potentially life-threatening consequences.
Consider a scenario where an attacker remotely disables a life-sustaining medical device, illustrating the extreme severity of this risk. This potential for physical harm underscores the critical need for robust security measures in IoT devices, particularly those with direct safety implications.
Scenario: A Compromised Smart Home
Imagine a family whose smart home system, encompassing security cameras, smart locks, and smart appliances, is compromised. The attacker initially gains access through a vulnerable smart thermostat. This breach allows them to access the home network, enabling them to view security camera footage, unlock the smart locks remotely, and even control smart appliances, potentially causing a gas leak by manipulating the smart stove.
The consequences escalate rapidly: personal data is stolen, the family’s home is invaded, and potentially dangerous situations are created. The cascading effects highlight the interconnectedness of IoT devices and the potential for a single point of failure to cause widespread damage.
Visual Representation of Impact
Imagine a concentric circle diagram. The central circle represents the compromised IoT device (e.g., a smart speaker). The next circle outwards depicts the immediate impact – data breach, home invasion, financial loss. The third circle encompasses wider repercussions – emotional distress, reputational damage, legal battles. The outermost circle represents societal consequences – erosion of trust in technology, increased cybersecurity concerns, and the need for stricter regulations.
Each circle is visually distinct, showing the escalating impact, with the outermost circle significantly larger to emphasize the widespread effects. The colors used could be increasingly darker as the circles move outward, representing the increasing severity of the consequences.
Mitigation Strategies and Best Practices
Securing your IoT devices isn’t just about protecting your smart home; it’s about safeguarding your personal data and preventing your devices from becoming part of a larger botnet. The good news is that many proactive steps can significantly reduce your risk. By implementing strong security practices, you can dramatically improve the safety and privacy of your connected devices.
Effective IoT security relies on a multi-layered approach. It’s not enough to focus on just one aspect; a holistic strategy covering device selection, network security, and user practices is crucial for robust protection.
Password Management
Strong and unique passwords are the foundation of any secure system. For IoT devices, this is especially critical, as many come with default passwords that are easily guessed. Avoid using simple passwords like “password” or “1234.” Instead, use long, complex passwords that combine uppercase and lowercase letters, numbers, and symbols. Consider using a password manager to generate and securely store these complex passwords for each device.
Regularly change passwords, especially if you suspect a compromise. For devices that don’t support complex passwords, consider using a virtual private network (VPN) to add an extra layer of security.
Firmware Updates
Regularly updating the firmware on your IoT devices is paramount. Firmware updates often include security patches that address known vulnerabilities. Failing to update exposes your devices to potential attacks. Many devices will notify you of available updates, but it’s good practice to periodically check for them manually. Be aware that some older devices may not receive updates anymore, highlighting the importance of choosing devices with long-term support.
Network Segmentation
Network segmentation involves dividing your network into smaller, isolated segments. This limits the impact of a compromise. For instance, you could separate your IoT devices onto a separate network from your computers and other sensitive devices. This way, even if one IoT device is compromised, the attacker won’t have immediate access to your more critical systems. A router with guest network capabilities can easily facilitate this separation.
Choosing Reputable Manufacturers and Devices
Not all IoT devices are created equal. Some manufacturers prioritize security more than others. Before purchasing a device, research its security features and the manufacturer’s reputation. Look for devices that support strong authentication methods, regular firmware updates, and encryption. Read reviews and look for independent security assessments.
Choosing devices from established and reputable manufacturers with a proven track record of security updates is crucial. Avoid obscure brands with little to no online presence or support.
Implementing Multi-Factor Authentication
Multi-factor authentication (MFA) adds an extra layer of security by requiring more than just a password to access a device or service. While not all IoT devices support MFA, those that do offer significantly enhanced security. Common MFA methods include one-time codes sent via SMS or email, or authentication apps like Google Authenticator or Authy. If your IoT device offers MFA, enable it immediately.
For devices lacking built-in MFA, consider using a VPN or other security measures to compensate.
The Future of IoT Security

The interconnected world of the Internet of Things (IoT) is rapidly expanding, bringing unprecedented convenience and efficiency. However, this expansion also presents increasingly complex security challenges. As IoT devices become more sophisticated and integrated into critical infrastructure, the potential consequences of security breaches grow exponentially. Understanding and addressing these emerging threats is crucial for ensuring a secure and reliable future for the IoT ecosystem.The landscape of IoT security is constantly evolving, driven by advancements in technology and the ingenuity of cybercriminals.
New attack vectors emerge regularly, requiring proactive and adaptive security measures. Moreover, the sheer volume and diversity of IoT devices, ranging from smart home appliances to industrial control systems, make comprehensive security management a formidable task. This necessitates a multi-faceted approach, combining technological innovation with robust security policies and user education.
Emerging Threats and Challenges in IoT Security
The proliferation of IoT devices introduces several new challenges. One significant threat is the increasing sophistication of botnet attacks. These attacks, leveraging the combined processing power of numerous compromised devices, can be used to launch large-scale denial-of-service (DoS) attacks or to conduct cryptocurrency mining operations. Another growing concern is the vulnerability of IoT devices to supply chain attacks, where malicious code is introduced during the manufacturing or distribution process.
Furthermore, the lack of standardized security protocols across different IoT devices creates a fragmented and vulnerable ecosystem, making it difficult to implement comprehensive security measures. Finally, the rise of edge computing, while offering performance benefits, also introduces new security considerations, as data processing occurs closer to the source, potentially increasing the risk of unauthorized access. The recent SolarWinds attack, while not solely focused on IoT, highlighted the potential devastation of supply chain compromises, emphasizing the need for enhanced security measures throughout the entire lifecycle of IoT devices.
The Role of Artificial Intelligence and Machine Learning in Enhancing IoT Security
Artificial intelligence (AI) and machine learning (ML) are playing an increasingly crucial role in bolstering IoT security. AI-powered security systems can analyze vast amounts of data from various IoT devices to identify anomalies and potential threats in real-time. ML algorithms can be trained to detect patterns indicative of malicious activity, such as unusual network traffic or device behavior.
For example, an ML model could be trained to recognize the signature of a specific malware strain targeting a particular type of IoT device, enabling proactive mitigation. Furthermore, AI can automate security tasks such as vulnerability scanning and incident response, freeing up human resources to focus on more strategic security initiatives. The use of AI in threat detection and response promises a significant improvement in the overall security posture of IoT networks.
Predictions for the Future of IoT Security
The future of IoT security will likely involve a convergence of several key advancements. We can expect to see a wider adoption of blockchain technology to enhance data integrity and security. Blockchain’s decentralized and immutable nature can help secure sensitive data transmitted between IoT devices and the cloud. Furthermore, advancements in hardware-based security, such as secure elements and trusted execution environments (TEEs), will play a crucial role in protecting IoT devices from physical tampering and software attacks.
We can also anticipate the development of more sophisticated security protocols, such as post-quantum cryptography, to withstand the threat of quantum computing. Finally, greater collaboration between manufacturers, developers, and security researchers will be essential to address the systemic vulnerabilities inherent in the IoT ecosystem. For instance, the development of standardized security frameworks and best practices will significantly improve the overall security posture of the IoT.
The ongoing development and implementation of these advancements should help mitigate many of the current and future threats to IoT security.
Conclusion
The rise of the IoT has undeniably improved our lives in countless ways, but it has also introduced a new level of complexity and risk to our digital security. Losing control of even a single IoT device can trigger a chain reaction of events with potentially devastating consequences. This cautionary tale serves as a wake-up call, urging us to be more proactive in securing our connected devices.
By understanding the vulnerabilities, recognizing the threats, and implementing the right security measures, we can navigate the increasingly complex landscape of the IoT and enjoy its benefits without sacrificing our safety and security. Remember, a little vigilance can go a long way in protecting yourself from the ever-growing threats in the connected world.
FAQs
What is the biggest risk associated with insecure IoT devices?
The biggest risk is the potential for cascading failures. A compromised device can act as a gateway to your entire network, exposing other devices and sensitive data.
How often should I update the firmware on my IoT devices?
Firmware updates are crucial. Check for updates regularly, ideally as soon as they are released, as they often patch critical security vulnerabilities.
Can I use the same password for all my IoT devices?
Absolutely not! Using unique, strong passwords for each device is essential to prevent a single breach from compromising your entire system.
What should I do if I suspect my IoT device has been compromised?
Disconnect the device from your network immediately. Change all relevant passwords and consider contacting a cybersecurity professional.