Maintain Software Audit Readiness & Mitigate Security Risks with BigFix Inventory
Maintain software audit readiness and mitigate security risks with BigFix Inventory: It sounds like a mouthful, right? But the reality is, keeping your software assets secure and compliant doesn’t have to be a nightmare. BigFix Inventory is a powerful tool that can streamline the entire process, from identifying vulnerabilities to generating audit-ready reports. This post dives into how BigFix Inventory helps you stay ahead of potential security breaches and regulatory scrutiny, making your life (and your audits!) significantly easier.
We’ll explore how BigFix Inventory helps you build a comprehensive software asset database, pinpoint outdated software, and generate reports demonstrating license compliance. Beyond asset management, we’ll uncover how it integrates with vulnerability databases to identify and prioritize security risks, enabling proactive patching and significantly reducing your attack surface. Finally, we’ll show you how to leverage BigFix Inventory data to effortlessly create audit-ready reports, ensuring compliance with regulations like HIPAA and GDPR.
Get ready to simplify your security posture and reclaim your sanity!
BigFix Inventory for Software Asset Management
BigFix Inventory is a powerful tool for managing software assets within an organization. It goes beyond simple inventorying; it provides crucial insights into software usage, licensing compliance, and security vulnerabilities, enabling proactive management and risk mitigation. This allows IT teams to optimize software spending, improve security posture, and ensure regulatory compliance.
Core Functionalities of BigFix Inventory
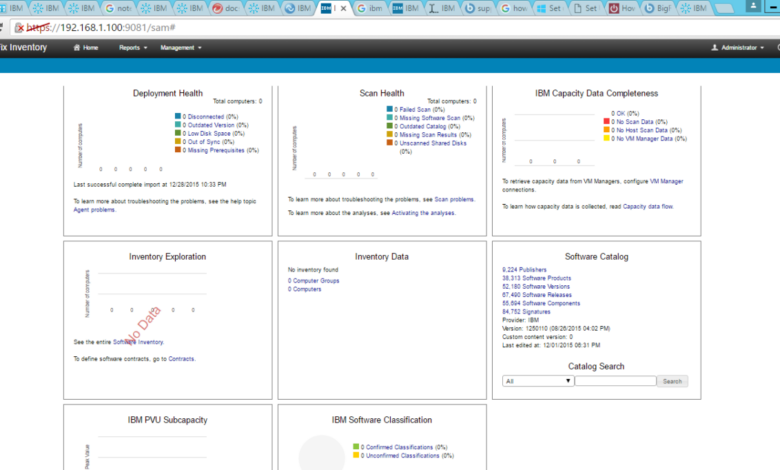
BigFix Inventory builds a comprehensive software asset database by automatically discovering and cataloging software installed across an organization’s endpoints. This includes operating systems, applications, and even drivers. It uses a client-server architecture, with agents deployed on each machine to collect and report inventory data. The central server then consolidates this information, providing a single pane of glass view of the entire software landscape.
This detailed inventory includes version numbers, installation dates, and other relevant metadata, facilitating accurate reporting and analysis. The system’s ability to handle large numbers of endpoints efficiently is a key strength, allowing it to scale to even the largest enterprise environments.
Identifying Outdated or Unsupported Software
BigFix Inventory facilitates the identification of outdated or unsupported software through several mechanisms. First, it maintains a database of software versions and their associated support lifecycles. By comparing the installed software versions against this database, BigFix Inventory can automatically flag outdated applications. Secondly, it can integrate with external vulnerability databases, allowing for identification of software with known security vulnerabilities.
This real-time identification of outdated software enables timely patching and mitigation of potential security risks, minimizing the organization’s vulnerability to exploits and malware. The system’s ability to automatically generate reports on this data makes prioritization and remediation efforts significantly more efficient.
Generating Software License Compliance Reports
BigFix Inventory streamlines the process of generating reports on software license compliance. By integrating with license management systems or by utilizing the inventory data itself, BigFix Inventory can compare the number of installed software licenses with the number of licenses actually purchased. This comparison allows for the identification of over-licensed or under-licensed software, optimizing software spending and avoiding potential legal issues.
The reports generated by BigFix Inventory can be customized to include various levels of detail, providing a clear and concise overview of the license compliance status across the organization. These reports are crucial for demonstrating compliance to auditors and for making informed decisions about future software purchases.
Feature Comparison of BigFix Inventory and Other SAM Tools
This table compares BigFix Inventory’s features against some other popular Software Asset Management (SAM) tools. Note that specific features and capabilities may vary depending on the version and configuration of each tool.
| Feature | BigFix Inventory | Other SAM Tool A (Example) | Other SAM Tool B (Example) |
|---|---|---|---|
| Automated Discovery | Yes, agent-based | Yes, agent-based | Yes, agentless and agent-based options |
| License Compliance Reporting | Yes, customizable reports | Yes, basic reports | Yes, advanced reporting and analytics |
| Vulnerability Management Integration | Yes | Yes, through third-party integrations | Integrated vulnerability scanning |
| Scalability | High, suitable for large enterprises | Medium | High |
Identifying Security Vulnerabilities with BigFix Inventory: Maintain Software Audit Readiness And Mitigate Security Risks With Bigfix Inventory
BigFix Inventory is more than just a software asset management tool; it’s a powerful asset for proactively identifying and mitigating security risks within your organization. By leveraging its comprehensive inventory capabilities and integrating with vulnerability databases, you can gain crucial insights into the security posture of your entire IT infrastructure. This allows for a more proactive approach to security, moving away from reactive patching and towards a predictive model.
Integrating BigFix Inventory with Vulnerability Databases
BigFix Inventory’s ability to identify vulnerabilities hinges on its integration with external vulnerability databases like the National Vulnerability Database (NVD). This integration allows BigFix Inventory to cross-reference the software it discovers on your managed devices against known vulnerabilities listed in the NVD. The process typically involves configuring BigFix Inventory to access the NVD’s data feeds (often through APIs) and then mapping this data to the software identified within your inventory.
This mapping involves matching software names, versions, and other identifying attributes to find potential vulnerabilities. Successful integration provides a real-time view of your organization’s exposure to known security threats.
Creating a Prioritized List of Vulnerabilities
Once BigFix Inventory is integrated with a vulnerability database, you can generate reports that highlight software with known vulnerabilities. These reports often allow for filtering and sorting based on criteria like severity (critical, high, medium, low), vulnerability age, and affected software. For example, you could prioritize vulnerabilities based on the Common Vulnerability Scoring System (CVSS) score, focusing first on those with the highest scores representing the most critical risks.
This prioritization helps focus remediation efforts on the most impactful vulnerabilities. The creation of this list is crucial for efficient resource allocation and risk mitigation.
Remediation Workflow Using BigFix Inventory Data
The vulnerability data from BigFix Inventory forms the basis for a streamlined remediation workflow. Once a prioritized list of vulnerabilities is generated, you can use BigFix Inventory’s reporting features to identify the specific devices affected by each vulnerability. This information can then be used to deploy patches or other remediation actions through your existing patch management system, ensuring that updates are targeted and efficient.
The entire process, from vulnerability identification to remediation, can be tracked and monitored within BigFix Inventory, providing a complete audit trail and improving overall security posture. For instance, a workflow might involve generating a report showing all devices with a specific high-severity vulnerability, then using this data to target a patch deployment via BigFix, followed by verification of successful patch application within BigFix Inventory.
Maintaining Audit Readiness using BigFix Inventory Data
BigFix Inventory is more than just a software asset management tool; it’s a powerful resource for maintaining audit readiness and demonstrating compliance. Its comprehensive data collection and reporting capabilities streamline the audit process, minimizing disruption and maximizing efficiency. By leveraging BigFix Inventory effectively, organizations can confidently demonstrate adherence to regulatory requirements and maintain a strong security posture.BigFix Inventory data provides the evidence needed to demonstrate compliance with various regulations.
Demonstrating Compliance with Regulations using BigFix Inventory Data, Maintain software audit readiness and mitigate security risks with bigfix inventory
BigFix Inventory’s ability to track software installations, configurations, and updates across your entire IT infrastructure is crucial for demonstrating compliance. For example, HIPAA requires strict controls over protected health information (PHI). BigFix Inventory can track which systems have access to PHI, ensuring only authorized devices and software are used. Similarly, GDPR demands detailed records of personal data processing. BigFix Inventory can help track software applications that process personal data, enabling organizations to demonstrate compliance with data subject access requests and other GDPR requirements.
The granular detail provided by BigFix Inventory allows for precise identification of systems and software involved in sensitive data handling, simplifying the process of demonstrating compliance during audits. This detailed tracking helps prove adherence to policies and procedures, providing concrete evidence for auditors.
Creating Audit-Ready Reports using BigFix Inventory Data
BigFix Inventory offers robust reporting capabilities to generate audit-ready documentation. Pre-built reports provide summaries of software assets, licenses, and vulnerabilities, while custom reports can be created to address specific audit requirements. These reports can include details such as software version numbers, installation dates, and associated users, providing a complete audit trail. For example, a report showing all devices with outdated antivirus software can quickly highlight a critical security risk and the steps taken to remediate it.
Another report might detail the software licenses held, demonstrating compliance with vendor agreements. The key is to tailor reports to address the specific requirements of the audit and to ensure they are clear, concise, and easily understandable.
Organizing and Archiving BigFix Inventory Data for Audit Purposes
Maintaining organized and readily accessible data is paramount for successful audits. BigFix Inventory allows for the scheduling of regular data backups and the archiving of historical data. This ensures that data is preserved for future audits, even if systems are upgraded or replaced. A well-defined data retention policy, aligning with regulatory requirements and internal guidelines, should be implemented.
This policy should specify which data needs to be retained, for how long, and how it will be archived. Regularly reviewing and updating this policy is crucial to maintain compliance. Consider using a structured file naming convention for archived data to facilitate easy retrieval and organization.
Tracking Changes to Software Assets over Time using BigFix Inventory
BigFix Inventory provides a comprehensive audit trail of changes made to software assets. This includes software installations, updates, uninstalls, and configuration changes. This historical data is invaluable for identifying the root cause of security incidents and demonstrating compliance over time. For instance, if a vulnerability is discovered in a specific software version, BigFix Inventory can identify all devices with that version and track when it was installed, providing crucial information for remediation.
This detailed history is crucial for demonstrating proactive security management and for complying with regulatory requirements that mandate the tracking of system changes. This historical data also allows for trend analysis, enabling proactive identification of potential risks before they escalate into major incidents.
Mitigating Security Risks through Proactive Patching with BigFix
BigFix offers a powerful solution for proactively addressing security vulnerabilities, moving beyond reactive patching and significantly reducing the attack surface of your IT infrastructure. By automating the patching process, BigFix enables organizations to stay ahead of threats and minimize the risk of exploitation. This proactive approach is crucial in today’s rapidly evolving threat landscape.BigFix automates the patching process by leveraging its robust agent technology to identify vulnerable systems, download and install necessary patches, and verify successful application.
The system integrates with various patch repositories, allowing for centralized management and streamlined deployment. This automation eliminates manual intervention, saving time and resources while ensuring consistent patching across the entire environment. Customizable remediation tasks can be built, allowing for fine-grained control and targeted deployment of patches based on operating system, application, or other criteria.
Benefits of Proactive Patching with BigFix
Proactive patching with BigFix offers significant advantages over reactive methods. Reactive patching, responding only after a vulnerability is exploited, leaves systems vulnerable for extended periods, increasing the risk of successful attacks. Proactive patching, on the other hand, minimizes this window of vulnerability. The automated nature of BigFix ensures consistent and timely patching across all managed devices, reducing the likelihood of successful attacks.
Furthermore, the detailed reporting and auditing capabilities of BigFix provide valuable insights into the patching status of your environment, facilitating better security posture management.
Comparison of Patching Strategies
Several patching strategies can be implemented with BigFix, each with varying levels of effectiveness. A “staged rollout” strategy, for example, involves deploying patches to a small test group first to verify functionality before wider deployment. This minimizes the risk of unforeseen issues affecting the entire environment. A “critical-first” strategy prioritizes patching the most critical vulnerabilities, focusing resources on the most immediate threats.
BigFix facilitates both these strategies, providing the flexibility to tailor the patching process to specific needs and risk tolerance. Finally, a “scheduled patching” strategy ensures consistent patching at predetermined intervals, maintaining a consistently secure environment.
BigFix Patching Process Flowchart
Imagine a flowchart depicting the process. It would begin with “Vulnerability Identification” using BigFix Inventory’s scanning capabilities. This would lead to “Patch Selection,” where BigFix identifies and selects appropriate patches from the configured repositories. Next, “Patch Deployment” shows BigFix deploying the patches to the identified vulnerable systems. This is followed by “Verification,” where BigFix confirms successful patch installation and reports the results.
Finally, “Reporting and Auditing” displays BigFix providing comprehensive reports on the patching process, enabling continuous monitoring and improvement. The entire process is automated and managed within the BigFix console.
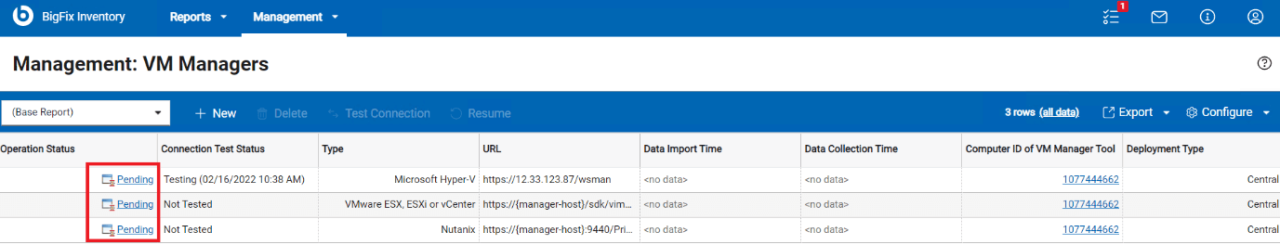
Integrating BigFix Inventory with Other Security Tools
BigFix Inventory’s power extends far beyond its core functionality of software asset management. By integrating it with other security tools, organizations can significantly enhance their overall security posture, achieving a more holistic and proactive approach to threat detection and response. This integration allows for a powerful synergy, leveraging BigFix Inventory’s detailed asset inventory and vulnerability data to inform and improve the efficiency of other security systems.Integrating BigFix Inventory data with other security tools offers numerous advantages.
It provides a single pane of glass view across your IT landscape, enabling more informed decision-making and faster response times to security incidents. The rich context provided by BigFix Inventory, such as software versions, operating systems, and hardware configurations, greatly enhances the accuracy and effectiveness of other security tools. This leads to reduced false positives, improved incident response times, and a more efficient use of security resources.
Methods for Integrating BigFix Inventory Data into SIEM Systems
BigFix Inventory offers several methods for integration with SIEM (Security Information and Event Management) systems. A common approach involves using BigFix Inventory’s API to extract relevant data, such as discovered vulnerabilities, missing patches, and software license information. This data can then be fed into the SIEM system through various mechanisms, including custom scripts, dedicated connectors, or third-party integration tools.
The specific method will depend on the capabilities of both BigFix Inventory and the target SIEM system. For example, some SIEMs may support direct integration via APIs, while others might require data transformation and formatting before ingestion. Successfully integrating this data allows the SIEM to correlate security events with asset information, providing valuable context for threat analysis and incident response.
This enriched context dramatically reduces investigation time and improves the accuracy of security alerts.
Examples of BigFix Inventory Data Enhancing Security Incident Response
Imagine a scenario where a SIEM system detects a malware infection on a specific endpoint. With BigFix Inventory integrated, the SIEM can automatically retrieve detailed information about the affected machine, including its operating system, installed software, and patch status. This detailed information immediately provides crucial context, allowing security analysts to quickly assess the risk, prioritize the response, and potentially identify other vulnerable systems.
For example, if the infection is linked to a known vulnerability in a specific software application, BigFix Inventory can identify all other systems with that same application and patch level, enabling proactive mitigation efforts to prevent further compromise. Similarly, if a zero-day exploit is discovered, BigFix Inventory’s detailed hardware and software inventory can help prioritize patching efforts based on the criticality of the affected systems.
Potential Integrations and Their Advantages and Disadvantages
The value of integrating BigFix Inventory extends beyond SIEMs. Integrating with various security tools enhances the effectiveness of your security operations.
- Integration with SIEM (e.g., Splunk, QRadar):
- Advantages: Centralized security monitoring, improved threat detection and correlation, faster incident response.
- Disadvantages: Requires configuration and potential data transformation; performance impact if not properly managed.
- Integration with SOAR (Security Orchestration, Automation, and Response) platforms (e.g., Palo Alto Networks Cortex XSOAR):
- Advantages: Automated incident response, reduced manual effort, improved efficiency.
- Disadvantages: Requires integration scripting and potential for increased complexity.
- Integration with Vulnerability Scanners (e.g., Nessus, OpenVAS):
- Advantages: Correlation of vulnerability scan results with asset information, prioritized remediation efforts.
- Disadvantages: Requires careful mapping of data between systems.
- Integration with Patch Management Systems (e.g., BigFix):
- Advantages: Streamlined patch deployment, reduced vulnerability exposure.
- Disadvantages: Overlapping functionalities may require careful coordination.
Visualizing Software Asset and Security Data with BigFix
BigFix Inventory’s power extends beyond simple data collection; it offers robust visualization tools to transform raw data into actionable insights. By creating charts and graphs, you can effectively communicate the state of your software assets and security posture to both technical and non-technical stakeholders. This visual representation simplifies complex information, facilitating quicker decision-making and improved resource allocation.Effective visualization is key to understanding the scope of security risks and compliance status.
Instead of wading through endless spreadsheets, stakeholders can quickly grasp the critical information, such as the number of vulnerable systems, the severity of identified risks, and the overall compliance posture of the organization. This allows for faster response times to critical security issues and more efficient resource allocation for remediation efforts.
Creating Custom Dashboards in BigFix Inventory
BigFix Inventory provides a flexible dashboarding system allowing you to tailor visualizations to your specific needs. You can select from a variety of chart types – bar charts, pie charts, line graphs – to represent different aspects of your software asset and security data. The process typically involves selecting the relevant data points (e.g., number of vulnerable applications, number of outdated operating systems, compliance status against specific regulations), choosing the appropriate chart type, and customizing the chart’s appearance (labels, colors, etc.) to enhance readability and impact.
These dashboards can then be shared with relevant stakeholders, providing a centralized view of the organization’s security and asset management status.
Examples of Effective Visualizations
Visualizations should be clear, concise, and easily understandable. Here are a few examples:
| Visualization Type | Data Represented | Benefits | Example |
|---|---|---|---|
| Bar Chart | Number of systems with critical vulnerabilities categorized by severity level (critical, high, medium, low). | Quickly identifies the most pressing vulnerabilities requiring immediate attention. | A bar chart showing four bars representing critical, high, medium, and low vulnerability counts. The length of each bar directly correlates to the number of affected systems. The chart clearly highlights that, for example, 15 systems have critical vulnerabilities, while only 5 have low-level vulnerabilities. |
| Pie Chart | Percentage of software licenses in use compared to total licenses purchased. | Illustrates license utilization and potential for cost savings through license reclamation. | A pie chart showing a breakdown of license usage. For example, 70% of licenses are actively used, 20% are unused, and 10% are expired. This quickly shows areas for potential license optimization. |
| Line Graph | Number of vulnerabilities discovered over time. | Tracks the effectiveness of vulnerability management processes and identifies trends. | A line graph showing the number of vulnerabilities discovered each month over the past year. This visual representation would reveal whether vulnerability discovery rates are increasing or decreasing, allowing for an assessment of the effectiveness of current security measures. A downward trend would indicate a successful vulnerability management strategy, while an upward trend might signal the need for improved processes. |
| Heatmap | Vulnerability distribution across different departments or geographical locations. | Pinpoints areas with higher concentrations of vulnerabilities, enabling targeted remediation efforts. | A heatmap showing the concentration of vulnerabilities across different departments (e.g., Marketing, Sales, IT). Darker colors indicate a higher density of vulnerabilities, allowing quick identification of departments requiring immediate attention. This visualization could be further broken down by geographical location if relevant. |
Final Conclusion
So, there you have it – a deep dive into leveraging BigFix Inventory for a more secure and audit-ready environment. By combining BigFix Inventory’s powerful asset management capabilities with proactive vulnerability patching, you’re not just meeting compliance requirements; you’re building a robust security posture that proactively mitigates risks. Remember, proactive security is more than just a best practice; it’s a necessity in today’s threat landscape.
Take control of your software assets, and sleep soundly knowing you’re prepared for any audit.
Common Queries
What if I don’t have a dedicated security team? Can I still use BigFix Inventory effectively?
Absolutely! BigFix Inventory is designed to be user-friendly, even for those without extensive security expertise. Its intuitive interface and automated features make it accessible to a wide range of users.
How much does BigFix Inventory cost?
Pricing varies depending on your needs and the scale of your deployment. It’s best to contact IBM directly for a customized quote.
Can BigFix Inventory integrate with my existing ticketing system?
BigFix Inventory offers various integration options, and compatibility with your existing ticketing system should be investigated during the implementation planning phase. Check IBM’s documentation for supported integrations.
What kind of reports can BigFix Inventory generate?
BigFix Inventory can generate a wide variety of reports, including software license compliance reports, vulnerability reports, and custom reports tailored to your specific needs. The possibilities are extensive.





