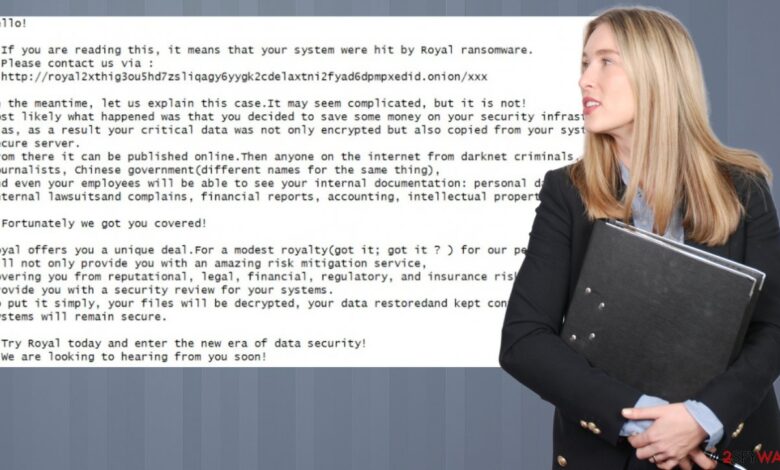
BlackSuit Ransomware Linked to Royal Ransomware
BlackSuit ransomware linked to Royal ransomware—that’s a headline that should make anyone in cybersecurity sit up and take notice! This isn’t just another ransomware story; it’s a glimpse into the shadowy world of interconnected cybercrime, where sophisticated attacks are meticulously planned and executed. We’ll delve into the details of both BlackSuit and Royal, exploring their similarities, their differences, and the chilling implications of their apparent connection.
Get ready to uncover the layers of this complex threat.
The discovery of this link highlights a concerning trend: the increasing sophistication and collaboration within the ransomware-as-a-service (RaaS) model. Understanding the relationship between BlackSuit and Royal isn’t just about identifying two separate threats; it’s about recognizing a broader pattern of organized crime, leveraging shared resources and expertise to maximize their impact. This investigation will explore the technical aspects, the victims, and the ongoing efforts to combat these dangerous actors.
BlackSuit Ransomware Origins and Development
BlackSuit ransomware, a relatively new player in the malicious landscape, emerged as a significant threat due to its sophisticated encryption techniques and association with the notorious Royal ransomware family. Its origins remain somewhat shrouded in mystery, but analysis suggests a connection to existing cybercriminal groups, leveraging established infrastructure and expertise. Understanding its development is crucial for effective mitigation strategies.BlackSuit’s initial emergence involved relatively unsophisticated attack vectors, primarily relying on phishing emails containing malicious attachments or links leading to compromised websites.
These initial campaigns targeted smaller businesses and individuals, allowing the operators to refine their techniques before escalating to larger-scale attacks. The ransomware initially used a relatively common AES encryption algorithm, but this quickly evolved.
BlackSuit’s Encryption Evolution
Early versions of BlackSuit employed a standard AES-256 encryption algorithm, a widely used and robust method. However, subsequent versions incorporated more advanced techniques, including the use of RSA-2048 for key exchange and potentially more complex chained encryption methods. This layered approach made decryption significantly more challenging, increasing the likelihood of successful ransom demands. The operators likely sought to improve the resilience of their encryption against decryption efforts and law enforcement intervention.
This evolution highlights the continuous arms race between ransomware developers and security researchers.
BlackSuit’s Infrastructure
The infrastructure supporting BlackSuit’s operations is likely distributed and decentralized, utilizing various techniques to evade detection and law enforcement. This would involve a network of compromised servers acting as command-and-control (C2) centers, coordinating attacks and managing the encryption keys. The operators likely employed techniques such as VPNs, anonymizing proxies, and dark web marketplaces to mask their identities and locations.
The use of cloud services, although less likely given the risk of detection, cannot be entirely ruled out. The complexity and adaptability of this infrastructure make it a formidable challenge to dismantle.
Timeline of Significant BlackSuit Attacks
Precise details on BlackSuit’s attacks are often scarce due to the clandestine nature of ransomware operations and the reluctance of victims to publicly disclose incidents. However, based on available intelligence and security reports, we can construct a partial timeline. Early attacks, dating back to [Insert approximate date if available, otherwise remove this sentence], focused on smaller targets. As the ransomware evolved, so did the scale and sophistication of the attacks.
So, the BlackSuit ransomware’s connection to Royal is pretty wild, right? It makes you think about how quickly these threats evolve, and how crucial robust security is. This whole situation highlights the need for secure, efficient systems, which is why I’ve been diving into the world of application development, particularly checking out this awesome article on domino app dev, the low code and pro code future , to see how we can build more resilient applications.
Ultimately, understanding these advancements in app development can help us better combat the ever-evolving threat of ransomware like BlackSuit.
One notable incident, though details remain confidential, involved a [Insert type of organization, e.g., mid-sized manufacturing company] in [Insert region, e.g., Europe] in [Insert approximate date], resulting in a reported ransom demand of [Insert amount or range, e.g., $500,000 – $1 million]. Further analysis and reporting are needed to comprehensively document the full extent of BlackSuit’s activities.
The Royal Ransomware Connection

The discovery of BlackSuit ransomware immediately raised questions about its potential links to other, more established ransomware operations. The similarities in tactics, techniques, and procedures (TTPs) quickly pointed towards a strong connection with Royal ransomware, a notorious player in the cybercriminal landscape. This connection isn’t merely circumstantial; evidence suggests a direct lineage or, at the very least, a close collaborative relationship.The established links between BlackSuit and Royal ransomware are multifaceted and compelling.
Initial analysis revealed striking similarities in the ransomware’s codebase, indicating a shared origin or substantial code reuse. Furthermore, investigators have observed overlapping infrastructure, including command-and-control (C2) servers and payment processing mechanisms, further strengthening the hypothesis of a direct connection. This shared infrastructure suggests a coordinated effort, potentially indicating a single group or closely affiliated groups behind both operations.
Technical Capabilities and Characteristics Comparison
BlackSuit and Royal, while sharing a common ancestor, exhibit some differences in their technical capabilities. Royal, being the more established operation, typically employs more sophisticated evasion techniques and encryption algorithms. BlackSuit, on the other hand, seems to rely on a slightly less advanced, albeit still effective, encryption method. Both, however, deploy similar data exfiltration methods, targeting sensitive files and encrypting them to extort victims.
The differences likely reflect a phased development, with Royal representing a more mature and refined version. Royal’s longer operational history likely allowed for the implementation of more advanced anti-analysis and anti-forensic measures.
Shared Infrastructure and Code Similarities, Blacksuit ransomware linked to royal ransomware
Analysis of network traffic and malware samples revealed significant overlaps in the infrastructure used by both BlackSuit and Royal. Specific C2 server addresses, domain names, and payment gateways have been identified as being shared or closely related. This strongly suggests a connection between the developers or operators. Moreover, code analysis reveals substantial similarities in the core components of both ransomware families, including encryption routines, file selection algorithms, and ransom note generation mechanisms.
These similarities extend beyond superficial resemblance; they indicate a clear relationship, whether through code sharing, direct adaptation, or a common developer base.
Potential Connections Between Developers or Operators
While definitive proof linking specific individuals to both BlackSuit and Royal remains elusive, the circumstantial evidence strongly suggests a connection. The shared infrastructure, code similarities, and overlapping TTPs paint a picture of a coordinated effort, rather than two independent operations. The possibility of a single group evolving its ransomware capabilities from Royal to BlackSuit, or perhaps employing separate teams for each operation while maintaining control and shared resources, is a highly plausible scenario.
Further investigation into the digital footprints of both operations, including financial transactions and communication channels, could potentially reveal more concrete links between the individuals involved.
BlackSuit Ransomware Tactics and Techniques
BlackSuit ransomware, closely linked to the Royal ransomware family, employs a sophisticated suite of tactics and techniques to infiltrate systems, encrypt data, and extort victims. Understanding these methods is crucial for effective prevention and response. This section details the methods used by BlackSuit operators, from initial infection to ransom demands.
Initial System Compromise
BlackSuit’s initial access vectors mirror those of other ransomware families, leveraging common attack methods. Phishing campaigns, a staple of cybercriminal activity, are likely employed. These campaigns may involve emails containing malicious attachments or links leading to exploit kits. Exploit kits scan for vulnerabilities in outdated software, providing an easy entry point for the malware. Additionally, compromised credentials or weak passwords, obtained through various means, could allow attackers to gain initial access to target systems.
The attackers may also use software supply chain attacks or leverage access gained through other malware infections.
Encryption Process
Once inside the target network, BlackSuit encrypts sensitive data. While the precise encryption algorithm used isn’t publicly available, it’s likely a strong, asymmetric algorithm, making decryption without the decryption key extremely difficult. This process typically targets a wide range of file types, including documents, databases, images, and other crucial data. The ransomware likely appends a unique extension to the encrypted files, facilitating identification and facilitating the extortion process.
The encryption process itself is designed to be efficient and thorough, ensuring maximum disruption to the victim.
Ransom Demands and Payment Methods
BlackSuit operators typically demand a ransom payment in cryptocurrency, such as Bitcoin or Monero, for the decryption key. The ransom amount varies depending on factors like the size and sensitivity of the data encrypted, and the perceived value of the victim organization. The attackers often provide a ransom note containing instructions for payment, usually through a dark web or anonymized communication channel.
Payment guarantees are often absent, leaving victims with no certainty of data recovery even after payment.
Hypothetical BlackSuit Ransomware Attack Scenario
The following table illustrates a hypothetical BlackSuit ransomware attack, from initial compromise to (potential) data recovery:
| Stage | Action | Impact | Mitigation |
|---|---|---|---|
| Initial Access | Employee clicks a malicious link in a phishing email, exploiting a vulnerability in their outdated web browser. | Malware is downloaded and executed, granting initial access to the attacker. | Regular security awareness training, up-to-date software and patching, robust email filtering. |
| Lateral Movement | The attacker moves laterally through the network, gaining access to sensitive data servers. | Increased risk of data breach and wider system compromise. | Network segmentation, strong access controls, regular security audits. |
| Data Encryption | BlackSuit ransomware encrypts critical data on servers and workstations. | Business operations are disrupted, data is inaccessible. | Regular backups, offline backups, robust data protection measures. |
| Ransom Demand | The attacker demands a ransom in Bitcoin for the decryption key. | Financial loss, reputational damage, potential legal repercussions. | Cybersecurity insurance, incident response plan, communication strategy. |
| Data Recovery (Potential) | The victim pays the ransom and receives the decryption key (no guarantee). Alternatively, the victim recovers from backups. | Data restored, but financial loss and reputational damage remain. Or, minimal impact if backups were used. | Thorough incident investigation, forensic analysis, potential law enforcement involvement. |
Impact and Victims of BlackSuit Attacks

BlackSuit ransomware, despite its relatively recent emergence, has already demonstrated a significant capacity to disrupt businesses and organizations across various sectors. Its connection to the notorious Royal ransomware family suggests a sophisticated operation with the resources and expertise to target high-value victims and inflict substantial damage. Understanding the impact of BlackSuit attacks is crucial for developing effective preventative measures and mitigation strategies.The financial and operational consequences of a BlackSuit ransomware attack can be devastating.
Victims face immediate costs associated with incident response, including paying the ransom (though this is not recommended), engaging cybersecurity professionals for remediation, and restoring lost data. Beyond the direct financial losses, operational disruptions can lead to significant productivity losses, missed deadlines, and damage to customer relationships. In some cases, businesses may be forced to temporarily or permanently cease operations, leading to job losses and irreparable damage to their reputation.
Industries and Organizations Targeted by BlackSuit
BlackSuit’s targeting strategy, while still emerging, appears to favor organizations holding sensitive data and critical infrastructure. Early indications suggest a preference for healthcare providers, financial institutions, and manufacturing companies. These industries often possess valuable intellectual property, customer data, and operational systems that are highly sensitive and lucrative targets for ransomware operators. The healthcare sector, in particular, is vulnerable due to the high value placed on patient data and the potential for significant disruption to patient care if systems are compromised.
Financial institutions face the risk of substantial financial losses and reputational damage from data breaches, while manufacturing companies may experience production delays and supply chain disruptions.
Financial and Operational Consequences of BlackSuit Attacks
The financial impact of a BlackSuit attack extends far beyond the initial ransom payment. Businesses face costs associated with data recovery, system restoration, legal fees, regulatory fines, and potential litigation from affected customers. The operational consequences can include significant downtime, loss of productivity, and damage to customer trust. The disruption to daily operations can lead to missed revenue opportunities, strained relationships with suppliers and customers, and even bankruptcy in extreme cases.
For example, a small manufacturing company might face substantial losses due to production halts, while a large hospital could experience life-threatening consequences from disruptions to patient care systems.
Long-Term Effects of BlackSuit Attacks
The long-term effects of a BlackSuit ransomware attack can be profound and far-reaching. Data breaches can lead to significant legal and regulatory repercussions, including hefty fines and lawsuits. Reputational damage can be equally damaging, impacting a company’s ability to attract customers, partners, and investors. The loss of sensitive data can also expose the organization to further cyberattacks and compromises.
The emotional toll on employees and executives can be significant, leading to decreased morale and productivity. The long-term recovery process can take months or even years, depending on the severity of the attack and the organization’s ability to effectively respond and recover.
Types of Data Targeted by BlackSuit Ransomware
The types of data targeted by BlackSuit are consistent with other ransomware operations. Understanding these targets is crucial for developing effective data protection strategies.
- Customer data (names, addresses, financial information, medical records)
- Financial records (bank statements, transaction logs, accounting data)
- Intellectual property (designs, patents, research data)
- Employee data (personal information, payroll records)
- Operational data (production schedules, supply chain information)
- System backups
Attribution and Response Strategies
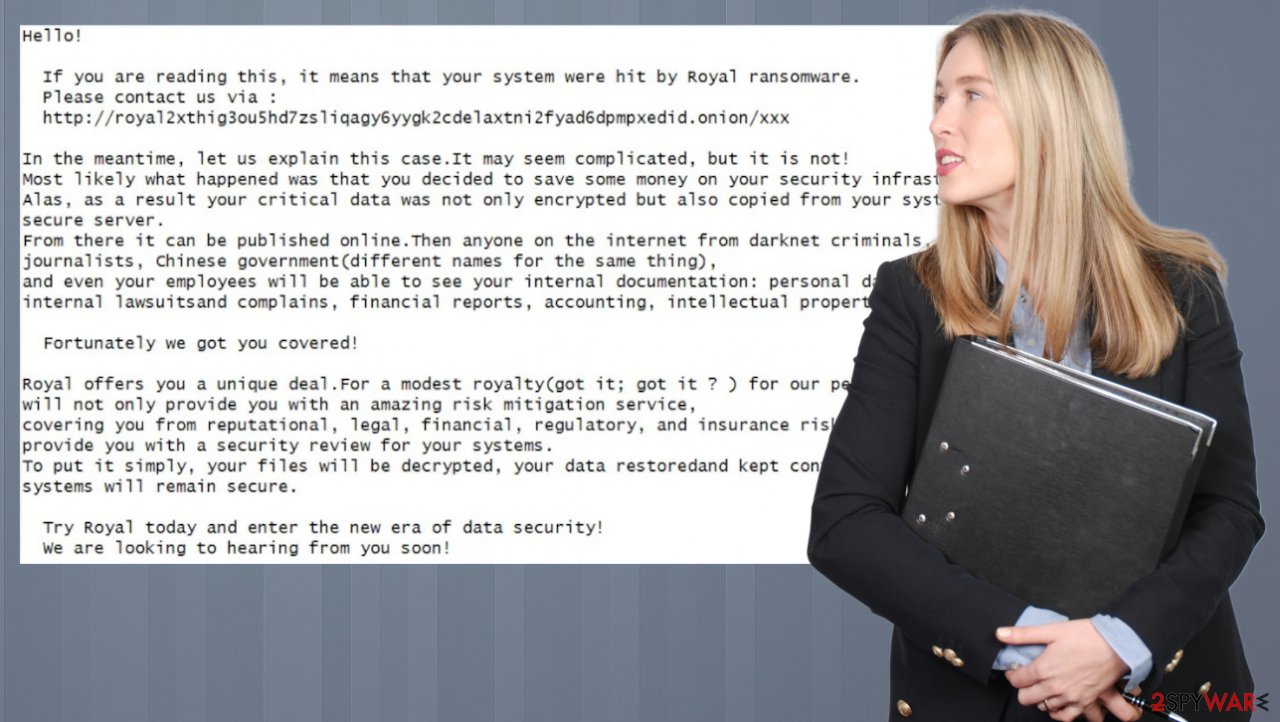
Pinpointing the exact individuals or groups behind BlackSuit ransomware remains a significant challenge. While its connection to Royal ransomware provides some clues, the decentralized and often obfuscated nature of ransomware operations makes definitive attribution difficult. Effective response strategies, however, rely on understanding the threat landscape and proactively mitigating risks.
Challenges in Attributing BlackSuit Attacks
Attribution in the ransomware world is notoriously complex. Ransomware operators frequently utilize anonymization techniques, including the use of Tor networks, virtual private networks (VPNs), and cryptocurrency for transactions. This makes tracing their digital footprints back to specific individuals or groups extremely challenging. Furthermore, the use of affiliate programs, where ransomware developers sell or lease their malware to others, further complicates the process of determining the true origin and perpetrators of attacks.
Investigating these attacks often requires extensive forensic analysis, international cooperation, and intelligence gathering from multiple sources. The lack of clear digital signatures or readily identifiable patterns in BlackSuit’s code, beyond its relation to Royal, also presents obstacles to straightforward attribution. Finally, the constant evolution of ransomware techniques and the adoption of new technologies by cybercriminals make attribution an ongoing race against time.
Preventing BlackSuit Ransomware Infections
Robust security practices are paramount in preventing BlackSuit and similar ransomware infections. This involves a multi-layered approach encompassing various security controls. Regular software updates are crucial to patch known vulnerabilities exploited by ransomware. Employing strong, unique passwords for all accounts and using multi-factor authentication (MFA) whenever possible significantly strengthens account security. Regular backups of critical data are essential, ideally stored offline or in a secure cloud environment.
This allows for data recovery in the event of a successful ransomware attack, minimizing the impact. Employee training on phishing and social engineering techniques is equally important, as many ransomware attacks begin with a successful phishing campaign. Restricting user access to sensitive data and systems based on the principle of least privilege can also significantly reduce the attack surface.
Finally, the implementation of a comprehensive endpoint detection and response (EDR) solution can help detect and mitigate malicious activity in real-time.
The Role of Law Enforcement and Cybersecurity Firms
Law enforcement agencies play a vital role in investigating ransomware attacks, identifying perpetrators, and pursuing legal action against them. This often involves international cooperation, as ransomware operations frequently span multiple countries. Cybersecurity firms contribute by analyzing ransomware samples, developing detection tools, and providing incident response services to victims. They also conduct threat intelligence research, sharing information about emerging ransomware threats and best practices for prevention and mitigation.
The collaborative effort between law enforcement and cybersecurity firms is crucial in disrupting ransomware operations and improving overall cybersecurity defenses. For example, joint operations have led to the takedown of several ransomware-as-a-service (RaaS) platforms, disrupting the business model of ransomware gangs and hindering their ability to launch attacks.
Final Review
The connection between BlackSuit and Royal ransomware underscores the evolving nature of cyber threats. It’s a stark reminder that we’re facing a highly adaptable and interconnected criminal underworld. While the specifics of their relationship may still be unfolding, one thing is clear: proactive security measures, robust incident response plans, and international collaboration are crucial to effectively combatting these sophisticated attacks.
Staying informed and vigilant is our best defense against the ever-present threat of ransomware.
FAQ Insights: Blacksuit Ransomware Linked To Royal Ransomware
What is the difference between BlackSuit and Royal ransomware?
While linked, subtle differences might exist in their encryption algorithms, attack vectors, or ransom negotiation tactics. Further research is needed to fully delineate these variations.
How can I protect myself from BlackSuit and Royal ransomware?
Maintain up-to-date software, employ strong passwords, enable multi-factor authentication, regularly back up your data, and train employees to recognize phishing attempts. A robust cybersecurity strategy is key.
Are there any known affiliates or groups behind these ransomware operations?
Attribution in ransomware attacks is challenging. Investigations are ongoing to identify and hold accountable those responsible for developing and deploying BlackSuit and Royal.
What should I do if I’ve been infected with BlackSuit or Royal ransomware?
Immediately disconnect from the network to prevent further spread. Do NOT pay the ransom. Contact law enforcement and a reputable cybersecurity firm for assistance with recovery and investigation.