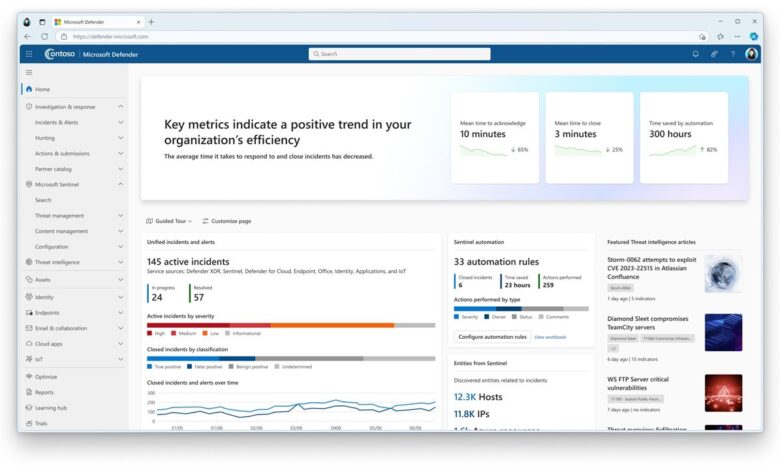
Microsoft to Release Windows Germanium with AI Security
Microsoft to release its Windows Germanium with AI security – that’s the buzz! Imagine an operating system that not only runs smoothly but also proactively protects you from cyber threats using the power of artificial intelligence. This hypothetical OS promises a new era of digital safety, leveraging AI for real-time threat detection, automated patching, and even predicting potential vulnerabilities before they’re exploited.
Could this be the future of secure computing? Let’s dive in!
Windows Germanium’s AI-powered security is poised to revolutionize how we interact with our computers. Features like predictive threat analysis and automated vulnerability patching will drastically reduce the risk of malware infections and data breaches. But with great power comes great responsibility – the privacy implications of AI-driven security are significant and require careful consideration. We’ll explore the potential benefits and drawbacks, along with the necessary safeguards to protect user data and privacy.
Introduction to Windows Germanium (Hypothetical OS)
Imagine a world where your operating system anticipates and thwarts cyber threats before they even reach your doorstep. That’s the promise of Windows Germanium, a hypothetical next-generation Windows operating system built from the ground up with AI-driven security at its core. This isn’t just incremental improvement; it’s a paradigm shift in how we think about operating system security.Windows Germanium leverages advanced machine learning algorithms to analyze system behavior in real-time, identifying and neutralizing threats with unprecedented speed and accuracy.
This proactive approach goes beyond traditional antivirus and firewall solutions, moving from reactive defense to predictive security. The OS learns your usage patterns, identifying anomalies that might indicate malware or unauthorized access. This predictive capability allows for a more seamless and secure user experience, minimizing interruptions and maximizing productivity. Furthermore, the AI engine continuously updates its threat models, ensuring the system remains resilient against the ever-evolving landscape of cyberattacks.
This constant learning and adaptation are key differentiators, making Germanium a truly self-improving security platform.
AI-Driven Security Features of Windows Germanium
Windows Germanium’s AI-powered security isn’t just a single feature; it’s woven into the fabric of the operating system. This holistic approach encompasses several key components working in concert. For instance, a sophisticated behavioral analysis engine constantly monitors system processes, flagging suspicious activity. This goes beyond simple signature-based detection; it looks for patterns and deviations from established baselines.
A built-in threat intelligence system automatically downloads and applies the latest threat data, ensuring the system stays ahead of emerging threats. This is supplemented by an advanced sandboxing environment that isolates potentially malicious code, preventing it from harming the system. Finally, a self-healing mechanism automatically repairs damaged system files and configurations, ensuring system stability and resilience. Imagine a system that not only detects a virus but also automatically cleans the infection and strengthens its defenses against future attacks – that’s the power of Windows Germanium.
Anticipated Market Impact of Windows Germanium
The release of Windows Germanium could significantly reshape the operating system market. Its advanced AI-driven security features would attract businesses and individuals concerned about data breaches and cyberattacks. The increased security would translate into reduced downtime, lower costs associated with security incidents, and improved user confidence. This could potentially lead to a shift in market share, with users migrating from competing operating systems seeking the enhanced security offered by Germanium.
We might see a reduction in the prevalence of ransomware attacks and phishing scams as the AI effectively prevents these threats from taking hold. The success of similar AI-powered security solutions in other sectors suggests a strong potential for widespread adoption of Windows Germanium. For example, the increased use of AI in fraud detection by financial institutions has demonstrated the effectiveness of this technology in preventing financial losses.
Tagline for Windows Germanium
Windows Germanium: AI Security. Predictive Protection.
AI-Powered Security Features in Windows Germanium
Windows Germanium represents a significant leap forward in operating system security, leveraging the power of artificial intelligence to proactively defend against evolving threats. Unlike previous generations relying primarily on signature-based detection, Germanium employs a multi-layered AI-driven approach, offering a more predictive and adaptive security posture. This results in a system that’s not only better at identifying known threats but also at anticipating and mitigating previously unseen attacks.
Threat Prediction and Proactive Defense
Windows Germanium’s AI engine analyzes system behavior, network traffic, and user activity to identify patterns indicative of impending attacks. This goes beyond simple signature matching; the AI learns from vast datasets of malicious activity, allowing it to predict potential threats before they manifest. For example, it might detect unusual access attempts to critical system files, even if the specific malware used is unknown.
This proactive approach significantly reduces the window of vulnerability, preventing many attacks before they can succeed. This contrasts sharply with traditional antivirus solutions that often react onlyafter* malware has already infiltrated the system. Existing operating systems offer some level of threat detection, but they generally lack the predictive capabilities of Germanium’s AI engine. For instance, while Windows 11 has improved threat detection, its reliance on signature updates makes it less effective against zero-day exploits.
Real-Time Malware Detection and Response
Germanium employs advanced machine learning algorithms to analyze running processes in real-time, identifying malicious behavior based on a combination of static and dynamic analysis. This means the system not only scans files for known malware signatures but also monitors process behavior for suspicious actions. If a suspicious process is detected, the AI can automatically quarantine or terminate it, preventing further damage.
This contrasts with many existing systems where malware may execute for some time before detection, potentially causing significant harm. For instance, while macOS’s XProtect offers real-time scanning, its capabilities are less sophisticated than the AI-driven approach in Windows Germanium.
Automated Vulnerability Patching and System Hardening
Windows Germanium’s AI continuously monitors for known and unknown vulnerabilities in the system and its applications. When a vulnerability is detected, the system automatically downloads and applies the necessary patches, minimizing the window of exposure. Furthermore, the AI can dynamically adjust system security settings based on identified threats and user behavior, hardening the system against attacks. This automated patching surpasses the manual or scheduled patching processes common in other operating systems like Linux distributions, which often rely on user intervention for updates.
This automated approach minimizes the risk of unpatched vulnerabilities.
AI Security Settings Management Interface
The user interface for managing AI security settings in Windows Germanium is designed for simplicity and clarity. It provides a clear overview of the system’s security status and allows users to customize certain aspects of the AI’s behavior.
| Feature | Description | Status | Action |
|---|---|---|---|
| Threat Prediction Level | Adjusts the sensitivity of the threat prediction engine. Higher levels provide more aggressive protection but may result in more false positives. | Medium | |
| Real-time Malware Protection | Enables or disables real-time scanning and automated response to malicious processes. | Enabled | |
| Automated Patching | Configures the automatic download and installation of security updates. | Automatic | |
| System Hardening Level | Adjusts the aggressiveness of system hardening measures. Higher levels provide enhanced protection but may impact system performance. | Balanced |
Impact on User Privacy and Data Security
The integration of AI into Windows Germanium’s security features presents a double-edged sword. While offering enhanced protection against threats, it also raises legitimate concerns about user privacy and the potential misuse of personal data. Microsoft’s commitment to responsible AI development is crucial in navigating this complex landscape. The balance between robust security and individual privacy rights must be carefully maintained and transparently communicated to users.AI-powered security inherently requires the processing of user data to identify patterns and anomalies indicative of malicious activity.
This data could range from browsing history and application usage to file access patterns and network connections. The potential for misuse, whether intentional or unintentional, is a serious consideration. Therefore, rigorous safeguards are essential to ensure user data remains secure and protected from unauthorized access, use, or disclosure.
Data Minimization and Purpose Limitation
Windows Germanium employs a strict data minimization policy. Only the data absolutely necessary for security analysis is collected and processed. This limits the potential impact of any data breach and ensures that only relevant information is used for its intended purpose – enhancing security, not profiling users. For example, instead of logging every single keystroke, the system might only analyze sequences of characters that match known malware patterns.
This approach drastically reduces the amount of personal data handled, mitigating privacy risks.
Data Encryption and Anonymization
All user data collected by Windows Germanium’s AI security features is encrypted both in transit and at rest using industry-standard encryption algorithms. This ensures that even if data is intercepted, it remains unreadable without the appropriate decryption keys. Furthermore, techniques like differential privacy and data anonymization are employed to further protect user identities and sensitive information. Data anonymization techniques replace identifying information with pseudonyms or aggregated data, preventing the re-identification of individuals.
Transparency and User Control
Microsoft is committed to transparency regarding the data collected and how it’s used. Windows Germanium provides users with clear and accessible information about the AI security features, the types of data collected, and how that data is processed. Users are given granular control over their privacy settings, allowing them to adjust the level of data collection and processing according to their preferences.
This includes the ability to opt out of certain features or to request the deletion of their data. This control empowers users to manage their privacy within the context of enhanced security.
Regular Security Audits and Compliance
To maintain the highest standards of data security and privacy, Windows Germanium undergoes regular independent security audits and adheres to relevant data privacy regulations such as GDPR and CCPA. These audits ensure that the system’s security measures are effective and that the data handling practices align with the highest ethical and legal standards. This commitment to ongoing scrutiny helps to build and maintain user trust.
- Data Minimization: Only essential data for security analysis is collected.
- End-to-End Encryption: All data is encrypted both in transit and at rest.
- Data Anonymization: Techniques like differential privacy are used to protect user identities.
- Transparency and User Control: Clear information and granular control over privacy settings are provided.
- Regular Security Audits and Compliance: Independent audits and adherence to data privacy regulations.
Hardware and Software Requirements
Windows Germanium, with its ambitious AI-powered security features, naturally demands a certain level of hardware and software capability to function optimally. This section details the minimum specifications and compatibility considerations for a smooth user experience. We’ll also compare these requirements to previous Windows iterations to highlight the advancements and potential upgrade needs.The minimum hardware requirements for Windows Germanium reflect the increased computational demands of its sophisticated AI engine and enhanced security protocols.
While aiming for broad accessibility, some compromises were necessary to ensure the seamless integration of these cutting-edge features. Meeting these minimum requirements will allow for basic functionality, but for a truly optimal experience, exceeding these specifications is strongly recommended.
Minimum Hardware Requirements
The minimum hardware specifications for running Windows Germanium are designed to ensure a functional, albeit potentially less responsive, user experience. Users with systems falling below these specifications might encounter performance bottlenecks, especially when utilizing the AI-driven features. Upgrading to meet or exceed these requirements is advised for a smoother experience.
- Processor: A quad-core processor with a minimum clock speed of 2.5 GHz. This ensures sufficient processing power for both the operating system and the AI security components. Examples of suitable processors include Intel Core i5-10400 or AMD Ryzen 5 3600.
- RAM: 8 GB of DDR4 RAM. This amount of memory is necessary to handle the multitasking demands of Windows Germanium and the AI processes running in the background. Increasing RAM to 16GB or more is recommended for better performance, especially with multiple applications running concurrently.
- Storage: 128 GB of SSD storage. Solid-state drives (SSDs) offer significantly faster boot times and application loading compared to traditional hard disk drives (HDDs). The speed advantage is crucial for the responsiveness of the AI security features.
- Graphics: Integrated graphics capable of DirectX 12 support. While not demanding high-end graphics, DirectX 12 support is essential for the smooth operation of certain system components.
Software Compatibility
Windows Germanium strives for broad software compatibility with existing applications and peripherals. However, due to the significant architectural changes implemented for enhanced security, some older applications might require updates or might not be fully compatible. Microsoft is actively working to ensure compatibility with the widest possible range of software, but users should anticipate some potential issues with very outdated software.The compatibility with peripherals is generally excellent, with support for a wide array of devices.
However, some specialized or very old peripherals might require updated drivers or might not be fully supported. Microsoft is working to address this compatibility challenge.
Comparative Analysis of System Requirements
Compared to previous Windows versions, Windows Germanium exhibits a noticeable increase in minimum system requirements. This increase is directly attributable to the integration of the AI-powered security features, which necessitate greater processing power and memory.
| Feature | Windows 10 | Windows 11 | Windows Germanium |
|---|---|---|---|
| Processor | 1 GHz or faster | 1 GHz or faster with 2 or more cores on a 64-bit processor | 2.5 GHz quad-core processor |
| RAM | 1 GB (32-bit) / 2 GB (64-bit) | 4 GB | 8 GB |
| Storage | 16 GB (32-bit) / 20 GB (64-bit) | 64 GB | 128 GB SSD |
The table above illustrates the progressive increase in system requirements from Windows 10 to Windows 11 and finally to Windows Germanium. The jump in requirements from Windows 11 to Germanium reflects the significant increase in computational demands of the AI security suite. Users upgrading from older systems should carefully consider these differences before installing Windows Germanium.
Potential Challenges and Limitations
Developing and deploying an AI-driven operating system like Windows Germanium presents a unique set of hurdles. The inherent complexity of integrating AI into the core functionality of an OS, coupled with the ever-evolving landscape of cyber threats, necessitates a thorough understanding of potential pitfalls and limitations. Successfully navigating these challenges will be crucial for ensuring the security and stability of the system.AI-based security, while promising, isn’t a silver bullet.
Its effectiveness depends heavily on the quality and quantity of training data, the sophistication of the algorithms employed, and the ability to adapt to novel attack vectors. Limitations in these areas can leave the system vulnerable to exploitation, highlighting the need for a multi-layered security approach that complements AI capabilities with traditional security measures.
Challenges in Developing and Deploying an AI-Driven OS
Developing an AI-driven OS involves significant technical challenges. First, integrating AI seamlessly into the OS’s core functions requires substantial engineering effort. This includes designing robust APIs, optimizing performance for resource-constrained environments, and ensuring compatibility with existing hardware and software. Secondly, maintaining the system’s stability and reliability while incorporating AI components is paramount. AI models can be unpredictable, and malfunctions could lead to system crashes or data loss.
Finally, the development process itself needs to be rigorous, involving extensive testing and validation to ensure the AI components meet the required security and performance standards. This includes rigorous testing for edge cases and potential vulnerabilities, which may be hard to predict and account for. Consider the complexity of developing self-driving cars; similar levels of rigorous testing and validation are needed for AI-driven OS components.
Limitations of AI-Based Security in Mitigating Emerging Threats, Microsoft to release its windows germanium with ai security
AI-based security solutions, while powerful, are not foolproof against all emerging threats. One key limitation is the “arms race” between attackers and defenders. As AI-powered security systems improve, attackers will inevitably develop more sophisticated methods to bypass them. Another limitation is the potential for adversarial attacks. Attackers can manipulate the input data to fool the AI system, leading to false negatives or inaccurate threat assessments.
For example, an attacker might craft a carefully designed piece of malware that is disguised to evade detection by the AI security system. Furthermore, AI models are only as good as the data they are trained on. If the training data does not adequately represent the full spectrum of threats, the AI system may fail to identify new or unusual attacks.
This highlights the ongoing need for human oversight and intervention in security systems.
Potential Vulnerabilities and Mitigation Strategies
The integration of AI into Windows Germanium introduces new potential vulnerabilities. It is crucial to proactively address these risks through robust mitigation strategies.
- Vulnerability: Data poisoning attacks, where malicious actors manipulate the training data to compromise the AI model’s accuracy. Mitigation: Implement rigorous data validation and verification processes, incorporating techniques like anomaly detection and data provenance tracking.
- Vulnerability: Adversarial examples, specifically crafted inputs designed to deceive the AI security system. Mitigation: Develop robust AI models that are resistant to adversarial attacks, employing techniques like adversarial training and input sanitization.
- Vulnerability: Model extraction attacks, where attackers attempt to steal or reverse-engineer the AI model. Mitigation: Employ model obfuscation techniques, such as differential privacy and model compression, to make it more difficult for attackers to extract valuable information.
- Vulnerability: Exploiting vulnerabilities in the AI model’s underlying code or infrastructure. Mitigation: Conduct thorough security audits of the AI components and underlying infrastructure, employing secure coding practices and regular penetration testing.
Marketing and Public Perception
Launching Windows Germanium, with its groundbreaking AI-powered security, requires a multifaceted marketing strategy that transcends typical OS releases. We need to effectively communicate the tangible benefits of this advanced security, while simultaneously addressing potential public concerns surrounding AI and data privacy. Success hinges on building trust and demonstrating the value proposition clearly and concisely.The public perception of AI security is currently a complex landscape.
Microsoft’s upcoming Windows Germanium, boasting AI-powered security, is a game-changer. This focus on enhanced security reminds me of the streamlined development offered by low-code/pro-code platforms; check out this great article on domino app dev the low code and pro code future for a different perspective on building secure and efficient applications. Ultimately, both advancements point towards a future where powerful tech is both innovative and easy to secure.
While many recognize the potential benefits of AI in enhancing security, there are also significant concerns about data privacy, algorithmic bias, and the potential for misuse. Successfully navigating this landscape requires a transparent and proactive approach, emphasizing the measures taken to protect user data and ensure responsible AI implementation. This will involve clearly articulating the ethical considerations and safeguards built into Windows Germanium.
Marketing Strategy for Windows Germanium
The marketing campaign for Windows Germanium should focus on the tangible benefits of its AI-powered security features. Instead of focusing solely on technical specifications, the campaign should highlight real-world scenarios where the AI security actively protects users from threats. For example, we could showcase how the AI proactively identifies and blocks sophisticated phishing attempts or malware before they can even reach the user’s system.
This approach, emphasizing user experience and peace of mind, is crucial for building trust and driving adoption. A multi-channel approach utilizing targeted online advertising, social media engagement, and partnerships with key influencers in the tech industry will also be vital. We should consider creating short, impactful video demonstrations showcasing the AI’s capabilities in a clear and easily understandable way.
These videos could depict real-world scenarios where the AI successfully thwarts cyberattacks, thereby directly demonstrating the value proposition to potential customers.
Public Perception of AI Security and Windows Germanium Adoption
Public trust is paramount for the successful adoption of Windows Germanium. Negative perceptions of AI, fueled by concerns about data privacy and potential misuse, could significantly hinder adoption rates. To mitigate this, Microsoft must actively engage in transparent communication about the data handling practices of Windows Germanium. This includes clearly outlining what data is collected, how it is used, and the measures in place to protect user privacy.
Building partnerships with independent security experts and organizations to conduct audits and verify the system’s security will also help build trust and credibility. Transparency and independent verification are key to reassuring potential users that their data is safe and their privacy is respected. Think of the success of Tesla’s Autopilot – while initially met with skepticism, consistent positive user experiences and data transparency have significantly improved public perception.
Competitor Reactions to Windows Germanium
The release of Windows Germanium is likely to provoke significant reactions from competitors in the operating system market. We can anticipate intensified marketing efforts from companies like Apple and Google, potentially highlighting the perceived weaknesses of AI-powered security or emphasizing the privacy features of their own operating systems. We should expect a heightened focus on competitive benchmarking and comparisons, potentially leading to an increase in marketing claims and counter-claims.
However, the focus on demonstrably superior security features in Windows Germanium, backed by transparent data handling practices and independent verification, can serve as a strong counterpoint to these competitive pressures. We can learn from Apple’s response to the introduction of Android – initially a defensive strategy, Apple eventually adapted and solidified its position through innovation and a focus on user experience.
Illustrative Example: AI-Driven Threat Detection
Let’s imagine a scenario where a user receives a seemingly legitimate email appearing to be from their bank, prompting them to update their account details via a provided link. This is a classic phishing attack, and Windows Germanium’s AI security features are designed to detect and neutralize such threats proactively. The system doesn’t rely solely on signature-based detection, but rather employs a multi-layered approach leveraging machine learning and behavioral analysis.This example will detail how Windows Germanium’s AI would handle this phishing attempt, demonstrating the power of its predictive and reactive capabilities.
AI-Driven Phishing Detection Process
The following steps illustrate how Windows Germanium’s AI would detect and respond to this sophisticated phishing attack. The system operates in real-time, analyzing various data points concurrently.
- Initial Email Analysis: Upon receiving the email, Windows Germanium’s AI immediately begins analyzing various aspects of the message. This includes examining the sender’s email address for inconsistencies, checking the email’s headers for suspicious routing information, and scrutinizing the email’s content for common phishing indicators such as urgent language, grammatical errors, and suspicious links.
- URL Analysis and Reputation Check: The AI focuses particularly on the embedded link. It checks the link’s reputation against its extensive database of known malicious URLs. This database is constantly updated using both static analysis (checking for known malicious patterns) and dynamic analysis (observing the behavior of the URL in a controlled environment).
- Behavioral Analysis: Even if the URL isn’t flagged as malicious, the AI doesn’t stop there. It analyzes the email’s behavior. For example, it checks if the email attempts to download files or execute scripts without user consent. Unusual email activity, such as sending the email to many recipients simultaneously, is also a red flag.
- Machine Learning Model Prediction: All the data collected from the previous steps is fed into a sophisticated machine learning model. This model is trained on millions of data points, including both benign and malicious emails. Based on this data, the model predicts the likelihood of the email being a phishing attempt. The prediction is based on a complex algorithm that weighs various factors, assigning different levels of importance to each.
- Real-time Response: If the AI’s prediction surpasses a predefined threshold (indicating a high probability of a phishing attack), it immediately intervenes. The user might receive a warning notification, highlighting the potential threat. The link might be blocked, preventing the user from accessing the malicious website. The email itself might be moved to a quarantined folder.
Mitigation and User Notification
Windows Germanium prioritizes user safety and transparency. The system doesn’t simply block threats silently. Users are informed about the potential threat and the actions taken. The notification provides clear and concise information, including the reason for the block, allowing users to understand the AI’s decision-making process and build trust in the system. Further, the user is given the option to review the details of the threat assessment, fostering user education and empowering them to make informed decisions about their online security.
Outcome Summary: Microsoft To Release Its Windows Germanium With Ai Security
The potential release of Windows Germanium with its AI-powered security represents a significant leap forward in digital security. While challenges remain in balancing security with user privacy, the prospect of an OS that proactively protects against emerging threats is undeniably exciting. The future of computing is undeniably intertwined with AI, and Windows Germanium could well be a leading example of this integration.
Only time will tell if it lives up to the hype, but the possibilities are certainly intriguing!
Top FAQs
What hardware will I need to run Windows Germanium?
Specific requirements haven’t been released, but expect higher specifications than previous Windows versions due to the AI processing demands.
Will my current software work with Windows Germanium?
Microsoft aims for broad compatibility, but some older applications might require updates or might not be supported.
How does Windows Germanium’s AI protect my privacy?
Microsoft promises robust data encryption and anonymization techniques to protect user privacy while utilizing AI for security.
Is Windows Germanium’s AI security foolproof?
No security system is completely foolproof. While AI significantly enhances security, it’s crucial to practice good online habits.





