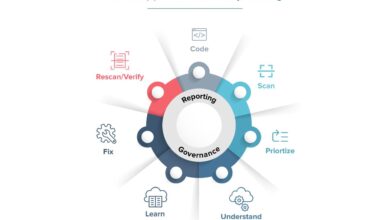
Mobile Application Security Testing Continues Upward Trajectory
Mobile application security testing continues upward trajectory, and it’s about time! With our ever-increasing reliance on apps for everything from banking to ordering groceries, the need for robust security measures has exploded. This isn’t just about protecting user data; it’s about protecting our digital lives. We’ll delve into the rising demand, explore various testing methodologies, uncover emerging threats, and discover how to build safer apps from the ground up.
Get ready for a deep dive into the world of app security!
This post will cover the crucial aspects of mobile application security, from understanding the different types of testing (like SAST and DAST) to implementing secure coding practices and leveraging automation tools. We’ll also look at the future of app security, including the impact of AI and the ever-evolving regulatory landscape. It’s a constantly evolving field, so staying informed is key.
Let’s get started!
The Rising Demand for Mobile Application Security Testing
The mobile landscape is exploding, with billions of users relying on apps for everything from banking and shopping to healthcare and communication. This ubiquitous reliance on mobile applications has, unsurprisingly, led to a dramatic increase in the demand for robust mobile application security testing. The consequences of neglecting security are simply too severe to ignore.The need for comprehensive mobile app security testing is fueled by several key factors.
Firstly, the increasing sophistication of cyberattacks targeting mobile platforms necessitates proactive security measures. Attackers are constantly developing new techniques to exploit vulnerabilities, making it crucial for developers to stay ahead of the curve. Secondly, the growing amount of sensitive personal and financial data handled by mobile apps makes them prime targets for malicious actors. Finally, regulatory compliance requirements, such as GDPR and CCPA, impose stringent security standards on businesses handling personal data, further driving the demand for thorough security testing.
Consequences of Inadequate Mobile App Security
Inadequate mobile app security can result in a range of devastating consequences, impacting both users and businesses. Data breaches can lead to the exposure of sensitive personal information, financial losses, reputational damage, and legal liabilities. Compromised apps can be used to deploy malware, steal credentials, or conduct other malicious activities. For businesses, the financial costs associated with a security breach, including investigation, remediation, legal fees, and potential fines, can be substantial.
Loss of customer trust can also have long-term negative effects on revenue and market share.
Examples of High-Profile Mobile App Security Breaches
Several high-profile mobile app security breaches have highlighted the critical importance of robust security testing. For instance, the 2017 Equifax breach, while not solely a mobile app issue, exposed the vulnerability of massive databases accessible through various channels, including potentially mobile applications connected to the compromised systems. The impact was widespread, affecting millions of consumers and costing Equifax billions in fines and remediation efforts.
Similarly, breaches affecting banking and financial apps have resulted in significant financial losses for both users and institutions. These events serve as stark reminders of the potential consequences of neglecting mobile app security.
Mobile App Security Testing Methodologies
A variety of methodologies exist for testing the security of mobile applications. The choice of methodology often depends on factors such as budget, time constraints, and the specific security risks being addressed.
| Methodology | Description | Advantages | Disadvantages |
|---|---|---|---|
| Static Application Security Testing (SAST) | Analyzes the application’s source code without executing it to identify vulnerabilities. | Early detection of vulnerabilities, relatively low cost. | May produce false positives, does not detect runtime vulnerabilities. |
| Dynamic Application Security Testing (DAST) | Tests the running application to identify vulnerabilities during runtime. | Detects runtime vulnerabilities, provides a realistic view of security risks. | Can be more time-consuming and expensive than SAST. |
| Interactive Application Security Testing (IAST) | Combines aspects of SAST and DAST, providing a more comprehensive approach. | Provides detailed insights into vulnerabilities, combines the strengths of SAST and DAST. | Requires specialized tools and expertise. |
| Penetration Testing | Simulates real-world attacks to identify vulnerabilities and assess the effectiveness of security controls. | Provides a realistic assessment of security risks, identifies potential attack vectors. | Can be expensive and time-consuming. |
Types of Mobile Application Security Testing
Mobile application security testing is crucial in today’s digital landscape, where mobile apps handle sensitive user data and are increasingly targeted by malicious actors. Understanding the different types of testing is essential for building robust and secure applications. This post delves into two primary approaches: Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST), comparing their strengths and weaknesses.
We’ll also explore the various facets of mobile penetration testing.
Static Application Security Testing (SAST) for Mobile Apps
SAST analyzes the source code and compiled binaries of a mobile application without actually executing it. Think of it as a thorough code review performed by a sophisticated automated tool. These tools examine the application’s code for known vulnerabilities, such as buffer overflows, SQL injection flaws, and insecure data storage practices. SAST is typically integrated into the development pipeline, allowing for early detection and remediation of security flaws before they reach production.
The process involves uploading the application’s codebase to the SAST tool, which then performs a comprehensive scan, generating a detailed report highlighting identified vulnerabilities along with their severity and location within the code. This allows developers to pinpoint the exact source of the problem and address it efficiently. A significant benefit is the ability to find vulnerabilities early in the development lifecycle, reducing the cost and effort associated with fixing them later.
Dynamic Application Security Testing (DAST) for Mobile Apps
Unlike SAST, DAST analyzes the application while it’s running. It simulates real-world attacks to identify vulnerabilities in the application’s runtime behavior. This includes testing for vulnerabilities like cross-site scripting (XSS), insecure authentication mechanisms, and improper input validation. The process involves running the application in a controlled environment and subjecting it to a series of automated attacks. The DAST tool monitors the application’s response to these attacks, identifying any weaknesses that could be exploited by malicious actors.
DAST provides a real-world perspective on the application’s security posture, complementing the code-level analysis provided by SAST. A key benefit is its ability to detect vulnerabilities that might not be apparent through static analysis alone, such as runtime errors or unexpected behavior.
SAST vs. DAST: A Comparison
SAST and DAST offer complementary approaches to mobile application security testing. SAST excels at finding vulnerabilities early in the development lifecycle, reducing the cost of remediation. However, it might miss vulnerabilities that only manifest during runtime. DAST, on the other hand, focuses on runtime vulnerabilities but can be more time-consuming and may require more specialized expertise to interpret the results.
An ideal approach often involves combining both SAST and DAST for a comprehensive security assessment.
| Feature | SAST | DAST |
|---|---|---|
| Testing Stage | Development (Early) | Deployment (Late) |
| Analysis Method | Code analysis | Runtime analysis |
| Vulnerability Detection | Code-level vulnerabilities | Runtime vulnerabilities |
| False Positives | Potentially higher | Potentially lower |
| Cost | Generally lower | Generally higher |
Types of Mobile Application Penetration Testing
Penetration testing is a crucial aspect of mobile app security. It involves simulating real-world attacks to identify vulnerabilities that could be exploited by malicious actors. Different approaches exist, each focusing on specific aspects of the application’s security.
The following list Artikels several types of mobile penetration testing:
- Black Box Testing: The tester has no prior knowledge of the application’s internal workings.
- White Box Testing: The tester has full access to the application’s source code and internal documentation.
- Grey Box Testing: The tester has some knowledge of the application, such as its architecture or functionality.
- Network Penetration Testing: This focuses on vulnerabilities in the network infrastructure supporting the application.
- Source Code Review: A manual examination of the application’s source code for security flaws.
- Reverse Engineering: Analyzing the compiled application to understand its functionality and identify vulnerabilities.
Emerging Threats in Mobile Application Security
The mobile landscape is constantly evolving, bringing with it new and sophisticated threats to application security. While established vulnerabilities remain a concern, the rapid pace of technological advancement introduces novel attack vectors that demand proactive and adaptive security measures. Understanding these emerging threats is crucial for developers and security professionals to build robust and resilient mobile applications.
Sophisticated Mobile Malware
Mobile malware is becoming increasingly sophisticated, leveraging advanced techniques to evade detection and achieve its malicious goals. We’re seeing a rise in polymorphic malware, which constantly changes its code to avoid signature-based detection, and malware that utilizes advanced obfuscation techniques to hide its true nature. Furthermore, the integration of AI and machine learning into malware development is leading to more autonomous and adaptive attacks, making traditional security measures less effective.
For example, the recent emergence of malware that utilizes deepfakes to bypass biometric authentication highlights the increasing sophistication of these threats. This necessitates a move beyond signature-based detection towards more behavioral analysis and machine learning-based security solutions.
Third-Party Library and API Vulnerabilities
The widespread use of third-party libraries and APIs significantly accelerates mobile app development, but it also introduces considerable security risks. These components often contain vulnerabilities that are unknown or unpatched, creating a significant attack surface for malicious actors. A single vulnerability in a widely used library can compromise thousands of applications, leading to large-scale data breaches or other security incidents.
For instance, the discovery of a critical vulnerability in a popular image processing library could expose sensitive user data stored within apps utilizing that library. Thorough vetting of third-party components, regular updates, and proactive security testing are essential to mitigate these risks.
Supply Chain Attacks Targeting Mobile Development
Supply chain attacks are becoming increasingly prevalent, targeting the entire software development lifecycle, including mobile app development. These attacks involve compromising trusted tools, libraries, or processes used in the development pipeline to introduce malicious code into applications. This can be achieved through compromised developer accounts, tainted build systems, or malicious third-party components. The consequences can be devastating, potentially leading to widespread compromise of applications and user data.
A recent example is the infiltration of a popular code repository, which led to the compromise of numerous applications relying on the affected code. Robust security practices throughout the development pipeline, including secure coding practices, code signing, and rigorous security audits, are crucial to mitigate the risk of supply chain attacks.
Vulnerabilities and Mitigation Strategies
| Threat | Vulnerabilities | Mitigation Strategies |
|---|---|---|
| Sophisticated Mobile Malware | Polymorphic code, advanced obfuscation, AI-powered attacks, evasion of traditional security measures. | Behavioral analysis, machine learning-based detection, sandboxing, regular security updates, proactive threat intelligence. |
| Third-Party Library and API Vulnerabilities | Unpatched vulnerabilities, insecure coding practices in libraries, lack of transparency in library code. | Thorough vetting of libraries, regular security audits of third-party components, using reputable sources, implementing robust dependency management. |
| Supply Chain Attacks | Compromised developer accounts, tainted build systems, malicious third-party components. | Secure coding practices, code signing, secure build processes, regular security audits of the development pipeline, multi-factor authentication. |
Best Practices for Secure Mobile Application Development: Mobile Application Security Testing Continues Upward Trajectory
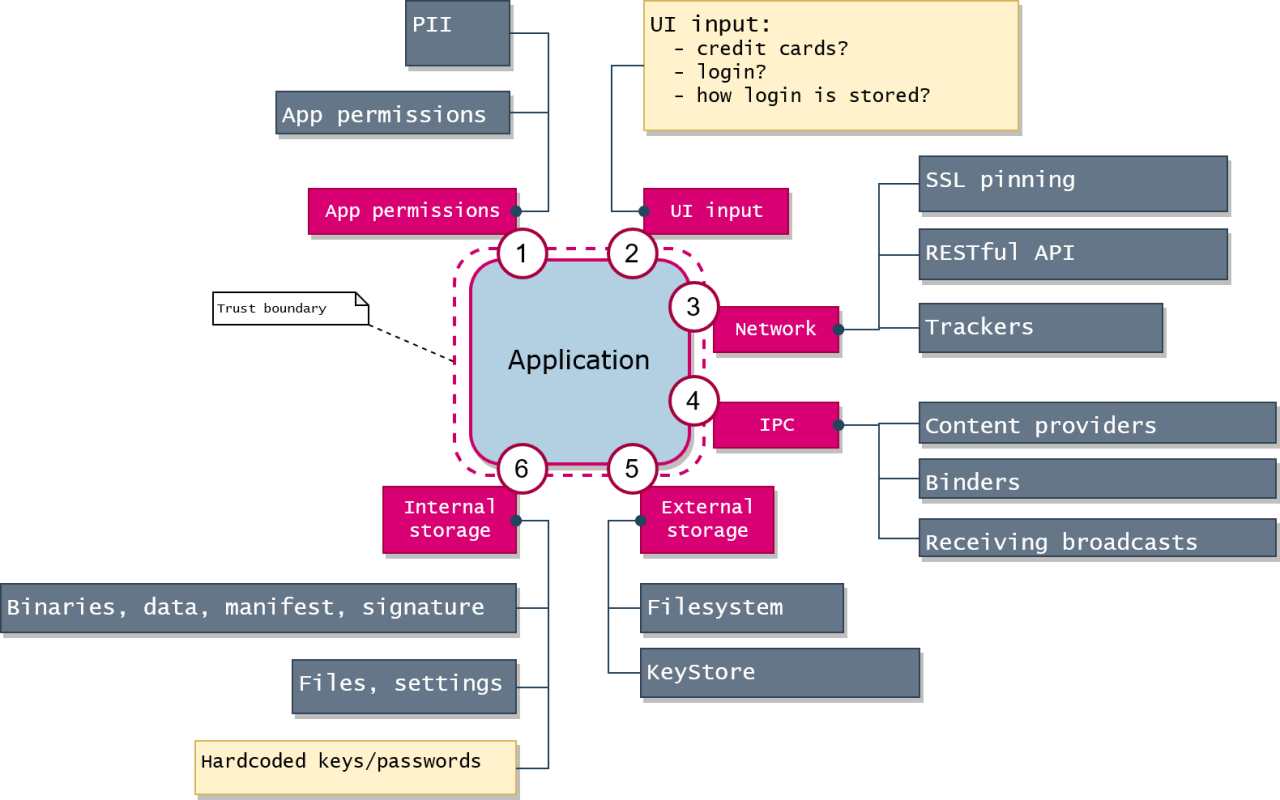
Building secure mobile applications requires a proactive approach integrated throughout the entire development lifecycle. Neglecting security from the outset can lead to costly vulnerabilities and reputational damage later. This section Artikels key best practices to embed security into your mobile development process, minimizing risks and ensuring user trust.
Secure Coding Practices
Secure coding is paramount. It involves following specific guidelines and techniques to prevent common vulnerabilities. This includes consistently using parameterized queries to prevent SQL injection, input validation to thwart cross-site scripting (XSS) attacks, and proper error handling to avoid revealing sensitive information. Regular code reviews, performed by individuals not directly involved in the initial development, are crucial for identifying potential weaknesses before deployment.
Adopting a secure coding standard, such as OWASP Mobile Security Project guidelines, provides a framework for consistent and effective implementation.
Code Signing and Certificate Management
Code signing digitally verifies the authenticity and integrity of your application. It ensures that the application hasn’t been tampered with since it was built and signed by the legitimate developer. Certificates, used for code signing, must be carefully managed and protected. This involves using strong key generation and storage practices, renewing certificates before expiration to prevent application malfunctions, and following best practices for key revocation if necessary.
Failure to properly manage certificates can lead to application distribution failures or, worse, users installing malicious applications masquerading as yours.
Data Encryption and Protection
Protecting sensitive user data is critical. All data transmitted to and from the application should be encrypted using strong, industry-standard algorithms like AES-256. Data at rest, stored on the device, should also be encrypted. Implement robust access controls to limit data access only to authorized components within the application. Consider using techniques like tokenization to replace sensitive data with non-sensitive substitutes when feasible.
For example, replacing a credit card number with a unique token for internal processing greatly reduces the risk if a data breach occurs. Regularly review and update your encryption methods to stay ahead of evolving cryptographic vulnerabilities.
Secure Development Lifecycle Flowchart
The following describes a flowchart for a secure mobile application development lifecycle.Imagine a flowchart with these stages:
1. Requirements Gathering & Security Analysis
This initial stage involves identifying security requirements and potential vulnerabilities early on. Security considerations are integrated into the initial design phase, not as an afterthought.
2. Design & Architecture
The application architecture is designed with security in mind, considering secure communication protocols, data storage mechanisms, and authentication methods.
3. Implementation & Secure Coding
Developers follow secure coding practices, utilizing secure libraries and frameworks, and adhering to coding standards. Regular code reviews and static analysis are performed.
4. Testing & Vulnerability Assessment
Comprehensive testing, including penetration testing, static and dynamic analysis, and security audits, is conducted to identify and address vulnerabilities. This phase includes both functional and security testing.
5. Deployment & Monitoring
The application is deployed securely, using appropriate deployment strategies and infrastructure. Post-deployment monitoring tracks application behavior and identifies any potential security incidents.
6. Maintenance & Updates
Regular security updates and patches are released to address newly discovered vulnerabilities. Continuous monitoring and analysis ensure the application remains secure over its lifecycle. This loop back to step 1 for iterative improvements.
The Role of Automation in Mobile Application Security Testing

In today’s fast-paced mobile app development landscape, manual security testing is simply not enough. The sheer volume of apps, coupled with the ever-evolving threat landscape, necessitates a shift towards automation. Automating mobile application security testing (MAST) allows development teams to significantly improve the speed and efficiency of their security efforts, ultimately leading to more secure applications.Automating MAST processes offers several key benefits.
It dramatically reduces the time required for testing, allowing security teams to cover more ground and identify vulnerabilities faster. This speed increase is particularly crucial in agile development environments where rapid release cycles are the norm. Furthermore, automation minimizes human error, ensuring consistency and thoroughness in testing procedures. Automated tools can perform repetitive tasks tirelessly, eliminating the fatigue and oversight that can plague manual testing.
This results in more reliable identification of vulnerabilities, leading to improved overall application security.
Popular Automation Tools for Mobile App Security Testing
Several powerful tools are available for automating mobile app security testing. These tools vary in their features and capabilities, catering to different needs and budgets. For example, OWASP ZAP (Open Web Application Security Project Zed Attack Proxy) is a widely used open-source tool that offers a comprehensive suite of automated security testing features. It’s highly versatile, supporting various testing methodologies, and is constantly being updated with new features.
Alternatively, commercial tools like AppScan and Mobile Security Framework (MobSF) provide more advanced features, often including integrated reporting and vulnerability management capabilities. AppScan, for instance, boasts powerful static and dynamic analysis capabilities, while MobSF is known for its ease of use and comprehensive reporting. The choice of tool often depends on factors such as budget, existing infrastructure, and the specific security needs of the application.
Key Considerations When Choosing an Automated Mobile App Security Testing Tool, Mobile application security testing continues upward trajectory
Selecting the right automation tool is crucial for effective MAST. Several key factors should be considered before making a decision.
- Ease of Use and Integration: The tool should seamlessly integrate with existing development workflows and be intuitive enough for developers and security testers to use effectively, regardless of their technical expertise.
- Testing Capabilities: Consider the types of vulnerabilities the tool can detect. Does it support static, dynamic, and interactive analysis? Does it cover the specific security concerns relevant to your application?
- Reporting and Analysis: The tool should provide clear, concise reports that accurately identify and prioritize vulnerabilities. Detailed analysis features are crucial for understanding the root causes of identified issues.
- Support and Documentation: Robust support and comprehensive documentation are essential for troubleshooting issues and maximizing the tool’s effectiveness. A responsive support team can significantly reduce downtime and ensure efficient problem resolution.
- Cost and Licensing: Evaluate the cost of the tool, considering both initial investment and ongoing maintenance costs. Open-source tools offer a cost-effective solution, but may require more technical expertise to set up and maintain.
Future Trends in Mobile Application Security Testing
The mobile app landscape is constantly evolving, driven by technological advancements and shifting user expectations. This dynamic environment necessitates a proactive approach to mobile application security testing, pushing the field towards innovative methodologies and tools. The future of mobile app security testing will be shaped by increased automation, the integration of AI and ML, and a heightened focus on regulatory compliance.
The coming years will see a significant transformation in how we approach securing mobile applications. This shift will be fueled by the increasing sophistication of cyber threats and the growing reliance on mobile devices for sensitive transactions and data storage.
Advancements in Mobile App Security Testing Technologies
We can expect to see significant advancements in static and dynamic analysis techniques, leveraging more powerful algorithms and leveraging the cloud for scalable testing. Automated tools will become increasingly sophisticated, capable of identifying a wider range of vulnerabilities with greater accuracy and speed. For instance, the use of symbolic execution, a technique that explores all possible execution paths of an application, will become more prevalent, enabling the detection of subtle and hard-to-find flaws.
Furthermore, the development of more robust fuzzing techniques will allow for more thorough testing of application inputs, uncovering vulnerabilities that traditional methods might miss.
The Impact of Artificial Intelligence and Machine Learning
AI and ML will play a crucial role in enhancing the effectiveness and efficiency of mobile app security testing. ML algorithms can be trained to identify patterns and anomalies in application behavior, flagging potential vulnerabilities that might be missed by human analysts. AI-powered tools can automate tasks such as vulnerability prioritization, allowing security teams to focus their efforts on the most critical risks.
For example, an ML model could be trained on a dataset of known vulnerabilities to identify similar patterns in new applications, significantly reducing the time and resources required for manual analysis. This predictive capability will also lead to more proactive security measures, identifying potential vulnerabilities before they can be exploited.
Evolving Mobile App Security Regulations and Compliance Requirements
The regulatory landscape surrounding mobile app security is constantly evolving. Governments and industry bodies are implementing stricter regulations to protect user data and ensure the security of mobile applications. Compliance with regulations like GDPR, CCPA, and HIPAA will become increasingly critical for businesses developing and deploying mobile applications. This will necessitate the adoption of more rigorous security testing practices and the implementation of robust security controls throughout the software development lifecycle.
For example, companies handling sensitive health information will need to demonstrate compliance with HIPAA regulations through rigorous security testing and documentation.
A Future Mobile Application Security Testing Landscape
Imagine a future where mobile app security testing is fully automated and integrated into the CI/CD pipeline. A centralized dashboard displays a comprehensive view of the security posture of all mobile applications, providing real-time insights into vulnerabilities and risks. AI-powered tools automatically identify and prioritize vulnerabilities, suggesting remediation strategies. Security testing is no longer a separate phase but an integral part of the development process, ensuring that security is built into applications from the ground up.
The dashboard would display a heatmap showing the risk level of each application, categorized by severity and type of vulnerability. Color-coded icons would represent different security testing stages, from static analysis to penetration testing, with progress bars indicating completion status. This comprehensive view allows developers and security teams to quickly identify and address critical vulnerabilities, reducing the time and resources required for remediation.
Conclusive Thoughts
Securing mobile applications isn’t just a trend; it’s a necessity. As we’ve seen, the risks are real and the consequences can be devastating. However, by understanding the different testing methods, implementing secure coding practices, and staying ahead of emerging threats, we can significantly improve the security posture of our mobile apps. The upward trajectory of mobile app security testing is a positive sign, indicating a growing awareness of the importance of protecting user data and maintaining trust.
Let’s continue to work together to make the digital world a safer place, one app at a time!
Top FAQs
What’s the difference between SAST and DAST?
SAST (Static Application Security Testing) analyzes code without actually running the application, identifying vulnerabilities in the source code. DAST (Dynamic Application Security Testing) tests the running application, identifying vulnerabilities in its runtime behavior.
How much does mobile app security testing cost?
The cost varies widely depending on the app’s complexity, the scope of testing, and the chosen testing methodology. Expect to pay anywhere from a few hundred to tens of thousands of dollars.
Is mobile app security testing mandatory?
While not always legally mandated, it’s highly recommended, especially for apps handling sensitive user data. Failure to implement adequate security measures can lead to significant financial and reputational damage.
How often should I test my mobile app for security vulnerabilities?
Regular testing is crucial. The frequency depends on factors like the app’s complexity, update frequency, and the sensitivity of the data it handles. Consider testing during development, before each release, and periodically throughout the app’s lifecycle.