More Flexibility for VOB Element Protection
More flexibility for VOB element protection – it’s a game-changer, isn’t it? We’re all familiar with the struggle of securing valuable digital assets. Current methods often fall short, leaving our VOB elements vulnerable. This post dives deep into why we need more adaptable protection strategies, exploring innovative approaches and considering the impact on security and performance. Get ready to rethink how you safeguard your digital treasures!
We’ll unpack the limitations of traditional VOB element protection, examining various methods and their effectiveness. Then, we’ll explore the exciting possibilities of more flexible solutions, outlining practical strategies and addressing potential challenges. We’ll even peek into the future, looking at emerging technologies that could revolutionize VOB element security.
Defining “VOB Element Protection” and its Current Limitations: More Flexibility For Vob Element Protection
VOB element protection, in the context of software configuration management and version control systems, refers to the mechanisms and strategies employed to safeguard the integrity and security of individual elements within a Version Object Base (VOB). A VOB acts as a central repository for all versions of files and other objects within a project. Effective protection ensures that unauthorized modifications, accidental deletions, or malicious attacks cannot compromise the integrity of the VOB’s contents, maintaining the reliability and traceability of the development process.The fundamental goal of VOB element protection is to prevent corruption or unauthorized alteration of project assets.
This is crucial for maintaining a consistent and reliable development history, enabling accurate tracking of changes and facilitating efficient collaboration among team members. Without robust protection, the entire project’s history and integrity could be jeopardized, leading to significant development setbacks and potential security breaches.
Current Methods for VOB Element Protection
Several methods are currently used to protect VOB elements. These methods range from access control mechanisms to version control functionalities and data integrity checks. The effectiveness of each method varies depending on the specific context and the nature of the threats being addressed.
- Access Control Lists (ACLs): ACLs restrict access to specific VOB elements based on user roles and permissions. This prevents unauthorized users from modifying or deleting critical files. For example, a developer might only have write access to their assigned modules, while a project manager might have read-only access to the entire VOB.
- Version Control Mechanisms: Version control systems inherently provide a level of protection by tracking changes and allowing for rollback to previous versions. This safeguards against accidental or malicious alterations. If a critical file is corrupted, a previous, known-good version can be restored.
- Data Integrity Checks: Hashing algorithms and checksums are used to verify the integrity of VOB elements. Any unauthorized modification will result in a mismatch between the stored checksum and the calculated checksum, alerting administrators to potential problems. This is a crucial method for detecting silent data corruption.
- Auditing and Logging: Detailed logs of all VOB access and modifications are maintained, providing a trail for auditing purposes. This allows for investigation of suspicious activities and identification of the source of any security breaches. A comprehensive audit trail is essential for compliance and accountability.
Limitations of Existing VOB Element Protection Methods
Despite the existence of these methods, several limitations hinder the complete protection of VOB elements. These limitations often arise from the complex nature of collaborative development environments and the ever-evolving landscape of cyber threats.
- Insider Threats: ACLs and other access controls are ineffective against malicious insiders who have legitimate access to the VOB. A disgruntled employee with sufficient privileges could still cause significant damage.
- Sophisticated Attacks: Advanced attacks, such as zero-day exploits or sophisticated malware, can bypass standard security measures. These attacks may exploit vulnerabilities in the version control system itself or in the underlying operating system.
- Accidental Data Corruption: While version control allows for rollback, it doesn’t entirely prevent accidental data corruption. For instance, a developer might inadvertently overwrite a critical file with an incorrect version.
- Lack of Granular Control: Existing methods may lack the granularity needed to protect specific sections or components within a larger file. This can make it difficult to isolate and protect sensitive information embedded within a larger document.
Comparative Effectiveness of Protection Strategies
The effectiveness of different VOB element protection strategies varies significantly depending on the specific threat model and the environment. For instance, ACLs are highly effective against unauthorized access but offer little protection against insider threats. Data integrity checks are excellent for detecting data corruption but are not a preventative measure. A robust strategy typically involves a layered approach, combining multiple methods to mitigate various risks.
For example, a combination of strong ACLs, version control, data integrity checks, and regular security audits provides a more comprehensive level of protection than any single method alone. The optimal strategy must be tailored to the specific needs and risk profile of each project.
Exploring the Need for More Flexibility
The current VOB element protection system, while functional, suffers from a rigidity that hinders efficient collaboration and project management in dynamic environments. A more flexible approach is needed to accommodate the evolving needs of modern software development and version control. This increased flexibility would streamline workflows and ultimately improve productivity.The demand for greater flexibility in VOB element protection stems from the limitations of the existing system in handling complex project structures and diverse team collaboration models.
The current constraints often lead to unnecessary restrictions on access, slowing down development cycles and potentially increasing the risk of errors. A more adaptable system would allow for granular control, tailoring protection levels to specific needs and contexts.
Situations Requiring Enhanced Flexibility
Several scenarios highlight the critical need for more flexible VOB element protection. Imagine a large-scale software project with multiple teams working concurrently on different modules. The current system might struggle to manage the intricate access permissions required for seamless collaboration, potentially leading to conflicts or delays. Another example is the need for temporary access grants for external consultants or contractors.
The existing system’s inflexibility might make it difficult to provide timely and controlled access to specific VOB elements. Finally, consider the scenario of rapid prototyping and iterative development. The current system might hinder agile methodologies by making it difficult to quickly adjust protection levels as project requirements evolve.
Benefits of Increased Flexibility in VOB Element Protection
Increased flexibility offers several key advantages. First, it improves team collaboration by enabling granular control over access permissions. Teams can work more efficiently without unnecessary restrictions. Second, it enhances security by allowing for more precise control over sensitive data, reducing the risk of unauthorized access. Third, it simplifies project management by streamlining workflows and reducing administrative overhead associated with managing access rights.
Fourth, it promotes agility by allowing for quick adjustments to protection levels as project requirements change. Finally, it facilitates better compliance with industry regulations and best practices.
Challenges in Implementing Flexible Protection Mechanisms
Implementing more flexible protection mechanisms presents several challenges. One major challenge is designing a system that is both flexible and secure. The system must be robust enough to prevent unauthorized access while still allowing for granular control over permissions. Another challenge is ensuring the system is user-friendly and easy to manage, even with complex protection schemes. The complexity of managing a more flexible system could potentially increase the risk of human error.
Finally, there is the challenge of integrating the new system with existing infrastructure and workflows, which may require significant effort and resources.
Hypothetical Scenario Demonstrating Enhanced Flexibility
Consider a scenario where a software development team is working on a new mobile application. The application consists of three modules: user interface, backend logic, and database. Each module has a dedicated team. With enhanced flexibility, the UI team only has access to the UI module’s VOB elements, the backend team only to the backend module’s, and so on.
However, the lead developer needs access to all modules for oversight. The enhanced system allows for this granular control, granting the lead developer access to all modules while maintaining restricted access for other team members. This prevents accidental modification of other modules while allowing for effective oversight and coordination. This level of control is difficult to achieve with the existing system.
Methods for Achieving Greater Flexibility
Improving the flexibility of VOB element protection requires a multifaceted approach, balancing security needs with the practical demands of collaborative development. We need solutions that allow for granular control over access and permissions, while minimizing administrative overhead and potential vulnerabilities. The following methods offer different avenues to achieve this goal.
Several approaches exist to enhance the flexibility of VOB element protection, each with its own strengths and weaknesses. These range from simple configuration changes within existing version control systems to the implementation of more sophisticated access control mechanisms. The optimal solution will depend on the specific needs and security requirements of the project.
Access Control Lists (ACLs) and Granular Permissions, More flexibility for vob element protection
Implementing fine-grained access control using ACLs allows for precise control over who can access and modify specific VOB elements. This method offers a significant improvement over simpler, all-or-nothing protection schemes. Instead of granting broad access to entire VOBs, ACLs enable administrators to assign specific read, write, and delete permissions to individual users or groups on a per-element basis.
Role-Based Access Control (RBAC)
RBAC offers a more structured approach to access control, defining roles (e.g., developer, tester, manager) with predefined permissions. Users are then assigned to these roles, inheriting the associated permissions. This simplifies administration and ensures consistency in access control across the VOB. Changes to permissions only need to be made at the role level, rather than individually for each user.
Attribute-Based Access Control (ABAC)
ABAC represents a more advanced approach, employing policies based on attributes of both the user (e.g., department, location, clearance level) and the VOB element (e.g., sensitivity level, project affiliation). This allows for highly dynamic and context-aware access control, adapting to changing needs and security requirements. ABAC can be more complex to implement but offers the greatest flexibility and granularity.
Comparison of Methods
The following table compares the three methods based on cost, implementation complexity, and security:
| Method | Cost | Implementation Complexity | Security |
|---|---|---|---|
| ACLs | Low | Low to Medium | Medium |
| RBAC | Medium | Medium | High |
| ABAC | High | High | Very High |
Step-by-Step Implementation of ACLs
Implementing ACLs for enhanced VOB element protection involves several key steps. This example focuses on a ClearCase environment, but the general principles apply to other VOB systems.
- Identify VOB elements requiring specific protection: Determine which files and directories need granular access control. This might involve categorizing elements based on sensitivity (e.g., confidential, public).
- Define user groups and permissions: Create appropriate user groups (e.g., “developers,” “testers,” “managers”) and assign specific permissions (read, write, execute) to each group for the identified VOB elements.
- Configure ACLs using ClearCase commands: Utilize ClearCase’s `chgrp` and `chmod` commands (or equivalent GUI tools) to set the group ownership and permissions for each VOB element. This involves specifying the group name and the desired permissions for each group.
- Test and verify access control: After implementing the ACLs, thoroughly test the access control mechanisms to ensure they function as expected. Verify that users can only access and modify the VOB elements permitted by their assigned permissions.
- Regularly review and update ACLs: Access control needs to be periodically reviewed and updated to reflect changes in project roles and security requirements. This is crucial to maintain the effectiveness of the protection mechanisms.
Impact on Security and Performance
Increased flexibility in VOB element protection presents a double-edged sword. While offering enhanced control and usability, it also introduces potential security vulnerabilities and performance implications that require careful consideration and proactive mitigation strategies. The balance between enhanced functionality and robust security is crucial for maintaining the integrity and reliability of the system.The primary concern revolves around the potential for misconfiguration.
Greater flexibility means more options, and with more options comes a greater chance of human error. Incorrectly configured access controls or insufficiently protected elements could expose sensitive data or compromise system stability. This necessitates a robust training program for administrators and clear, concise documentation outlining best practices and security considerations for each configuration option.
Security Implications of Increased Flexibility
Expanding the options for VOB element protection inherently increases the attack surface. A more complex system with numerous configurable settings offers more opportunities for attackers to exploit vulnerabilities. For example, a poorly implemented custom access control list (ACL) could inadvertently grant unauthorized access to sensitive data. Similarly, an overly permissive configuration might leave critical system components vulnerable to malicious modification or deletion.
This necessitates a thorough security audit and penetration testing following any significant changes to the VOB protection system.
Performance Considerations and Resource Consumption
Increased flexibility in VOB protection might lead to increased system overhead. More granular control mechanisms, such as fine-grained access control lists or sophisticated encryption schemes, can consume more processing power and memory resources. This increased resource consumption could potentially impact the overall performance of the system, especially under heavy load. Careful performance testing and optimization are essential to ensure that the enhanced flexibility does not negatively impact the responsiveness and stability of the system.
Load balancing and resource allocation strategies should be implemented to mitigate potential performance bottlenecks.
Potential Vulnerabilities and Mitigation Strategies
A comprehensive approach to mitigating the risks associated with increased flexibility involves a multi-layered security strategy. This includes not only technical safeguards but also robust administrative procedures and security awareness training.
- Vulnerability: Misconfiguration of access controls leading to unauthorized access. Mitigation: Implement strict access control policies, regular security audits, and comprehensive training for administrators on secure configuration practices.
- Vulnerability: Exploitation of vulnerabilities in custom access control mechanisms. Mitigation: Thoroughly test and validate all custom implementations before deployment, utilize established security frameworks and standards, and conduct regular penetration testing.
- Vulnerability: Denial-of-service (DoS) attacks targeting the VOB protection system. Mitigation: Implement robust rate limiting and intrusion detection/prevention systems to mitigate DoS attacks. Ensure sufficient system resources are allocated to handle peak loads.
- Vulnerability: Data breaches due to insufficient encryption or key management. Mitigation: Utilize strong encryption algorithms and implement secure key management practices, including regular key rotation and secure storage.
Future Directions and Technological Advancements
The quest for more flexible VOB element protection is intrinsically linked to the rapid evolution of cryptographic techniques and distributed ledger technologies. The limitations of current methods, primarily centered around key management and scalability, can be significantly mitigated by embracing these advancements. This section explores how emerging technologies can reshape the landscape of VOB protection, paving the way for more robust and adaptable security measures.The integration of advanced cryptographic techniques, such as homomorphic encryption and post-quantum cryptography, offers a pathway to enhanced flexibility.
These methods allow computations to be performed on encrypted data without decryption, thereby significantly reducing the risk of exposure during processing. Post-quantum cryptography, in particular, provides a hedge against the threat of quantum computing, which could potentially break many currently used encryption algorithms. Furthermore, the inherent scalability of blockchain technology can address the limitations imposed by centralized key management systems.
Distributed ledger technology provides a transparent and tamper-proof record of access permissions and modifications, offering improved accountability and auditability.
Homomorphic Encryption and Post-Quantum Cryptography Enhancements
Homomorphic encryption allows for computations to be performed directly on encrypted data, preserving confidentiality even during processing. This is particularly relevant for VOB elements requiring complex analysis or manipulation while maintaining security. For instance, imagine a scenario where financial data within a VOB needs to be analyzed for fraud detection. Homomorphic encryption would allow this analysis to be performed on the encrypted data, eliminating the need to decrypt it and exposing it to potential breaches.
Post-quantum cryptography offers resilience against attacks from future quantum computers, ensuring long-term security of VOB elements. This is crucial for protecting sensitive information over extended periods, as the threat of quantum computing becomes more prominent. Implementing these cryptographic advancements would necessitate significant changes in system architecture, requiring the integration of specialized libraries and potentially hardware acceleration for efficient processing.
Blockchain Integration for Enhanced Access Control
Blockchain technology can revolutionize access control for VOB elements. By recording all access attempts, modifications, and permissions on a distributed ledger, blockchain provides an immutable audit trail, enhancing transparency and accountability. This eliminates single points of failure inherent in centralized systems, making the system more resilient to attacks. Consider a scenario where multiple users need to collaborate on a VOB.
Blockchain can manage access permissions dynamically, ensuring only authorized users can access specific elements at designated times. This would involve a system architecture where each VOB element is linked to a unique entry on the blockchain, detailing its access controls and version history. The system would then utilize smart contracts to automatically enforce these access rules, eliminating the need for manual intervention.
Visual Representation of Integrated System
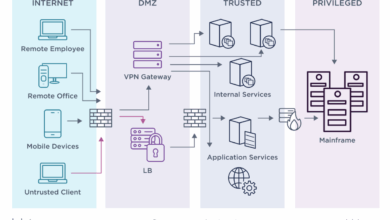
Imagine a diagram showing a central VOB database. Around this database, three concentric circles represent different layers of security. The innermost circle depicts the core VOB elements, protected by homomorphic encryption and post-quantum cryptography. The middle circle illustrates the access control layer, managed by a blockchain network, recording all access attempts and modifications. The outermost circle represents the user interface and external systems interacting with the VOB, which are secured through standard authentication and authorization protocols.
The arrows connecting the circles depict data flow, showing how encrypted data is processed within the inner layer, access is controlled and logged by the blockchain in the middle layer, and external interactions are managed by the outer layer. This visual representation highlights the layered security approach provided by the integration of these advanced technologies, creating a robust and flexible system for VOB element protection.
Wrap-Up
So, there you have it – a journey into the world of enhanced VOB element protection! We’ve uncovered the need for more flexible strategies, explored various methods, and considered the implications for security and performance. The future of VOB security is bright, with emerging technologies promising even more robust and adaptable protection. By embracing these advancements and adopting a proactive approach, we can significantly improve the safety and integrity of our valuable digital assets.
Let’s build a future where VOB elements are truly secure!
Commonly Asked Questions
What exactly are VOB elements?
VOB elements refer to the valuable components within a Version Object Base (VOB), a repository commonly used in software configuration management. These elements can include source code, documents, and other crucial project assets.
What are the common risks associated with inadequate VOB protection?
Inadequate protection can lead to data breaches, unauthorized access, modification, or deletion of crucial project assets, resulting in significant financial losses, project delays, and reputational damage.
How does increased flexibility affect performance?
The performance impact depends on the chosen method. Some approaches might introduce minor overhead, while others could be optimized for minimal impact. Careful planning and implementation are key.
Are there any open-source tools to help with more flexible VOB protection?
The availability of open-source tools varies. Researching tools specializing in access control and encryption within the context of version control systems is recommended.