
Myths Small Businesses Arent Cybercrime Targets
Myths small businesses not targets – Myths: Small Businesses Aren’t Cybercrime Targets – that’s the dangerous misconception we’re tackling today. Think small businesses are immune to cyberattacks? Think again! This isn’t just about big corporations; the reality is that small businesses are increasingly becoming prime targets for cybercriminals, facing significant financial and reputational risks. We’ll explore why this is happening, the devastating consequences of data breaches, and most importantly, the practical steps you can take to protect your business.
We’ll delve into the common cyber threats small businesses face, from phishing scams and ransomware attacks to malware infections. We’ll also uncover why small businesses are attractive targets – often due to limited resources and less sophisticated security measures. This isn’t about fear-mongering; it’s about empowering you with the knowledge and strategies to safeguard your business and its valuable data.
Debunking the Myth: Small Businesses are Not Cybercrime Targets
It’s a common misconception that only large corporations with vast amounts of data are targets for cybercriminals. The reality is far more alarming: small businesses are increasingly becoming prime targets for cyberattacks. Their often-limited security resources and perceived vulnerability make them easy prey for malicious actors seeking quick financial gains or access to sensitive information.
Prevalence of Cyberattacks Targeting Small Businesses
Small businesses represent a significant portion of cybercrime victims. They lack the robust security infrastructure and dedicated cybersecurity teams that larger companies possess, making them attractive targets for various cyber threats. Statistics from organizations like the FBI and the Small Business Administration consistently highlight the disproportionate number of cyberattacks targeting small businesses compared to their representation in the overall economy.
This isn’t simply anecdotal; data shows a clear trend of increased attacks and significant financial losses.
Common Cyber Threats Faced by Small Businesses
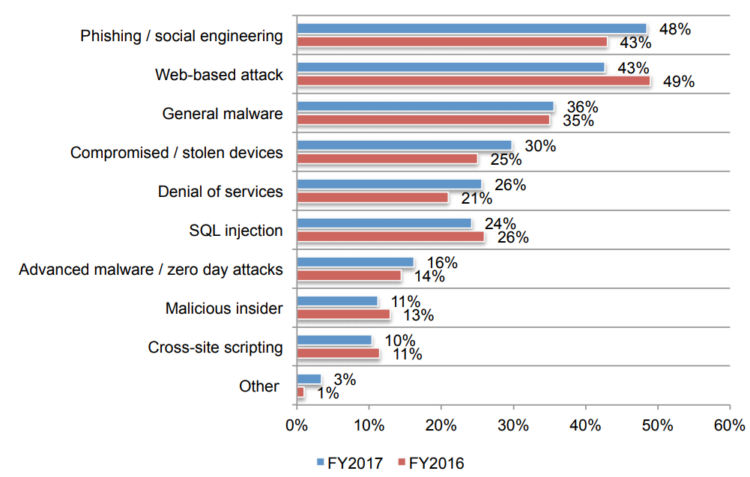
Small businesses face a wide array of cyber threats. Phishing attacks, where malicious emails or messages trick employees into revealing sensitive information like login credentials or financial details, remain incredibly common. Ransomware attacks, which encrypt a business’s data and demand a ransom for its release, are another significant threat, often crippling operations and leading to substantial financial losses. Malware, encompassing viruses, worms, and Trojans, can infect systems, steal data, and disrupt business operations.
Other threats include denial-of-service attacks (DoS), which overwhelm a website or network, making it inaccessible to legitimate users, and data breaches, which can expose sensitive customer and business information.
Financial and Reputational Consequences of Cyberattacks
The consequences of a cyberattack on a small business can be devastating. The direct financial costs can include ransom payments, data recovery expenses, legal fees, and the cost of replacing damaged or stolen equipment. Beyond the immediate financial impact, there are significant indirect costs such as lost productivity, business interruption, and damage to reputation. A single successful attack can severely impact a small business’s ability to operate, potentially leading to bankruptcy.
The loss of customer trust and damaged reputation can also be long-lasting, making it difficult to regain business. Many small businesses simply do not recover from a major cyberattack.
Resource and Vulnerability Comparison: Small Businesses vs. Large Corporations
| Characteristic | Small Businesses | Large Corporations |
|---|---|---|
| IT Budget | Limited; often prioritized for other operational needs. | Substantial; dedicated to cybersecurity infrastructure and personnel. |
| Cybersecurity Personnel | Often lacking dedicated cybersecurity staff; reliance on external consultants or outsourced services may be unreliable or insufficient. | Dedicated cybersecurity teams, including analysts, engineers, and incident responders. |
| Security Infrastructure | Basic security measures, potentially outdated or improperly configured. | Robust and multi-layered security infrastructure, including firewalls, intrusion detection systems, and data loss prevention tools. |
| Vulnerability | High due to limited resources and potentially weaker security practices. | Lower due to substantial investment in security measures and expertise. However, still vulnerable to sophisticated attacks. |
Why Small Businesses are Attractive Targets
Small businesses, despite their size, are increasingly becoming prime targets for cybercriminals. This isn’t because they hold more valuable data than larger corporations, but rather because they often present easier, less-defended pathways for attacks. The perception that small businesses are “too small” to be targeted is a dangerous misconception that leaves them vulnerable to significant financial and reputational damage.Cybercriminals are driven by profit, and small businesses, often lacking robust security measures, represent a low-hanging fruit.
Their limited resources, both financial and human, mean they’re less likely to have dedicated IT staff or advanced security systems in place. This makes them significantly more susceptible to various cyberattacks, ranging from simple phishing scams to sophisticated ransomware deployments. The relative ease of breaching their defenses, combined with the potential for significant financial gains, makes them highly attractive targets.
Limited Security Resources and Sophisticated Defenses, Myths small businesses not targets
Small businesses often lack the financial resources to invest in comprehensive cybersecurity solutions. This includes specialized software, regular security audits, employee training, and incident response planning. They may rely on outdated systems or free, less secure software, leaving them exposed to known vulnerabilities. Furthermore, the absence of dedicated IT personnel means that security is often a secondary concern, handled by already overburdened staff who may lack the necessary expertise.
This lack of proactive security measures significantly increases the likelihood of a successful cyberattack.
Cyberattack Success Rates Against Small Businesses
While precise statistics vary depending on the source and methodology, numerous studies consistently show a high success rate of cyberattacks against small businesses. For example, a study by the Ponemon Institute indicated that 60% of small businesses experience a cyberattack annually, and a significant percentage of those attacks result in substantial financial losses. The relatively low cost of targeting small businesses, coupled with the high probability of success, fuels the ongoing trend of cybercriminals focusing their efforts on this demographic.
This is not just a hypothetical threat; it’s a reality impacting countless businesses daily.
Methods Used to Target Small Businesses
Cybercriminals employ a range of methods to target small businesses, often leveraging the lack of sophisticated defenses. Social engineering attacks, such as phishing emails or phone calls, remain highly effective. These attacks manipulate employees into divulging sensitive information or clicking on malicious links, granting attackers access to systems. Exploiting known software vulnerabilities is another common tactic. Out-of-date software and operating systems are particularly vulnerable to attacks that exploit security flaws.
Ransomware attacks, which encrypt a business’s data and demand a ransom for its release, are also a significant threat, often crippling operations until the ransom is paid. These attacks often target the business’s critical data, such as customer information or financial records.
Common Misconceptions About Cybersecurity
It’s crucial to address the common misconceptions that contribute to the vulnerability of small businesses. These misconceptions often prevent businesses from taking the necessary steps to protect themselves.
- “It won’t happen to me”: This is a dangerous assumption. Cybercriminals target businesses of all sizes, and no business is immune.
- “We don’t have anything worth stealing”: Even small businesses hold valuable data, including customer information, financial records, and intellectual property, which can be highly valuable to criminals.
- “Cybersecurity is too expensive”: While comprehensive security can be costly, there are many affordable options and free resources available to help small businesses improve their security posture.
- “Our employees are too smart to fall for phishing scams”: Phishing attacks are sophisticated and can deceive even experienced users. Regular employee training is essential.
- “We’re too small to be a target”: Small businesses are attractive targets due to their often weaker security measures and limited resources.
The Impact of Data Breaches on Small Businesses
Data breaches aren’t just a problem for massive corporations; they pose a significant threat to small businesses, often with devastating consequences. The financial impact, reputational damage, and legal liabilities can be crippling, pushing many small businesses to the brink of closure. Understanding the potential ramifications is crucial for effective preventative measures and a robust response plan.
Types of Sensitive Data Held by Small Businesses
Small businesses, despite their size, often hold a wealth of sensitive data valuable to cybercriminals. This includes customer data (names, addresses, credit card information, and purchase history), employee information (social security numbers, payroll data, and health records), intellectual property (trade secrets, designs, and client lists), and financial records (bank account details and tax information). The specific type and value of data will vary depending on the industry and business model, but the potential for exploitation is undeniable.
A small bakery might hold less sensitive data than a medical practice, but a breach of either could have significant consequences.
Legal and Regulatory Ramifications of Data Breaches
Data breaches trigger significant legal and regulatory repercussions for small businesses. Regulations like the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) in the United States mandate strict data protection measures and impose hefty fines for non-compliance following a breach. These regulations require businesses to notify affected individuals and regulatory bodies within specific timeframes, implement robust security measures, and demonstrate compliance.
Failure to comply can lead to substantial fines, legal battles, and lasting reputational damage. For example, a small business in California failing to comply with CCPA notification requirements could face fines up to $7,500 per violation. Similarly, GDPR violations can result in fines up to €20 million or 4% of annual global turnover, whichever is greater.
Recovery Costs Associated with Data Breaches
The cost of recovering from a data breach is disproportionately higher for small businesses compared to larger enterprises. Larger companies often have dedicated cybersecurity teams, insurance policies, and resources to mitigate the impact. Small businesses, however, often lack these resources, leaving them vulnerable to crippling financial losses. Costs include legal fees, regulatory fines, credit monitoring services for affected customers, public relations efforts to repair reputational damage, and the cost of system recovery and data restoration.
A Ponemon Institute study estimated that the average cost of a data breach for small and medium-sized businesses (SMBs) is significantly higher than for larger organizations, often exceeding their financial capacity.
Responding to a Data Breach: A Scenario
Imagine “Cozy Corner Cafe,” a small bakery, experiences a data breach exposing customer credit card information. Their immediate actions should include:
1. Containing the Breach
Immediately isolate affected systems to prevent further data exfiltration.
2. Identifying the Extent of the Breach
Determine precisely what data was compromised and how many customers are affected.
3. Notifying Affected Individuals
Comply with all relevant data breach notification laws (GDPR, CCPA, etc.) and inform customers promptly.
4. Notifying Law Enforcement
Report the breach to appropriate law enforcement agencies.
5. Engaging Cybersecurity Experts
Consult with cybersecurity professionals to investigate the breach, assess vulnerabilities, and implement remedial measures.
6. Implementing Remedial Measures
Strengthen security protocols, patch vulnerabilities, and enhance data protection measures.
7. Cooperating with Regulatory Bodies
Fully cooperate with investigations and regulatory inquiries.
8. Offering Credit Monitoring
Provide affected customers with credit monitoring services to mitigate potential financial harm.
Effective Cybersecurity Strategies for Small Businesses: Myths Small Businesses Not Targets

Protecting your small business from cyber threats doesn’t require a massive budget or a dedicated IT team. By implementing a few key strategies, you can significantly reduce your risk and safeguard your valuable data and reputation. This section Artikels practical, affordable measures to bolster your cybersecurity posture.
Practical and Affordable Cybersecurity Measures
Implementing strong cybersecurity doesn’t necessitate breaking the bank. A multi-layered approach, combining several cost-effective measures, provides robust protection. This includes prioritizing essential security practices that offer a high return on investment in terms of reduced risk.
- Strong Passwords and Multi-Factor Authentication (MFA): Enforce the use of complex, unique passwords for all accounts and enable MFA wherever possible. MFA adds an extra layer of security, requiring a second form of verification (like a code sent to your phone) in addition to your password.
- Regular Software Updates: Keep all software, including operating systems, applications, and antivirus programs, updated with the latest security patches. Outdated software is a prime target for hackers.
- Firewall Protection: A firewall acts as a barrier between your network and the internet, blocking unauthorized access attempts. Most routers include built-in firewalls, but consider upgrading to a more robust solution if needed.
- Antivirus and Anti-malware Software: Install and regularly update reputable antivirus and anti-malware software on all devices. These tools can detect and remove malicious software before it causes damage.
- Secure Wi-Fi Networks: Use strong passwords for your Wi-Fi network and enable WPA2 or WPA3 encryption. Avoid using public Wi-Fi for sensitive transactions.
- Employee Access Control: Implement the principle of least privilege; grant employees only the access they need to perform their jobs. Regularly review and update user permissions.
Employee Cybersecurity Training and Awareness
Educated employees are your first line of defense against cyber threats. Regular training programs significantly reduce the likelihood of successful phishing attacks and other social engineering techniques.
Effective training should cover common threats like phishing emails, malicious links, and social engineering tactics. Regular simulated phishing campaigns can help assess employee awareness and reinforce training. It’s crucial to emphasize the importance of reporting suspicious activity immediately. This includes providing clear reporting channels and ensuring employees feel comfortable reporting without fear of reprisal.
Data Backups and Disaster Recovery Planning
Data loss can cripple a small business. Regular data backups and a comprehensive disaster recovery plan are essential for business continuity.
Backups should be performed regularly and stored securely, ideally offsite. Consider using cloud-based backup solutions for added security and redundancy. A disaster recovery plan should Artikel procedures for restoring data and systems in the event of a disaster, including hardware failure, natural disasters, or cyberattacks. This plan should be tested regularly to ensure its effectiveness.
Developing a Comprehensive Cybersecurity Policy
A well-defined cybersecurity policy provides a framework for all cybersecurity efforts. It Artikels acceptable use of company resources, data protection procedures, and incident response protocols.
- Define Scope and Objectives: Clearly state the policy’s purpose and who it applies to (employees, contractors, etc.).
- Password and Access Control Policies: Specify password complexity requirements, account lockout policies, and procedures for managing user access.
- Data Security Policies: Artikel procedures for handling sensitive data, including encryption, access controls, and data disposal.
- Acceptable Use Policy: Define acceptable use of company computers, networks, and internet access. This includes restrictions on personal use and downloading of unauthorized software.
- Incident Response Plan: Detail steps to take in the event of a security incident, including reporting procedures, investigation methods, and communication protocols.
- Training and Awareness: Artikel the frequency and content of employee cybersecurity training.
- Review and Update: The policy should be reviewed and updated regularly to reflect changes in technology and threats.
Illustrating the Vulnerability

Let’s examine a hypothetical scenario to understand how easily a small business can fall victim to a cyberattack. This case study will highlight the vulnerabilities, the attack methodology, and the preventative measures that could have been implemented.The fictional “Cozy Corner Cafe,” a small, family-run bakery and coffee shop, relied heavily on a single, aging computer system for all its operations: point-of-sale (POS) transactions, customer database management, and online ordering.
They lacked a robust cybersecurity strategy, believing their small size made them an unlikely target. This proved to be a fatal miscalculation.
The Cyberattack on Cozy Corner Cafe
The attack began with a phishing email seemingly from their internet service provider. The email warned of an imminent service interruption unless immediate action was taken by clicking a link to “verify” their account. The link led to a cleverly disguised website mirroring their ISP’s login page. Unsuspecting, the cafe owner entered their login credentials, unknowingly handing over the keys to their entire digital kingdom.The attackers quickly gained access to the cafe’s computer system.
Their first step was to install malware, a sophisticated piece of software designed to steal data and disable security measures. This malware allowed the attackers to exfiltrate sensitive customer data, including names, addresses, credit card information, and email addresses. Simultaneously, they encrypted the cafe’s files, rendering them inaccessible. A ransom note appeared on the cafe’s computer screen, demanding a significant sum of cryptocurrency in exchange for decryption and the promise not to release the stolen customer data.The impact was immediate and devastating.
The cafe was forced to shut down operations while they attempted to deal with the attack. They lost revenue during the downtime, incurred significant costs in data recovery and cybersecurity remediation, and faced potential legal liabilities due to the data breach. The damage to their reputation, though difficult to quantify, was substantial. Customers lost trust, and the cafe’s online presence suffered.
Preventive Measures
Cozy Corner Cafe could have avoided this disaster by implementing several key security measures. Firstly, employee cybersecurity training on recognizing and avoiding phishing scams is crucial. Regular updates on security awareness are essential to combat evolving threats. Secondly, multi-factor authentication (MFA) would have added an extra layer of security, making it significantly harder for attackers to access the system even if they obtained login credentials.
Thirdly, robust antivirus and anti-malware software, regularly updated, should have been installed and actively monitored. Finally, regular data backups stored offline would have minimized the impact of data encryption, allowing for quicker recovery. Investing in a firewall and intrusion detection system would also have significantly improved their overall security posture.
Visual Representation of the Attack
Imagine a diagram. At the top, a phishing email is depicted, its subject line and link cleverly disguised. An arrow points from the email to the cafe’s computer. Inside the computer, a visual representation of the malware infiltrating the system, like a virus spreading through cells. Another arrow points from the infected computer to a cloud icon representing the stolen data being exfiltrated.
A padlock icon on the computer screen is shown turning red, indicating the encryption of files. Finally, a banner appears on the screen showing the ransom demand. The overall image communicates a clear progression of the attack, from initial intrusion to the final crippling effect. The diagram visually represents the vulnerability and the devastating consequences of inadequate cybersecurity measures.
Ultimate Conclusion
So, are small businesses safe from cyberattacks? Absolutely not. The myth that they are immune is costing businesses dearly. But the good news is that effective cybersecurity doesn’t have to be expensive or overly complex. By understanding the threats, implementing practical security measures, and educating your employees, you can significantly reduce your risk.
Taking proactive steps today will protect your business’s future, saving you from the potentially devastating consequences of a cyberattack. Don’t wait until it’s too late; start building a robust cybersecurity strategy now.
Answers to Common Questions
What is the most common type of cyberattack against small businesses?
Phishing attacks are incredibly common, often targeting employees with deceptive emails or websites to steal login credentials or sensitive information.
How much does it cost to recover from a data breach?
The cost varies greatly depending on the size of the business and the severity of the breach, but it can easily reach tens of thousands, even hundreds of thousands of dollars.
Do I need expensive software to protect my business?
No, many affordable and effective security measures exist, including strong passwords, regular software updates, and employee training.
What should I do if I suspect a data breach?
Immediately isolate affected systems, contact law enforcement and relevant authorities, and engage cybersecurity professionals to assess the damage and assist with recovery.




