Nemty Ransomware Hackers Exploit Dead Staff Credentials
Nemty ransomware hackers using dead staff credentials sets the stage for a chilling exploration of cybercrime’s dark underbelly. This isn’t your typical ransomware story; it delves into the disturbing reality of attackers exploiting the vulnerabilities created by deceased employees’ lingering digital footprints. We’ll uncover how these credentials are acquired, the methods used to breach systems, and the devastating consequences for victims.
Prepare for a deep dive into a disturbing yet crucial aspect of modern cybersecurity threats.
The Nemty ransomware attacks we’ll discuss are particularly insidious because they leverage information that’s often overlooked in standard security protocols. The acquisition of credentials from deceased employees isn’t always a sophisticated hacking operation; sometimes, it’s as simple as failing to properly revoke access after an employee passes away. We’ll examine various attack vectors, from phishing campaigns targeting grieving families to exploiting outdated access control lists.
The impact on businesses isn’t just financial; it includes significant reputational damage and legal repercussions. We’ll explore mitigation strategies and best practices to help you protect your organization from similar attacks.
Nemty Ransomware
Nemty ransomware, active from approximately 2019 to 2020, was a particularly nasty piece of malware known for its sophisticated encryption techniques and relatively efficient operational lifecycle. Unlike some ransomware strains that rely on brute-force methods, Nemty demonstrated a level of technical proficiency that made it a significant threat. While its activity has subsided, understanding its mechanics remains relevant for cybersecurity professionals and researchers.
Nemty Ransomware Attack Lifecycle
The typical Nemty ransomware attack followed a fairly standard lifecycle, beginning with initial infection, often through phishing emails containing malicious attachments or links leading to compromised websites. Once executed, the malware would proceed to scan the infected system, identifying valuable files for encryption. This selection process often targeted specific file types known to hold significant value to the victim, such as documents, databases, and media files.
Following encryption, a ransom note would be displayed, demanding payment for decryption. Finally, the encrypted files would be rendered inaccessible until the ransom was paid. The attackers’ operational speed and efficiency contributed to the malware’s success.
Nemty Ransomware Encryption Methods
Nemty utilized AES-256 encryption, a robust and widely used symmetric encryption algorithm. This meant that the same key was used to encrypt and decrypt the files. The encryption process itself was performed locally on the victim’s machine, making it difficult to decrypt the files without the decryption key. The attackers generated a unique encryption key for each victim, further enhancing the effectiveness of the encryption.
The strength of AES-256 and the unique key generation made decryption without the key extremely challenging.
Nemty Ransomware Ransom Payment Methods
The attackers behind Nemty ransomware typically demanded payment in Bitcoin, a cryptocurrency known for its relative anonymity and untraceability. This choice allowed the attackers to receive payments without leaving a readily traceable audit trail. The ransom amount varied depending on factors such as the size and perceived value of the encrypted data. Instructions for payment were usually provided within the ransom note displayed after encryption.
The use of Bitcoin underscored the attackers’ efforts to remain anonymous and operate outside the reach of traditional law enforcement.
Nemty Ransomware Variants
The following table summarizes some known Nemty variants and their key differences. Note that detailed information on all variants is limited due to the nature of underground ransomware operations.
| Variant | Distinguishing Features | Encryption Method | Ransom Note Differences |
|---|---|---|---|
| Nemty v1 | Initial release, simpler ransom note | AES-256 | Generic ransom demand |
| Nemty v2 | Improved stealth capabilities, more targeted file selection | AES-256 | More personalized ransom demand, potentially including victim-specific information |
| Nemty v3 (if any) | Further refinements to evade detection, potentially including new evasion techniques | AES-256 | Potentially includes updated contact information or payment methods |
| Other Variants | Minor variations in ransom note wording or obfuscation techniques | AES-256 | Slight differences in messaging or contact information |
Compromised Credentials
The use of deceased employees’ credentials in cyberattacks represents a particularly insidious form of credential theft. Unlike traditional methods targeting active employees, this tactic exploits the inherent vulnerabilities created by the death of an individual, leveraging a lack of immediate account deactivation and the emotional complexities surrounding bereavement. The acquisition of these credentials relies on a combination of opportunistic methods and targeted social engineering, often exploiting the trust and access associated with the deceased individual’s former role within the organization.The methods used to obtain credentials from deceased employees are often less technologically sophisticated than other hacking techniques, relying instead on exploiting human vulnerabilities and lax security practices.
This makes these attacks particularly effective, as they often go undetected for extended periods.
Methods of Credential Acquisition
The acquisition of credentials from deceased employees often involves exploiting vulnerabilities in organizational security procedures and leveraging human interactions. These methods are frequently opportunistic, capitalizing on the window of time between an employee’s death and the subsequent account deactivation. For example, a malicious actor might discover an employee’s password through a poorly secured password manager or by accessing their personal computer, especially if left unattended for an extended period.
Another common method is simply attempting to log in with common passwords or easily guessable variations of the deceased employee’s name, birthdate, or other personally identifiable information. The success of these methods often hinges on the organization’s failure to implement robust account management and password security policies.
Social Engineering Techniques
Social engineering plays a crucial role in obtaining credentials from deceased employees. Attackers often target grieving family members or HR departments, leveraging their emotional vulnerability or bureaucratic processes. For example, a sophisticated phishing attack might impersonate an IT department employee requesting access to the deceased’s account for “legacy data retrieval” or “account closure,” thereby tricking the recipient into revealing password information or granting access.
Seriously, the Nemty ransomware hackers using dead staff credentials? It highlights the urgent need for robust security practices. To build truly secure systems, we need to embrace modern development approaches, like those discussed in this great article on domino app dev the low code and pro code future , which emphasizes secure coding practices from the ground up.
Ultimately, preventing these kinds of attacks relies on a multi-pronged approach, including better credential management and secure application design.
Phishing Attacks Targeting HR and Family
Phishing attacks are particularly effective in this context. Imagine a scenario where an attacker sends an email to the HR department, impersonating a family member requesting access to the deceased employee’s retirement information. The email might contain a link to a fake login page, designed to capture credentials. Similarly, an attacker could target family members directly, posing as a representative from the deceased’s employer, claiming to need access to their online accounts to process final payments or benefits.
The urgency and emotional distress associated with the death create an environment ripe for exploitation.
Insider Threats and Credential Access
Insider threats can also play a significant role. A disgruntled employee or someone with access to sensitive information within the company could exploit the situation. This insider might already possess knowledge of the deceased employee’s login credentials or might have access to systems containing that information. This access could be leveraged after the death, providing a much easier route to obtaining the credentials than external social engineering attempts.
The insider might also be motivated by personal gain, revenge, or simply opportunistic access to sensitive company data.
Exploitation of Dead Staff Credentials: Nemty Ransomware Hackers Using Dead Staff Credentials
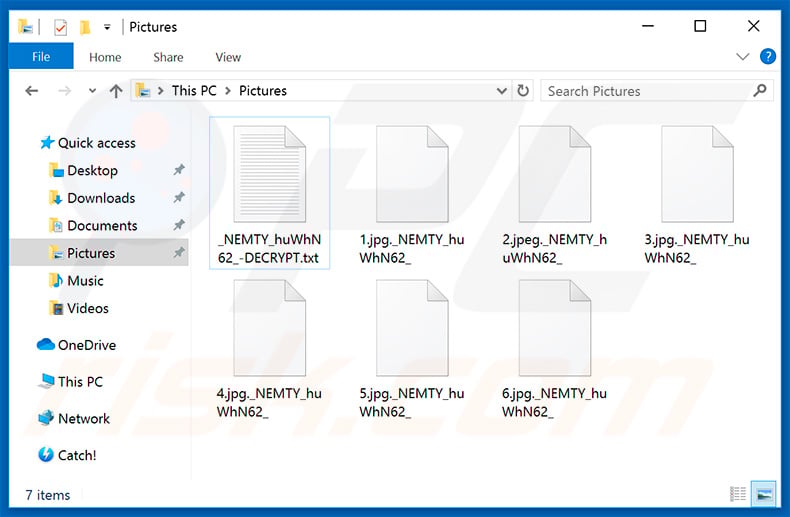
The Nemty ransomware attacks leveraging deceased employees’ credentials highlight a critical vulnerability in many organizations’ security posture. These attacks demonstrate the severe consequences of inadequate account management and the persistent threat posed by compromised accounts, even after an employee’s departure. The attackers likely employed a multi-stage process to exploit these credentials, combining technical expertise with a degree of social engineering or insider knowledge.The attackers likely followed a systematic approach to exploit these compromised credentials.
First, they would obtain the credentials themselves, potentially through phishing attacks targeting HR or IT departments, or by exploiting weaknesses in password management systems. Once obtained, the credentials would then be tested against various network resources.
Initial Access Methods
Gaining initial access is the first step in a ransomware attack. The Nemty attackers likely used the compromised credentials to log into various systems, starting with less privileged accounts. This could involve attempting to log into email accounts, shared network drives, or even less secure remote access portals. Success here grants them a foothold within the network. For example, a low-privilege account with access to a shared folder containing sensitive documents could provide a pathway to more critical systems.
The attackers might also explore the possibility of leveraging the credentials to access VPN gateways or other remote access points. Successful access at this stage could allow the attackers to move laterally within the network.
Exploiting Outdated Access Control Lists
Outdated access control lists (ACLs) represent a significant vulnerability. Even if an account is deactivated within an organization’s systems, if the ACLs haven’t been updated to reflect this change, the associated credentials may still grant access to sensitive data or systems. For instance, a former employee’s account might still have permissions to access a server containing financial records or customer databases.
The attackers could exploit this to gain unauthorized access and deploy the ransomware. Imagine a scenario where a former IT administrator’s account retains elevated privileges to critical servers; this would be a prime target for attackers.
Privilege Escalation Techniques
After gaining initial access, the attackers would likely attempt privilege escalation to gain more control over the network. This involves exploiting vulnerabilities within the system to elevate their access level from a low-privilege account to an administrator or domain administrator account. This could involve exploiting known vulnerabilities in the operating system or applications, using readily available exploit tools, or even leveraging weak passwords on other accounts accessible from the initial compromised account.
A successful privilege escalation could give the attackers the ability to install ransomware across the entire network, encrypting critical data and disrupting business operations. For example, the attackers might use a known vulnerability in a specific application to gain administrative privileges on a server, then use those privileges to spread the ransomware.
Impact and Consequences of the Nemty Ransomware Attack
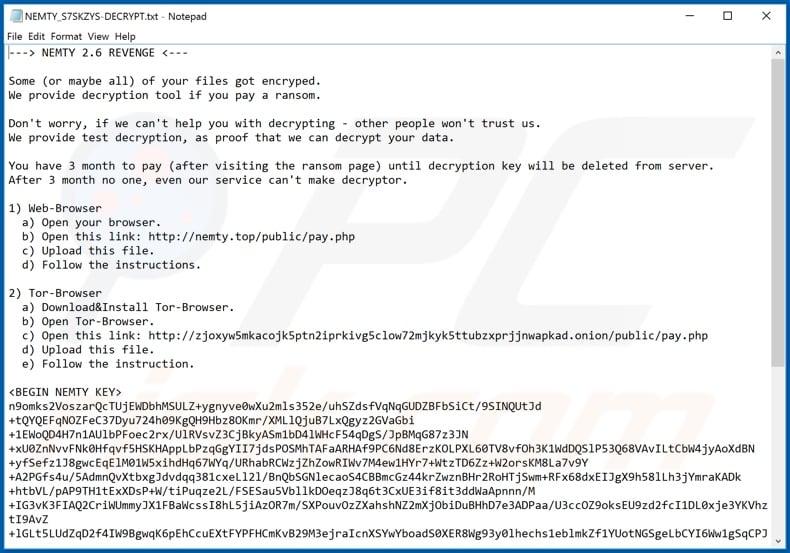
The exploitation of deceased employees’ credentials to deploy Nemty ransomware can have devastating consequences for an organization, far exceeding the immediate cost of the ransom itself. The ripple effect extends across financial, reputational, legal, and operational domains, significantly impacting the long-term health and stability of the business. Understanding these multifaceted consequences is crucial for effective mitigation and recovery planning.The financial impact of a Nemty ransomware attack is multifaceted and often underestimated.
Direct costs include the ransom payment (if made), the cost of incident response services (forensics, legal counsel, data recovery), and the cost of system restoration and business interruption. Indirect costs, however, can be far more substantial and long-lasting. These include lost productivity, the cost of regaining customer trust, potential fines and legal fees, and the expense of implementing improved security measures.
For example, a small business might face tens of thousands of dollars in immediate costs, while a larger corporation could see losses in the millions, depending on the extent of the data breach and business downtime.
Financial Losses
The financial burden of a Nemty ransomware attack extends beyond the immediate ransom demand. Consider the cost of recovering encrypted data, which might involve purchasing specialized software or engaging expensive data recovery specialists. Furthermore, lost revenue due to operational downtime can significantly impact profitability, especially for businesses that rely heavily on their IT infrastructure. The longer the systems remain offline, the greater the financial strain.
Legal fees associated with investigations and potential lawsuits add to the mounting financial pressure. Finally, the cost of enhancing security measures to prevent future attacks, including employee training, security audits, and updated software, represents a significant long-term financial commitment. A realistic budget should encompass all these factors.
Reputational Damage
A successful ransomware attack, particularly one exploiting the credentials of deceased employees, severely damages an organization’s reputation. News of a data breach, especially one highlighting security vulnerabilities, can quickly spread through news outlets and social media, damaging public trust and impacting customer loyalty. Potential clients might hesitate to engage with a company perceived as having weak security practices, leading to lost business opportunities.
This reputational damage can take years to overcome, even with proactive efforts to rebuild trust. The negative publicity can also affect employee morale and recruitment efforts. For instance, a healthcare provider experiencing a data breach might lose patients’ trust, impacting its long-term viability.
Legal and Regulatory Ramifications
Data breaches trigger significant legal and regulatory ramifications, particularly regarding compliance with regulations like GDPR (General Data Protection Regulation) or CCPA (California Consumer Privacy Act). Failure to comply with these regulations can result in substantial fines and penalties. Organizations may also face lawsuits from affected individuals or business partners, adding to the financial and legal burdens. Investigations by regulatory bodies are common, potentially leading to further scrutiny and penalties.
The legal complexities associated with data breaches necessitate expert legal counsel to navigate the intricate landscape of regulations and potential liabilities.
Business Disruptions
The operational disruption caused by a Nemty ransomware attack can be extensive and far-reaching.
- System downtime and data unavailability: Critical business operations may be halted, leading to significant productivity losses.
- Interruption of customer services: Inability to access customer data or provide services can damage customer relationships and lead to revenue loss.
- Supply chain disruptions: Disruptions to internal systems can affect communication and collaboration with suppliers and partners.
- Loss of intellectual property: Compromised systems may expose valuable intellectual property, giving competitors an unfair advantage.
- Decreased employee productivity: Employees may spend considerable time dealing with the aftermath of the attack, diverting resources from their primary tasks.
Mitigation Strategies and Best Practices
The Nemty ransomware attack, exploiting the credentials of deceased employees, highlights a critical vulnerability in many organizations’ security posture. Preventing similar incidents requires a multi-layered approach encompassing robust password management, proactive credential revocation procedures, and a strong commitment to regular security assessments. This section Artikels key strategies and best practices to mitigate this specific risk and improve overall cybersecurity.
Robust Password Management Policy, Nemty ransomware hackers using dead staff credentials
A strong password policy is the first line of defense against credential reuse and unauthorized access. This policy should mandate the use of complex, unique passwords for each account, encouraging the use of password managers to assist employees. Regular password changes, enforced at least every 90 days, are crucial, alongside a policy prohibiting the reuse of passwords across different platforms.
The policy should also clearly Artikel acceptable password complexity requirements, including minimum length, character types (uppercase, lowercase, numbers, symbols), and the prohibition of easily guessable passwords such as names, dates, or common phrases. Consider implementing password complexity checks during the account creation process to ensure compliance from the outset. Regular employee training on password hygiene and security best practices is also essential.
Timely Credential Revocation Upon Employee Death
A well-defined and immediately actionable procedure for revoking credentials upon employee death is paramount. This process should involve a designated team or individual responsible for swiftly deactivating all accounts associated with the deceased employee across all systems and platforms. This includes not only network accounts but also access to cloud services, software applications, and any other relevant systems. The procedure should be clearly documented and readily accessible to all relevant personnel, including HR, IT, and security teams.
Consider using automated systems or scripts to facilitate rapid account deactivation to minimize the window of vulnerability. This procedure should be tested regularly through simulations to ensure its effectiveness and identify potential bottlenecks. For example, a clear chain of command for notification and execution, combined with pre-defined account disabling scripts, would significantly reduce the time it takes to revoke access.
Implementation of Multi-Factor Authentication
Multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide multiple forms of authentication before gaining access. This significantly reduces the risk of unauthorized access even if credentials are compromised. Implementing MFA across all critical systems and applications is a vital step in enhancing security. Common MFA methods include one-time passwords (OTPs) via authenticator apps, security keys, or biometric authentication.
The choice of MFA method should depend on the sensitivity of the data and the level of security required. For instance, systems holding highly sensitive financial or personal data should utilize stronger MFA methods like security keys or biometric authentication. Employee training on the proper use and management of MFA methods is crucial for successful implementation.
Regular Security Audits and Vulnerability Assessments
Regular security audits and vulnerability assessments are essential for identifying and addressing potential weaknesses in an organization’s security infrastructure. These assessments should be conducted on a regular basis, ideally at least annually, or more frequently for critical systems. They should encompass both technical and procedural aspects of security, including network security, application security, and data security. Vulnerability scanning tools can automate the identification of security vulnerabilities, while penetration testing simulates real-world attacks to identify exploitable weaknesses.
The results of these assessments should be used to develop and implement remediation plans to address identified vulnerabilities promptly. Regular review of security logs and incident response plans is also critical for detecting and responding to potential security breaches.
Forensic Analysis and Response

A Nemty ransomware attack, particularly one leveraging compromised credentials of deceased employees, necessitates a thorough and swift forensic investigation to understand the attack’s scope, identify vulnerabilities, and implement effective remediation strategies. This process involves meticulous data collection, analysis, and ultimately, the restoration of affected systems and data.
Steps Involved in a Forensic Investigation
The forensic investigation of a Nemty ransomware attack follows a structured approach. First, the incident response team must secure the affected systems to prevent further damage and data exfiltration. This includes isolating infected machines from the network and disabling any active ransomware processes. Next, a comprehensive data acquisition process begins, capturing images of hard drives and volatile memory. This data is then analyzed to identify the entry point of the attack, the methods used for lateral movement within the network, and the specific encryption techniques employed by Nemty.
Finally, a detailed report is compiled, documenting the findings, outlining the remediation steps, and offering recommendations to prevent future attacks. This report is crucial for both internal review and potential legal proceedings.
Key Data Sources for Analysis
Several key data sources are essential for a comprehensive forensic analysis. Network logs provide valuable information about the attacker’s activity, including IP addresses, timestamps, and communication patterns. System logs from infected machines offer insights into the ransomware’s execution, file modifications, and registry changes. Memory dumps can reveal running processes, network connections, and potentially even the ransomware’s code itself.
Finally, the ransomware’s encrypted files themselves can be analyzed to understand the encryption algorithm and potentially aid in decryption efforts. Analyzing these data sources in conjunction allows investigators to piece together a complete picture of the attack.
Incident Response Procedures Checklist
| Phase | Action | Responsible Party | Timeline |
|---|---|---|---|
| Preparation | Develop and test incident response plan. Establish communication protocols. | IT Security Team | Ongoing |
| Identification | Detect and confirm ransomware infection. Isolate affected systems. | Security Operations Center (SOC) | Within 1 hour |
| Containment | Prevent further spread of ransomware. Disable compromised accounts. | SOC, IT Admins | Within 2 hours |
| Eradication | Remove ransomware from infected systems. Restore from backups. | IT Admins, Forensic Team | Within 24-48 hours |
| Recovery | Restore data and systems to operational state. | IT Admins, Data Recovery Specialists | Ongoing |
| Post-Incident Activity | Conduct thorough forensic analysis. Review security controls. Update incident response plan. | Forensic Team, IT Security Team | Ongoing |
Data Recovery and System Restoration Methods
Data recovery and system restoration methods depend on the extent of the encryption and the availability of backups. If backups are available and up-to-date, restoring from backups is the quickest and most reliable method. However, if backups are unavailable or compromised, data recovery may involve specialized tools that can attempt to decrypt the files. In cases where decryption is not possible, the affected data may be lost.
System restoration often involves reinstalling the operating system and necessary applications, followed by the restoration of recovered data. In some cases, rebuilding affected systems from scratch might be necessary. The choice of method will depend on factors like the severity of the attack, the availability of resources, and the business’s recovery time objectives (RTO).
Illustrative Scenario
Imagine “Green Valley Farms,” a mid-sized agricultural company, relying heavily on its aging, but seemingly secure, internal network. Their IT infrastructure, while functional, lacked the robust security measures needed to withstand a sophisticated ransomware attack. Unbeknownst to them, the compromised credentials of a deceased accountant, Martha Jenkins, held the key to their downfall. Martha, a long-time employee, had access to a significant portion of the company’s network, including financial records, operational data, and even some aspects of their automated irrigation systems.The attack began subtly.
A phishing email, cleverly disguised as a routine payroll update, was sent to several Green Valley Farms employees. While most deleted the email, one unsuspecting employee, unaware of Martha’s passing, clicked the link, unknowingly granting the attackers access to the network using Martha’s still-active credentials. This initial breach went undetected for several weeks, a testament to the company’s limited monitoring capabilities.
Initial Compromise and Lateral Movement
The attackers, leveraging Martha’s elevated privileges, moved laterally across the network with ease. They initially mapped the network’s structure, identifying high-value targets like the financial database and the control systems for the farm’s irrigation and harvesting equipment. They carefully avoided triggering any alerts, demonstrating a high level of sophistication in their approach. The attackers then proceeded to encrypt sensitive data, including customer records, financial statements, and crucial operational documents.
The encryption process was swift and thorough, rendering the data inaccessible without the decryption key.
Ransomware Deployment and Impact
Once the encryption process was complete, the Nemty ransomware’s signature message appeared on every affected system. The message demanded a substantial ransom in Bitcoin for the decryption key, threatening to release the stolen data publicly if the payment wasn’t made within a specific timeframe. The impact on Green Valley Farms was immediate and devastating. Their operations ground to a halt as they lost access to critical systems.
Financial reporting became impossible, and their ability to manage their crops was severely hampered. The potential for reputational damage and legal repercussions loomed large.
Response and Recovery
Green Valley Farms immediately contacted law enforcement and hired a cybersecurity firm specializing in ransomware attacks. The firm’s forensic analysis confirmed the use of compromised credentials and identified the Nemty ransomware variant. While the company considered paying the ransom, they ultimately decided against it, fearing further repercussions and the lack of guarantee for data recovery. The recovery process was lengthy and expensive, involving rebuilding systems from backups, restoring data from offline copies, and implementing enhanced security measures.
The incident highlighted the critical need for regular security audits, employee training, and the prompt disabling of accounts upon employee termination or death. The attack served as a stark reminder of the potential damage caused by outdated security practices and the critical importance of proper credential management.
Closing Notes
The unsettling truth revealed by the Nemty ransomware attacks using dead staff credentials highlights a critical gap in many organizations’ cybersecurity strategies. It’s a stark reminder that comprehensive security isn’t just about firewalls and antivirus software; it’s about anticipating the unexpected and proactively addressing vulnerabilities that might seem obscure. By understanding the methods used by these attackers, and by implementing the robust security protocols discussed, businesses can significantly reduce their risk of falling victim to this particularly cruel form of cybercrime.
Protecting your organization goes beyond simply securing active employees; it requires a proactive approach to managing the digital legacy of those who are no longer with us.
FAQ
What makes Nemty ransomware particularly dangerous?
Nemty’s sophisticated encryption methods and the attackers’ focus on quick exfiltration of data make recovery difficult and costly. The use of stolen credentials from deceased employees adds a unique and often overlooked vulnerability.
How can I tell if my organization is vulnerable to this type of attack?
Conduct a thorough review of your access control lists, ensuring timely revocation of credentials upon employee termination or death. Assess your password management policies and consider implementing multi-factor authentication.
What is the best way to prevent this type of attack?
Implement robust password management policies, including multi-factor authentication and regular password changes. Develop a clear procedure for revoking access upon employee death or termination. Conduct regular security audits and vulnerability assessments.
What should I do if I suspect my organization has been targeted?
Immediately isolate affected systems, contact law enforcement and cybersecurity experts, and initiate your incident response plan. Do not pay the ransom unless explicitly advised by law enforcement.