New Report Sheds Light on Software Supply Chain Risks
New report sheds light on software supply chain risks – a phrase that should send shivers down the spine of any tech professional! We’re increasingly reliant on interconnected software, and this report highlights just how vulnerable that system is. From sneaky vulnerabilities hidden in open-source libraries to the ever-present threat of compromised third-party vendors, the risks are real and far-reaching.
This isn’t just a technical issue; it impacts businesses, consumers, and even national security. Let’s dive into the details and explore what we can do to protect ourselves.
The report meticulously dissects the various types of vulnerabilities, offering real-world examples to illustrate the devastating consequences of supply chain attacks. It then delves into the crucial role of open-source software, weighing its benefits against the inherent security challenges. A significant portion focuses on effective third-party risk management, providing a framework for assessing and mitigating risks from external vendors.
The report concludes with a look at best practices, emerging technologies, and the evolving regulatory landscape, leaving us with a clear understanding of the path forward.
Software Supply Chain Vulnerabilities
The software supply chain, a complex network of developers, libraries, and tools, is increasingly vulnerable to attacks. Understanding these vulnerabilities is crucial for businesses and consumers alike, as compromises can lead to significant financial losses, data breaches, and reputational damage. This section delves into the common types of vulnerabilities, real-world examples, and their impact.
Common Software Supply Chain Vulnerabilities
Software supply chains are susceptible to various attack vectors. These vulnerabilities often stem from weaknesses in the code itself, insecure development practices, or compromised components within the chain. Common types include malicious code injections, dependency confusion, typosquatting, and supply chain attacks targeting open-source components. These attacks can manifest in various ways, leading to significant consequences.
Real-World Incidents Illustrating Supply Chain Compromises
Several high-profile incidents highlight the severity of supply chain vulnerabilities. For example, the SolarWinds attack in 2020 involved the compromise of the SolarWinds Orion software, allowing attackers to infiltrate numerous organizations. This attack demonstrated the far-reaching consequences of a compromised software update, affecting thousands of businesses and government agencies. Another example is the widespread use of malicious npm packages, showcasing how seemingly benign components can harbor malicious code.
These incidents underscore the need for robust security measures throughout the entire software supply chain.
Impact of Vulnerabilities on Businesses and Consumers
The impact of software supply chain vulnerabilities extends far beyond simple inconvenience. For businesses, these vulnerabilities can result in significant financial losses due to downtime, remediation costs, and legal repercussions. Data breaches can expose sensitive customer information, leading to reputational damage and potential fines. Consumers, on the other hand, may experience identity theft, financial fraud, or the compromise of personal devices.
The ripple effects of a single compromised component can be vast and devastating.
Comparison of Vulnerability Types, Severity, and Mitigation Strategies
| Vulnerability Type | Severity | Potential Mitigation Strategies | Example |
|---|---|---|---|
| Malicious Code Injection | High | Secure coding practices, code signing, vulnerability scanning | Insertion of malware into a legitimate software package. |
| Dependency Confusion | Medium to High | Strict dependency management, verifying package origins, using private repositories | Attacker publishes a malicious package with the same name as a legitimate dependency, tricking the system into using it. |
| Typosquatting | Medium | Careful dependency specification, automated dependency checks | Attacker registers a package with a slightly misspelled name of a legitimate package, hoping developers will make a typo. |
| Open-Source Component Compromise | High | Regular security audits, using trusted open-source repositories, SBOM generation and analysis | Compromise of a widely used open-source library, allowing attackers to gain access to systems relying on it. |
The Role of Open Source Software
Open-source software (OSS) has become the backbone of modern software development, woven into the fabric of almost every application we use daily. From the libraries powering our web browsers to the operating systems running our smartphones, the reliance on OSS components is undeniable and continues to grow exponentially. This pervasive use, however, introduces a complex set of security considerations within the software supply chain.The increased reliance on open-source components stems from several factors.
Firstly, the collaborative nature of OSS development often leads to faster innovation and bug fixes compared to proprietary software. Secondly, the readily available source code allows for greater transparency and scrutiny, theoretically enhancing security. Finally, the cost-effectiveness of using free and open-source software is a significant driver for businesses of all sizes.
Benefits and Drawbacks of Using Open-Source Software from a Supply Chain Security Perspective
The benefits of using OSS in terms of security are often touted, but they come with significant caveats. The transparency of open-source code allows for community-based security audits and vulnerability discovery. This “many eyes” approach can lead to quicker identification and patching of security flaws compared to closed-source alternatives. However, the very openness that fosters this collaborative security review also exposes potential vulnerabilities to malicious actors.
A well-known vulnerability in a widely used OSS library can cascade across countless applications, creating a massive attack surface. The sheer volume of OSS components used in modern software also increases the complexity of managing and securing the entire supply chain.
Potential Risks Associated with Incorporating Open-Source Libraries Without Proper Vetting
Incorporating unvetted open-source libraries into a software project is akin to inviting uninvited guests into your house. Without proper due diligence, developers risk introducing malicious code, backdoors, or vulnerabilities that could compromise the entire system. These vulnerabilities might be intentionally inserted by malicious actors or simply overlooked flaws in poorly maintained libraries. A classic example is the inclusion of outdated or vulnerable libraries that have known exploits but haven’t been updated by the original maintainers.
This can lead to significant security breaches and data loss, as evidenced by numerous real-world incidents involving compromised open-source packages. For instance, the infamous “EventStream” incident demonstrated how a compromised package could be used to steal sensitive information from various applications.
Best Practices for Securely Managing Open-Source Components Within a Software Supply Chain
Securely managing open-source components requires a multi-faceted approach. This begins with meticulous selection and vetting of libraries, involving careful examination of the project’s history, community activity, and security track record. Utilizing reputable package managers and employing automated dependency analysis tools are crucial for identifying vulnerabilities and ensuring that all dependencies are up-to-date with security patches. Regular security audits, penetration testing, and incorporating software composition analysis (SCA) into the development lifecycle are also vital.
Furthermore, establishing a robust process for patching and updating open-source components is essential to mitigate the risk of known vulnerabilities. Finally, actively engaging with the open-source community, reporting vulnerabilities, and contributing to security improvements strengthens the overall security posture of the entire ecosystem.
Third-Party Risk Management
Managing risk from third-party vendors is crucial in today’s interconnected software landscape. A single vulnerability in a component from an external supplier can compromise the security and stability of an entire system, leading to significant financial and reputational damage. Effective third-party risk management involves a proactive and multi-faceted approach that integrates security considerations throughout the software development lifecycle.Third-party risk management approaches vary widely depending on an organization’s size, industry, and risk tolerance.
Some organizations opt for a largely manual process relying on questionnaires and due diligence, while others leverage automated tools and platforms to streamline the assessment and monitoring of their third-party vendors. A common approach involves a tiered system where vendors are categorized based on their criticality to the organization, with higher-risk vendors receiving more rigorous scrutiny. Regardless of the specific approach, effective third-party risk management requires a consistent and documented process that ensures all vendors meet acceptable security standards.
Vendor Risk Assessment Framework
A robust framework for assessing and mitigating third-party software supplier risks should encompass several key stages. Firstly, a comprehensive identification of all third-party vendors and the software components they provide is necessary. This includes mapping dependencies and understanding the role each vendor plays within the system. Secondly, a risk assessment should be conducted using a standardized methodology, considering factors such as the vendor’s security posture, location, compliance certifications, and the criticality of the software component they provide.
This assessment should also incorporate threat modeling to identify potential vulnerabilities and attack vectors. Finally, mitigation strategies should be developed and implemented, which might include contractual obligations, security audits, penetration testing, and ongoing monitoring. For example, a company might require a vendor to implement multi-factor authentication or undergo regular security assessments. Regular reassessment and updates to the framework are also essential to adapt to evolving threats and changes in the vendor landscape.
Key Questions for Potential Third-Party Vendors
Before engaging with a third-party vendor, it’s vital to ask specific questions to assess their security practices. These questions should cover aspects such as their security policies, incident response plans, and vulnerability management processes. For example, inquiring about their software development lifecycle (SDLC) security practices, penetration testing frequency, and use of secure coding practices is crucial. Further, understanding their approach to data protection, including data encryption and access controls, is vital, especially if they handle sensitive data.
Finally, it’s essential to ascertain their compliance with relevant industry regulations and standards, such as ISO 27001 or SOC 2. These questions help determine if the vendor’s security posture aligns with the organization’s risk tolerance and security requirements.
Integrating Third-Party Risk Management into the SDLC, New report sheds light on software supply chain risks
Effective third-party risk management shouldn’t be a standalone process; it must be seamlessly integrated into the software development lifecycle. This integration begins during the initial planning and design phases, where dependencies on third-party components are identified and assessed. During the development phase, security considerations should be factored into the integration process, and appropriate security testing should be conducted.
Throughout the deployment and maintenance phases, ongoing monitoring and vulnerability management should be in place to identify and address any emerging risks associated with the third-party components. This integrated approach ensures that security considerations are not an afterthought but rather an integral part of the entire software development process. For instance, automated security scanning tools can be integrated into the CI/CD pipeline to identify vulnerabilities in third-party components before deployment.
Security Best Practices and Mitigation Strategies
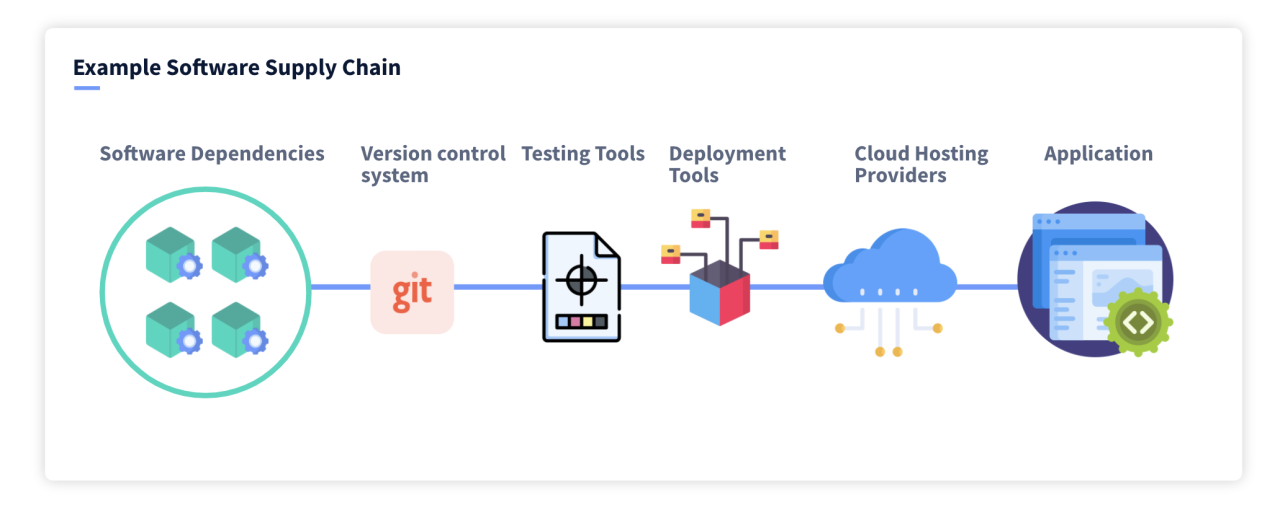
Securing the software supply chain requires a multi-faceted approach encompassing secure coding practices, robust tooling, and well-defined processes. Ignoring any one of these elements significantly increases the risk of vulnerabilities being introduced and exploited. This section details practical steps organizations can take to bolster their defenses and mitigate the inherent risks.
Secure Coding Practices
Secure coding is the foundation of a robust software supply chain. It involves writing code that is resistant to common vulnerabilities such as buffer overflows, SQL injection, and cross-site scripting (XSS). This requires developers to adopt a proactive mindset, incorporating security considerations throughout the entire software development lifecycle (SDLC). This isn’t just about avoiding obvious flaws; it’s about building in layers of defense to make exploitation significantly harder, even if a vulnerability is discovered.
Effective Security Tools and Technologies
Leveraging appropriate security tools and technologies is crucial for identifying and mitigating supply chain risks. Static and dynamic application security testing (SAST and DAST) tools can automatically scan code for vulnerabilities before and after deployment. Software Composition Analysis (SCA) tools help identify open-source components and their associated vulnerabilities within the software, enabling timely patching and remediation. Other tools, like container security scanners and vulnerability databases, play a crucial role in maintaining a secure environment.
For example, a widely used SCA tool might identify a specific version of a widely used library as having a known vulnerability, alerting developers to immediately upgrade to a patched version.
Software Bill of Materials (SBOM) Implementation
A Software Bill of Materials (SBOM) is a formal record containing details of all software components used in a product. This includes both open-source and proprietary components, their versions, and their licenses. A comprehensive SBOM facilitates vulnerability detection, facilitates license compliance, and improves traceability throughout the supply chain. Implementing a robust SBOM process requires standardized formats (like SPDX or CycloneDX) and integration with the organization’s CI/CD pipeline to ensure SBOMs are generated and updated automatically with each software build.
This allows for efficient tracking of changes and rapid identification of potential risks. Without a readily available and accurate SBOM, identifying the source of a vulnerability within a complex software system can be a time-consuming and challenging task.
Actionable Steps for Improved Software Supply Chain Security
Implementing effective security measures requires a concerted effort. Here are actionable steps organizations can take:
- Implement secure coding practices and training programs for developers.
- Integrate SAST and DAST tools into the SDLC.
- Utilize SCA tools to identify and manage open-source component vulnerabilities.
- Establish a robust SBOM process and utilize standardized formats.
- Regularly update and patch software components.
- Conduct regular security audits and penetration testing.
- Implement access control and least privilege principles.
- Establish a vulnerability disclosure program.
- Develop and maintain an incident response plan.
- Foster a culture of security awareness throughout the organization.
Impact and Future Trends
The escalating sophistication and frequency of software supply chain attacks underscore the urgent need to understand their far-reaching consequences and proactively adapt to emerging threats. The economic and reputational damage inflicted by these attacks can be catastrophic, impacting businesses of all sizes and sectors. Moreover, the increasing interconnectedness of our digital world means that a single compromised component can trigger a domino effect, leading to widespread disruption.The economic impact of software supply chain attacks is multifaceted.
Direct costs include remediation efforts, legal fees, and the loss of sensitive data. Indirect costs are equally significant, encompassing lost revenue due to downtime, damage to brand reputation, and the erosion of customer trust. For example, the SolarWinds attack in 2020, which compromised thousands of organizations worldwide, resulted in billions of dollars in losses and lasting reputational damage for the affected companies.
The reputational impact extends beyond immediate financial losses; it can severely impact future business opportunities and investor confidence.
Economic and Reputational Impact of Software Supply Chain Attacks
Software supply chain attacks can lead to significant financial losses through direct costs such as incident response, remediation, legal fees, and regulatory fines. Indirect costs include lost revenue due to business disruption, damage to brand reputation, and decreased customer trust. The reputational damage can be long-lasting, impacting future business opportunities and investor confidence. The severity of the impact is often proportional to the scale and scope of the attack, as well as the nature of the compromised data.
For instance, a data breach involving sensitive customer information can lead to hefty fines and lawsuits, severely impacting a company’s financial stability and public image. This necessitates proactive measures to mitigate such risks.
Emerging Technologies for Enhanced Software Supply Chain Security
Several emerging technologies hold the promise of strengthening software supply chain security. Blockchain technology, with its immutable ledger, can enhance transparency and traceability throughout the software development lifecycle. By recording every change and modification to the software code, blockchain creates an auditable trail that can help identify and prevent malicious tampering. Artificial intelligence (AI) is also playing an increasingly important role, enabling automated vulnerability detection and threat analysis.
AI-powered systems can analyze vast amounts of data to identify patterns and anomalies indicative of malicious activity, allowing for proactive threat mitigation. Furthermore, AI can assist in prioritizing vulnerabilities and automating security patching processes, reducing the window of vulnerability.
The Evolving Regulatory Landscape
Governments worldwide are recognizing the critical need for enhanced software supply chain security and are actively developing regulations to address the growing threat. These regulations often mandate increased transparency, stronger security practices, and robust vulnerability disclosure mechanisms. Compliance with these evolving regulations requires a proactive and comprehensive approach to security management. The increasing regulatory scrutiny is driving organizations to adopt more robust security practices, further incentivizing the adoption of new technologies and methodologies aimed at improving software supply chain security.
Failure to comply with these regulations can lead to significant financial penalties and reputational damage.
Visual Representation of Software Supply Chain Security Evolution (2013-2023)
Imagine a graph charting the evolution of software supply chain security over the past decade. The X-axis represents the years (2013-2023), and the Y-axis represents the level of sophistication and adoption of security practices. The initial years (2013-2016) show a relatively flat line, indicating limited awareness and adoption of robust security measures. A noticeable upward trend begins around 2017, reflecting the increasing awareness of supply chain vulnerabilities following high-profile attacks.
The line continues to rise sharply from 2020 onwards, coinciding with the increased regulatory scrutiny and the emergence of technologies like AI and blockchain. The graph would visually demonstrate the shift from a reactive to a more proactive and technologically advanced approach to securing software supply chains.
End of Discussion
The new report isn’t just a list of problems; it’s a roadmap to a more secure future. By understanding the vulnerabilities, implementing robust risk management strategies, and embracing emerging technologies, we can significantly strengthen our software supply chains. It’s a call to action, urging developers, businesses, and policymakers to prioritize security and work collaboratively to mitigate these significant risks.
The journey towards a more secure digital world starts with awareness, and this report provides the crucial first step.
FAQ Explained: New Report Sheds Light On Software Supply Chain Risks
What are some common examples of software supply chain attacks?
Examples include malicious code injected into open-source libraries, compromised third-party components, and supply chain disruptions caused by ransomware attacks.
How can I identify vulnerable open-source components?
Utilize vulnerability databases, regularly scan your dependencies, and employ static and dynamic analysis tools.
What is an SBOM and why is it important?
A Software Bill of Materials (SBOM) is a formal record of all software components in a system. It’s crucial for identifying and managing vulnerabilities within the software supply chain.
What role does AI play in improving software supply chain security?
AI can automate vulnerability detection, predict potential attacks, and enhance threat intelligence, improving overall security posture.