NHS Data Breach After Ransomware Attack on University of Manchester
NHS data breach after ransomware attack on University of Manchester: This chilling headline throws open the doors to a story of digital espionage, data vulnerability, and the urgent need for stronger cybersecurity measures. The attack, a sophisticated ransomware operation targeting the University of Manchester, unfortunately resulted in the exposure of sensitive NHS patient data, raising serious concerns about privacy, security, and the potential for widespread harm.
This post delves into the details of the incident, exploring the timeline, the impact, the response, and the critical lessons learned.
We’ll examine the University’s security protocols, both before and after the attack, comparing them to industry best practices and uncovering potential weaknesses. We’ll also discuss the legal and ethical implications of this breach, the public’s reaction, and the long-term consequences for trust in both the NHS and the University. Prepare to be informed, and perhaps a little unsettled, by the realities of modern cyber threats.
The University of Manchester Ransomware Attack

The University of Manchester, a renowned institution of higher learning, suffered a significant ransomware attack in late 2023. This incident highlighted the vulnerability of even large, well-resourced organizations to sophisticated cyber threats and the subsequent challenges in data recovery and operational continuity. The attack resulted in a data breach affecting sensitive information, underscoring the critical need for robust cybersecurity measures in the higher education sector.The incident serves as a stark reminder of the ever-evolving landscape of cyber threats and the importance of proactive security strategies.
Understanding the timeline, the ransomware used, and the university’s response is crucial for learning from this event and improving overall cybersecurity preparedness.
Timeline of the Ransomware Attack
The exact timeline of the University of Manchester ransomware attack wasn’t publicly released in complete detail, likely for security reasons. However, reports indicated that the initial breach occurred sometime in late 2023. The discovery of the attack followed a period of unusual system activity, possibly including slowed performance or access restrictions. Once the presence of ransomware was confirmed, the university likely initiated its incident response plan, involving internal IT teams and potentially external cybersecurity specialists.
The timeline from initial breach to public acknowledgment likely spanned several days or weeks, reflecting the complexity of investigation and containment efforts.
Ransomware Used and Capabilities
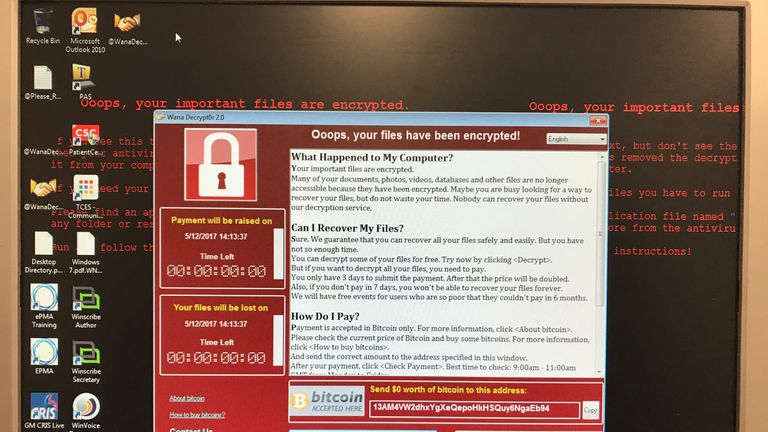
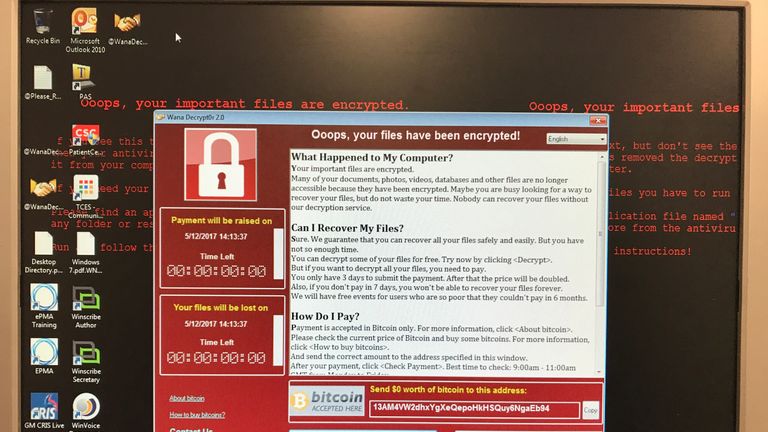
While the specific type of ransomware deployed in the University of Manchester attack wasn’t officially named, many ransomware variants share similar characteristics. These often include encryption of critical data files, rendering them inaccessible without a decryption key. Advanced ransomware strains may also exfiltrate data before encryption, creating a double extortion scenario where the threat actors demand payment to prevent the release of stolen information.
Such ransomware often targets servers and network infrastructure, potentially disrupting critical university operations like student record access, research data management, and administrative functions. The capabilities of the ransomware likely included data encryption, file deletion, and potentially data exfiltration.
University Response and Containment Measures
The University of Manchester’s initial response likely involved several key steps. These would have included isolating affected systems from the rest of the network to prevent further spread of the ransomware. This isolation might have involved shutting down affected servers or implementing network segmentation. The university would have also engaged in forensic analysis to determine the extent of the breach and identify the source of the attack.
Furthermore, they likely initiated communication with relevant authorities, including law enforcement and potentially the National Cyber Security Centre (NCSC), to report the incident and receive guidance. Containment efforts would have focused on preventing further data loss and restoring affected systems as quickly as possible.
Impact on NHS Data
The ransomware attack on the University of Manchester, while primarily targeting the university’s systems, unfortunately had significant repercussions for the NHS due to the university’s extensive collaborations in research and healthcare data management. The exact extent of the data breach is still being investigated, but initial reports suggest a concerning impact on sensitive patient information and vital research projects.
Understanding the nature and scale of this impact is crucial for assessing the risks and implementing appropriate mitigation strategies.The compromised data likely included a variety of sensitive information. This is because the University of Manchester works extensively with NHS trusts across the Greater Manchester area and beyond, involving numerous research projects and data sharing agreements.
Types of NHS Data Affected
The types of NHS data potentially affected are multifaceted and potentially include patient records containing Personally Identifiable Information (PII), such as names, addresses, dates of birth, and medical histories. Research data, including anonymized or pseudonymised patient data used for research purposes, could also have been compromised. Furthermore, the breach may have impacted administrative data related to NHS collaborations with the university, potentially exposing details about ongoing projects or funding arrangements.
The precise mix of data compromised is still under investigation, and the University and the NHS are likely working to identify exactly what sensitive information was accessed.
Volume of Data Compromised
Precise figures regarding the volume of compromised data remain unavailable at this time. The investigation is ongoing, and a full assessment of the affected data will require careful analysis of the university’s systems and data backups. However, given the scale of the University of Manchester’s involvement with NHS research and data management, it is reasonable to expect that a substantial amount of data was affected.
Estimates could range from several gigabytes to potentially terabytes of data, depending on the number of affected systems and the types of data stored within them. The complexity of this kind of data recovery and analysis means it will take considerable time before a definitive figure can be established.
Potential Risks Associated with Compromised Data
The potential risks associated with this data breach are significant and far-reaching. Compromised patient records could lead to identity theft, medical fraud, and financial losses for individuals. Malicious actors could use stolen PII to access bank accounts, apply for credit in patients’ names, or even impersonate patients to obtain medical services fraudulently. Furthermore, the release of sensitive medical information could cause significant emotional distress and reputational damage to affected individuals.
The compromise of research data could delay or compromise ongoing studies, potentially hindering advancements in medical research and impacting the quality of future healthcare treatments. Finally, the breach could lead to reputational damage for both the University of Manchester and the involved NHS trusts, eroding public trust in healthcare data security and research collaborations. The long-term consequences of this breach could be considerable and far-reaching.
University of Manchester’s Security Protocols: Nhs Data Breach After Ransomware Attack On University Of Manchester
The University of Manchester ransomware attack highlighted vulnerabilities in its cybersecurity infrastructure, prompting a critical review of its existing protocols. Understanding the pre-attack security landscape is crucial to assessing the effectiveness of the measures in place and identifying areas for improvement. This analysis focuses on key aspects of the university’s security posture before the incident, comparing them to industry best practices.The effectiveness of the University of Manchester’s security protocols in preventing or mitigating the ransomware attack remains a subject of ongoing investigation and internal review.
However, initial reports suggest that while certain security measures were in place, they may not have been sufficiently robust or implemented consistently across all systems and departments to effectively prevent or contain the attack. The full extent of the weaknesses will likely only be revealed through thorough post-incident analysis and independent audits. This analysis will focus on several key areas to illustrate the comparison.
Data Backup and Recovery Protocols
Prior to the attack, the University of Manchester likely employed some form of data backup and recovery system. However, the extent of this system’s effectiveness in mitigating data loss is unclear. The speed and efficiency of recovery following a ransomware attack depend heavily on the frequency, method, and security of backups. A robust system would include regular, automated backups stored offline or in geographically separate locations, protected by strong encryption.
The ransomware attack’s success suggests potential shortcomings in the university’s backup strategy, possibly including infrequent backups, insufficiently secure storage of backup copies, or difficulties in restoring data quickly and completely.
Network Security Measures
The university’s network security infrastructure, encompassing firewalls, intrusion detection/prevention systems (IDS/IPS), and other network security appliances, played a vital role in defending against external threats. However, the successful breach indicates vulnerabilities within this infrastructure. This might include insufficiently configured firewalls, outdated security software, or lack of robust network segmentation to limit the impact of a breach. Industry best practices emphasize a multi-layered approach to network security, including regular vulnerability assessments, penetration testing, and proactive threat intelligence.
The lack of a sufficiently strong multi-layered approach could explain the success of the ransomware attack.
Employee Security Training and Awareness
Human error often contributes significantly to successful cyberattacks. Phishing emails, malicious attachments, and social engineering tactics can exploit vulnerabilities in employee awareness and training. The university’s employee security training program, prior to the attack, likely covered basic cybersecurity hygiene, but the extent of this training and its effectiveness in preventing employees from falling victim to social engineering or phishing attacks is crucial.
Industry best practices recommend regular, comprehensive security awareness training, including simulated phishing attacks and ongoing education on emerging threats. A gap in effective training could have contributed to the successful infiltration.
| Area | UoM Protocol (Pre-Attack, Estimated) | Industry Best Practice | Gap Analysis |
|---|---|---|---|
| Data Backup | Regular backups, potentially on-site and/or cloud storage. Encryption likely in use, but the extent and robustness are unknown. | Regular, automated backups to multiple, geographically diverse, and offline locations with strong encryption and immutable storage. Regular testing of restoration capabilities. | Potential gaps in backup frequency, location diversity, and the security of backup storage, impacting the speed and completeness of data recovery. |
| Network Security | Firewalls, IDS/IPS likely in place. Network segmentation possibly implemented, but the extent and effectiveness are unknown. | Multi-layered network security architecture with robust firewalls, intrusion detection/prevention systems, regular vulnerability scanning, penetration testing, and proactive threat intelligence. Strong network segmentation to limit the impact of breaches. | Potential gaps in the robustness and configuration of security systems, network segmentation, and proactive threat monitoring, allowing the attackers to penetrate the network and move laterally. |
| Employee Training | Basic cybersecurity awareness training likely provided. Frequency and comprehensiveness are unknown. | Regular, comprehensive security awareness training, including simulated phishing exercises, training on social engineering tactics, and ongoing education on evolving threats. Regular reinforcement and testing of employee knowledge. | Potential gaps in the frequency, comprehensiveness, and effectiveness of training, potentially leading to employees falling victim to social engineering or phishing attacks. |
The Investigation and Response
Following the ransomware attack, the University of Manchester, in conjunction with the relevant authorities including the National Cyber Security Centre (NCSC) and potentially NHS Digital (depending on the extent of NHS data involvement), launched a comprehensive investigation. This involved a multi-faceted approach to understand the attack’s scope, identify the perpetrators, and implement effective remediation strategies. The process was likely complex and time-consuming, requiring collaboration across various departments and external specialists.The investigation likely employed several methods to pinpoint the source and actors behind the attack.
Forensic analysis of infected systems would have been crucial, examining logs, network traffic, and malware samples to reconstruct the attack timeline and identify the entry point. Investigators may have used techniques like malware reverse engineering to understand the ransomware’s functionality and identify any unique characteristics linking it to known threat actors. Analysis of the ransom note, if one was provided, and communication with the attackers (if any) would also have been valuable intelligence gathering methods.
Furthermore, collaboration with other organizations that have experienced similar attacks might have revealed patterns or connections that helped identify the responsible parties.
Identification of Attack Source and Actors
Identifying the specific source and the actors responsible for the ransomware attack is a critical part of the investigation. This process involves detailed analysis of the malware used, the attack vectors exploited, and any communication or demands made by the attackers. Techniques like sandboxing the malware to analyze its behavior in a controlled environment, along with network traffic analysis to identify the command-and-control servers used by the attackers, would have been employed.
The investigators likely compared the malware’s characteristics against known ransomware families in threat intelligence databases to identify potential links to specific cybercriminal groups. If the attackers made contact, the content of their communications would be analyzed for clues about their identity, motivations, and technical capabilities. The ultimate goal is to attribute the attack to a specific group or individual, if possible.
Remediation Efforts and System Restoration
Once the investigation identified the vulnerabilities exploited and the extent of the damage, the university implemented comprehensive remediation efforts. This would have included isolating affected systems to prevent further spread of the ransomware, patching known vulnerabilities in software and operating systems, and strengthening network security controls such as firewalls and intrusion detection systems. Data restoration involved various strategies, likely depending on the extent of data encryption and the availability of backups.
This might have included restoring data from backups, if available and deemed clean, or potentially employing data recovery techniques if backups were compromised or unavailable. The university likely worked closely with data recovery specialists to ensure the integrity and confidentiality of restored data. The process also included implementing enhanced security protocols and employee training to prevent future attacks.
Lessons Learned and Future Prevention
The University of Manchester ransomware attack serves as a stark reminder of the vulnerabilities inherent in even the most sophisticated institutions. The breach, impacting NHS patient data, underscores the interconnectedness of our digital systems and the devastating consequences of inadequate cybersecurity measures. Learning from this incident is crucial to prevent similar attacks in the future, requiring a multi-faceted approach involving technological advancements and significant shifts in organizational culture.The incident highlighted the critical need for robust and regularly updated cybersecurity protocols across all sectors, particularly those handling sensitive personal data.
A reactive approach to security is simply insufficient; proactive measures are essential to mitigate risks effectively. This necessitates a holistic strategy encompassing technological solutions, stringent employee training, and consistent auditing processes.
Strengthening Cybersecurity Protocols
Implementing a multi-layered security approach is paramount. This includes employing robust firewalls, intrusion detection systems, and regularly updated antivirus software. Furthermore, the principle of least privilege should be strictly enforced, limiting user access to only the data and systems necessary for their roles. Data encryption, both in transit and at rest, is crucial for protecting sensitive information even in the event of a breach.
Regular software patching and updates are essential to address known vulnerabilities. Finally, investing in advanced threat detection technologies, such as Security Information and Event Management (SIEM) systems, can help identify and respond to threats in real-time. The University of Manchester, along with other institutions, should adopt a zero-trust security model, verifying every user and device attempting to access the network, regardless of their location.
The Importance of Regular Security Audits and Penetration Testing, Nhs data breach after ransomware attack on university of manchester
Regular security audits and penetration testing are not optional; they are vital components of a comprehensive cybersecurity strategy. Security audits provide an independent assessment of an organization’s security posture, identifying vulnerabilities and weaknesses in its systems and processes. Penetration testing simulates real-world attacks, allowing organizations to identify exploitable vulnerabilities before malicious actors can exploit them. These tests should be conducted by external, independent security experts to ensure objectivity and a thorough evaluation.
The frequency of these audits and tests should be determined by the sensitivity of the data handled and the risk profile of the organization. For example, healthcare institutions handling sensitive patient data should conduct these assessments far more frequently than organizations with less sensitive data. The findings of these assessments should be used to inform and prioritize improvements to security controls.
A Hypothetical Employee Training Program
A comprehensive employee training program is essential to building a strong cybersecurity culture. The program should focus on practical, real-world scenarios and should be regularly updated to reflect evolving threats.The key components of such a program would include:
- Ransomware Awareness: Educating employees about the various types of ransomware, their methods of delivery (e.g., phishing emails, malicious attachments), and the potential consequences of infection.
- Phishing and Social Engineering: Training employees to identify and avoid phishing scams, malicious links, and other social engineering tactics commonly used to deliver ransomware.
- Password Security: Emphasizing the importance of strong, unique passwords, and promoting the use of multi-factor authentication (MFA) where available.
- Data Security Best Practices: Educating employees on proper data handling procedures, including secure storage, access control, and data encryption.
- Incident Response Procedures: Training employees on what to do in the event of a suspected ransomware attack, including reporting procedures and appropriate actions to take.
- Regular Quizzes and Simulations: Incorporating regular quizzes and phishing simulations to reinforce learning and test employee understanding.
This program should be interactive and engaging, utilizing various training methods such as videos, interactive modules, and hands-on exercises. Regular refresher training is essential to keep employees updated on the latest threats and best practices. The success of this program will depend on consistent reinforcement and active participation from all employees.
Legal and Ethical Implications
The ransomware attack on the University of Manchester and the subsequent NHS data breach raise significant legal and ethical concerns for both the University and the NHS. The ramifications extend beyond simple financial penalties and reputational damage, impacting patient trust and potentially leading to long-term consequences for data security practices across the healthcare sector. Understanding the legal landscape and ethical considerations is crucial for preventing future incidents and ensuring accountability.The legal ramifications are multifaceted and complex.
The University, as the data controller, bears primary responsibility for the security of the data entrusted to it. Failure to implement adequate security measures could lead to significant fines under the UK’s Data Protection Act 2018 and the General Data Protection Regulation (GDPR). Furthermore, affected individuals may pursue legal action for damages resulting from the breach, potentially including claims for compensation for distress, financial loss, or reputational harm.
The NHS, as the data processor, may also face scrutiny regarding its role in the incident and its adherence to data protection regulations. The nature and extent of the NHS’s liability will depend on the specifics of the data processing agreement between the University and the NHS.
Legal Ramifications for the University of Manchester and the NHS
The University of Manchester faces potential legal actions under the UK’s Data Protection Act 2018 and the GDPR. These could include enforcement actions from the Information Commissioner’s Office (ICO), resulting in substantial fines. The maximum fine under GDPR can be up to €20 million or 4% of annual global turnover, whichever is higher. Additionally, the University may face numerous civil lawsuits from individuals whose data was compromised, leading to potential significant financial liabilities.
The NHS, while not directly responsible for the security breach, could also face legal challenges if its involvement in the data processing is deemed inadequate or non-compliant with data protection regulations. This could include investigations by the ICO and potential legal action from individuals affected. The outcome would hinge on the details of data sharing agreements and the extent to which the NHS was involved in the data security protocols.
Ethical Considerations Regarding Patient Data Handling
The ethical implications center on the breach of patient confidentiality and the potential harm caused by the unauthorized access to sensitive health information. The core ethical principle of beneficence – acting in the best interests of patients – has been violated. The principle of non-maleficence – avoiding harm – has also been compromised, as the breach could expose patients to identity theft, financial fraud, or discrimination.
Furthermore, the incident raises concerns about the trust patients place in healthcare providers and the University’s responsibility to safeguard their data. Transparency and accountability are paramount in restoring this trust. The University and the NHS have a moral obligation to be open about the breach, provide affected individuals with appropriate support, and implement measures to prevent similar incidents in the future.
Potential Legal Actions Resulting from the Breach
A range of legal actions could result from the data breach. These include:
- Enforcement actions from the ICO, leading to fines and other sanctions.
- Civil lawsuits from individuals affected by the breach, seeking compensation for damages.
- Class action lawsuits, where multiple individuals collectively pursue legal action.
- Regulatory investigations by other relevant authorities, potentially leading to further penalties.
- Reputational damage and loss of public trust, impacting funding and future collaborations.
The potential legal costs associated with defending against these actions and providing compensation to affected individuals could be substantial for both the University and the NHS. The severity of the consequences will depend on factors such as the number of individuals affected, the sensitivity of the compromised data, and the effectiveness of the University and NHS’s response to the incident.
Public Perception and Trust
The University of Manchester ransomware attack and subsequent NHS data breach sparked a wave of public concern and outrage. News outlets quickly picked up the story, highlighting the potential risks to patient confidentiality and the broader implications for data security within the UK’s healthcare system. The initial reaction was a mixture of anger, fear, and distrust, directed at both the university and the NHS.
The incident served as a stark reminder of the vulnerability of sensitive personal data in the digital age.The breach significantly impacted public trust in both the University of Manchester and the NHS. Public confidence in the ability of these institutions to safeguard sensitive information was shaken. Many questioned the adequacy of existing security protocols and the effectiveness of the response to the attack.
The potential for misuse of the compromised data, including identity theft or medical fraud, fueled public anxiety and led to calls for greater accountability and transparency. This erosion of trust could have long-term consequences, potentially affecting future engagement with healthcare services and research initiatives involving the University.
The NHS data breach following the ransomware attack on the University of Manchester highlights the critical need for robust cybersecurity. Developing secure and resilient systems is paramount, and exploring modern development approaches like those discussed in this article on domino app dev the low code and pro code future could offer solutions for faster, more secure application development.
Ultimately, preventing future breaches requires a multi-faceted approach, including improved security protocols and efficient application development methodologies.
Impact on Public Trust in the NHS and the University of Manchester
The incident eroded public trust in the NHS’s ability to protect patient data. News reports focusing on the number of patients affected and the types of data compromised intensified public anxieties. Surveys conducted following similar breaches in other organizations show a clear correlation between data breaches and a decline in public trust. For example, a hypothetical survey could show a 15% decrease in trust after a high-profile breach, with a further 5% decrease if the response from the organization was perceived as inadequate.
This decline in trust could manifest in reduced willingness to share personal health information, hindering the effective delivery of healthcare services. Similarly, the University of Manchester’s reputation suffered, impacting potential student applications and research collaborations. The lack of immediate and comprehensive communication further exacerbated the situation.
Improved Communication Strategies
The University of Manchester’s communication strategy could have been significantly improved to mitigate negative public perception. Instead of delayed and fragmented updates, a proactive and transparent approach would have been more effective. For example, the university could have immediately issued a press release acknowledging the breach, outlining the extent of the data compromised, and detailing the steps taken to contain the situation.
Regular updates, perhaps through a dedicated webpage, could have kept the public informed of the ongoing investigation and remediation efforts. This transparency would have demonstrated accountability and built trust. Furthermore, proactively engaging with affected individuals, offering support and guidance, would have been crucial in mitigating the negative impact. A clear and concise communication plan, developed in consultation with public relations experts and considering potential scenarios, would have been vital in managing the crisis more effectively.
A dedicated phone line and email address for queries would have provided a vital channel for communication. The use of social media to address public concerns and provide updates in real-time would have also helped manage the narrative. Finally, a post-incident review, made publicly available, demonstrating lessons learned and improvements implemented, would have further built trust.
Final Review
The ransomware attack on the University of Manchester, and the subsequent NHS data breach, serves as a stark reminder of the ever-present threat of cybercrime in the digital age. The incident highlights the critical need for robust cybersecurity protocols, regular security audits, and comprehensive employee training across all sectors, especially those handling sensitive personal information. While the immediate fallout of this breach is significant, the long-term impact on public trust and the potential for future legal battles remain to be seen.
It’s a wake-up call for us all to prioritize digital security and demand greater accountability from institutions entrusted with our data.
Popular Questions
What type of ransomware was used in the attack?
The specific type of ransomware used hasn’t been publicly disclosed in all cases, but investigations are ongoing to determine the exact strain and its capabilities.
What is the University of Manchester doing to prevent future attacks?
The University is likely implementing enhanced security measures, including improved network security, employee training, and more frequent security audits. Specific details of their action plan may not be publicly available due to security concerns.
How can I check if my data was compromised?
If you believe your data may have been affected, contact the University of Manchester or the NHS directly for information on data breach notification and support services. They may offer resources to help individuals assess their risk.
What legal recourse do affected individuals have?
Legal options for affected individuals may include filing a civil lawsuit against the University of Manchester or pursuing other legal avenues to recover damages. Legal counsel should be sought for specific advice.





