Protecting Software Supply Chains with SBOM PBOM
Protecting software supply chains with sbom pbom – Protecting software supply chains with SBOMs (Software Bills of Materials) and PBOMs (Product Bills of Materials) is no longer a luxury; it’s a necessity. In today’s interconnected world, software underpins almost everything, making vulnerabilities a massive risk. Think of it like building a house – you wouldn’t use substandard materials, right? SBOMs and PBOMs provide that crucial inventory list of software components, allowing us to identify and address potential weaknesses before they’re exploited.
This deep dive explores how these critical tools can safeguard our digital infrastructure.
We’ll explore the differences between SBOMs and PBOMs, examining their practical applications in vulnerability management and risk mitigation. We’ll look at how to generate and manage these crucial documents, the legal landscape surrounding their use, and the exciting future of AI-driven SBOM analysis. Get ready to level up your understanding of software supply chain security!
Introduction to Software Supply Chain Security
Modern software is rarely built in isolation. It relies on a vast network of components, libraries, and frameworks, creating a complex and intricate software supply chain. This interconnectedness, while enabling rapid development and innovation, introduces significant vulnerabilities that can have devastating consequences. Understanding and mitigating these risks is crucial for maintaining the integrity and security of our digital world.The importance of securing the software supply chain cannot be overstated.
A single compromised component can lead to widespread breaches, impacting countless users and organizations. The consequences range from data breaches and financial losses to reputational damage and disruptions to critical infrastructure. The sheer scale and complexity of modern software supply chains make them particularly challenging to secure, requiring a multi-faceted approach involving proactive measures and robust security practices.
Software Supply Chain Vulnerabilities
Modern software supply chains are susceptible to various attack vectors. Malicious actors can introduce vulnerabilities at any stage, from the initial development of components to the deployment and maintenance of the final software product. These vulnerabilities can include malicious code injected into open-source libraries, compromised build systems, supply chain attacks targeting trusted developers, and weaknesses in dependency management.
The sheer number of components involved in even relatively simple software applications magnifies the potential attack surface. For example, a single application might rely on hundreds or even thousands of open-source libraries, each potentially harboring unknown vulnerabilities. This complexity makes it difficult to track and manage all dependencies effectively.
The Role of SBOMs and PBOMs
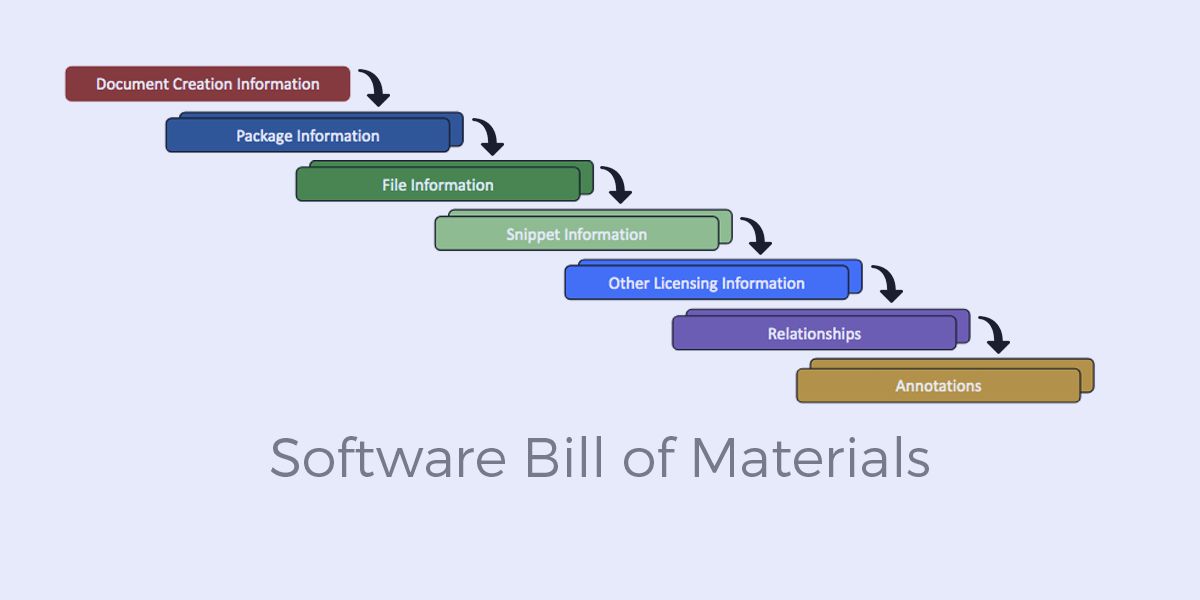
An SBOM (Software Bill of Materials) is a formal record containing information about the software components, libraries, and dependencies used in a software product. It essentially provides a detailed inventory of everything that makes up the software. Similarly, a PBOM (Product Bill of Materials) is a comprehensive list of all the components and materials that constitute a physical product, including software components.
Both SBOMs and PBOMs are crucial for enhancing software supply chain security by providing transparency and traceability. They allow developers and security teams to identify and assess risks associated with specific components, facilitating vulnerability detection and remediation. By providing a clear picture of the software’s composition, SBOMs and PBOMs enable organizations to make informed decisions about security and compliance.
The use of standardized formats for SBOMs, such as SPDX, allows for easier sharing and automated analysis.
SBOMs and PBOMs
Understanding Software Bills of Materials (SBOMs) and Product Bills of Materials (PBOMs) is crucial for securing modern software supply chains. While both provide inventory lists, they focus on different aspects of the software and hardware ecosystem, offering complementary insights into potential vulnerabilities. This deeper dive explores their distinctions, formats, and practical applications.
SBOM and PBOM Functionality and Uses
SBOMs list all the software components within a piece of software, including libraries, frameworks, and dependencies. This provides a comprehensive view of the software’s composition, allowing for identification of known vulnerabilities within those components. PBOMs, on the other hand, focus on the hardware and physical components that make up a system. This includes things like processors, memory chips, and other physical parts.
While seemingly distinct, they work together; a complete understanding of both allows for a holistic security assessment, connecting software vulnerabilities to the physical systems they run on. For example, a vulnerability in a specific library (identified via SBOM) might only affect systems with a certain processor (identified via PBOM).
SBOM Types and Formats
Several standards exist for representing SBOMs, each with its own strengths and weaknesses. SPDX (Software Package Data Exchange) is a widely adopted standard offering a rich, flexible format capable of representing a broad range of software components and their relationships. CycloneDX is another popular choice, known for its machine-readability and ease of integration into automated systems. The choice of format often depends on the specific tools and processes used within an organization.
Other formats exist, but these two are prevalent in the industry. A crucial point is that the format itself is less important than the completeness and accuracy of the SBOM data.
Benefits of Integrating SBOMs and PBOMs into the SDLC
Integrating SBOMs and PBOMs throughout the software development lifecycle offers significant advantages. Early integration allows for proactive vulnerability identification and mitigation, reducing the risk of security breaches. Automated SBOM generation during the build process ensures up-to-date inventory, enabling rapid response to newly discovered vulnerabilities. Furthermore, SBOMs and PBOMs are essential for compliance with emerging regulations and industry best practices, demonstrating due diligence and transparency to stakeholders.
The use of these documents facilitates easier collaboration between development teams, security teams, and vendors.
Hypothetical Scenario: SBOMs and PBOMs in Risk Mitigation
Imagine a company developing a medical device. Their SBOM reveals a critical vulnerability in a third-party library used for data transmission. Simultaneously, their PBOM indicates that a significant number of devices utilize a specific, now-vulnerable, processor. By cross-referencing these documents, the company can quickly assess the risk: the vulnerability in the library, combined with the widespread use of the vulnerable processor, poses a significant threat to patient data and device functionality.
The company can then prioritize patching the vulnerability, issuing firmware updates, and potentially recalling devices with the vulnerable processor. This demonstrates the power of SBOMs and PBOMs in proactive risk management and mitigation.
Utilizing SBOMs and PBOMs for Vulnerability Management
SBOMs (Software Bill of Materials) and PBOMs (Product Bill of Materials) are increasingly vital for managing vulnerabilities within software supply chains. They provide a comprehensive inventory of components, allowing for efficient identification and remediation of security flaws. By leveraging this detailed information, organizations can significantly reduce their attack surface and strengthen their overall security posture.
Common Vulnerabilities and Exposures (CVEs) Detectable with SBOMs and PBOMs
SBOMs and PBOMs enable the detection of a wide range of CVEs. These range from well-known vulnerabilities in widely used libraries (like Log4j) to less common flaws specific to individual components. By correlating the components listed in the SBOM/PBOM with publicly available vulnerability databases (like the National Vulnerability Database – NVD), organizations can quickly identify potential security risks.
This proactive approach allows for timely patching and mitigation before exploitation attempts occur. For example, an SBOM revealing the presence of a specific version of a database driver known to have a remote code execution vulnerability (CVE-XXXX-YYYY) would allow for immediate action.
Integrating SBOMs and PBOMs into Vulnerability Scanning and Remediation Processes, Protecting software supply chains with sbom pbom
Effective integration of SBOMs and PBOMs into vulnerability management workflows requires a structured approach. First, generate accurate and up-to-date SBOMs and PBOMs for all software components. Then, integrate these SBOMs/PBOMs into your existing vulnerability scanning tools. Many modern tools offer direct SBOM/PBOM import capabilities. The output from the vulnerability scan, highlighting identified CVEs associated with components listed in the SBOM/PBOM, should then be fed into your remediation workflow, prioritizing critical vulnerabilities for immediate patching or mitigation.
Regular updates of the SBOMs/PBOMs are crucial to maintain the accuracy and effectiveness of this process. Automated processes can significantly streamline this integration.
Generating and Using SBOMs to Identify Vulnerable Components
Generating and utilizing SBOMs to identify vulnerabilities follows a straightforward process.
- SBOM Generation: Use a suitable SBOM generation tool (e.g., CycloneDX, SPDX, or tools integrated into CI/CD pipelines) during the software build process. Specify the desired SBOM format (e.g., SPDX-JSON, CycloneDX JSON). Ensure the SBOM accurately reflects all dependencies, including transitive dependencies.
- SBOM Analysis: Import the generated SBOM into a vulnerability scanning tool. These tools often allow for direct SBOM import or integration with SBOM repositories.
- Vulnerability Identification: The vulnerability scanner will cross-reference the components listed in the SBOM with known vulnerability databases. This process identifies CVEs associated with the software components used in the project.
- Remediation: Based on the identified vulnerabilities, prioritize remediation efforts. This might involve updating components, implementing workarounds, or developing alternative solutions.
Comparison of Vulnerability Scanning Tools with SBOM Integration
| Tool Name | SBOM Formats Supported | Vulnerability Databases | Integration Capabilities |
|---|---|---|---|
| Snyk | SPDX, CycloneDX | NVD, Snyk vulnerability database | API, CLI, IDE plugins |
| Anchore | SPDX, CycloneDX | NVD, Anchore vulnerability database | API, CLI, integration with container registries |
| Black Duck | SPDX, CycloneDX | NVD, Black Duck vulnerability database | API, integration with CI/CD pipelines |
| FOSSA | SPDX, CycloneDX | NVD, FOSSA vulnerability database | API, CLI, web UI |
SBOM and PBOM Creation and Management

Generating and managing Software Bill of Materials (SBOMs) and Product Bill of Materials (PBOMs) is crucial for securing your software supply chain. Effective SBOM and PBOM management allows for proactive vulnerability identification, improved traceability, and faster response times to security incidents. This process, however, presents unique challenges requiring careful planning and implementation.SBOMs and PBOMs are not static documents; they require ongoing maintenance to reflect changes in the software throughout its lifecycle.
This necessitates a robust strategy encompassing automated generation, secure storage, and regular updates.
Automated SBOM Generation During the Build Process
Several tools and techniques facilitate the automated generation of SBOMs during the build process. These methods significantly reduce manual effort and ensure the SBOM reflects the current state of the software. Popular choices include leveraging build system plugins or dedicated SBOM generation tools. For instance, many CI/CD platforms offer plugins that automatically generate SBOMs in various formats (e.g., SPDX, CycloneDX) as part of the build process.
These plugins often integrate with dependency management tools to accurately capture all components and their versions. Dedicated tools, on the other hand, can be integrated into the build pipeline and provide more advanced features such as vulnerability scanning and reporting. The choice depends on the specific build system and desired level of integration.
SBOM and PBOM Storage and Management Best Practices
Effective management of SBOMs and PBOMs requires a structured approach to storage and access control. Storing these documents in a centralized, secure repository ensures easy retrieval and version control. Version control systems like Git can be used to track changes and maintain a history of SBOMs and PBOMs. Furthermore, access control mechanisms should be implemented to restrict access to authorized personnel only.
Regular backups and disaster recovery plans are also critical to ensure data availability and business continuity. Consider using a secure, immutable storage solution for long-term archival of SBOMs and PBOMs.
Challenges in Maintaining Accurate and Up-to-Date SBOMs and PBOMs
Maintaining accurate and up-to-date SBOMs and PBOMs presents ongoing challenges. The dynamic nature of software development, with frequent updates and dependencies, necessitates continuous monitoring and updates. Changes in dependencies, updates to components, or even the build process itself can render an SBOM inaccurate. Tracking open-source components and their associated vulnerabilities is another significant hurdle. Furthermore, the lack of standardization across different SBOM formats can complicate data integration and analysis.
Addressing these challenges requires a combination of automated tools, rigorous processes, and a commitment to ongoing maintenance. For example, integrating automated vulnerability scanning into the CI/CD pipeline can help detect outdated components and trigger alerts for necessary updates.
Integrating SBOM Generation into a CI/CD Pipeline
Integrating SBOM generation into a CI/CD pipeline is crucial for automating the process and ensuring that SBOMs are generated consistently and reliably. This involves adding a step to the pipeline that uses a chosen SBOM generation tool to create the SBOM after the build process completes. The generated SBOM can then be stored in the artifact repository alongside the built software.
This integration enables automated security checks and vulnerability assessments as part of the release process, ensuring that only secure software is deployed. The pipeline can also be configured to trigger alerts if vulnerabilities are detected in the SBOM, preventing the release of insecure software. A well-integrated system ensures timely identification and remediation of vulnerabilities. For example, a Jenkins pipeline can be configured to use a CycloneDX plugin to generate an SBOM after each successful build, storing it in a Nexus repository.
Legal and Compliance Considerations: Protecting Software Supply Chains With Sbom Pbom
The increasing reliance on software necessitates a robust understanding of the legal and compliance landscape surrounding software supply chain security. Failing to address these aspects can lead to significant financial and reputational damage, not to mention potential legal repercussions. The use of Software Bills of Materials (SBOMs) and Product Bills of Materials (PBOMs) is becoming increasingly crucial in navigating this complex terrain.The regulatory landscape is rapidly evolving, pushing organizations to proactively integrate SBOMs and PBOMs into their security practices.
Several key pieces of legislation and standards highlight the importance of transparency and accountability within software supply chains. Non-compliance can result in hefty fines, legal battles, and a loss of customer trust.
Regulatory Requirements and Industry Standards Related to SBOM Usage
Several key initiatives are driving the adoption of SBOMs. The US government’s Executive Order 14028 on Improving the Nation’s Cybersecurity significantly emphasizes the importance of SBOMs for federal agencies and their contractors. This executive order mandates the use of SBOMs to improve visibility into software components and vulnerabilities. Furthermore, standards like NIST SP 800-190 provide guidance on SBOM creation and usage, promoting interoperability and standardization across different sectors.
The ISO/IEC 5962 standard on Software Product Data Units (SPDU) provides a related framework that can help organizations manage and exchange product data effectively. These standards and regulations aim to improve supply chain security and reduce the risk of vulnerabilities.
Potential Legal Implications of Not Using SBOMs and PBOMs
The absence of SBOMs and PBOMs can expose organizations to a range of legal risks. In the event of a security breach attributable to vulnerabilities within the software supply chain, a lack of SBOMs could hinder investigations and demonstrate a lack of due diligence. This can lead to significant legal liabilities, including lawsuits from affected customers or regulatory penalties for non-compliance with mandates like Executive Order 14028.
Furthermore, contracts with government agencies or other organizations may explicitly require the provision of SBOMs, making their absence a breach of contract. The legal implications extend beyond direct penalties to include reputational damage and loss of business opportunities.
Examples of Organizations Leveraging SBOMs to Meet Compliance Requirements
Many organizations are proactively adopting SBOMs to demonstrate compliance and mitigate risk. For instance, large technology companies are incorporating SBOM generation into their software development lifecycle (SDLC) processes, ensuring that SBOMs are created and maintained for all released software. This proactive approach helps them meet regulatory requirements, such as those Artikeld in Executive Order 14028, and build trust with their customers.
Government agencies are also leading the charge, mandating SBOM usage for their contractors and actively developing their own SBOM capabilities to enhance visibility and control over their software ecosystems. These examples demonstrate that SBOM adoption is not just a compliance issue but a strategic move towards improving overall software supply chain security and building a more resilient and trustworthy digital ecosystem.
Future Trends in SBOM and PBOM Usage
The world of software supply chain security is rapidly evolving, and SBOMs and PBOMs are at the forefront of this change. Their increasing adoption is driving innovation, leading to new technologies and approaches that will significantly impact their future use and effectiveness. We’re moving beyond simply generating these documents to leveraging their power for proactive security and automated vulnerability management.The integration of AI and machine learning promises to revolutionize how we create, manage, and utilize SBOMs and PBOMs.
This isn’t just about efficiency gains; it’s about fundamentally altering our ability to identify and mitigate risks within complex software ecosystems. The future will see a shift towards more automated and intelligent systems, reducing the manual effort and human error associated with current processes.
Automated SBOM Generation and Analysis using AI and Machine Learning
AI and machine learning algorithms are poised to automate many aspects of SBOM generation. Imagine a future where tools automatically analyze code repositories, build processes, and dependency graphs, generating accurate and up-to-date SBOMs in real-time. This would eliminate the current manual effort and reduce errors, leading to more reliable and consistent SBOMs. Furthermore, AI can analyze these SBOMs, identifying potential vulnerabilities by cross-referencing them against known vulnerability databases and identifying patterns indicative of malicious code or insecure practices.
For example, an AI-powered system could detect unusual dependencies or versions that deviate from established security best practices, flagging them for immediate investigation. This proactive approach significantly improves the speed and effectiveness of vulnerability detection and response. Machine learning models could also learn from past incidents and adapt their analysis to identify emerging threats more effectively. Companies like Synopsys and Black Duck are already incorporating AI into their software composition analysis (SCA) tools, demonstrating the practical application of this technology.
Enhanced Vulnerability Management through SBOM and PBOM Integration
The integration of SBOMs and PBOMs into existing vulnerability management systems will significantly improve the efficiency and effectiveness of security operations. This integration will enable automated vulnerability identification and prioritization, allowing security teams to focus on the most critical risks. For example, by linking SBOMs to vulnerability databases, security tools can automatically identify components with known vulnerabilities within a software system.
This automated process reduces the time and resources needed for manual vulnerability assessments, allowing for faster response times to emerging threats. Furthermore, the combination of SBOM and PBOM data provides a comprehensive view of the software supply chain, from component-level details to the finished product, enabling more accurate risk assessment and mitigation strategies. This improved visibility will be crucial in responding effectively to supply chain attacks.
SBOM and PBOM Standardization and Interoperability
The future success of SBOMs and PBOMs hinges on standardization and interoperability. Consistent formats and data structures will be critical for efficient data exchange and automated analysis. Efforts like the SPDX standard are crucial in achieving this goal. Increased interoperability between different tools and platforms will enable seamless integration into existing workflows, maximizing the benefits of SBOMs and PBOMs.
The development of standardized APIs and data exchange formats will facilitate this interoperability, allowing different systems to communicate and share SBOM and PBOM data effectively. This will create a more efficient and collaborative ecosystem for software supply chain security. Increased industry adoption of standardized formats will also lead to the development of more sophisticated analysis tools, improving the overall effectiveness of SBOM and PBOM usage.
Last Word

Securing our software supply chains is a continuous journey, not a destination. By embracing SBOMs and PBOMs, we’re not just patching vulnerabilities; we’re building a more resilient and trustworthy digital ecosystem. The benefits extend beyond simple risk reduction – they foster collaboration, improve compliance, and pave the way for more innovative and secure software development practices. The future of software security hinges on our collective adoption of these essential tools, and I hope this post has equipped you with the knowledge to get started.
FAQ Insights
What’s the difference between an SBOM and a PBOM?
An SBOM focuses specifically on the software components within a product, while a PBOM provides a broader view, including hardware and other non-software elements. Think of the SBOM as a detailed parts list for the software engine, and the PBOM as the complete parts list for the entire vehicle.
Are SBOMs mandatory?
The legal requirements for SBOMs vary depending on your industry and location. However, many governments and organizations are increasingly mandating or strongly recommending their use due to growing security concerns. Staying informed about relevant regulations is crucial.
How much does SBOM creation cost?
The cost varies greatly depending on the complexity of your software, the tools you use, and whether you automate the process. While there are upfront costs, the potential savings from avoiding security breaches far outweigh the investment.
Can I create an SBOM manually?
While technically possible for very small projects, manual SBOM creation is impractical for anything beyond a tiny scale. Automated tools are essential for efficiency and accuracy, especially as your software grows.