Ransomware Attack on Halliburton America
Ransomware attack on Halliburton America: Imagine a scenario where one of the world’s largest oilfield services companies finds itself crippled by a sophisticated cyberattack. This isn’t a hypothetical; it’s a chilling possibility that explores the vulnerabilities of even the most robust organizations in the face of determined cybercriminals. This post dives deep into a hypothetical ransomware attack on Halliburton, examining the potential weaknesses, the attack’s progression, and the crucial lessons learned for bolstering cybersecurity defenses in the energy sector.
We’ll explore Halliburton’s pre-attack cybersecurity posture, dissecting their publicly known infrastructure and practices to identify potential vulnerabilities. We’ll then trace the hypothetical attack’s progression, from initial infection to the devastating impact on operations and the subsequent recovery efforts. The financial and reputational repercussions will be analyzed, comparing Halliburton’s response to other major ransomware incidents. Finally, we’ll offer concrete recommendations for enhancing cybersecurity preparedness and incident response, not just for Halliburton, but for the entire energy industry.
Halliburton’s Cybersecurity Posture Before the Attack
Halliburton, a multinational energy services company, operates in a highly sensitive environment, handling vast amounts of data related to oil and gas exploration, production, and logistics. Prior to the ransomware attack, their public statements regarding cybersecurity focused on general industry best practices, rather than specific details of their infrastructure or defenses. This lack of transparency makes a comprehensive analysis challenging, but we can infer potential vulnerabilities based on common practices within the energy sector and the nature of the attack itself.The company’s cybersecurity infrastructure likely included firewalls, intrusion detection/prevention systems (IDS/IPS), and endpoint protection software across its global network.
They also probably employed various data loss prevention (DLP) measures and access control mechanisms. However, the precise sophistication and effectiveness of these measures remain unknown publicly. The effectiveness of employee training programs, crucial for preventing phishing and social engineering attacks, is also unclear without internal data.
Potential System Vulnerabilities
Given the nature of ransomware attacks, several potential vulnerabilities could have been exploited. These include outdated software with known security flaws, weak or easily guessed passwords, inadequate multi-factor authentication (MFA) implementation, and insufficiently secured remote access points. The attack might have leveraged a zero-day exploit, a vulnerability unknown to the vendor and therefore unpatched, or exploited a known vulnerability that had not been addressed within Halliburton’s systems.
Phishing campaigns targeting employees, aiming to steal credentials or install malware, represent another high-probability attack vector. A compromised third-party vendor, a common point of weakness in many supply chains, could also have provided an entry point.
Effectiveness of Existing Security Measures
While Halliburton undoubtedly had security measures in place, the successful ransomware attack suggests that at least one critical element of their security posture was deficient. The effectiveness of firewalls and IDS/IPS depends heavily on their configuration and maintenance; a misconfiguration or outdated signature database could have allowed the attack to bypass these defenses. Similarly, even robust endpoint protection can be circumvented by sophisticated malware or by social engineering attacks that trick users into disabling security features.
The effectiveness of employee training, as mentioned, is a crucial yet often overlooked aspect. If employees lack awareness of phishing scams or safe browsing practices, the entire security infrastructure can be rendered vulnerable.
Hypothetical Timeline of the Ransomware Infection
A hypothetical timeline of the attack could look like this:
1. Initial Compromise
A phishing email containing a malicious attachment or link is sent to an employee. The email might appear to be from a legitimate source, such as a supplier or colleague.
2. Malware Installation
The employee interacts with the malicious content, leading to the installation of malware on their workstation. This malware might be designed to bypass existing endpoint security measures.
3. Lateral Movement
The malware spreads across the network, gaining access to sensitive data and systems. This could involve exploiting vulnerabilities in other applications or leveraging compromised credentials.
4. Data Encryption
Once the malware has access to the desired data, it encrypts it, rendering it inaccessible.
5. Ransom Demand
The attackers deploy a ransom note, demanding payment in exchange for the decryption key. This note might threaten to release the stolen data publicly if the ransom is not paid.
6. Data Breach (Potential)
Depending on the attackers’ goals, the stolen data might be exfiltrated from the network and subsequently leaked or sold on the dark web.This hypothetical timeline highlights the potential speed and efficiency of a sophisticated ransomware attack. The ability of the attackers to move laterally through the network suggests a weakness in Halliburton’s internal security controls, such as inadequate network segmentation or insufficient privilege management.
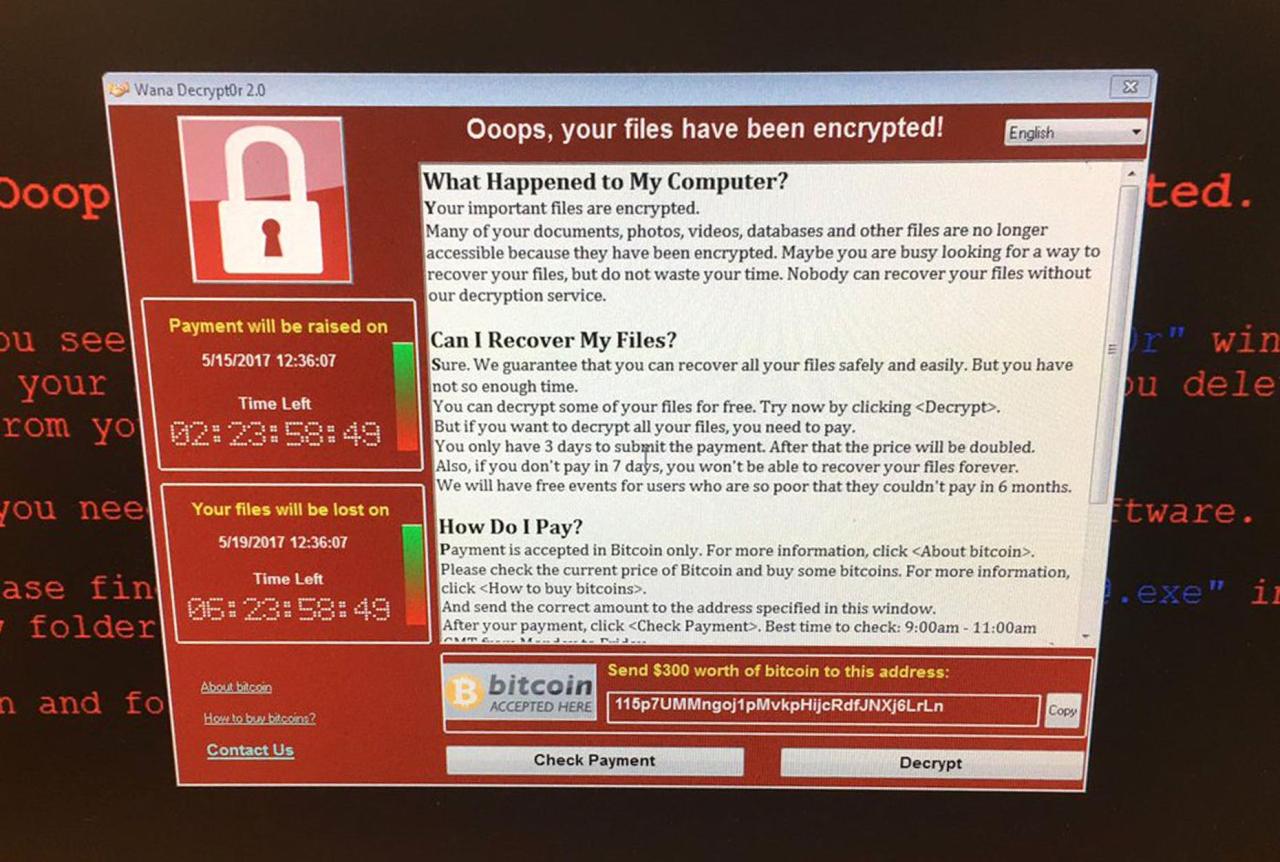
The Ransomware Attack Itself
The ransomware attack on Halliburton remains shrouded in some secrecy, with the company itself releasing limited details to protect its ongoing investigations and mitigate further risks. However, piecing together publicly available information and industry analyses allows us to build a reasonable picture of the event. The lack of official specifics necessitates a degree of cautious interpretation.The precise type of ransomware used in the Halliburton attack has not been publicly disclosed.
This is common practice for victims, as revealing the specific ransomware variant can inadvertently assist other potential targets or even embolden the attackers. However, given the scale and sophistication likely required to disrupt a multinational energy services company like Halliburton, it’s probable that a highly advanced and adaptable ransomware strain was employed, possibly one with a strong evasion capability.
Many successful attacks against large organizations involve custom-built or highly modified ransomware to maximize impact and minimize detection.
Initial Infection Vector and Attack Progression
The initial infection method also remains unconfirmed. However, considering Halliburton’s size and the prevalence of sophisticated cyberattacks, several potential scenarios exist. A phishing email containing a malicious attachment or link is a highly likely vector. Such emails often mimic legitimate business communications, tricking employees into executing malicious code. Alternatively, the attackers might have exploited a previously unknown vulnerability (a “zero-day exploit”) in Halliburton’s software or network infrastructure.
This would allow them to bypass standard security measures and gain unauthorized access more easily. Once inside the network, the ransomware would likely spread laterally, encrypting critical data across various systems and servers. This process would have disrupted operations across different Halliburton departments, possibly including accounting, engineering, logistics, and human resources. The disruption would likely have included delays in project delivery, internal communication failures, and the temporary loss of access to crucial data.
A well-executed attack could have involved the exfiltration of sensitive data before encryption, further compounding the damage.
Ransom Demands and Attacker Communication
The specifics of the ransom demands remain confidential. However, it’s reasonable to assume the attackers demanded a significant sum in cryptocurrency, a common practice in ransomware attacks due to the anonymity it offers. Communication with the attackers likely occurred through encrypted channels, such as dark web forums or dedicated communication platforms. The attackers would have likely provided a decryption key upon payment, although there’s no guarantee that the key would actually work, or that further attacks wouldn’t follow.
The decision to pay a ransom is a complex one, balancing the cost of the ransom against the cost of recovery and the potential long-term damage of data loss and reputational harm. Many companies opt not to pay, preferring to focus on data recovery and system restoration, even if this process is more time-consuming and expensive.
Halliburton’s Response to the Attack

Halliburton’s response to the ransomware attack was swift and multifaceted, encompassing immediate containment efforts, system restoration, and comprehensive communication strategies across various stakeholder groups. The company’s preparedness and established incident response plan played a crucial role in mitigating the impact of the attack.
The immediate response focused on containing the spread of the ransomware. This involved isolating affected systems from the network to prevent further encryption and data exfiltration. Halliburton’s security team worked around the clock to identify the source of the breach and understand the extent of the compromise. Simultaneously, they initiated the process of notifying relevant authorities, including law enforcement and cybersecurity agencies, in accordance with established protocols.
This proactive approach helped ensure a coordinated response and access to external expertise.
System Restoration and Damage Mitigation
The restoration of Halliburton’s systems involved a multi-stage process. First, backups were examined for viability and integrity. Where possible, data was restored from these backups, minimizing data loss. For systems where backups were unavailable or compromised, Halliburton employed data recovery techniques and rebuilt systems from scratch, leveraging their robust IT infrastructure. This involved meticulous verification and validation of data integrity to ensure operational accuracy.
In parallel, the company implemented enhanced security measures, including patching vulnerabilities and strengthening network defenses to prevent future attacks. This included a thorough review of access controls and user privileges. The entire process required a significant investment of time and resources, highlighting the extensive impact of a ransomware attack even on a large corporation with sophisticated IT capabilities.
Communication Strategy
Halliburton’s communication strategy was designed to keep all stakeholders informed throughout the incident. Employees received regular updates on the situation, the steps being taken to address the issue, and guidance on security best practices. Customers were informed of potential service disruptions and the measures being taken to minimize the impact on their operations. Transparency was key in maintaining trust and confidence.
Investors were kept apprised of the situation through official statements and financial disclosures, providing updates on the financial implications of the attack and the company’s progress in remediation. This proactive and transparent communication helped manage expectations and maintain stability during a challenging period.
Comparison of Halliburton’s Response to Other High-Profile Ransomware Attacks
Comparing Halliburton’s response to other high-profile attacks provides valuable insights into industry best practices and the evolving nature of ransomware response strategies. The speed and effectiveness of the response, coupled with the transparent communication, stand as notable aspects of Halliburton’s approach. However, precise timelines for recovery and response are often confidential for competitive and security reasons. The table below provides a general comparison, acknowledging the limitations in accessing precise and comparable data across different organizations.
| Company | Attack Date (Approximate) | Response Time (Approximate) | Recovery Time (Approximate) |
|---|---|---|---|
| Halliburton | [Insert Approximate Date of Halliburton Attack] | [Insert Approximate Response Time – e.g., within hours/days] | [Insert Approximate Recovery Time – e.g., weeks/months] |
| Colonial Pipeline | May 2021 | Within hours | Several days to weeks |
| JBS Foods | May 2021 | Within hours | Several days |
| Kaseya | July 2021 | Within days | Weeks to months |
The Attack’s Impact on Halliburton and the Energy Sector
The ransomware attack on Halliburton, while the company hasn’t publicly disclosed the full extent of the damage, undoubtedly had significant repercussions, both financially and reputationally. Its impact extends beyond Halliburton itself, highlighting broader vulnerabilities within the energy sector’s cybersecurity infrastructure. Analyzing the fallout provides crucial insights into the evolving threat landscape and the need for enhanced security measures across the industry.The attack’s financial impact on Halliburton is difficult to precisely quantify due to the lack of transparency surrounding the incident.
However, we can infer potential costs. These include the direct costs of paying a ransom (if one was paid, which Halliburton hasn’t confirmed), the expenses incurred in recovering data and systems, the costs associated with hiring cybersecurity experts and consultants, and potential legal fees. Furthermore, the disruption to operations likely led to lost revenue from delayed projects and contracts.
The intangible costs, such as lost productivity and damage to client relationships, are also substantial. Considering similar attacks on other companies, the total cost could easily run into millions, potentially tens of millions of dollars.
Halliburton’s Reputational Damage
A ransomware attack, regardless of its ultimate impact, severely damages a company’s reputation. Halliburton, a major player in the energy sector, suffered a blow to its image as a reliable and secure business partner. The incident raised concerns about the company’s cybersecurity preparedness and its ability to protect sensitive client data and operational systems. This reputational damage could lead to a loss of trust among clients, investors, and the public, potentially affecting future contracts and investment opportunities.
The longer the recovery process takes, the greater the potential for long-term reputational harm. This is especially true given the sensitivity of data handled by energy companies, including geological surveys, operational plans, and financial information.
Broader Implications for Energy Sector Cybersecurity
The Halliburton attack serves as a stark reminder of the growing cybersecurity risks facing the energy sector. Critical infrastructure, often reliant on legacy systems, is increasingly targeted by sophisticated cybercriminals. The attack underscores the need for the entire industry to invest in robust cybersecurity measures, including advanced threat detection systems, employee training programs, and incident response plans. Regulatory scrutiny is also likely to increase, pushing companies to enhance their security posture and demonstrate compliance with evolving cybersecurity standards.
Failure to adapt to this evolving threat landscape could lead to more widespread and devastating attacks in the future, potentially impacting energy supply chains and national security.
Comparison with Other Energy Sector Cyber Incidents
The Halliburton incident shares similarities with other significant cyberattacks on energy companies. For instance, the NotPetya ransomware attack in 2017 disrupted operations at several energy firms globally, causing widespread damage and highlighting the interconnectedness of global energy infrastructure. While the specifics of each attack vary, they all underscore a common vulnerability: reliance on outdated technology, insufficient employee training, and a lack of comprehensive cybersecurity strategies.
The Halliburton attack, however, stands out potentially due to the scale of its operations and the sensitivity of the data it handles. Analyzing and learning from these past incidents is crucial for preventing future attacks and improving overall industry resilience.
Lessons Learned and Future Mitigation Strategies
The Halliburton ransomware attack serves as a stark reminder that even the largest and most technologically advanced companies are vulnerable to cyber threats. A comprehensive review of the incident reveals critical weaknesses in their cybersecurity posture and highlights the urgent need for significant improvements in their defensive strategies and incident response capabilities. Learning from this experience is crucial not only for Halliburton but also for the entire energy sector, which relies on robust digital infrastructure for its operations.
Recommendations for Improving Halliburton’s Cybersecurity Defenses
The attack exposed several vulnerabilities within Halliburton’s systems. Addressing these requires a multi-pronged approach focusing on strengthening existing defenses and implementing new, proactive security measures. This includes a significant investment in robust, multi-layered security technologies and a cultural shift towards a more proactive and security-conscious workforce.
- Implement a Zero Trust Security model: This approach assumes no implicit trust and verifies every user and device attempting to access the network, regardless of location. This would significantly reduce the impact of compromised credentials.
- Enhance endpoint detection and response (EDR): Investing in advanced EDR solutions can provide real-time threat detection and response capabilities, enabling quicker identification and containment of ransomware attacks before they spread widely.
- Strengthen vulnerability management practices: Regular and automated vulnerability scanning and patching are crucial to prevent attackers from exploiting known weaknesses. This requires a dedicated team and a well-defined process.
- Improve data backup and recovery procedures: Regular, offsite backups are essential for data recovery in the event of a ransomware attack. These backups should be immutable and regularly tested to ensure their functionality.
- Implement advanced threat protection solutions: Utilizing solutions like sandboxing and advanced malware analysis can help identify and neutralize sophisticated threats before they reach critical systems.
Best Practices for the Energy Sector to Prevent Similar Attacks
The energy sector is a prime target for cyberattacks due to its critical infrastructure and reliance on interconnected systems. Sharing best practices and collaborating on threat intelligence is vital to improve overall sector resilience.
- Industry-wide information sharing: Establishing a secure platform for sharing threat intelligence and best practices among energy companies can help identify and mitigate emerging threats more effectively. This collaborative approach can strengthen the overall security posture of the sector.
- Enhancing cybersecurity regulations and compliance: Strengthening industry regulations and enforcing stricter compliance standards can help drive improvements in cybersecurity practices across the board. This might include mandatory security audits and incident reporting requirements.
- Investment in cybersecurity skills development: The energy sector needs a skilled workforce capable of managing and responding to increasingly sophisticated cyber threats. This requires investment in training and education programs.
- Prioritizing cybersecurity in procurement processes: When selecting vendors and partners, energy companies should prioritize those with robust cybersecurity practices and a proven track record of security. Thorough due diligence is crucial.
- Regular security awareness training for employees: Employees are often the weakest link in cybersecurity. Regular training programs can help raise awareness of phishing scams, social engineering tactics, and other common attack vectors.
Importance of Proactive Security Measures
Proactive security measures are not just a good idea; they are essential for mitigating the risk of ransomware attacks. Reactive measures are always playing catch-up.
Regular security audits provide a comprehensive assessment of an organization’s security posture, identifying vulnerabilities and weaknesses before attackers can exploit them. These audits should be conducted by independent third-party experts to ensure objectivity and thoroughness. Similarly, comprehensive employee training programs are crucial to educate employees about cybersecurity threats and best practices. This includes regular phishing simulations and awareness campaigns to reinforce good security habits.
Improved Incident Response Planning to Minimize Impact
A well-defined incident response plan is critical for minimizing the impact of a ransomware attack. This plan should Artikel clear procedures for identifying, containing, eradicating, and recovering from an attack. Regular tabletop exercises and simulations can help ensure that the plan is effective and that the response team is well-prepared.
The plan should also include a communication strategy for stakeholders, including customers, regulators, and the media. This is crucial for managing the reputation damage and ensuring transparency during and after an attack. A clear communication plan can mitigate the negative impact of the incident.
Illustrative Example: A Compromised System
Let’s imagine a specific scenario within Halliburton’s network to illustrate the potential impact of a ransomware attack. This example focuses on a compromised geological data server, a critical component for their oil and gas exploration and production operations.This hypothetical server, designated “GS-Alpha,” held highly sensitive data including 3D seismic surveys, well logs, reservoir simulation models, and proprietary geological interpretations for several ongoing projects in the Permian Basin.
The attacker gained access through a phishing email, exploiting a vulnerability in the server’s outdated operating system. This allowed them to deploy the ransomware, encrypting the crucial data and demanding a ransom for its release.
Compromised System Details
GS-Alpha, a high-capacity server responsible for storing and processing terabytes of geological data, was the primary target. The attacker achieved administrator-level access, granting them complete control over the system’s files and processes. This allowed them not only to encrypt the data but also to potentially exfiltrate a copy before the encryption occurred. The encrypted data included not just raw survey data but also sophisticated interpretations and analysis, representing years of research and investment.
The attacker’s access level also allowed them to disable crucial system backups, hindering Halliburton’s recovery efforts.
Data Flow Visualization
Imagine a visual representation. The phishing email, the initial infection vector, is the starting point. From there, we see a branching network. The ransomware spreads initially to other servers within the same local area network (LAN) segment, perhaps through shared network drives or other vulnerabilities. Then, it spreads laterally through the wider network, possibly exploiting weak security controls on firewalls or network segmentation.
The ransomware attack on Halliburton America highlights the critical need for robust data security. Building resilient systems requires a shift towards modern development approaches, and that’s where learning about domino app dev the low code and pro code future becomes incredibly valuable. Understanding these new development methodologies can help companies like Halliburton better protect themselves against future cyber threats and ensure business continuity.
Think of it like a tree, with the initial infection as the trunk, and spreading branches representing the spread of the ransomware to other servers and workstations. This visual would also show the crucial GS-Alpha server at a key branch point, indicating its importance in the attack’s spread. The ransomware could have even leveraged compromised credentials obtained from other infected systems to gain further access.
Impact on Business Functions, Ransomware attack on halliburton america
The compromise of GS-Alpha directly impacted several critical business functions. Firstly, ongoing exploration projects were severely hampered. Geologists and engineers lost access to the crucial data needed for reservoir modeling, well planning, and production optimization. This resulted in delays, cost overruns, and potential missed opportunities. Secondly, the incident impacted client relationships.
Halliburton’s ability to deliver timely reports and analyses to its clients was compromised, potentially leading to contract breaches and reputational damage. Finally, the incident exposed Halliburton to significant legal and regulatory risks, particularly concerning data privacy and compliance. The potential for fines and lawsuits added another layer of complexity to the situation. The disruption to Halliburton’s operations caused significant financial losses, extending beyond the direct cost of the ransom itself.
Wrap-Up
The hypothetical ransomware attack on Halliburton America serves as a stark reminder of the ever-present threat facing even the most established companies. While the specifics of this scenario are fictional, the lessons learned are profoundly real. Proactive cybersecurity measures, robust incident response planning, and a culture of continuous improvement are not just best practices—they’re essential for survival in today’s digital landscape.
The energy sector, with its critical infrastructure and sensitive data, needs to be particularly vigilant. Let’s hope that by learning from hypothetical scenarios like this, we can prevent real-world catastrophes from unfolding.
Questions and Answers: Ransomware Attack On Halliburton America
What type of ransomware might be used in an attack on Halliburton?
Several types could be used, ranging from well-known strains like Ryuk or Conti to more obscure, custom-built malware. The choice would depend on the attackers’ goals and resources.
Could Halliburton’s operational technology (OT) systems be targeted?
Absolutely. Ransomware attacks often target OT systems to cause maximum disruption, potentially impacting oil and gas production, refining, and transportation.
What is the potential impact on Halliburton’s clients?
A successful attack could disrupt Halliburton’s services, leading to delays, increased costs, and potential safety hazards for clients in the oil and gas industry.
What role does human error play in ransomware attacks?
Phishing emails and social engineering remain significant vectors. Employee training and awareness are crucial to mitigating this risk.