Ransomware Attack on Serco and UK Research & Innovation
Ransomware attack on serco and uk research and innovation – Ransomware attack on Serco and UK Research & Innovation: This chilling tale plunges us into the heart of a cybersecurity crisis impacting a major player in UK research. Imagine the disruption – sensitive research data potentially compromised, projects delayed, and the very fabric of scientific progress threatened. We’ll delve into the specifics of this attack, exploring the methods used, the impact on vital research initiatives, and the lessons learned for future cybersecurity strategies.
It’s a story that highlights the ever-present threat of ransomware and the crucial need for robust security measures.
We’ll uncover how this attack unfolded, examining the potential entry points, the timeline of events, and the possible motivations behind the attack. We’ll also look at Serco’s response, analyzing their incident response plan and considering what could have been done differently. The consequences for UK Research & Innovation are significant, and we’ll explore the potential financial, reputational, and research-related impacts.
Finally, we’ll discuss the crucial lessons learned and how this incident underscores the urgent need for enhanced cybersecurity protocols across the board.
Serco’s Role in UK Research and Innovation
Serco, a large international service company, plays a significant role in supporting UK Research and Innovation (UKRI), the UK’s largest public funder of research and innovation. Their involvement spans various administrative and operational aspects, crucial to the smooth functioning of UKRI’s extensive portfolio of projects. Understanding this relationship is vital to assessing the potential consequences of a ransomware attack targeting Serco’s systems.Serco’s involvement in UKRI projects encompasses a broad range of activities.
They often manage crucial back-office functions, including financial administration, grant management, and IT infrastructure support. This means they handle sensitive data related to researchers, research projects, and funding allocations. The extent of their involvement varies depending on the specific UKRI program or initiative. For instance, they might manage the procurement processes for large-scale research equipment or oversee the disbursement of grants to universities and research institutions.
This extensive reach makes them a critical link in the UKRI ecosystem.
The Potential Impact of a Ransomware Attack on UKRI Projects
A successful ransomware attack on Serco’s systems could severely disrupt UKRI’s operations and impact ongoing research projects. The loss or encryption of crucial data, such as research findings, grant applications, and financial records, could halt progress, lead to delays in funding disbursements, and compromise the integrity of research data. Furthermore, the reputational damage to both Serco and UKRI could be significant, eroding public trust in the funding body and potentially affecting future research collaborations.
The cost of recovery, including data restoration, system rebuilds, and potential legal liabilities, could also be substantial. Consider, for example, a scenario where a clinical trial’s data is encrypted – this could delay the development of life-saving treatments.
Security Measures Serco Might Have in Place to Protect UKRI Data
Given the sensitivity of the data they handle for UKRI, Serco likely employs a multi-layered security approach. This might include robust firewalls, intrusion detection systems, data encryption both in transit and at rest, regular security audits, employee training on cybersecurity best practices, and robust backup and disaster recovery plans. They are also likely subject to rigorous data protection regulations such as GDPR and UK data protection legislation, requiring them to maintain appropriate security controls.
The specific measures employed would depend on the level of risk associated with the data being handled and the specific contractual agreements with UKRI.
Types of Data Serco Handles for UKRI and Their Sensitivity Levels
The following table categorizes the types of data Serco might handle for UKRI, along with their sensitivity levels, potential storage locations, and likely security measures.
| Data Type | Sensitivity Level | Storage Location | Security Measures |
|---|---|---|---|
| Researcher Personal Information (names, addresses, contact details) | High | Secure cloud servers, on-premise data centers | Encryption at rest and in transit, access control lists, multi-factor authentication |
| Grant Applications and Funding Details | High | Secure cloud servers, on-premise data centers | Encryption at rest and in transit, access control lists, audit trails |
| Research Data (scientific findings, experimental results) | High/Medium (depending on the nature of the research) | Secure cloud servers, on-premise data centers, potentially research-specific repositories | Encryption at rest and in transit, version control, access control based on research roles |
| Financial Transactions and Records | High | Secure cloud servers, on-premise data centers | Encryption at rest and in transit, two-factor authentication, regular security audits |
| Intellectual Property (patents, copyrights) | High | Secure cloud servers, on-premise data centers, potentially specialized IP management systems | Access control, digital rights management, encryption |
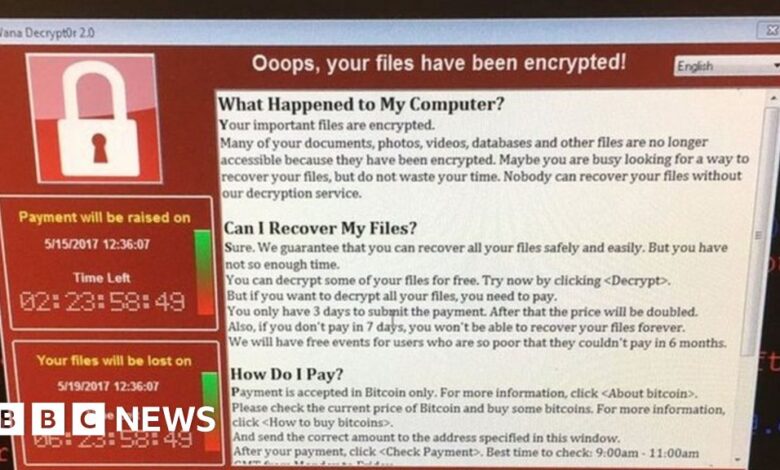
Nature of the Ransomware Attack

The ransomware attack on Serco and UK Research and Innovation (UKRI) remains shrouded in some secrecy, with official details limited. However, based on publicly available information and common ransomware attack vectors, we can speculate on the nature of the incident. Understanding the attack’s mechanics is crucial to preventing future incidents and improving cybersecurity resilience within the UK’s research infrastructure.The likely methods employed were sophisticated and likely involved a combination of techniques.
A multi-pronged approach is typical for successful ransomware attacks, maximizing the chances of breaching security.
Potential Attack Methods
Several common attack methods could have been used. Phishing emails, disguised as legitimate communications, are a prime suspect. These emails might contain malicious attachments or links leading to exploit kits. Exploit kits automatically scan for vulnerabilities in target systems, exploiting weaknesses in software or operating systems to gain unauthorized access. Another possibility is a supply chain attack, where the attackers compromised a third-party vendor Serco uses, gaining access through a less secure point in their network.
This approach often goes undetected for longer periods.
Likely Entry Point
Pinpointing the exact entry point is difficult without internal Serco investigation details. However, given Serco’s role in managing various UKRI projects, it’s plausible the attack leveraged vulnerabilities within systems handling sensitive data or collaborative research platforms. This could include weaknesses in legacy systems, poorly configured servers, or insufficiently patched software. A compromised employee account, whether through phishing or other social engineering techniques, also remains a strong possibility.
Timeline of Events and Impact
Precise timing is not publicly available. However, a typical ransomware attack unfolds in stages. First, the attackers gain initial access. Then, they move laterally within the network, mapping systems and identifying valuable data. The encryption phase follows, rendering systems and data unusable.
Finally, the ransom demand is delivered. The impact on Serco and UKRI likely included disrupted operations, data loss or corruption, financial losses, and reputational damage. The disruption to research projects would have been significant, potentially delaying crucial work and impacting the UK’s research output.
Motivations Behind the Attack
The primary motivation was almost certainly financial gain. Ransomware attacks are frequently driven by the prospect of a lucrative payout. However, espionage cannot be entirely ruled out. Serco handles sensitive data related to government contracts and research projects. Access to this information could be valuable to state-sponsored actors or competitors seeking an advantage.
The attackers may have sought both financial gain and intelligence gathering, maximizing their return on investment. The lack of public information makes definitive conclusions difficult, but a financial motive seems most probable given the nature of ransomware attacks.
Impact on UK Research and Innovation
The ransomware attack on Serco, a significant contractor for UK Research and Innovation (UKRI), presents a serious threat to the UK’s research landscape. The potential consequences extend far beyond a simple data breach; they ripple through numerous research projects, impacting funding, timelines, and ultimately, the advancement of scientific knowledge. The scale of the disruption depends heavily on the extent of data loss and the specific projects affected, but the potential for significant damage is undeniable.The attack’s impact on UKRI is multifaceted, encompassing financial losses, reputational damage, and severe disruptions to ongoing research and development activities.
The financial implications could be substantial, ranging from the costs of remediation and recovery to potential legal liabilities and compensation claims. The reputational damage could undermine public trust in UKRI’s ability to safeguard sensitive data and manage its contracts effectively, potentially impacting future funding opportunities and collaborations.
Financial and Reputational Damage to UKRI
The financial repercussions for UKRI could be extensive. Direct costs include the expense of investigating the breach, engaging cybersecurity experts for remediation, restoring corrupted data, and potentially paying a ransom (though this is generally discouraged). Indirect costs could be even higher, stemming from delays in research projects, lost grant funding due to missed deadlines, and potential legal battles arising from data breaches.
Reputational damage, leading to a loss of confidence from researchers, funders, and the public, could impact future funding applications and international collaborations. For example, a similar attack on a major university could lead to a loss of public trust and difficulties in attracting top researchers and securing funding. This reputational damage could be long-lasting and difficult to repair.
Disruption to Ongoing Research and Development Activities
The ransomware attack could severely disrupt numerous research projects currently underway. The loss or corruption of research data – including experimental results, simulations, and publications – could set back projects by months or even years. This disruption could affect everything from the timely submission of grant applications and publication deadlines to the overall progress of long-term research initiatives. The inability to access critical data could also hinder collaboration between researchers and institutions, delaying the dissemination of findings and impacting the overall efficiency of the research process.
Consider, for instance, a clinical trial suddenly halted due to inaccessible patient data; the consequences would be significant and far-reaching.
Types of Research Affected by the Attack
The breadth of research affected is potentially vast, given Serco’s involvement in various UKRI-funded projects. The attack’s impact could span numerous fields.
- Biomedical Research: Loss of patient data, clinical trial results, and genomic information could have serious implications for patient care and the development of new treatments.
- Environmental Science: Compromised environmental monitoring data could hinder climate change research and environmental protection efforts.
- Engineering and Technology: Loss of design specifications, simulation data, and test results could delay the development of new technologies.
- Social Sciences: Compromised survey data and research findings could impact social policy development and public understanding of social issues.
- Physical Sciences: Loss of experimental data and research findings could impede scientific breakthroughs and technological advancements.
Serco’s Response to the Attack
Serco’s response to the ransomware attack on its systems, impacting UK Research and Innovation (UKRI), was a crucial determinant of the overall damage and recovery time. Their actions, both immediate and long-term, highlight the complexities of dealing with such a significant cybersecurity breach. A thorough examination of their response is essential to understand the effectiveness of their incident response plan and to identify areas for improvement in future preparedness.Serco’s initial response involved isolating affected systems to prevent further spread of the ransomware.
This containment strategy, while standard procedure, was vital in limiting the extent of the damage. They also engaged cybersecurity experts to analyze the attack, identify the source, and develop a recovery strategy. This included working closely with UKRI and relevant law enforcement agencies. The recovery process involved restoring data from backups, implementing new security measures, and conducting a thorough system audit to identify vulnerabilities.
While the precise details of their response remain partially undisclosed for security reasons, publicly available information indicates a multi-faceted approach that involved both technical and operational elements.
Containment and Recovery Efforts
The containment phase focused on quickly isolating affected systems and networks to prevent the ransomware from spreading further. This likely involved disconnecting affected servers from the network, implementing network segmentation, and disabling user accounts to limit potential lateral movement. The recovery phase, however, was likely more complex and prolonged. It involved data restoration from backups, a critical process requiring meticulous verification to ensure data integrity and avoid reintroducing malware.
This was likely followed by a rigorous system patching and update process to address identified vulnerabilities. Finally, a thorough review of security protocols and employee training programs was probably undertaken to prevent future incidents.
Effectiveness of Serco’s Incident Response Plan
Assessing the effectiveness of Serco’s incident response plan requires evaluating its speed, efficiency, and overall success in mitigating the damage. While the precise details remain confidential, the incident’s impact suggests areas for potential improvement. A swift response was crucial in minimizing the damage, and the engagement of external cybersecurity experts indicates a proactive approach. However, the fact that a ransomware attack was successful in the first place points to potential weaknesses in their pre-existing security posture and incident response plan.
A thorough post-incident review, a standard practice in such scenarios, is essential to identify these shortcomings and enhance future preparedness. The duration of the disruption also provides insight into the effectiveness of their recovery procedures.
Comparison with Similar Incidents, Ransomware attack on serco and uk research and innovation
Comparing Serco’s response to similar incidents in other organizations provides valuable context. Organizations like Colonial Pipeline and NotPetya victims have shown that ransomware attacks can have devastating consequences. The effectiveness of Serco’s response can be benchmarked against these cases, considering factors like the speed of containment, the recovery time, and the overall financial and operational impact. A comparative analysis would reveal whether Serco’s response was faster, more efficient, or less damaging than similar incidents in other organizations.
For example, Colonial Pipeline’s response, while ultimately successful, involved significant downtime and financial losses, which can be used as a comparative metric for evaluating Serco’s performance.
Hypothetical Improved Incident Response Plan for Serco
An improved incident response plan for Serco should incorporate several key enhancements. First, a more robust and regularly tested backup and recovery system is crucial. This includes offsite backups, immutable backups (unalterable copies), and a well-defined recovery procedure. Second, a stronger emphasis on proactive security measures, including regular security audits, penetration testing, and employee security awareness training, is necessary.
Third, clear roles and responsibilities should be defined within the incident response team, ensuring efficient communication and coordination during a crisis. Finally, a detailed communication plan should be established to keep stakeholders, including clients, regulators, and the public, informed during and after the incident. This plan should include pre-approved messaging and designated communication channels. This multifaceted approach, incorporating proactive security measures and a refined response protocol, aims to mitigate the impact of future cyberattacks.
Lessons Learned and Future Implications

The ransomware attack on Serco, impacting UK Research and Innovation (UKRI), serves as a stark reminder of the ever-evolving cyber threat landscape and the critical need for robust cybersecurity measures within organizations handling sensitive research data. This incident exposed vulnerabilities not just within Serco’s systems, but also highlighted the interconnectedness and potential weaknesses within the broader UKRI ecosystem. Addressing these weaknesses is crucial to safeguarding future research endeavors and maintaining public trust.The attack underscores the limitations of relying solely on perimeter security.
The attackers clearly bypassed existing defenses, demonstrating the need for a multi-layered, proactive approach to cybersecurity. A reactive approach, focused primarily on incident response, is insufficient in today’s threat environment. A shift towards preventative measures and a more comprehensive understanding of potential attack vectors is paramount.
Vulnerabilities in UKRI Cybersecurity Practices
The incident highlights several key vulnerabilities within the UKRI ecosystem. Firstly, the reliance on a single contractor, Serco, for critical IT infrastructure and data management created a single point of failure. A compromise of Serco’s systems directly impacted UKRI’s operations and data security. Secondly, the attack exposed potential weaknesses in data access controls and privilege management within Serco’s systems.
Insufficient monitoring and detection capabilities allowed the ransomware to spread undetected for a period of time. Finally, the lack of adequate backup and recovery mechanisms exacerbated the impact of the attack, leading to potential data loss and disruption. These vulnerabilities necessitate a comprehensive review and strengthening of cybersecurity protocols across the entire UKRI ecosystem.
Necessary Improvements to Cybersecurity Protocols
Several improvements are urgently needed to prevent future attacks. This includes diversifying IT infrastructure providers to mitigate single points of failure, implementing robust multi-factor authentication across all systems, and strengthening data access controls based on the principle of least privilege. Furthermore, enhanced intrusion detection and prevention systems, coupled with regular security audits and penetration testing, are essential. Investing in advanced threat intelligence capabilities will allow for proactive identification and mitigation of emerging threats.
Regular employee cybersecurity awareness training is also crucial to reduce the risk of human error, a frequent entry point for attackers. Finally, a comprehensive incident response plan, including robust data backup and recovery mechanisms, must be in place and regularly tested.
Recommendations for Enhancing Data Security and Resilience
For Serco, implementing zero-trust security architecture is a critical step. This involves verifying every user and device attempting to access the network, regardless of location. Regular vulnerability assessments and penetration testing, coupled with prompt patching of identified vulnerabilities, are crucial. Serco should also invest in advanced threat detection and response capabilities, including endpoint detection and response (EDR) solutions.
For UKRI, fostering stronger collaboration and information sharing with its contractors is essential. Regular security assessments of all contractors’ systems and processes should be conducted, and a common cybersecurity framework should be adopted across the entire ecosystem. This should include standardized security policies, procedures, and incident response protocols.
Visual Representation of Information Flow and Attack Vectors
Imagine a network diagram. At the center is Serco’s data center, represented as a large, heavily guarded vault. Several smaller vaults, representing different UKRI research projects and data sets, are connected to the central vault through multiple digital pathways. These pathways represent various network connections and data transfer mechanisms. The attackers, depicted as shadowy figures outside the perimeter, utilize various attack vectors: phishing emails targeting Serco employees (represented by arrows entering the perimeter through a weak point in the wall), exploiting vulnerabilities in Serco’s software (arrows penetrating the vault walls), and potentially leveraging compromised credentials to gain access (a keyhole being picked).
Once inside the central vault, the attackers spread laterally to other connected vaults, encrypting data and disrupting operations. The diagram clearly illustrates how a breach in one area can cascade throughout the entire system, highlighting the importance of a holistic and layered security approach.
The recent ransomware attack on Serco and UK Research and Innovation highlights the urgent need for robust, secure systems. Building resilient applications is key, and that’s where exploring options like domino app dev, the low-code and pro-code future , becomes crucial. These modern development approaches could help organizations like Serco better protect their data and infrastructure against future cyber threats.
The vulnerability exposed by this attack underscores the need for proactive security measures in application development.
Ultimate Conclusion
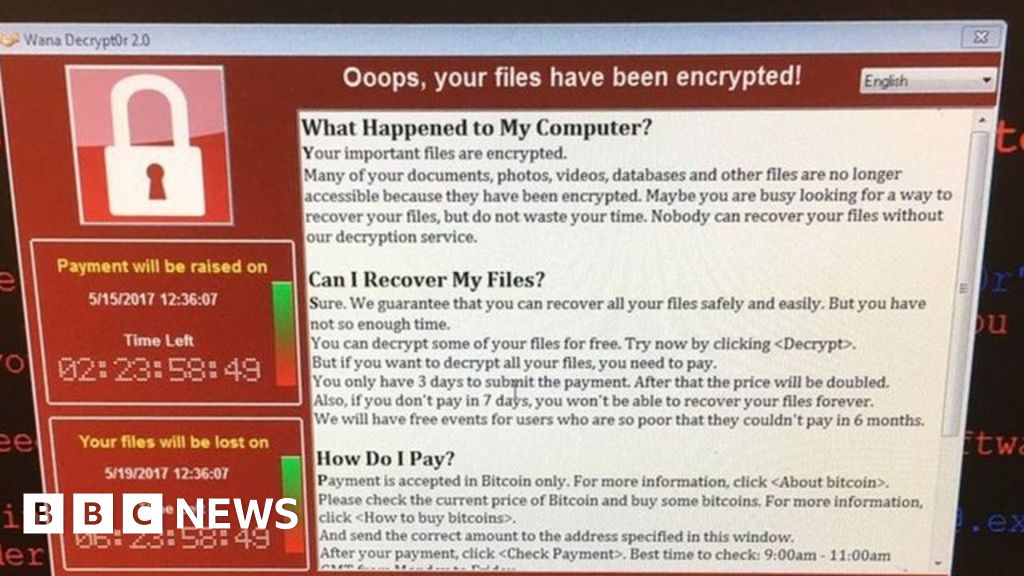
The ransomware attack on Serco and UK Research & Innovation serves as a stark reminder of the vulnerabilities inherent in even the most sophisticated systems. While the full extent of the damage may take time to fully assess, the incident highlights the critical need for proactive cybersecurity measures and robust incident response plans. The lessons learned from this attack should be a catalyst for significant improvements in data security and resilience, not just for Serco and UKRI, but for all organizations handling sensitive information.
The future of research depends on it.
Key Questions Answered: Ransomware Attack On Serco And Uk Research And Innovation
What type of data was potentially compromised in the Serco ransomware attack?
The exact nature of the compromised data hasn’t been publicly released, but it likely included sensitive research data, intellectual property, and potentially personal information depending on the projects Serco managed for UKRI.
What is the estimated financial cost of the attack?
The financial cost is difficult to estimate precisely and likely includes direct costs (ransom, recovery, investigation), indirect costs (lost productivity, reputational damage), and potential legal liabilities.
Did Serco pay the ransom?
Whether or not Serco paid the ransom is generally not publicly disclosed due to security and legal considerations. Paying a ransom often doesn’t guarantee data recovery and can incentivize further attacks.
What legal ramifications could Serco face?
Depending on the nature of the data breached and the adequacy of Serco’s security measures, they could face investigations and potential fines under data protection regulations like the GDPR.