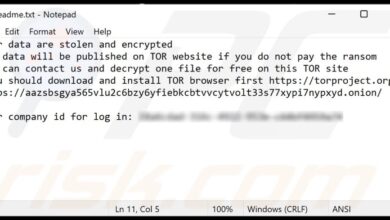
Ransomware Attack on Timberline Billing Service
Ransomware Attack on Timberline Billing Service: Imagine this – your business, reliant on Timberline for billing, suddenly crippled by a ransomware attack. Data locked, operations halted, and a ticking clock demanding a ransom. This isn’t a hypothetical threat; it’s a very real danger facing businesses that use this popular accounting software. This post dives deep into the vulnerabilities, impacts, and strategies for preventing and recovering from such a devastating attack.
We’ll explore the common attack vectors used to target Timberline, the financial and operational havoc a successful attack can wreak, and the crucial steps businesses must take to protect themselves. From robust data backup strategies to comprehensive security awareness training, we’ll cover everything you need to know to safeguard your business from the nightmare of a ransomware attack on your Timberline system.
Real-world examples and a fictional case study will illustrate the gravity of the situation and provide valuable insights.
Timberline Billing Service Vulnerability Assessment

The recent ransomware attack targeting Timberline Billing Service highlights the critical need for robust cybersecurity measures within accounting software. While the specifics of the attack remain undisclosed, a thorough vulnerability assessment is crucial to understand potential weaknesses and prevent future incidents. This assessment will examine potential vulnerabilities within Timberline’s system, common attack vectors, and the resulting impact on users.
Potential Vulnerabilities in Timberline’s System
Timberline, like many legacy accounting systems, may possess vulnerabilities stemming from outdated software, insufficient patching, and weak security configurations. These could include unpatched security flaws in the core application, vulnerabilities in third-party integrations (such as payment gateways or cloud storage services), and inadequate access controls allowing unauthorized access to sensitive data. Furthermore, the reliance on older technologies might expose Timberline to exploits targeting known vulnerabilities in outdated operating systems or databases.
The lack of multi-factor authentication could further weaken the system’s security posture, making it easier for attackers to gain unauthorized access. A lack of regular security audits and penetration testing could also leave hidden vulnerabilities undetected.
Common Attack Vectors in Ransomware Attacks Targeting Accounting Software
Ransomware attacks against accounting software often leverage several common attack vectors. Phishing emails containing malicious attachments or links remain a primary method, tricking users into downloading malware. Exploiting known vulnerabilities in the software itself or its integrations is another common tactic. Compromised credentials, obtained through phishing or brute-force attacks, provide attackers with direct access to the system. Finally, malware infections on employee workstations, often through infected USB drives or compromised websites, can provide a pathway for ransomware to spread throughout the network and ultimately reach the accounting software.
Potential Impact of a Successful Ransomware Attack on Timberline’s Users
A successful ransomware attack on Timberline could have devastating consequences for its users. The immediate impact would be the encryption of critical financial data, including invoices, payments, and client information. This disruption could halt business operations, leading to significant financial losses due to inability to process payments, generate invoices, or access essential financial records. Beyond the immediate financial impact, the attack could damage the reputation of businesses using Timberline, leading to loss of client trust and potential legal repercussions.
The cost of recovery, including data restoration, system remediation, and potential legal fees, could be substantial. Furthermore, the theft or exposure of sensitive client data could lead to further regulatory penalties and compliance issues.
Comparison of Ransomware Families and Attack Methods
The following table compares several prominent ransomware families and their typical attack methods:
| Ransomware Family | Attack Method | Encryption Method | Extortion Tactics |
|---|---|---|---|
| Ryuk | Exploiting vulnerabilities, credential theft | AES-256 | Data encryption, data leak threats |
| REvil (Sodinokibi) | Phishing, exploit kits | AES-256 | Data encryption, data leak threats |
| LockBit | Compromised credentials, network access | AES | Data encryption, data leak threats |
| Conti | Phishing, RDP brute-forcing | AES | Data encryption, data leak threats |
Impact of Ransomware on Timberline Users
A ransomware attack targeting Timberline, a widely used accounting software, can have devastating consequences for businesses of all sizes. The impact extends far beyond the immediate cost of a ransom payment, encompassing significant financial losses, operational disruptions, and potentially severe legal ramifications. Understanding these potential consequences is crucial for businesses to implement robust cybersecurity measures and develop a comprehensive incident response plan.The financial consequences of a ransomware attack on businesses utilizing Timberline can be substantial.
Direct costs include the ransom payment itself (which may be substantial and doesn’t guarantee data recovery), the cost of hiring cybersecurity experts to remediate the attack, and potential legal fees. Indirect costs are often far greater and include lost revenue due to business interruption, the expense of recovering or recreating lost data, the cost of notifying affected customers and partners, and potential reputational damage leading to lost future business.
The longer the downtime, the more significant these indirect costs become.
Disruption to Business Operations
A ransomware attack crippling Timberline’s functionality directly impacts a business’s core operations. Access to crucial financial data—including invoices, payments, payroll information, and tax records—becomes impossible. This immediately halts invoicing, payment processing, and financial reporting, causing significant delays and potentially leading to missed deadlines for tax filings or payments. Furthermore, the disruption extends to other departments reliant on this financial information, leading to project delays, supply chain disruptions, and overall operational inefficiency.
The severity of the disruption is directly proportional to the size of the business and its dependence on Timberline for daily operations. Even partial data loss can cause significant delays and errors.
Legal and Regulatory Implications
Ransomware attacks targeting Timberline data can trigger significant legal and regulatory implications. Businesses are obligated to comply with data privacy regulations like GDPR (in Europe) and CCPA (in California), which mandate the notification of affected individuals in the event of a data breach. Failure to comply with these regulations can result in substantial fines and legal action. Furthermore, depending on the nature of the data compromised (e.g., sensitive personal information, financial records), businesses might face legal action from affected individuals or regulatory bodies.
The investigation and remediation process itself can be lengthy and expensive, adding to the overall burden on the business. Insurance coverage may be crucial in mitigating some of these costs, but obtaining adequate coverage requires proactive planning and risk assessment.
Real-World Examples of Ransomware Attacks on Accounting Software
The threat of ransomware targeting accounting software is not hypothetical. Numerous real-world examples illustrate the severe damage it can inflict.
- In 2022, a small manufacturing company experienced a ransomware attack that encrypted their data held within their accounting software, resulting in a three-week shutdown. The company lost significant revenue during this period and incurred substantial costs for data recovery and cybersecurity remediation.
- A larger healthcare provider suffered a ransomware attack in 2021 targeting their accounting system. The attack resulted in the theft of patient financial data, triggering costly regulatory investigations and substantial legal fees associated with notification and remediation efforts. Their reputation was also significantly damaged.
- A regional law firm experienced a ransomware attack in 2023 that compromised client billing information. The firm had to pay a significant ransom to regain access to their data, and they faced substantial legal and reputational damage.
These examples highlight the far-reaching and costly consequences of ransomware attacks targeting accounting software like Timberline. Proactive security measures, regular backups, and comprehensive incident response planning are essential to mitigate the risks and minimize the impact of such attacks.
Data Recovery and Mitigation Strategies

A ransomware attack targeting Timberline billing software can be devastating, leading to significant financial losses and operational disruptions. Effective data recovery and mitigation strategies are crucial for minimizing the impact and ensuring business continuity. This section Artikels best practices for preventing data loss, restoring data from backups, removing ransomware, and responding to such an attack.
Best Practices for Backing Up Timberline Data
Regular and robust backups are the cornerstone of any ransomware defense. Simply having backups isn’t enough; they must be reliable, easily accessible, and protected from the attack itself. This involves employing the 3-2-1 backup rule: maintain at least three copies of your data, on two different media types, with one copy offsite. For Timberline data, consider using a combination of methods.
For example, you could use an on-site network-attached storage (NAS) device for a quick local backup, a cloud-based backup service for offsite protection, and an external hard drive for a secondary local copy. Remember to test your backups regularly to ensure they are restorable. Regularly verify your backup and restoration procedures. This means performing a full or partial restore to a test system to confirm data integrity and functionality.
Restoring Data from Backups After a Ransomware Attack, Ransomware attack on timberline billing service
Once a ransomware attack is confirmed, immediately isolate affected systems from the network to prevent further spread. Then, begin the data recovery process using your verified backups. This involves booting from a clean system (ideally a recovery image or a separate machine) and using the backup software to restore data to a clean system. Before restoring to production systems, thoroughly scan the restored data for any remaining traces of ransomware.
The speed and success of the restoration will depend on the type and frequency of your backups, as well as the extent of the encryption. Prioritizing the restoration of critical data and systems is essential to minimize business disruption.
Methods for Identifying and Removing Ransomware
Identifying and removing ransomware requires a multi-pronged approach. First, use reputable anti-malware software to scan all affected systems. This will help identify and quarantine any malicious files. Next, manually examine system logs and event viewers for suspicious activity, such as unusual file creations, modifications, or network connections. Consider using specialized ransomware removal tools, but exercise caution and only use those from trusted sources.
Remember that simply deleting encrypted files won’t remove the ransomware; it must be eradicated from the system. After removal, reinstall operating systems and applications from clean sources to ensure a fresh start. Thoroughly check the system for residual files that may not have been removed by the initial scan.
Incident Response Plan for a Ransomware Attack
A well-defined incident response plan is crucial for minimizing the impact of a ransomware attack. This plan should include clear roles and responsibilities, communication protocols, and escalation procedures. Here’s a step-by-step example:
- Preparation: Establish a comprehensive security baseline, including regular backups, security awareness training, and robust security software.
- Detection: Implement monitoring systems to detect unusual activity that may indicate a ransomware attack.
- Containment: Isolate affected systems from the network to prevent further spread.
- Eradication: Identify and remove the ransomware using appropriate tools and techniques.
- Recovery: Restore data from backups and verify system functionality.
- Post-Incident Activity: Conduct a thorough post-incident analysis to identify vulnerabilities and implement corrective measures. This should also include documenting the event for future reference and potential legal proceedings.
This plan should be tested and updated regularly to ensure its effectiveness. Regular simulations of attack scenarios will help identify weaknesses and refine response procedures. Consider including legal counsel in your plan, as ransomware attacks often have legal ramifications.
Prevention and Security Measures
The Timberline ransomware attack highlights the critical need for robust cybersecurity practices. Ignoring preventative measures is akin to leaving your front door unlocked – inviting disaster. Proactive security is not just about reacting to threats; it’s about building a resilient system that can withstand attacks. Investing in comprehensive security is an investment in the long-term health and stability of your business.
Implementing a multi-layered security approach is crucial. This involves combining various security solutions and strategies to create a strong defense against ransomware and other cyber threats. No single solution is foolproof, but a layered approach significantly reduces vulnerabilities and the impact of successful attacks.
The Timberline ransomware attack really got me thinking about data security. It highlights the need for robust, reliable systems, which is why I’ve been diving into domino app dev the low code and pro code future – exploring how these development approaches might offer more secure and agile solutions. Ultimately, though, the Timberline incident underscores the importance of proactive security measures, regardless of the tech stack you use.
Essential Security Measures for Preventing Ransomware Attacks
A proactive approach to security necessitates a range of measures, from technical solutions to employee training. The following list Artikels key strategies to bolster your defenses.
- Regular Software Updates: Patching vulnerabilities promptly is paramount. Outdated software is a prime target for ransomware. Automated update systems should be enabled wherever possible.
- Strong Password Policies: Enforce strong, unique passwords for all accounts, utilizing password managers to assist. Regular password changes are also beneficial.
- Multi-Factor Authentication (MFA): Implementing MFA adds an extra layer of security, requiring more than just a password to access accounts. This significantly reduces the risk of unauthorized access.
- Data Backups: Regularly backing up data to an offline, secure location is crucial for recovery in case of a ransomware attack. The 3-2-1 backup rule (3 copies of data, on 2 different media, with 1 copy offsite) is a widely accepted best practice.
- Network Security: Employ firewalls, intrusion detection/prevention systems (IDS/IPS), and robust network segmentation to control access and monitor network traffic for suspicious activity.
- Email Security: Utilize email security solutions, including spam filters and anti-phishing measures, to prevent malicious emails from reaching employees’ inboxes.
- Endpoint Detection and Response (EDR): EDR solutions monitor endpoints for malicious activity and provide real-time threat detection and response capabilities. They are invaluable in identifying and containing ransomware infections before they spread.
Comparing Security Solutions
Different security solutions offer varying levels of protection. Choosing the right combination depends on your specific needs and resources. A layered approach is always recommended.
| Security Solution | Description | Effectiveness Against Ransomware |
|---|---|---|
| Endpoint Detection and Response (EDR) | Monitors endpoints for malicious activity, providing real-time threat detection and response. | High – detects and prevents ransomware execution, often before encryption occurs. |
| Intrusion Detection/Prevention Systems (IDS/IPS) | Monitors network traffic for malicious activity, alerting administrators to potential threats and blocking malicious traffic. | Moderate – can detect network-based attacks but may not prevent all ransomware infections. |
| Antivirus Software | Scans files and applications for known malware, including ransomware. | Moderate – effective against known ransomware variants but may miss new or sophisticated threats. |
| Firewall | Controls network traffic, blocking unauthorized access to systems and networks. | Moderate – helps prevent unauthorized access but doesn’t directly prevent ransomware execution. |
Comprehensive Security Awareness Training
Human error is often the weakest link in cybersecurity. A robust security awareness training program is essential to educate employees about ransomware threats and best practices for preventing social engineering attacks. This training should be ongoing and reinforced regularly.
- Phishing Simulations: Regular phishing simulations help employees identify and report suspicious emails, improving their ability to avoid social engineering attacks.
- Security Policies and Procedures: Clear and concise security policies and procedures should be communicated to all employees, emphasizing their roles in maintaining a secure environment.
- Best Practices Training: Training should cover best practices for password management, recognizing phishing attempts, identifying malicious attachments, and reporting suspicious activity.
- Consequences of Security Breaches: Employees need to understand the potential consequences of security breaches, both for the organization and themselves, to emphasize the importance of following security protocols.
Legal and Insurance Considerations: Ransomware Attack On Timberline Billing Service
A ransomware attack on a billing service like Timberline carries significant legal and financial ramifications. Understanding your legal obligations and having appropriate insurance coverage is crucial for mitigating the damage and ensuring business continuity. This section Artikels the key legal and insurance aspects businesses should consider following such an attack.
Legal Obligations Following a Ransomware Attack
Businesses have several legal obligations following a ransomware attack, varying by jurisdiction. These obligations often involve notification requirements for affected customers and regulatory bodies. For example, under the GDPR (General Data Protection Regulation) in Europe, organizations must notify the relevant supervisory authority within 72 hours of becoming aware of a data breach that is likely to result in a risk to the rights and freedoms of individuals.
Similar notification laws exist in many other countries, such as the California Consumer Privacy Act (CCPA) in the United States. Furthermore, businesses may face legal action from customers whose data was compromised, leading to potential lawsuits and financial penalties. Failure to comply with these regulations can result in hefty fines and reputational damage. A thorough understanding of applicable data privacy laws and breach notification procedures is paramount.
Cyber Insurance Policies for Ransomware Mitigation
Cyber insurance policies can significantly reduce the financial burden of a ransomware attack. Several types of policies can help, including:
- First-party coverage: This covers the costs incurred by the business itself, such as data recovery, system restoration, and business interruption expenses. For example, this could cover the cost of hiring cybersecurity experts to restore your systems and the lost revenue during the downtime.
- Third-party coverage: This protects the business from liability claims from customers or other parties whose data was compromised. This would cover legal fees and settlements if you are sued by customers for a data breach.
- Ransomware coverage: Some policies specifically cover the ransom payment itself, though this is often subject to strict conditions and limitations. For example, the policy might require you to report the incident immediately and cooperate fully with the investigation.
- Cybersecurity incident response: This coverage helps fund the costs associated with responding to the attack, including forensic investigation, legal advice, and public relations support. This can cover the cost of hiring professionals to investigate the attack, clean up the system, and communicate with affected parties.
It is crucial to carefully review policy terms and conditions to understand the extent of coverage and any exclusions before purchasing a cyber insurance policy. The specific coverage needed will vary depending on the size and nature of the business and the type of data it handles.
Reporting a Ransomware Attack to Relevant Authorities
Reporting a ransomware attack is a critical step in mitigating its impact and fulfilling legal obligations. This typically involves contacting:
- Law enforcement: Agencies like the FBI (in the US) or equivalent agencies in other countries should be notified to investigate the attack and potentially identify and prosecute the perpetrators. Providing detailed information about the attack, including any ransom demands received, is essential.
- Data protection authorities: Depending on the jurisdiction and the data involved, the relevant data protection authority (e.g., the ICO in the UK, or state Attorney Generals in the US) must be notified if a data breach has occurred. Failure to do so can result in significant penalties.
The timing and specific details required for reporting vary by jurisdiction, so it’s crucial to understand the specific legal requirements in your area.
Communicating with Stakeholders After a Ransomware Attack
Effective communication with stakeholders—customers, employees, and investors—is crucial after a ransomware attack. This should involve:
- Transparency: Be open and honest with stakeholders about the incident, the extent of the impact, and the steps being taken to address it. Avoid downplaying the severity of the situation.
- Timeliness: Communicate promptly and keep stakeholders updated on the progress of the investigation and recovery efforts. Regular updates build trust and demonstrate responsibility.
- Clear and concise messaging: Use clear and easily understandable language to explain the situation and what steps stakeholders should take. Avoid technical jargon.
- Dedicated communication channels: Establish dedicated communication channels, such as a website or hotline, to handle inquiries and provide support.
Proactive and transparent communication can help mitigate reputational damage and maintain stakeholder confidence.
Illustrative Case Study
Northwest Construction, a mid-sized general contractor, relied heavily on Timberline Office for its billing and project management. Their smooth operation, however, was shattered when a ransomware attack crippled their systems. The attack began subtly, with a few slowdowns and unusual pop-up messages. Initially dismissed as minor technical glitches, the true nature of the intrusion became horrifyingly clear when critical files were encrypted, replaced with the infamous ransomware message demanding a hefty sum for decryption.
The Initial Response and Data Recovery
The IT team immediately disconnected Northwest Construction’s network from the internet to prevent further spread. They contacted their managed service provider, who confirmed the ransomware infection. A forensic analysis revealed the attack vector: a phishing email containing a malicious attachment cleverly disguised as a legitimate invoice. The company had no robust backup system in place for their Timberline data, relying instead on infrequent manual backups stored on a local server—a server that was also encrypted.
Data recovery efforts focused on restoring from the last available backup, which was unfortunately several weeks old, resulting in significant data loss. They also engaged a cybersecurity firm specializing in ransomware recovery to assist with data decryption and forensic investigation. The cost of this professional assistance added considerably to the overall financial burden.
Financial Losses and Reputational Damage
The ransomware attack cost Northwest Construction dearly. Beyond the ransom itself (which they ultimately refused to pay, opting instead for data recovery efforts), they faced substantial losses due to project delays, lost productivity, and the expense of remediation and recovery. Clients were understandably frustrated by the delays in billing and project updates, impacting the company’s reputation. Several projects were delayed, leading to penalty clauses in contracts, further exacerbating financial losses.
The incident also raised concerns among potential clients, impacting their ability to secure new business. Accurate financial quantification of these losses was difficult in the immediate aftermath but was projected to be in the hundreds of thousands of dollars.
Emotional and Operational Toll
The ransomware attack was deeply stressful for Northwest Construction’s employees. The uncertainty surrounding data recovery, the fear of job losses, and the sheer disruption to their daily routines created a climate of anxiety and apprehension. Morale plummeted, and productivity suffered even after the immediate crisis subsided. The operational toll extended beyond the immediate IT issues. The billing department struggled to catch up, resulting in delayed payments from clients.
Project managers had to scramble to reconstruct project schedules and budgets, creating extra workload and stress. The incident served as a stark reminder of the vulnerability of even established businesses to cyberattacks and highlighted the significant emotional burden such events place on employees.
Closure
A ransomware attack on your Timberline billing service isn’t just a technological problem; it’s a business crisis. The potential financial losses, operational disruptions, and legal ramifications are significant. However, by proactively implementing robust security measures, investing in comprehensive backups, and educating your employees, you can significantly reduce your vulnerability. Remember, prevention is always better than cure, and understanding the threat is the first step towards effective protection.
Don’t wait until it’s too late – take control of your cybersecurity today.
Key Questions Answered
What types of data are most at risk in a Timberline ransomware attack?
Client information, financial records, invoices, and payment details are all prime targets.
How long does it typically take to recover from a Timberline ransomware attack?
Recovery time varies greatly depending on the severity of the attack, the availability of backups, and the resources available. It could range from days to weeks or even longer.
Can insurance cover the costs associated with a Timberline ransomware attack?
Yes, cyber insurance policies often cover costs related to ransomware attacks, including data recovery, legal fees, and business interruption expenses. However, coverage varies depending on the policy.
What is the role of law enforcement in a Timberline ransomware incident?
Law enforcement agencies can investigate the attack, potentially track down the perpetrators, and provide support to victims. Reporting the incident is crucial.