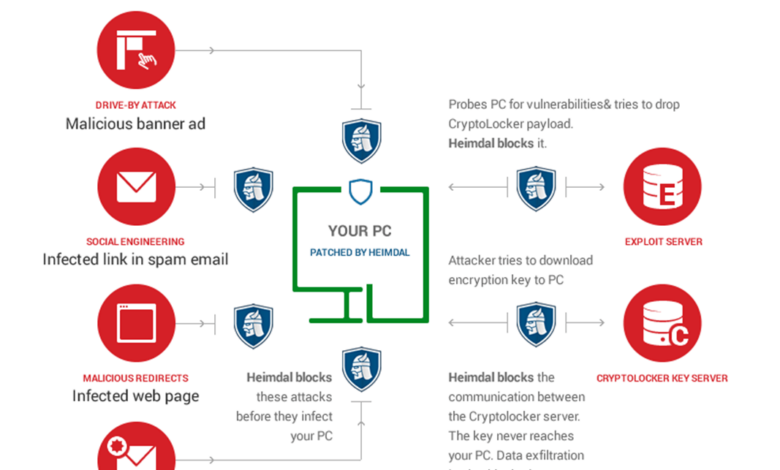
Ransomware Hype and Prevention Strategies 3
Ransomware Hype and Prevention Strategies 3: We’re living in a digital world where the threat of ransomware feels almost omnipresent. News headlines scream about massive data breaches and crippling attacks, leaving many feeling helpless and overwhelmed. But is the hype justified? Are we truly facing an unprecedented level of ransomware risk, or is the media fueling a sense of panic?
This post dives deep into the reality of ransomware threats, separating fact from fiction and equipping you with the knowledge and strategies to protect yourself and your data.
We’ll explore the evolution of ransomware, debunk common misconceptions, and examine both technical and human-centric prevention strategies. From robust security architectures and data backup procedures to employee training and incident response planning, we’ll cover the essential steps to minimize your risk. We’ll also look at emerging trends and future threats, ensuring you’re prepared for what lies ahead in the ever-evolving landscape of cybersecurity.
Understanding the Ransomware Threat Landscape: Ransomware Hype And Prevention Strategies 3
The ransomware threat has evolved dramatically over the past few years, becoming increasingly sophisticated and impactful. No longer a niche threat, ransomware now targets individuals, small businesses, and large corporations alike, causing significant financial and operational disruption. Understanding this evolving landscape is crucial for effective prevention and mitigation.
Ransomware Attack Evolution (2020-2023)
The past three years have witnessed a significant shift in ransomware tactics. Early attacks often relied on simple phishing emails and relatively unsophisticated malware. However, we’ve seen a move towards more targeted attacks, leveraging advanced techniques like double extortion (encrypting data and then leaking it publicly if the ransom isn’t paid), supply chain attacks (compromising a vendor to gain access to multiple targets), and the use of ransomware-as-a-service (RaaS) platforms, which democratize access to powerful ransomware tools for even less technically skilled actors.
The rise of RaaS has dramatically increased the volume and frequency of attacks, making it harder to defend against. Furthermore, the sophistication of evasion techniques employed by attackers has also grown, making detection and prevention more challenging.
Okay, so we’ve been talking about ransomware hype and prevention strategies 3 – it’s seriously stressing me out! But you know what helps me de-stress? Learning about new tech, like exploring the possibilities of application development with the domino app dev the low code and pro code future , which could potentially revolutionize how we secure systems.
Getting back to ransomware though, robust backups and multi-factor authentication remain key in our ongoing fight against these digital threats.
Ransomware Types and Sectoral Impact
Various ransomware families exist, each with unique capabilities and targeting preferences. Some, like Ryuk and Conti, historically focused on large enterprises, while others, like LockBit, have broader targets, including individuals and smaller businesses. The healthcare sector has been particularly hard hit, facing disruptions to patient care and data breaches with significant compliance and reputational consequences. The financial sector, with its sensitive data and critical infrastructure, is another major target, potentially facing significant financial losses and regulatory penalties.
Manufacturing and critical infrastructure industries are also vulnerable, facing potential production downtime and safety risks.
Financial Costs of Ransomware Attacks
The financial burden of ransomware attacks is substantial and often underestimated. Direct costs include the ransom payment itself (if made), the cost of data recovery or restoration, and the fees for cybersecurity consultants and forensic investigators. Indirect costs are often far greater and include business interruption, lost productivity, reputational damage, legal fees, regulatory fines, and the cost of restoring customer trust.
A recent study estimated the average cost of a ransomware attack to be in the millions of dollars, with some incidents costing tens or even hundreds of millions. For example, the Colonial Pipeline attack in 2021 cost an estimated $4.4 million in ransom and millions more in remediation costs and lost revenue.
Comparison of Ransomware Families
The following table compares the features and capabilities of five prominent ransomware families:
| Ransomware Family | Encryption Method | Extortion Tactics | Target Sector |
|---|---|---|---|
| Ryuk | AES-256 | Data encryption, data exfiltration | Large enterprises |
| Conti | AES-256 | Data encryption, data exfiltration, DDoS attacks | Large enterprises |
| LockBit | AES-256 | Data encryption, data leak sites | Broad range of targets |
| REvil (Sodinokibi) | AES-256 | Data encryption, data exfiltration, double extortion | Broad range of targets |
| Phobos | RSA | Data encryption, data leak sites | Broad range of targets |
Debunking the Hype

Ransomware attacks are frequently portrayed in the media as an unstoppable force, capable of crippling businesses and individuals alike. This sensationalized coverage often overshadows the reality of the threat, leading to a skewed perception of risk and ineffective preventative measures. Understanding the facts behind the hype is crucial for developing a robust cybersecurity strategy.The role of media coverage in shaping public perception of ransomware is significant.
News outlets often focus on high-profile attacks, highlighting the financial losses and operational disruptions. This emphasis on the dramatic aspects can create a sense of inevitability and fear, overlooking the fact that many organizations successfully prevent or mitigate ransomware incidents. Furthermore, the language used in reporting – terms like “cyber-attack” and “digital hostage-taking” – often amplifies the perceived severity of the threat.
Media Influence and Exaggerated Risk
The constant stream of ransomware headlines contributes to an exaggerated perception of risk. Many smaller, less impactful attacks go unreported, creating a skewed understanding of the overall threat landscape. This is further exacerbated by the lack of readily available data on successful ransomware prevention efforts. The focus tends to be on the failures, leading to a perception that ransomware is virtually unavoidable.
For example, a small business losing a few hundred dollars in a ransomware attack might be overshadowed by a major corporation losing millions, yet both are equally victims of the same threat.
Comparing Ransomware to Other Cybersecurity Threats
While ransomware is a serious threat, it’s essential to compare its actual impact with other cybersecurity risks. Phishing attacks, for instance, are far more common and often lead to significant data breaches with long-term consequences. Supply chain attacks, which compromise software or hardware, can have a broader and more devastating impact than a single ransomware incident. The focus on ransomware, while understandable given its immediate financial impact, should not overshadow the importance of mitigating other, potentially more pervasive threats.
A balanced perspective considers the entire cybersecurity threat landscape, allocating resources effectively to address all potential vulnerabilities. Focusing solely on ransomware, while neglecting other threats, can leave an organization exposed to even greater risks.
Proactive Prevention Strategies
Ransomware attacks are becoming increasingly sophisticated, making proactive prevention crucial. A multi-layered security approach is no longer a luxury but a necessity for organizations of all sizes. This section details technical measures that form the bedrock of a robust ransomware defense strategy. Implementing these strategies reduces the likelihood of a successful attack and minimizes the impact should one occur.
Building a comprehensive security architecture requires a holistic view of your IT infrastructure, encompassing endpoints, networks, and data storage. This layered approach ensures that even if one layer of defense is breached, others are in place to contain the threat. The key is to create a system where multiple checks and balances are in place to prevent malicious software from gaining a foothold.
Endpoint Protection Best Practices
Effective endpoint protection is the first line of defense against ransomware. This involves a combination of tools and techniques designed to secure individual computers and devices within your network. A robust strategy includes a multi-faceted approach that combines several layers of security.
This goes beyond simply installing antivirus software. While crucial, antivirus alone isn’t sufficient. It needs to be complemented by other security measures for comprehensive protection. Regular updates are also paramount to ensure the software remains effective against the latest threats.
- Antivirus Software: Real-time scanning and signature-based detection are essential. Consider solutions offering behavioral analysis and machine learning capabilities to identify zero-day threats.
- Firewalls: Network firewalls control incoming and outgoing network traffic, blocking malicious connections and preventing unauthorized access to your systems. They act as a barrier, preventing ransomware from entering your network through external vulnerabilities.
- Intrusion Detection/Prevention Systems (IDS/IPS): These systems monitor network traffic for suspicious activity, alerting administrators to potential threats and automatically blocking malicious attempts. They can detect unusual patterns indicative of ransomware deployment.
- Regular Software Updates and Patching: Keeping operating systems, applications, and firmware up-to-date is crucial. Many ransomware attacks exploit known vulnerabilities, so patching promptly is critical in minimizing your attack surface.
Robust Data Backup and Recovery Procedures
Regular and reliable data backups are critical to mitigating the impact of a ransomware attack. Even with the best security measures, the possibility of a breach always exists. Having a solid backup strategy allows you to restore your data quickly and minimize downtime.
The 3-2-1 backup rule is a widely accepted best practice: three copies of your data, on two different media types, with one copy offsite. This redundancy ensures data protection even in the event of a major disaster or data loss.
- Frequency: Backups should be performed regularly, ideally daily or even more frequently for critical data. The frequency depends on the rate of data changes and the acceptable level of data loss.
- Media Types: Utilize a combination of storage options, such as local drives, network-attached storage (NAS), and cloud storage. This diversification reduces the risk of data loss due to a single point of failure.
- Offsite Storage: Store at least one backup copy offsite, ideally in a geographically separate location, to protect against physical disasters such as fire or theft.
- Testing: Regularly test your backup and recovery procedures to ensure they work correctly and that you can restore your data quickly and efficiently. This prevents unpleasant surprises during a real emergency.
Security Technologies: Sandboxing and Application Whitelisting
Advanced security technologies like sandboxing and application whitelisting offer additional layers of protection against ransomware. While not a replacement for fundamental security practices, they can significantly enhance your defenses.
These technologies work by restricting what can run on your systems, thus limiting the opportunities for malicious code to execute. They add another critical layer of protection, reducing the risk of infection, even if other defenses fail.
- Sandboxing: Sandboxing allows you to run potentially unsafe programs in an isolated environment. This prevents malicious code from affecting your main system. If the program is malicious, the damage is contained within the sandbox.
- Application Whitelisting: This approach only allows pre-approved applications to run on your system. Any unauthorized application is blocked, preventing unknown or malicious software from executing. This significantly reduces the attack surface.
Proactive Prevention Strategies
The most sophisticated ransomware protection technology is useless if your employees fall for a simple phishing email. Human error remains the weakest link in cybersecurity, making proactive strategies focused on human factors crucial for preventing ransomware attacks. Investing in employee training and establishing robust incident response plans are far more effective than solely relying on technical solutions.
This section focuses on bolstering your organization’s defenses through employee education and preparedness, transforming your workforce into your strongest line of defense against ransomware.
Employee Training on Phishing and Social Engineering
A comprehensive training program is essential to equip employees with the knowledge and skills to identify and avoid phishing scams and other social engineering tactics. This program should go beyond simple awareness; it needs to simulate real-world scenarios and teach practical techniques for identifying suspicious emails, links, and attachments. For example, training should cover the identification of common phishing indicators like poor grammar, unexpected requests, urgent tones, and suspicious sender addresses.
Hands-on exercises, such as simulated phishing campaigns, are particularly effective in reinforcing learning and highlighting vulnerabilities. Regular refresher training ensures that knowledge remains current and that employees remain vigilant against evolving threats.
Best Practices for Securing Remote Access and Mobile Devices
Securing remote access and mobile devices is paramount in today’s increasingly mobile workforce. Strong password policies, multi-factor authentication (MFA), and the use of virtual private networks (VPNs) for remote access are critical. Regular software updates and patching are also essential to mitigate vulnerabilities. Mobile devices should be managed through a Mobile Device Management (MDM) system, allowing for remote wiping and security policy enforcement.
Employees should be trained on the importance of only connecting to secure Wi-Fi networks and avoiding public charging stations when possible. Clear guidelines should be provided regarding acceptable use of personal devices for work purposes.
Security Awareness Training and Simulated Phishing Attacks
Regular security awareness training is not a one-time event; it’s an ongoing process. Employees need consistent reinforcement of best practices. Simulated phishing attacks provide valuable real-world experience. These controlled exercises allow you to assess employee vulnerability and identify areas for improvement in your training program. Analyzing the results of these simulated attacks can pinpoint weaknesses in employee understanding and provide targeted training to address those specific areas.
Feedback and reinforcement are key components of effective security awareness training. For instance, analyzing which employees clicked on phishing links can help tailor future training to their specific needs.
Incident Response Planning for Ransomware Attacks
A well-defined incident response plan is critical for minimizing the impact of a ransomware attack. This plan should Artikel clear steps for detection, containment, eradication, recovery, and post-incident activity. It should also specify roles and responsibilities for each team member involved in the response. Regular drills and simulations are necessary to ensure that the plan is effective and that employees are familiar with their roles and responsibilities.
The plan should include procedures for isolating infected systems, backing up critical data, and communicating with stakeholders. For example, a well-defined plan would include a communication protocol to inform relevant authorities and affected parties about the incident.
Effective Communication Strategies During a Ransomware Incident
Effective communication is crucial during a ransomware incident. A communication plan should be in place to inform employees, customers, and other stakeholders about the situation and the steps being taken to address it. This plan should Artikel who is responsible for communicating with each stakeholder group and what information should be shared. Transparency is essential; withholding information can damage trust and exacerbate the situation.
The communication should be clear, concise, and factual, avoiding technical jargon that may confuse non-technical audiences. For example, a company might issue a press release outlining the incident and the steps taken to mitigate its impact, while simultaneously providing regular updates to employees via email or internal communication channels.
Post-Incident Response and Recovery
A ransomware attack can be devastating, but a well-defined response plan can significantly mitigate the damage and expedite recovery. This section Artikels the crucial steps to take after a ransomware attack, focusing on containment, data recovery, legal considerations, and damage assessment. Remember, speed and decisiveness are key in minimizing the impact.
Incident Response Procedure
Responding to a ransomware attack requires a structured approach. A well-defined incident response plan should be developed and tested
before* an attack occurs. This plan should detail roles and responsibilities, communication protocols, and escalation procedures. The following steps provide a framework for responding to an incident
- Isolate Infected Systems: Immediately disconnect infected systems from the network to prevent further spread. This includes disconnecting from the internet, local network, and any shared storage devices.
- Contain the Breach: Identify the extent of the infection. Determine which systems and data have been compromised. Network segmentation and endpoint detection and response (EDR) solutions can help limit the impact.
- Secure the Perimeter: Strengthen network security controls, such as firewalls and intrusion detection systems, to prevent further attacks. Patch any known vulnerabilities.
- Data Recovery: Begin the process of restoring data from backups. Ensure the backups are clean and uninfected before restoring them.
- Forensic Investigation: Conduct a thorough forensic investigation to determine the source of the attack, the methods used, and the extent of the damage. This information is crucial for remediation and prevention.
- System Restoration: Once data is recovered, restore systems to a clean state, applying all necessary security patches and updates.
- Post-Incident Review: After the immediate crisis has passed, conduct a thorough review of the incident to identify weaknesses in security and improve future prevention strategies.
Containing Ransomware Spread
The rapid containment of a ransomware attack is critical to minimizing its impact. Effective containment strategies involve several key actions. Failing to contain the spread can lead to significantly higher recovery costs and prolonged downtime.
Effective containment requires a multi-pronged approach, encompassing network segmentation, endpoint security measures, and swift isolation of affected systems. For example, a company using network segmentation might find that the ransomware is limited to a specific segment, allowing for quicker recovery of unaffected areas. This is in contrast to a company without such segmentation, where the ransomware could potentially spread throughout the entire network.
Data Recovery from Backups
Regular and reliable backups are the cornerstone of ransomware recovery. The process involves verifying backup integrity, selecting the appropriate recovery point, and restoring data to clean systems. It’s crucial to test backups regularly to ensure they are functional and restorable. A successful recovery relies heavily on having multiple, well-tested backups stored offline or in a secure, geographically separate location.
Consider the following when recovering data: Verify the integrity of your backups before restoring them. Ensure the recovery environment is clean and free of malware. Restore data to a clean, patched system, not the originally infected one. Document the recovery process meticulously for future reference.
Legal and Regulatory Considerations, Ransomware hype and prevention strategies 3
Ransomware attacks trigger various legal and regulatory obligations. Depending on the nature of the data compromised (e.g., personally identifiable information, protected health information), organizations may be required to notify affected individuals and regulatory bodies. Failure to comply with these regulations can result in significant fines and legal repercussions. For example, the GDPR in Europe mandates specific notification procedures in case of data breaches.
Similarly, HIPAA in the US has strict regulations for protecting health information.
Damage Assessment and Remediation
Assessing the damage caused by a ransomware attack is a crucial step in developing a comprehensive remediation plan. This involves identifying the compromised systems, the extent of data loss or corruption, the financial impact (including ransom demands, recovery costs, and potential business disruption), and the reputational damage. The remediation plan should address all aspects of the damage, including data recovery, system restoration, security enhancements, and legal compliance.
For example, a company might assess the damage by quantifying the lost revenue due to downtime, the cost of restoring data, and the potential legal fees associated with notifying affected individuals.
Emerging Trends and Future Threats
The ransomware landscape is constantly evolving, driven by technological advancements and the ingenuity of cybercriminals. Understanding emerging trends is crucial for effective prevention and mitigation. The convergence of AI, cloud computing, and the Internet of Things (IoT) presents both new opportunities for attackers and increased challenges for defenders.The increasing sophistication of ransomware attacks necessitates a proactive and adaptive approach to security.
This section will explore several key emerging trends and their potential impact on individuals, businesses, and society as a whole.
Artificial Intelligence and Machine Learning in Ransomware Attacks
AI and machine learning are rapidly transforming the cyber threat landscape. Attackers are leveraging these technologies to automate various stages of ransomware attacks, from identifying vulnerable systems to encrypting data and exfiltrating it. AI-powered tools can analyze vast amounts of data to identify weaknesses in security systems, personalize phishing attacks, and create more effective encryption algorithms. For example, AI can be used to generate highly convincing phishing emails, increasing the likelihood of successful attacks.
Conversely, machine learning models can be trained to detect anomalies in network traffic and file behavior, providing early warnings of potential ransomware infections. The arms race between attackers using AI for offensive purposes and defenders using AI for defensive purposes will likely intensify in the coming years.
Ransomware-as-a-Service (RaaS) and its Implications
The rise of Ransomware-as-a-Service (RaaS) has significantly lowered the barrier to entry for cybercriminals. RaaS platforms provide aspiring attackers with readily available tools, infrastructure, and expertise, allowing them to launch ransomware attacks with minimal technical skills. This democratization of ransomware attacks leads to a higher volume and frequency of incidents, making it more difficult for organizations to manage and respond to threats.
The ease of access to RaaS also increases the likelihood of less sophisticated actors launching attacks, broadening the range of potential targets. The increasing complexity of RaaS offerings, including features such as data exfiltration and double extortion, poses a significant challenge to security professionals.
Ransomware in the Age of Cloud Computing and IoT
The proliferation of cloud computing and IoT devices expands the attack surface for ransomware. Cloud environments, while offering numerous benefits, can also become targets for ransomware attacks, potentially leading to data loss and service disruptions. IoT devices, often lacking robust security measures, can be easily compromised and used as entry points for ransomware attacks. The interconnected nature of cloud and IoT systems means that a successful attack on one device can quickly spread to other connected systems, resulting in widespread damage.
For example, a ransomware attack targeting a poorly secured IoT device in a manufacturing facility could cripple the entire production line. The challenge lies in securing these diverse and often heterogeneous environments.
Future Evolution of Ransomware and its Societal Impact
The future of ransomware is likely to involve increasingly sophisticated attacks, leveraging AI, automation, and the vulnerabilities of cloud and IoT environments. We can anticipate a rise in targeted attacks against critical infrastructure, potentially causing significant societal disruption. The potential for widespread data breaches and the resulting financial and reputational damage will continue to be a major concern.
Furthermore, the increasing use of double extortion tactics, where attackers both encrypt data and threaten to leak sensitive information, will likely escalate the pressure on victims to pay ransoms. The long-term impact could include increased cybersecurity costs for businesses and governments, erosion of public trust in digital systems, and potentially even disruptions to essential services. The development and implementation of robust cybersecurity measures will be paramount in mitigating these risks.
Concluding Remarks
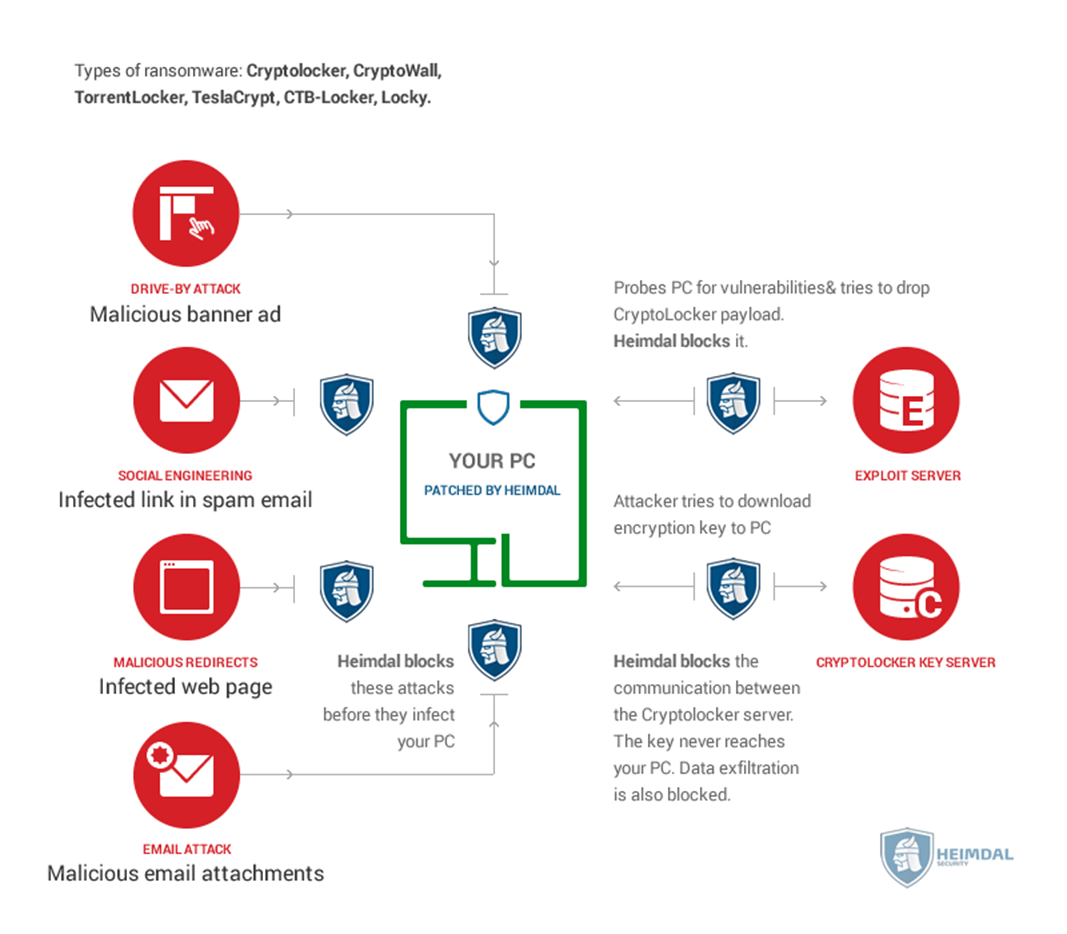
The threat of ransomware is real, but understanding the landscape and implementing proactive strategies can significantly reduce your vulnerability. While the hype surrounding ransomware can be overwhelming, focusing on a multi-layered approach to security – encompassing technical safeguards, robust employee training, and a well-defined incident response plan – is key. Remember, it’s not about eliminating risk entirely, but about mitigating it effectively.
By staying informed, proactive, and adaptable, you can navigate this challenging environment and protect your valuable data and digital assets.
Questions Often Asked
What’s the difference between ransomware and malware?
Ransomware is a
-type* of malware. Malware is a broad term for any malicious software, while ransomware specifically encrypts your data and demands a ransom for its release.
Can I recover my data without paying the ransom?
Sometimes, yes! If you have good backups, you can restore your data without paying. However, paying the ransom doesn’t guarantee data recovery and often funds further criminal activity.
How often should I update my security software?
Security software updates should be installed as soon as they’re available. These updates often include critical patches that protect against the latest threats.
What should I do if I suspect a ransomware attack?
Immediately disconnect from the network to prevent further spread. Do not pay the ransom. Contact your IT team or cybersecurity professionals and start your incident response plan.





