
Ransomware Spreading Hackers Threaten Employees
Ransomware spreading hackers threatening to harass employees and business partners is a chilling reality in today’s digital landscape. It’s not just about encrypted files anymore; it’s about the calculated psychological warfare waged against individuals and organizations, leveraging stolen data and the fear of public exposure to extort payments. This isn’t a theoretical threat; it’s a sophisticated operation impacting businesses of all sizes, leaving a trail of financial losses and reputational damage in its wake.
Let’s dive into the disturbing tactics used and explore how we can better protect ourselves.
The methods employed by these cybercriminals are constantly evolving, ranging from cleverly crafted phishing emails to exploiting software vulnerabilities. They meticulously target individuals within an organization, using their access to sensitive information to escalate their extortion attempts. Understanding the different attack vectors, the psychological manipulation techniques, and the legal implications is crucial in building a robust defense against this increasingly prevalent threat.
This isn’t just a tech problem; it’s a human problem requiring a multi-faceted approach.
Ransomware Attack Vectors
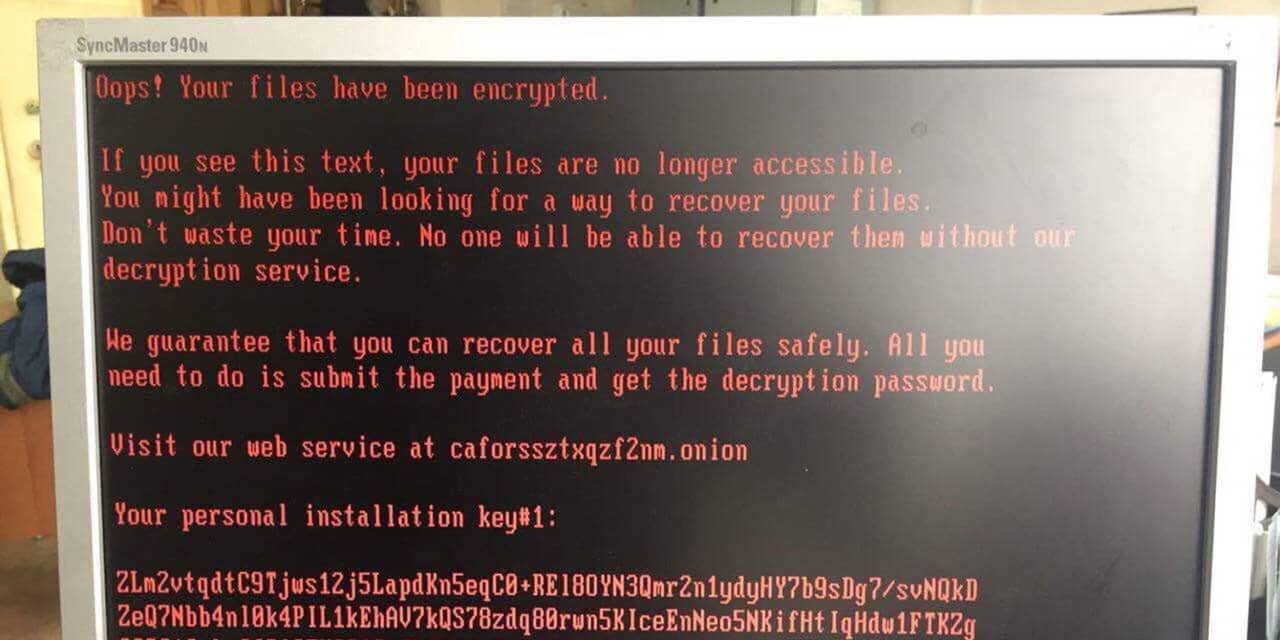
Ransomware attacks, unfortunately, are becoming increasingly sophisticated and prevalent. Understanding the various methods used to spread this malicious software is crucial for effective prevention and mitigation. This exploration delves into the common attack vectors, highlighting their strengths and weaknesses to provide a clearer picture of how these cyber threats infiltrate systems.
The initial infection point is often the weakest link in a company’s security chain. Hackers exploit vulnerabilities in software, operating systems, and human behavior to gain entry. They leverage a variety of techniques to bypass security measures, often focusing on social engineering and exploiting known vulnerabilities before patching becomes available.
Phishing Emails
Phishing emails remain a highly effective ransomware delivery mechanism. These emails often appear legitimate, mimicking communications from trusted sources like banks, shipping companies, or even colleagues. They may contain malicious attachments (e.g., .doc, .pdf, .exe files) or links to websites hosting malware. Once clicked, the malware can install ransomware, encrypting sensitive data and demanding a ransom for its release.
A successful phishing campaign can compromise numerous systems simultaneously, leading to widespread data loss and operational disruption.
Malicious Software Downloads
Many users inadvertently download malicious software disguised as legitimate programs. This often occurs through untrusted websites, file-sharing platforms, or compromised software repositories. Hackers may also employ drive-by downloads, where malware is automatically installed when a user visits a compromised website. These downloads often bypass traditional antivirus software, especially if the malware is newly developed or uses sophisticated evasion techniques.
Exploit Kits
Exploit kits are collections of automated tools that scan for vulnerabilities in web browsers and other software. Once a vulnerability is identified, the exploit kit automatically exploits it to install malware, including ransomware. These kits are constantly updated to target newly discovered vulnerabilities, making them a particularly dangerous threat. The automated nature of exploit kits allows for rapid and widespread attacks, impacting a large number of users simultaneously.
Hypothetical Ransomware Attack Scenario
Imagine a company that uses outdated software, relies heavily on email communication, and lacks comprehensive employee security training. A sophisticated attacker could launch a multi-pronged attack: First, they send a phishing email containing a malicious link to a website hosting an exploit kit. Employees who click the link unknowingly download and install ransomware. Simultaneously, the attacker launches a separate campaign using malicious software downloads embedded within seemingly harmless files shared on a frequently used file-sharing platform.
This combination of attack vectors significantly increases the chances of a successful ransomware deployment and the scale of the resulting damage.
Comparison of Ransomware Delivery Mechanisms
| Delivery Mechanism | Strengths | Weaknesses | Mitigation |
|---|---|---|---|
| Phishing Emails | High success rate, low cost, easily scalable | Relies on user interaction, easily detected with strong security awareness training | Security awareness training, email filtering, multi-factor authentication |
| Malicious Software Downloads | Can bypass some security measures, effective against less security-conscious users | Requires user interaction, detection rates are improving with advanced antivirus software | Up-to-date antivirus software, careful download practices, restricted access to untrusted websites |
| Exploit Kits | Automated, rapid deployment, targets known vulnerabilities | Relies on unpatched vulnerabilities, can be detected and blocked by intrusion detection systems | Regular software patching, web application firewalls, intrusion detection systems |
Employee and Business Partner Harassment Tactics
Ransomware attacks aren’t just about encrypting data; they’re often accompanied by a chilling campaign of harassment targeting employees and business partners. Attackers leverage this tactic to maximize pressure and increase the likelihood of a ransom payment. This harassment extends beyond simple threats and often involves sophisticated psychological manipulation.The methods used are designed to cause significant distress and disruption, aiming to force victims into paying the ransom before the situation escalates further.
Understanding these tactics is crucial for both preventing them and mitigating their impact if an attack occurs.
Examples of Harassment Tactics
Attackers employ a range of harassment tactics, from relatively simple to extremely sophisticated. These tactics aim to create fear, uncertainty, and doubt, ultimately driving the victim towards paying the ransom. Common examples include the dissemination of stolen data, targeted phishing campaigns against employees and partners, and the threat of public exposure of sensitive information. They may also use doxxing, revealing personal information of employees online, or even threaten physical harm.
The severity and scale of these tactics vary depending on the attackers’ goals and the perceived vulnerability of the target.
Pressure Tactics to Secure Ransom Payment
The pressure tactics used are designed to create a sense of urgency and fear. Attackers might set deadlines for payment, threatening to release sensitive data or escalate harassment if the ransom isn’t paid promptly. They may also employ a drip-feed approach, releasing small amounts of data initially to demonstrate their capabilities and further incentivize payment. The constant threat of further data leaks and the potential for reputational damage create immense pressure on victims.
Furthermore, attackers might directly contact employees and business partners, using stolen information to personalize their threats and make them seem more credible.
Psychological Impact of Harassment
The psychological impact of these harassment methods can be devastating. Employees and business partners may experience anxiety, stress, fear, and even depression. The constant threat of data exposure and reputational damage can lead to sleeplessness, decreased productivity, and even health problems. Organizations may face decreased morale, loss of trust, and damage to their reputation. The psychological toll on individuals and the organization as a whole can be significant, even after the immediate threat has passed.
In some cases, victims may experience long-term psychological trauma.
Legal Ramifications of Harassment
The harassment tactics employed by ransomware attackers are illegal in most jurisdictions. These actions constitute various crimes, including extortion, cyberstalking, and potentially even threats of violence. Victims have legal recourse to pursue criminal and civil actions against the attackers. Law enforcement agencies can investigate these crimes, and victims can seek compensation for damages suffered. However, identifying and prosecuting the perpetrators can be challenging due to the often anonymous nature of ransomware attacks.
Preventative Measures to Mitigate Harassment Impact
Preparing for the possibility of harassment is vital. A robust cybersecurity strategy is the first line of defense, but it’s also essential to have a plan in place to deal with the psychological and legal consequences of a ransomware attack. This includes: developing a comprehensive incident response plan that addresses communication strategies, legal counsel engagement, and employee support; conducting regular security awareness training for employees and business partners to help them recognize and avoid phishing attempts and other social engineering tactics; implementing strong data protection measures, including encryption and regular backups; establishing clear communication protocols for responding to a ransomware attack; and ensuring access to mental health resources for affected employees and partners.
The news is full of stories about ransomware attacks, with hackers not only encrypting data but also threatening to harass employees and business partners if the ransom isn’t paid. This highlights the urgent need for robust security solutions, and thinking about how we build applications impacts this directly. Learning more about secure application development, like exploring the possibilities of domino app dev the low code and pro code future , could help businesses better protect themselves against these increasingly sophisticated attacks.
Ultimately, stronger, more secure applications are crucial in mitigating the risk of ransomware and the associated harassment campaigns.
Proactive measures like these significantly reduce the impact of harassment and strengthen an organization’s resilience.
Data Exfiltration and Extortion Methods: Ransomware Spreading Hackers Threatening To Harass Employees And Business Partners
Ransomware attacks are rarely limited to simple file encryption. Increasingly, threat actors exfiltrate sensitive data before or after deploying ransomware, significantly escalating the pressure on victims and expanding the potential for financial damage. This stolen data becomes a powerful weapon in the extortionist’s arsenal, used to leverage further payments or inflict reputational harm.Data exfiltration techniques vary widely depending on the ransomware family and the attacker’s sophistication.
The goal is always the same: to steal valuable data undetected and then use it for leverage. The methods used, however, range from simple file transfers to highly sophisticated techniques designed to evade detection. The types of data targeted are equally diverse, reflecting the varied needs and priorities of different threat actors.
Data Exfiltration Techniques
Several techniques are employed to steal data before or after ransomware deployment. These include using readily available tools and scripts to copy files, employing custom-built malware for stealthy data exfiltration, and leveraging compromised credentials to access cloud storage or network shares. The choice of method often depends on the attacker’s resources and the security posture of the target.
For example, a less sophisticated attacker might simply copy files to a removable drive, while a more advanced actor might use a command-and-control server to exfiltrate data in encrypted packets over a covert channel. Some ransomware families even incorporate data exfiltration directly into their encryption process, making it seamless and difficult to detect.
Targeted Data Types
The type of data targeted reflects the value it holds for the attackers. High-value targets often include personally identifiable information (PII), financial records, intellectual property (IP), customer databases, and trade secrets. PII can be sold on dark web marketplaces, financial records can be used for identity theft or fraud, and IP can provide a significant competitive advantage to the attackers or their clients.
The attackers carefully select their targets based on the potential for financial gain or other forms of leverage. For instance, a healthcare provider might be targeted for patient records, while a financial institution might be targeted for customer account details and transaction history.
Extortion Leveraging Stolen Data
Stolen data is used in several ways to pressure victims into paying ransoms. Threat actors may threaten to publicly release the data, sell it on the dark web, or use it for blackmail or other forms of extortion. The threat of reputational damage from a data breach can be incredibly damaging, particularly for companies that handle sensitive customer information.
The pressure exerted by the threat of data release is often far greater than the threat of simple data encryption alone, driving victims to pay ransoms to avoid severe financial and reputational consequences. For example, a threat actor might demand a ransom in exchange for not releasing a company’s customer database containing sensitive personal and financial information.
Data Exfiltration Methods Across Ransomware Families
Different ransomware families employ varying methods of data exfiltration. Some families, like Ryuk, are known for their focus on data exfiltration before encryption, aiming to maximize their leverage. Others, like Conti, have demonstrated a capacity for both data encryption and exfiltration, using a double extortion approach. The sophistication of the techniques employed can vary significantly, ranging from simple file transfers to the use of sophisticated tools designed to bypass security measures and evade detection.
The choice of method often depends on the resources and capabilities of the specific threat actor.
Impact on Business Operations
Data encryption and exfiltration can severely disrupt business operations. Encrypted data renders critical systems and applications unusable, halting production and causing significant financial losses. The exfiltration of sensitive data can lead to legal and regulatory penalties, reputational damage, and loss of customer trust. The combined impact of these factors can be devastating for businesses of all sizes, often leading to significant financial losses and long-term operational disruption.
The recovery process can be lengthy and costly, requiring significant investments in IT resources and expertise. The disruption caused by ransomware attacks extends far beyond the immediate impact of data encryption; the threat of data exfiltration adds another layer of complexity and risk.
Impact on Business Operations and Reputation

A ransomware attack that includes the harassment of employees and business partners goes far beyond simple data encryption. The cascading effects on business operations, financial stability, and brand reputation can be devastating, potentially leading to long-term damage and even insolvency. The added layer of personal attacks significantly amplifies the crisis, creating a complex and challenging situation for affected organizations.The financial consequences are multifaceted.
Direct costs include the ransom payment itself (if paid), the cost of incident response services (forensic analysis, legal counsel, public relations), system recovery, data restoration, and potential fines and legal penalties for data breaches. Indirect costs, often more significant, stem from operational downtime, lost productivity, damaged client relationships, and the erosion of investor confidence. The harassment component further increases these costs through lost employee time dealing with the attacks, potential legal battles stemming from the harassment, and the need for additional security measures to protect employees.
Financial and Operational Consequences
The financial fallout from a ransomware attack combined with employee and partner harassment can be crippling. Consider the case of a mid-sized manufacturing company where a ransomware attack crippled production for two weeks, costing them hundreds of thousands of dollars in lost revenue and requiring significant overtime pay to catch up. Simultaneously, the harassment campaign against employees resulted in several key personnel taking extended leave, further hindering operations and incurring additional costs.
This scenario highlights how the combined impact can exponentially amplify financial losses. Operational disruptions extend beyond immediate production halts. Supply chains can be disrupted, impacting both production and sales. Customer service may be severely impacted, leading to lost sales and damaged customer relationships. Internal processes, such as accounting and HR, can be severely hampered, causing further delays and financial strain.
Reputational Damage and Brand Erosion
The reputational damage caused by such an attack can be long-lasting. News of a ransomware attack, especially one involving the harassment of employees and partners, is likely to be widely publicized, damaging the company’s image and potentially leading to a loss of customer trust. This negative publicity can affect investor confidence, making it harder to secure funding or attract new talent.
Customers may switch to competitors, fearing their own data might be compromised or that they might become targets of harassment. The negative publicity can also lead to a decrease in stock value, impacting shareholder investments. For example, a well-known retailer experiencing a similar incident might see a significant drop in its stock price and a decrease in customer traffic immediately following the news, potentially leading to long-term financial difficulties.
Long-Term Effects on Customer Trust and Relationships
Rebuilding customer trust after a ransomware attack, particularly one involving harassment, requires a significant investment of time and resources. Customers need reassurance that their data is safe and that the company is taking steps to prevent future attacks. Transparency and open communication are critical in this process. Failure to address the situation effectively can lead to long-term damage to customer relationships, impacting future revenue streams and growth opportunities.
A lack of proactive communication and swift response could lead to customers feeling abandoned and betrayed, making it much harder to regain their trust and loyalty.
Best Practices for Crisis Communication
Effective crisis communication is paramount during and after a ransomware attack. A well-defined communication plan should be in place before an incident occurs. This plan should Artikel key messages, communication channels, and designated spokespeople. Transparency is crucial; companies should communicate openly and honestly with customers, employees, and stakeholders, providing regular updates on the situation and the steps being taken to address it.
Acknowledging the incident promptly, demonstrating empathy for affected individuals, and outlining a clear recovery plan can help mitigate the negative impact.
Steps to Recover from a Ransomware Attack, Ransomware spreading hackers threatening to harass employees and business partners
Effective recovery requires a systematic approach.
- Secure the affected systems: Immediately isolate infected systems to prevent further spread of the ransomware.
- Conduct a thorough forensic investigation: Determine the extent of the breach and identify the source of the attack.
- Restore data from backups: Ensure that backups are clean and not affected by the ransomware.
- Enhance security measures: Implement stronger security protocols to prevent future attacks.
- Notify relevant authorities: Report the incident to law enforcement and regulatory bodies.
- Communicate with stakeholders: Keep customers, employees, and partners informed about the situation.
- Review and update incident response plan: Learn from the experience and improve the plan for future incidents.
Prevention and Mitigation Strategies
Ransomware attacks are a serious threat to businesses of all sizes. The combination of data encryption and the threat of employee and partner harassment significantly amplifies the pressure on victims. Effective prevention and mitigation strategies are crucial for minimizing the risk and impact of such attacks. A multi-layered approach, combining technical safeguards, employee training, and robust incident response planning, is the most effective defense.
A comprehensive security plan needs to be proactive, addressing vulnerabilities before they can be exploited. This requires a combination of technical controls and security awareness training, backed by solid incident response procedures.
Comprehensive Security Plan Design
A robust security plan should encompass several key areas. Network security is paramount, requiring firewalls, intrusion detection/prevention systems (IDS/IPS), and regular security audits to identify and patch vulnerabilities. Endpoint security, including antivirus software and endpoint detection and response (EDR) solutions, protects individual computers and devices. Access control measures, such as multi-factor authentication (MFA) and strong password policies, limit unauthorized access to sensitive data.
Regular software updates and patching are critical to address known vulnerabilities exploited by ransomware. Finally, a strict policy on acceptable use of company devices and networks helps prevent accidental infections. For example, a company might implement a strict policy prohibiting the use of personal USB drives or downloading files from untrusted sources.
Security Measures Checklist for Data Exfiltration and Harassment Prevention
Preventing data exfiltration and employee/partner harassment requires a proactive approach. This checklist Artikels crucial security measures:
The following measures are essential to protect against data exfiltration and harassment related to ransomware attacks. A layered approach, combining technical controls and procedural safeguards, provides the strongest protection.
- Implement strong password policies and enforce multi-factor authentication (MFA) for all accounts.
- Regularly back up all critical data to an offline location, ensuring the backups are tested and easily restorable.
- Restrict access to sensitive data based on the principle of least privilege.
- Employ robust email security solutions to filter out phishing emails and malicious attachments.
- Monitor network traffic for suspicious activity using intrusion detection systems (IDS).
- Conduct regular security awareness training for employees, covering phishing, social engineering, and safe internet practices.
- Establish clear incident response procedures, including communication protocols and escalation paths.
- Develop a data loss prevention (DLP) strategy to monitor and prevent sensitive data from leaving the network.
Employee Training and Awareness Programs
Regular and comprehensive employee training is not just a best practice; it’s a necessity. Employees are often the weakest link in the security chain. Training should focus on practical skills to identify and avoid phishing scams, recognizing malicious links and attachments, and understanding the importance of strong passwords and MFA. Simulated phishing exercises can effectively test and improve employee awareness.
For example, a company might send out a simulated phishing email to assess employee response rates and identify vulnerabilities in their security awareness. Regular refresher courses keep employees updated on the latest threats and best practices.
Robust Data Backup and Recovery Procedures
Data backup and recovery are crucial components of any ransomware mitigation strategy. The 3-2-1 backup rule (3 copies of data, on 2 different media types, with 1 copy offsite) is a widely accepted best practice. Regular testing of the backup and recovery process ensures data can be restored quickly and efficiently in the event of an attack. This includes verifying the integrity and recoverability of the backups.
For example, a company might perform a full restore test every quarter to ensure that their backup system is functioning correctly. This minimizes downtime and data loss during a ransomware incident.
Incident Response Plans for Ransomware Attacks
A well-defined incident response plan is crucial for minimizing the impact of a ransomware attack. The plan should Artikel clear steps to be taken in case of an attack, including immediate actions (such as isolating affected systems), communication protocols (informing relevant stakeholders), and data recovery procedures. The plan should also include steps for engaging with law enforcement and cybersecurity experts, if necessary.
For instance, a company’s incident response plan might specify the contact information for their incident response team, legal counsel, and cybersecurity consultants. Regularly testing and updating the plan is essential to ensure its effectiveness.
Legal and Regulatory Considerations

Ransomware attacks present significant legal and regulatory challenges for organizations. Navigating the complex web of laws and regulations surrounding data breaches and extortion requires a proactive and informed approach. Failure to comply can result in substantial financial penalties, reputational damage, and even criminal prosecution.
Relevant Legal Frameworks and Regulations
Numerous legal frameworks and regulations govern the handling of ransomware attacks and data breaches. These vary significantly depending on the location of the affected organization and the type of data involved. Key legislation includes the General Data Protection Regulation (GDPR) in Europe, the California Consumer Privacy Act (CCPA) in California, and the Health Insurance Portability and Accountability Act (HIPAA) in the United States for protected health information.
Beyond specific data privacy laws, organizations must also consider broader cybersecurity regulations and criminal laws relating to extortion and theft. These laws often mandate specific security measures and impose strict reporting requirements following a data breach. The specifics of these requirements depend on the jurisdiction and the nature of the attack.
Organizational Responsibilities in Incident Reporting
Organizations have a legal responsibility to report ransomware attacks and data breaches to relevant authorities. The specifics of reporting obligations vary by jurisdiction and often depend on the volume of data compromised and the sensitivity of the information. Failure to report a breach as required can result in significant penalties. For example, under GDPR, organizations must report breaches to supervisory authorities within 72 hours of becoming aware of them.
In the US, while there’s no single federal mandate for all data breaches, various state laws require notification to affected individuals and potentially to state attorneys general. The process usually involves a thorough investigation to determine the extent of the breach, the affected individuals, and the steps taken to mitigate the damage. Accurate and timely reporting is crucial to limit further harm and demonstrate compliance with the law.
Potential Legal Liabilities for Inadequate Security Measures
Organizations face significant legal liabilities if they fail to implement adequate security measures to protect against ransomware attacks. This negligence can lead to lawsuits from affected individuals, regulatory fines, and even criminal charges. Courts may consider factors such as the industry standard of care, the organization’s size and resources, and the steps taken to prevent the attack when determining liability.
Demonstrating a commitment to robust cybersecurity practices through risk assessments, security awareness training, and incident response planning can help mitigate legal risks. A lack of proactive measures, however, can significantly increase the likelihood of facing legal consequences. For instance, a company failing to patch known vulnerabilities, leaving systems exposed to known ransomware exploits, might be found negligent.
Best Practices for Complying with Data Privacy Regulations
Complying with data privacy regulations requires a multi-faceted approach. This includes implementing robust security measures, conducting regular risk assessments, developing and testing incident response plans, providing employee training on data security, and establishing clear data governance policies. Data minimization, purpose limitation, and data encryption are vital for minimizing the impact of a potential breach. Regular audits and independent security assessments can help ensure compliance and identify vulnerabilities.
Furthermore, organizations should maintain detailed records of their security practices and incident response activities to demonstrate compliance and facilitate investigations. A proactive approach to data privacy, including implementing a comprehensive data protection program, is critical for mitigating legal risks and protecting organizational reputation.
Comparison of Legal Jurisdictions and Regulations
| Jurisdiction | Key Legislation | Reporting Requirements | Penalties for Non-Compliance |
|---|---|---|---|
| European Union | GDPR | 72-hour breach notification to supervisory authority | Up to €20 million or 4% of annual global turnover |
| United States | Various state laws (e.g., CCPA, HIPAA) | Varies by state and type of data; often includes notification to affected individuals | Varies by state; can include fines, legal action, and reputational damage |
| United Kingdom | UK GDPR | Similar to EU GDPR, 72-hour breach notification | Similar to EU GDPR, significant fines |
| Canada | PIPEDA | Notification to individuals and potentially the Office of the Privacy Commissioner | Fines and other penalties |
Summary
The threat of ransomware spreading hackers targeting employees and business partners isn’t going away anytime soon. The sophistication of these attacks, coupled with the devastating consequences they can inflict, underscores the urgent need for proactive security measures. From comprehensive security training for employees to robust data backup and recovery plans, a layered approach is essential. Remember, it’s not just about protecting data; it’s about protecting people and the overall health of your organization.
Staying informed, adapting to evolving threats, and prioritizing cybersecurity is no longer a luxury—it’s a necessity for survival in the digital age.
Essential Questionnaire
What should I do if I receive a ransomware demand?
Do NOT pay the ransom. Contact law enforcement and a cybersecurity professional immediately. Paying encourages further attacks and doesn’t guarantee data recovery.
How can I protect my business from ransomware?
Implement multi-factor authentication, regularly update software, conduct employee security training, and maintain robust backups of your data. Consider investing in threat detection and response tools.
What legal repercussions can a company face for a ransomware attack?
Companies can face hefty fines for failing to comply with data privacy regulations (like GDPR or CCPA) if a breach occurs due to inadequate security measures. They may also face lawsuits from affected customers or partners.
What is data exfiltration, and why is it dangerous?
Data exfiltration is the unauthorized copying of data from a computer system. Hackers use this stolen data for extortion, blackmail, or to sell on the dark web, causing significant financial and reputational harm.





