Intel & Check Point Ransomware Defense Partnership
Intel and Check Point software extend partnership for ransomware protection, forging a powerful alliance to combat the escalating threat of ransomware. This collaboration combines Intel’s cutting-edge hardware expertise with Check Point’s robust software solutions, creating a comprehensive defense system. The partnership leverages the strengths of both companies, offering a multi-layered approach to secure systems against various ransomware attack vectors.
This promises significant implications for the future of cybersecurity, potentially setting a new standard for protecting against this ever-evolving menace.
The partnership aims to create a unified platform that integrates seamlessly, offering a proactive defense against ransomware attacks. By combining Intel’s hardware-level security enhancements with Check Point’s advanced threat intelligence and software, they are targeting vulnerabilities across the entire attack chain. This collaborative effort promises to be a major step forward in the fight against ransomware.
Partnership Overview

Intel and Check Point’s expanded collaboration marks a significant step in bolstering cybersecurity defenses against the ever-evolving threat landscape. This strategic alliance brings together the strengths of two industry giants, combining Intel’s hardware expertise with Check Point’s software prowess to create a more robust and effective response to ransomware attacks. This synergy promises to provide a comprehensive solution that protects both individual users and critical infrastructure.This partnership goes beyond a simple business arrangement; it signifies a shared commitment to safeguarding digital assets.
By integrating their respective technologies, Intel and Check Point aim to create a more secure digital environment for everyone.
Areas of Collaboration
The collaboration between Intel and Check Point focuses specifically on integrating Check Point’s security software with Intel’s hardware. This integration aims to enhance real-time threat detection and response capabilities. This focused approach tackles the challenge of ransomware by combining advanced threat intelligence with efficient processing capabilities. The specific areas of collaboration include threat intelligence sharing, joint development of security solutions, and the integration of hardware and software for improved performance and detection.
Ransomware Protection
The partnership’s primary focus is strengthening defenses against ransomware attacks. This involves leveraging Intel’s hardware capabilities, such as advanced processing units, to accelerate threat detection and response times. Check Point’s software, with its sophisticated security algorithms and threat intelligence, is integral to identifying and mitigating ransomware threats in real-time.
Mutual Benefits
This collaboration delivers significant advantages for both companies. For Intel, the partnership enhances its reputation as a leader in cybersecurity solutions, providing a crucial market edge in the growing cybersecurity industry. For Check Point, it broadens access to a wider range of hardware platforms, ensuring their software can perform optimally across a larger user base and enhance their software’s performance.
Historical Context
The two companies have a history of collaboration in various technological sectors. Their previous collaborations have demonstrated a commitment to innovation and mutual benefit. This new focus on ransomware protection builds upon that foundation, recognizing the critical need for enhanced security measures.
Intel and Check Point’s expanded partnership for ransomware protection is a smart move, but the real vulnerability might lie within the code itself. To truly bolster security, developers need to equip themselves with “AI Code Safety Goggles” – tools that help identify potential security flaws in software before they’re deployed, like those discussed in Deploying AI Code Safety Goggles Needed.
This proactive approach to code security is crucial, even with partnerships like the one between Intel and Check Point, ensuring the long-term protection of systems from the insidious threat of ransomware.
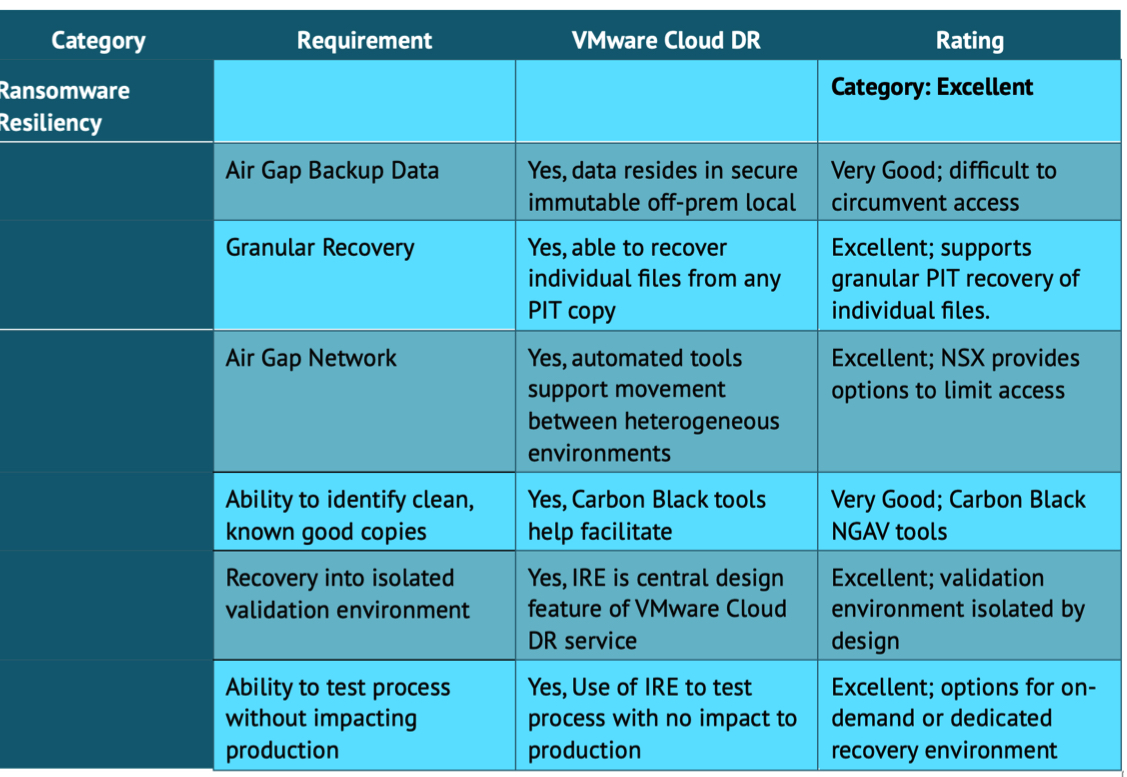
Comparative Strengths
| Feature | Intel | Check Point |
|---|---|---|
| Hardware Expertise | Exceptional expertise in processor design, memory management, and network interface cards, enabling high-performance processing. | Strong expertise in software-defined security, including network security and threat intelligence gathering. |
| Software Capabilities | Intel provides the foundation for hardware, allowing software to perform faster and more efficiently. Focus is on high-performance computing, enabling quick detection and response to threats. | Deep understanding of cyber threats and advanced algorithms for detecting and blocking malicious activity. Expertise in identifying and classifying malicious software (malware). |
| Security Focus | Focus on hardware security, performance, and scalability. | Focus on software security, threat intelligence, and incident response. |
Technical Aspects of Ransomware Protection: Intel And Check Point Software Extend Partnership For Ransomware Protection
Intel and Check Point’s partnership offers a robust defense against the ever-evolving ransomware threat landscape. This collaboration leverages the strengths of both companies, combining Intel’s hardware expertise with Check Point’s deep software security knowledge. This synergistic approach allows for a layered security strategy, significantly increasing protection against sophisticated attacks.The partnership focuses on a multifaceted approach to ransomware protection, employing a combination of proactive prevention measures and reactive response mechanisms.
This approach incorporates security features at the hardware and software levels, providing a comprehensive defense. Intel’s hardware-level security features work in conjunction with Check Point’s software solutions, creating a robust security architecture.
Intel’s Hardware-Level Security
Intel’s processors are equipped with a range of hardware-level security features designed to thwart malicious code execution. These features include memory encryption, hardware-based isolation of critical system components, and enhanced security management capabilities. These hardware-level protections are a crucial first line of defense, making it harder for attackers to gain a foothold in the system.
Check Point’s Software-Based Security
Check Point’s software solutions leverage advanced threat intelligence and machine learning to identify and mitigate ransomware threats. These solutions use deep packet inspection, behavioral analysis, and sandboxing to detect malicious code and prevent its execution. This approach complements the hardware-level security, providing a layered protection against various ransomware attack vectors.
Interoperability of Solutions
The seamless interoperability between Intel’s hardware and Check Point’s software is critical. Intel’s hardware-based security measures can restrict access to sensitive areas of the system, preventing malicious code from escalating privileges. Check Point’s software then analyzes the traffic and behavior within the restricted environment, further identifying and blocking potential ransomware threats. This integration allows for a proactive, multi-layered defense mechanism.
Security Features in the Solutions
The integrated security solutions offer a suite of security features, including:
- Advanced Threat Prevention: Utilizing threat intelligence feeds, these solutions can identify and block known and unknown ransomware strains before they can compromise systems.
- Behavioral Analysis: This feature examines the actions of processes in real-time to detect unusual behavior indicative of ransomware activity. This is crucial in identifying zero-day attacks.
- Sandboxing: Suspect files are executed in isolated environments, allowing security solutions to observe their behavior without risking the integrity of the main system. This is particularly useful in identifying polymorphic ransomware.
- Intrusion Prevention Systems (IPS): These systems proactively identify and block malicious network traffic, effectively preventing ransomware from entering the system.
Ransomware Protection Against Various Attack Vectors
The combined solution effectively addresses various ransomware attack vectors. This is achieved by leveraging the complementary strengths of Intel’s hardware-level protection and Check Point’s software-based threat detection.
| Ransomware Attack Vector | Intel & Check Point Defense |
|---|---|
| Phishing Emails | Check Point’s email security solutions block malicious attachments and suspicious links. |
| Exploit Kits | Intel’s hardware-based security measures and Check Point’s intrusion prevention system can detect and block malicious code attempting to exploit vulnerabilities. |
| Malicious Downloads | Check Point’s endpoint security solutions can detect and block malicious downloads, preventing ransomware from installing on the system. |
| Vulnerable Software | Intel’s hardware security features and Check Point’s software updates can mitigate the risk of exploits by preventing malicious code from accessing critical system components. |
Market Impact and Trends
The global ransomware landscape is constantly evolving, demanding innovative solutions to combat this escalating threat. This partnership between Intel and Check Point, focused on bolstering ransomware protection, is a significant development in the cybersecurity arena. Its implications extend beyond the immediate benefits, shaping the future of enterprise security.The ransomware market continues its growth trajectory, driven by the increasing sophistication of attacks and the persistent vulnerabilities in digital infrastructure.
This relentless threat demands a proactive and collaborative approach, which is exactly what this partnership aims to provide.
Overall Market Trends in Ransomware Protection
The ransomware landscape is characterized by a relentless increase in attack frequency and sophistication. Cybercriminals are constantly innovating their tactics, exploiting new vulnerabilities and employing more sophisticated encryption techniques. This dynamic environment necessitates continuous development and adaptation in security solutions. Furthermore, the rise of ransomware-as-a-service (RaaS) models has democratized access to these attacks, making them easier to launch and deploy, increasing the overall threat.
Significance of the Partnership in the Broader Market
This partnership between Intel and Check Point is strategically significant due to the combined strengths of each company. Intel’s expertise in hardware and chip design can enhance the performance and efficiency of Check Point’s security software, potentially leading to faster threat detection and response. Conversely, Check Point’s deep understanding of cybersecurity threats can inform Intel’s hardware designs, creating a more resilient ecosystem.
This combined approach can address the growing need for more robust and proactive security measures.
Key Competitors and Their Strategies
Several prominent players are actively competing in the ransomware protection market. Companies like Palo Alto Networks, McAfee, and Trend Micro are investing heavily in research and development to stay ahead of the curve. Their strategies typically involve developing comprehensive security suites with advanced threat detection capabilities, as well as proactive security solutions to prevent attacks. Their competitive advantage often lies in the breadth of their solutions, providing a more holistic security approach.
Comparison with Alternative Solutions
Alternative solutions to ransomware protection often focus on specific aspects of the problem. For example, some solutions focus on network security, others on endpoint protection, and still others on data backup and recovery. This partnership, however, seeks to integrate hardware and software capabilities, offering a more holistic and comprehensive approach. By integrating hardware-level protection with software-level analysis, it can potentially provide a more efficient and robust defense against ransomware attacks.
Potential Impact on the Future of Ransomware Protection
This partnership has the potential to revolutionize the way organizations approach ransomware protection. The combination of Intel’s hardware expertise with Check Point’s software knowledge could lead to a new generation of security solutions, with a focus on both preventing and mitigating the impact of attacks. By proactively integrating security measures at the hardware level, the partnership could significantly enhance the overall security posture of systems, reducing the attack surface and improving response times.
Growth of Ransomware Attacks (Illustrative Data)
| Year | Estimated Number of Attacks |
|---|---|
| 2020 | ~300,000 |
| 2021 | ~600,000 |
| 2022 | ~800,000 |
| 2023 (Estimated) | ~1,000,000+ |
Note: These figures are estimates and represent the general trend. Exact figures are often difficult to obtain due to underreporting and the constantly evolving nature of the threat.
Security Implications and Risks
This partnership between Intel and Check Point, while promising in its aim to bolster ransomware protection, also introduces potential security implications that require careful consideration. Integrating two complex security systems inherently creates new points of vulnerability that need to be addressed proactively. Understanding these risks is crucial for maximizing the benefits of the partnership while mitigating potential harm.
Intel and Check Point’s expanded partnership for ransomware protection is a smart move, especially considering recent vulnerabilities. For example, the recent Azure Cosmos DB Vulnerability Details highlight the critical need for robust security measures across the board. Understanding these weaknesses, like those detailed in Azure Cosmos DB Vulnerability Details , helps organizations strengthen their defenses. This increased collaboration between Intel and Check Point is a crucial step toward a more secure digital future.
Potential Vulnerabilities of the Integrated Solution
The integration of Intel and Check Point’s technologies creates a complex system. Any new system, especially one built upon the intricate layers of modern security, is susceptible to vulnerabilities that were not present in the individual components. These vulnerabilities could stem from misconfigurations, unforeseen interactions between the two systems, or even previously unknown exploits that could be leveraged by attackers.
It’s essential to rigorously test and validate the integration process to identify and address these issues before deployment.
Risks of Misuse or Unintended Consequences
Integrated security solutions can be prone to unintended consequences if not properly designed and tested. One example could be a scenario where a feature intended to enhance protection against one type of ransomware inadvertently creates a pathway for another type to exploit. Careful analysis of potential interactions and edge cases is vital during the development and testing phases to minimize these risks.
Attacker Exploitation of Potential Weaknesses
Attackers are constantly seeking new vulnerabilities. The combination of Intel and Check Point technologies presents a new target for their efforts. Attackers could attempt to exploit weaknesses in the integration process or misconfigurations within the integrated system. They might also try to leverage vulnerabilities in either individual component to compromise the combined solution. Cybersecurity professionals must be proactive in anticipating these potential exploits.
Importance of Ongoing Security Updates and Maintenance
A critical aspect of any security solution is ongoing maintenance. The integrated system will require regular updates to address emerging threats and vulnerabilities. Failure to implement these updates promptly could leave the solution susceptible to exploitation. The partnership needs to establish a clear update and maintenance plan, including communication channels and processes for addressing potential issues.
Potential Security Threats and Mitigation Strategies
The following table Artikels potential security threats and corresponding mitigation strategies for the integrated solution.
| Potential Security Threat | Mitigation Strategy |
|---|---|
| Configuration Errors | Thorough configuration testing, rigorous validation procedures, and comprehensive documentation to prevent misconfigurations during deployment and maintenance. |
| Exploits Targeting Integration Points | Continuous vulnerability assessments of the integrated system, penetration testing to identify weaknesses, and proactive patching and security updates. |
| Zero-Day Exploits | Collaboration with security researchers to rapidly identify and address emerging threats, continuous monitoring for anomalies, and rapid response mechanisms. |
| Insider Threats | Robust access controls, regular security awareness training for personnel involved in managing the integrated solution, and stringent monitoring of system activity. |
| Supply Chain Attacks | Rigorous vetting of all components and suppliers, implementing security measures at the supply chain level, and maintaining transparent communication channels. |
Future Directions and Implications
This Intel and Check Point partnership holds significant potential for the future of ransomware protection. The combined expertise and resources of these two industry giants can drive innovation and shape the cybersecurity landscape in ways that benefit both businesses and consumers. The evolving nature of ransomware attacks necessitates adaptable and proactive strategies, and this partnership is poised to address these challenges head-on.The partnership’s future trajectory hinges on its ability to adapt to emerging threats and maintain its leading position in the fight against ransomware.
This involves not only technical innovation but also proactive collaboration with other security players and a deep understanding of the ever-changing threat landscape.
Potential Future Developments
The partnership’s future will likely involve the development of more sophisticated and integrated security solutions. This includes tools that proactively identify and neutralize ransomware threats before they can cause significant damage. Anticipating and mitigating vulnerabilities is crucial.
Evolution and Adaptation to New Threats
The partnership’s success will depend on its ability to adapt to the constant evolution of ransomware tactics. This requires ongoing research and development, incorporating real-time threat intelligence into the solutions, and enabling rapid updates and patches. For instance, the emergence of ransomware-as-a-service (RaaS) necessitates solutions that target the entire attack chain, not just the endpoint.
Implications for the Broader Cybersecurity Landscape
This partnership could set a new standard for collaboration and information sharing among cybersecurity providers. It may also influence the development of industry-wide best practices and regulatory frameworks for ransomware protection. The collaboration might lead to improved security protocols and more robust defense mechanisms across various sectors.
Influence on Future Industry Standards
The partnership’s advancements could significantly impact future industry standards for ransomware protection. For example, the development of standardized testing procedures for ransomware-resistant software could help ensure that products meet minimum security requirements. This could lead to increased trust and confidence in security solutions.
Potential Challenges
- Maintaining Competitive Advantage: The cybersecurity landscape is highly competitive. Maintaining a leading edge in the face of continuous innovation from other players and emerging threats is crucial. The partnership must consistently innovate and improve its offerings to stay ahead of the competition.
- Integration Complexity: Combining two large and complex software ecosystems can present significant integration challenges. This may involve technical complexities in merging their respective technologies and ensuring seamless data exchange and communication.
- Maintaining Data Security: The partnership must prioritize data security to maintain customer trust. This means robust data protection mechanisms and adherence to strict privacy regulations.
- Scalability and Support: The partnership must be prepared to scale its solutions to meet the demands of a growing market. This includes ensuring adequate support resources to address user needs and potential issues.
Illustrative Examples
This section delves into practical scenarios demonstrating the efficacy of the Intel and Check Point partnership’s ransomware protection solution. We’ll explore how these technologies work in tandem to thwart attacks, recover from breaches, and mitigate vulnerabilities. Understanding these examples provides valuable insights into the real-world applications and potential impact of this innovative approach.
Intel and Check Point’s expanded partnership on ransomware protection is a smart move, especially given the current threat landscape. It’s crucial for businesses to stay ahead of evolving cyberattacks. This kind of proactive security measure is essential, and dovetails nicely with the Department of Justice’s recent “Safe Harbor” policy for Massachusetts transactions, Department of Justice Offers Safe Harbor for MA Transactions.
Ultimately, both initiatives highlight the importance of robust security measures for companies navigating the complex world of data protection and compliance.
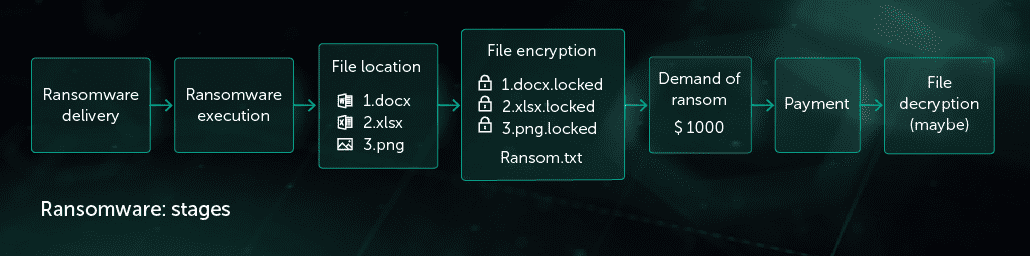
Hypothetical Ransomware Attack and Response, Intel and check point software extend partnership for ransomware protection
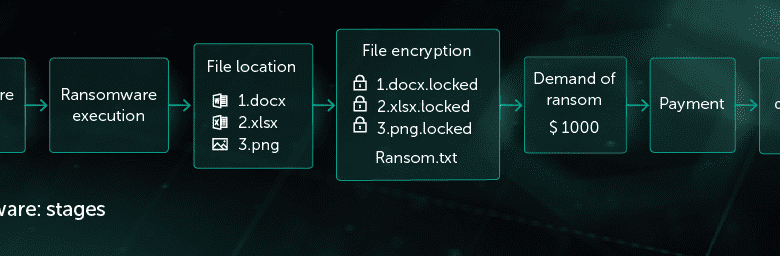
A mid-sized manufacturing company, “TechPro,” experiences a ransomware attack targeting their critical production databases. The attackers encrypt the files, demanding a hefty ransom to restore access. The Intel and Check Point solution, proactively deployed, identifies the attack in real-time using advanced threat detection. Check Point’s security gateway prevents further data exfiltration, while Intel’s hardware-based security features isolate the compromised systems.
This rapid containment prevents the spread of the malware and limits the damage. Recovery involves using the solution’s built-in recovery mechanisms to restore the affected databases from secure backups.
Successful Ransomware Defense Case Study
A large financial institution, “FinCorp,” successfully defended against a sophisticated ransomware attack leveraging a zero-day exploit. Employing a combination of Intel SGX (Software Guard Extensions) and Check Point’s threat intelligence, they quickly identified the attack vector. The threat detection and response capabilities of Check Point’s security infrastructure blocked the attack before the malware could encrypt sensitive data. Intel’s hardware security features isolated the compromised servers, preventing the malware from spreading across the network.
This swift action minimized the damage and disruption to FinCorp’s operations.
Demonstrating a Potential Vulnerability and Mitigation
A potential vulnerability exists in older versions of the company’s software that lack strong access controls. A malicious actor could exploit this to gain unauthorized access to sensitive data. The Intel and Check Point solution addresses this by providing granular access controls, coupled with threat intelligence and proactive security monitoring. Check Point’s advanced threat detection and response capabilities identify and block malicious attempts.
Intel’s hardware-based security features isolate and contain any potential breach. This comprehensive approach ensures that vulnerabilities are addressed proactively. This is further reinforced by regular security updates and vulnerability assessments.
Comparative Analysis of Ransomware Response Strategies
| Response Strategy | Description | Strengths | Weaknesses |
|---|---|---|---|
| Proactive Prevention | Implement strong security measures, including multi-factor authentication, endpoint detection and response (EDR), and regular security audits. | Reduces the likelihood of a successful attack. | Requires ongoing effort and resources. |
| Rapid Containment | Detect and isolate infected systems quickly to limit the damage. | Minimizes the impact of a breach. | Requires a robust incident response plan. |
| Data Recovery | Restore data from backups or using advanced recovery mechanisms. | Preserves critical business operations. | Time-consuming if backups are not regularly updated. |
| Post-Incident Analysis | Identify the cause of the attack to prevent future incidents. | Provides valuable insights for improvement. | Requires thorough investigation and documentation. |
This table highlights the core strategies for ransomware response. A successful strategy usually involves a combination of these approaches, with proactive prevention being the foundation for robust security.
Closing Summary
In conclusion, the Intel and Check Point partnership represents a significant advancement in ransomware protection. By combining hardware and software strengths, they are creating a more comprehensive and robust security solution. This approach not only addresses current threats but also positions them to adapt and evolve as ransomware tactics change. The future of cybersecurity may very well be shaped by this innovative collaboration.
Commonly Asked Questions
What are the specific technologies used by Intel and Check Point in this partnership?
The partnership details specific technologies used, integrating Intel’s hardware-level security features with Check Point’s software solutions for advanced threat detection and response. Precise details are not yet publicly available, but it’s expected that they will include advanced threat intelligence, behavioral analysis, and hardware-based protection.
How does this partnership compare to existing solutions in the market?
The partnership aims to offer a more comprehensive and proactive defense, integrating hardware and software for a multi-layered approach to ransomware protection. Direct comparisons to existing solutions will require more in-depth analysis and testing.
What are the potential risks or vulnerabilities associated with this integrated solution?
Any integrated system, like this one, can potentially introduce new vulnerabilities if not thoroughly tested. However, the companies are expected to address these risks through rigorous testing and ongoing security updates.
What is the estimated market impact of this partnership on ransomware protection?
The impact is difficult to quantify without specific data, but the partnership is expected to drive innovation and potentially shift the market towards more integrated security solutions, leading to more robust protection against ransomware.