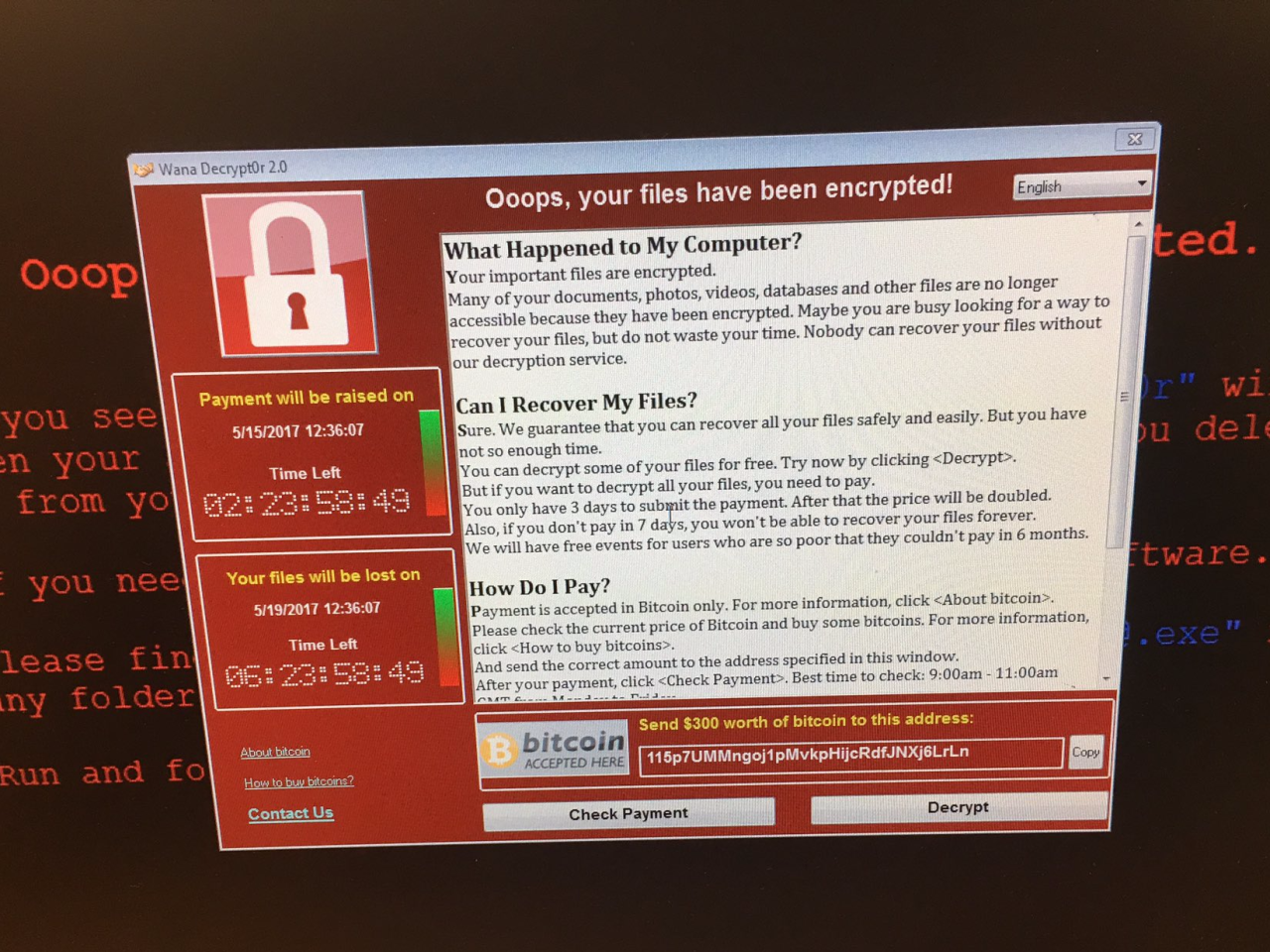
Repeat Ransomware Attacks on 78 Victims Who Paid
Repeat ransomware attacks on 78 of victims who pay – it sounds unbelievable, right? But it’s a chilling reality highlighting a critical flaw in our current cybersecurity landscape. This isn’t just about losing data; it’s about the devastating financial, reputational, and emotional toll on businesses and individuals who, despite paying the ransom, become repeat targets. We’ll dive into why this happens, what vulnerabilities are exploited, and most importantly, how to protect yourself from becoming another statistic.
This alarming trend underscores the ineffectiveness of simply paying the ransom. We’ll explore the common threads connecting these repeat victims, examining their security practices (or lack thereof) before and after the initial attack. We’ll also delve into the psychology behind these attacks, looking at why cybercriminals repeatedly target those who’ve already paid up. Get ready to uncover the strategies these malicious actors use and discover how to bolster your defenses against future attacks.
The Phenomenon of Repeat Ransomware Attacks
The disturbing reality is that many organizations, despite paying ransoms, find themselves victims of repeat ransomware attacks. This isn’t simply bad luck; it’s a complex issue stemming from a combination of factors, highlighting vulnerabilities in cybersecurity practices and the persistent threat landscape. Understanding these factors is crucial for developing effective preventative measures.
Repeat ransomware attacks often hinge on the initial breach’s lasting impact. Cybercriminals might exploit initial vulnerabilities left unpatched after the first attack, or they may have successfully exfiltrated data during the initial incident, which they then use for blackmail or further exploitation. Even if systems are restored, residual malware or backdoors might remain undetected, providing a convenient re-entry point for subsequent attacks.
Furthermore, the initial attack might have exposed weaknesses in an organization’s security posture, such as insufficient employee training or outdated security protocols, making them a prime target for future attacks. The criminals often leverage the same or similar techniques, demonstrating a pattern of exploiting known vulnerabilities rather than developing entirely new methods. This highlights the importance of comprehensive security audits and remediation following any ransomware incident.
Factors Contributing to Repeat Victimization
Several factors significantly increase the likelihood of repeat ransomware attacks. These include inadequate incident response plans, insufficient employee training on phishing and social engineering techniques, and a lack of robust security monitoring and threat detection capabilities. A failure to thoroughly investigate the root cause of the initial attack also contributes to recurring incidents. Organizations often focus solely on data recovery and ransom payment, neglecting the critical step of identifying and addressing the underlying vulnerabilities that allowed the initial breach.
This leaves them exposed to similar attacks in the future. The use of weak or easily guessable passwords, combined with insufficient multi-factor authentication, further compounds the risk. Finally, a lack of regular security updates and patching across all systems and software creates numerous entry points for malicious actors.
Typical Timeframe Between Attacks
The timeframe between initial and subsequent ransomware attacks varies considerably, ranging from a few weeks to several months or even years. Several factors influence this timeline. If the attackers left behind a backdoor or exploited a persistent vulnerability, the subsequent attack might occur relatively quickly. In other cases, the attackers might wait to observe the organization’s recovery efforts and identify any remaining weaknesses before launching a second attack.
Sometimes, the same group might target multiple organizations simultaneously, using the same tactics and techniques, leading to seemingly unrelated but connected incidents. In some cases, the interval can be prolonged, as attackers might focus on other targets and then return to the same victim once they have improved their techniques or have a more sophisticated attack plan. Predicting the exact timeframe is challenging, emphasizing the need for continuous vigilance and proactive security measures.
Examples of Repeat Ransomware Attacks
| Victim Type | Industry | Ransomware Variant | Time Between Attacks |
|---|---|---|---|
| Small Business | Retail | Ryuk | 6 months |
| Large Corporation | Healthcare | REvil | 1 year |
| Government Agency | Local Government | Conti | 3 months |
| Educational Institution | University | LockBit | 9 months |
Analysis of Payment and Subsequent Attacks: Repeat Ransomware Attacks On 78 Of Victims Who Pay
The disturbing reality of repeat ransomware attacks on victims who previously paid ransoms highlights a critical flaw in the common belief that paying up guarantees safety. This section delves into the reasons behind this phenomenon, comparing the security postures of those who paid with those who didn’t, and examining the motivations and methods employed by attackers in these subsequent attacks.The effectiveness of paying ransoms as a preventative measure is demonstrably low.
While some victims might experience a temporary reprieve, many find themselves targeted again, often with more sophisticated attacks. This suggests that the initial payment doesn’t deter attackers, but rather might incentivize them to return, possibly due to perceived vulnerability or the success of their previous extortion attempt.
Comparison of Security Measures Implemented by Victims
Victims who paid ransoms often believed they had mitigated their risk by complying with the attacker’s demands. However, this perception frequently proves false. Many fail to implement comprehensive security upgrades following the initial attack, leaving them vulnerable to future exploitation. In contrast, victims who refused to pay often felt a stronger impetus to improve their security infrastructure, investing in updated software, robust patching procedures, and enhanced network security measures.
This proactive approach, though demanding upfront investment, ultimately proves more effective in preventing repeat attacks.
Effectiveness of Ransom Payments in Preventing Future Attacks
Paying a ransom is not a guarantee of future security. In fact, data from numerous cybersecurity firms indicates that a significant percentage of ransomware victims who pay are targeted again. This is due to several factors. First, the attacker’s initial success confirms the victim’s vulnerability, making them a prime target for further exploitation. Second, the payment itself can be seen as a confirmation that the victim is willing to pay, making them an easier target for future attacks.
Third, attackers often use the same vulnerabilities in repeat attacks, suggesting a lack of thorough remediation by the victim following the initial incident. For example, the infamous Colonial Pipeline ransomware attack highlighted this issue; while they paid the ransom, they later suffered further disruptions due to insufficient security improvements.
Motivations of Attackers in Targeting Previous Payers
Attackers target previous payers for several reasons. The most obvious is financial gain. A victim who has already paid once is perceived as a low-risk, high-reward target. They’ve demonstrated a willingness to pay, making future extortion attempts more likely to succeed. Furthermore, attackers might seek to exploit previously identified vulnerabilities, streamlining the process and increasing their chances of success.
The perceived ease of access also contributes to the decision to re-target these victims. They may also use the information gained during the first attack to launch more targeted and sophisticated attacks.
Common Vulnerabilities Exploited in Repeat Attacks
Repeat attacks often leverage the same vulnerabilities exploited in the initial attack, indicating a failure by the victim to adequately address the root cause of the breach. This includes outdated software, unpatched systems, weak passwords, and insufficient network security. For example, if the initial attack exploited a vulnerability in a specific software application, the attackers might attempt to exploit the same vulnerability or similar vulnerabilities in other applications in subsequent attacks.
Furthermore, attackers often use phishing emails or other social engineering tactics to gain access, demonstrating a lack of employee security awareness training. These repeated vulnerabilities highlight the need for comprehensive security assessments and remediation strategies, rather than simply paying the ransom and hoping for the best.
The Role of Data Recovery and Restoration

Paying a ransom doesn’t guarantee a smooth data recovery process. In fact, many organizations find themselves facing significant challenges even after handing over the money. The recovery process itself is fraught with potential pitfalls, and mistakes made during this critical phase can leave organizations vulnerable to future attacks. Understanding these challenges and implementing robust recovery and security protocols is crucial for minimizing long-term damage.The process of data recovery after a ransomware attack typically begins with decrypting the affected files.
This often involves using the decryption key provided by the attackers (if they deliver one that actually works), or employing specialized tools developed by cybersecurity firms or the affected software vendor. However, this is not always straightforward. The decryption process might be incomplete, leaving some files corrupted or inaccessible. Furthermore, the decryption key might not work effectively, or the ransomware may have inflicted damage beyond simple encryption, such as data deletion or system corruption.
This highlights a critical weakness: reliance on the attacker’s goodwill and the effectiveness of their decryption tools. Another significant weakness lies in the potential for backdoors or other malicious code to remain on the system even after decryption, creating a lingering security risk.
Data Restoration Mistakes and Vulnerabilities
Rushing the restoration process is a common mistake. Organizations, eager to get back to business, often skip crucial steps like verifying the integrity of restored data and thoroughly cleaning the affected systems. This haste can lead to the reintroduction of malware, data corruption, or the persistence of vulnerabilities. Another frequent error is failing to properly back up restored data.
This oversight leaves the organization vulnerable to a repeat attack, as the restored data becomes the new target. Some organizations also neglect to update their security protocols after a ransomware attack, leaving themselves open to similar attacks in the future. For instance, an organization might restore data from an infected backup, effectively reinstalling the ransomware. Or, they might fail to patch known vulnerabilities exploited in the initial attack, making them easy targets again.
Securing Data After Ransom Payment
After paying a ransom and recovering data, organizations must take immediate and decisive steps to secure their systems. This includes a complete forensic analysis of the affected systems to identify the attack vector and any remaining malware. A thorough system rebuild, rather than simply restoring data, is often necessary. This involves reinstalling the operating system and applications from clean, uninfected sources.
All software should be updated to the latest versions, patching known vulnerabilities. Furthermore, robust multi-factor authentication should be implemented across all systems, and access controls should be reviewed and tightened. Regular security audits and penetration testing are also essential to identify and address any remaining vulnerabilities. Finally, implementing a comprehensive backup and recovery strategy is paramount, ensuring regular backups are stored offline or in an air-gapped environment.
Data Recovery and Security Best Practices Checklist
Before initiating data recovery, it’s crucial to have a comprehensive plan in place. This plan should include detailed steps for data recovery, system restoration, and security enhancements. The following checklist summarizes critical steps:
- Conduct a thorough forensic analysis to identify the attack vector and any remaining malware.
- Verify the integrity of the decryption key and the restored data.
- Rebuild affected systems from clean installations, avoiding restoration from potentially infected backups.
- Update all software and operating systems to the latest versions, including security patches.
- Implement robust multi-factor authentication and access controls.
- Regularly back up critical data to offline or air-gapped storage.
- Conduct regular security audits and penetration testing to identify vulnerabilities.
- Develop and implement an incident response plan to address future attacks effectively.
- Educate employees about cybersecurity best practices and phishing awareness.
- Review and update security policies and procedures regularly.
Security Gaps and Remediation Strategies
The horrifying reality of repeat ransomware attacks highlights significant weaknesses in current cybersecurity practices. Organizations that pay ransoms often find themselves targeted again, demonstrating that simply paying the ransom doesn’t guarantee safety. Understanding the vulnerabilities exploited and implementing robust remediation strategies is crucial to breaking this vicious cycle.The persistence of repeat ransomware attacks underscores the need for a proactive, multi-layered approach to security.
Simply patching known vulnerabilities isn’t enough; organizations must adopt a holistic strategy that addresses both technical and human factors. This includes implementing strong authentication methods, regularly updating software, and educating employees about phishing and social engineering tactics.
Commonly Exploited Security Vulnerabilities
Many security vulnerabilities are frequently exploited in repeat ransomware attacks. These vulnerabilities often stem from outdated software, misconfigured systems, and inadequate employee training. For example, unpatched vulnerabilities in older versions of Windows or other operating systems can provide easy entry points for malicious actors. Similarly, weak or default passwords, along with insufficient access controls, can allow attackers to easily gain unauthorized access to sensitive data.
Furthermore, phishing emails and social engineering attacks continue to be highly effective in bypassing technical security measures, especially when employees lack awareness and training. Exploiting these vulnerabilities often allows attackers to move laterally within a network, gaining access to more critical systems and data.
Comparison of Security Measures Effectiveness
Antivirus software, while a critical first line of defense, is often insufficient on its own to prevent repeat attacks. Many sophisticated ransomware variants can evade detection by traditional antivirus solutions. Firewalls can effectively block malicious traffic, but they can’t prevent attacks that originate from within the network or exploit zero-day vulnerabilities. Data backups are crucial for recovery, but they don’t prevent the initial infection.
The most effective security measures involve a combination of technical controls and employee training, emphasizing a proactive approach rather than solely relying on reactive measures. Multi-factor authentication (MFA), for instance, significantly reduces the risk of unauthorized access, even if passwords are compromised. Regular security audits and penetration testing can help identify and address vulnerabilities before attackers exploit them.
Recommended Security Protocols and Technologies
Implementing a robust security posture requires a layered approach encompassing several key protocols and technologies. This includes:
- Multi-factor authentication (MFA): MFA adds an extra layer of security by requiring multiple forms of authentication, such as a password and a one-time code from a mobile app or security key. This makes it significantly harder for attackers to gain access even if they obtain a password.
- Regular software updates and patching: Keeping all software, including operating systems, applications, and firmware, up-to-date with the latest security patches is crucial in mitigating known vulnerabilities.
- Strong password policies and password management tools: Enforcing strong, unique passwords for all accounts and utilizing password managers to securely store and manage them is essential.
- Network segmentation: Dividing the network into smaller, isolated segments limits the impact of a successful attack, preventing attackers from easily moving laterally across the network.
- Intrusion detection and prevention systems (IDS/IPS): IDS/IPS systems monitor network traffic for suspicious activity and can block or alert on malicious attempts.
- Regular security awareness training for employees: Educating employees about phishing scams, social engineering tactics, and safe internet practices is vital in preventing human error, a common entry point for ransomware attacks.
- Data backups and recovery plans: Regularly backing up critical data to offline or cloud storage is crucial for recovery in the event of a ransomware attack. A well-defined recovery plan ensures a swift and efficient restoration process.
Implementing Multi-Factor Authentication and Robust Security Controls
Implementing MFA involves integrating a second factor of authentication beyond a password. This could be a time-based one-time password (TOTP) generated by an authenticator app, a hardware security key, or a biometric authentication method like fingerprint scanning. Robust security controls go beyond MFA, encompassing all the measures mentioned previously. For example, enforcing strong password policies, regularly updating software, and implementing network segmentation are all vital components of a comprehensive security strategy.
Consider deploying a security information and event management (SIEM) system to centralize security logs and facilitate threat detection and response. Regular security audits and penetration testing by external security experts can identify vulnerabilities and weaknesses that might be missed by internal teams. The implementation process requires careful planning, considering the specific needs and resources of the organization.
It’s also crucial to provide adequate training to employees on the use and importance of these new security measures.
It’s crazy how 78% of ransomware victims who pay get hit again! This highlights the urgent need for robust, secure systems. Building those systems is easier than ever thanks to advancements like domino app dev the low code and pro code future , which allows for faster development of secure applications. Ultimately, though, even the best tech can’t completely eliminate the risk of repeat ransomware attacks, so vigilance remains key.
The Legal and Ethical Implications
Paying ransoms and suffering repeat ransomware attacks presents a complex web of legal and ethical dilemmas for organizations. The decision to pay, while seemingly pragmatic in the short term, can have significant long-term repercussions, both financially and legally. Furthermore, the ethical implications of rewarding criminal behavior are profound and demand careful consideration.The legal ramifications for organizations that pay ransoms and experience repeat attacks are multifaceted.
While there’s no universally enforced law explicitly prohibiting ransom payments, several legal frameworks can be brought to bear. For example, regulations related to data privacy (like GDPR in Europe or CCPA in California) might hold organizations accountable for failing to adequately protect sensitive data, even if a ransom was paid. Furthermore, insurance policies often exclude coverage for losses resulting from paying ransoms, leaving organizations financially exposed.
Repeat attacks, particularly, can be used to argue negligence on the part of the organization, leading to further legal action from affected parties or regulatory bodies. The potential for shareholder lawsuits, alleging mismanagement and failure to implement adequate security measures, is also a significant concern.
Legal Ramifications of Ransom Payments and Repeat Attacks
Organizations that pay ransoms and subsequently experience repeat attacks face potential legal liabilities stemming from several sources. These include violations of data privacy regulations, breaches of contract (if data protection is part of service level agreements), and potential civil lawsuits from affected individuals or businesses. The fact that a ransom was paid might be interpreted as an admission of guilt or negligence, making the organization more vulnerable to legal challenges.
Moreover, investigations by law enforcement agencies, spurred by repeat incidents, could lead to fines and penalties. A company’s insurance provider might also contest claims based on the payment of ransom, claiming that it encouraged further attacks. The legal landscape is complex and varies by jurisdiction, making it crucial for organizations to seek legal counsel specializing in cybersecurity and data privacy.
Ethical Considerations Surrounding Ransom Payments
The ethical implications of paying ransoms are significant. Paying a ransom directly funds criminal activity, potentially empowering cybercriminals and encouraging further attacks, not only against the victim but also against other organizations. This creates a moral hazard, undermining efforts to combat ransomware. While the immediate goal of restoring operations is understandable, the long-term consequences of rewarding malicious actors outweigh the short-term benefits.
The ethical dilemma lies in balancing the need to protect data and operations with the broader societal impact of supporting criminal enterprises. Furthermore, paying a ransom doesn’t guarantee data recovery or prevent future attacks; it merely delays the inevitable and potentially makes the organization a more attractive target.
Legal Liabilities Associated with Inadequate Security Measures
Inadequate security measures leading to repeat ransomware attacks expose organizations to substantial legal liabilities. This stems from a failure to meet their legal obligations regarding data protection and security. Demonstrating a lack of reasonable security measures, such as failing to implement multi-factor authentication, neglecting regular software updates, or failing to conduct security audits, can be used in legal proceedings to establish negligence.
This negligence can lead to substantial fines, legal fees, and reputational damage. The burden of proof rests on the organization to demonstrate that they took reasonable steps to protect their data and systems. Failure to do so can result in significant financial and legal consequences.
Ethical Guidelines for Organizations Facing Ransomware Threats, Repeat ransomware attacks on 78 of victims who pay
Developing and implementing a robust cybersecurity strategy is paramount. Here are ethical guidelines to help organizations navigate ransomware threats:
- Prioritize proactive security measures over reactive responses. This includes regular software updates, employee training on security best practices, and robust data backup and recovery plans.
- Refrain from paying ransoms unless absolutely necessary and only after consulting with legal and cybersecurity experts. Paying a ransom should be a last resort, not a first response.
- Report ransomware attacks to law enforcement immediately. This aids in investigations and helps combat cybercrime.
- Maintain transparent communication with affected parties, including customers and employees, regarding the incident and the steps taken to mitigate the impact.
- Conduct thorough post-incident analysis to identify vulnerabilities and implement corrective actions to prevent future attacks.
- Invest in comprehensive cybersecurity insurance to mitigate financial risks.
The Impact on Victims
Repeat ransomware attacks inflict devastating and long-lasting consequences on victims, extending far beyond the initial data breach and financial losses. The cumulative effect of multiple attacks compounds the damage, creating a cycle of disruption and insecurity that can cripple even the most resilient organizations. Understanding the full impact is crucial for developing effective mitigation strategies and supporting affected businesses.The long-term ramifications of repeat ransomware attacks are profound and multifaceted.
Financially, organizations face repeated extortion payments, escalating legal fees, the cost of data recovery and restoration, and potentially significant losses in revenue due to operational downtime and damaged reputation. Beyond the direct financial burden, the reputational damage can be equally devastating. Customers may lose trust, leading to decreased sales and potential business failure. Investors may withdraw support, impacting the organization’s long-term viability.
Furthermore, the repeated security breaches can erode stakeholder confidence, affecting employee morale and attracting negative media attention.
The Emotional and Psychological Toll
The emotional and psychological impact on employees and stakeholders should not be underestimated. The constant threat of another attack creates a climate of fear and anxiety. Employees may experience stress, burnout, and decreased productivity. The pressure to meet deadlines while dealing with the aftermath of a security breach can be immense, leading to increased levels of stress and mental health challenges.
Stakeholders, including investors and customers, may also experience anxiety and distrust, impacting their relationship with the organization. The repeated nature of the attacks amplifies these effects, creating a cycle of trauma and uncertainty.
Examples of Successful Recovery
While the recovery process is challenging, some organizations have successfully navigated the aftermath of repeat ransomware attacks. For example, a mid-sized manufacturing company implemented a robust cybersecurity framework after their first attack, including multi-factor authentication, regular security audits, and employee training. This proactive approach significantly reduced the impact of a subsequent attack, limiting the damage and enabling a faster recovery.
Another example involves a healthcare provider that invested heavily in data backups and disaster recovery planning after experiencing a ransomware attack. Their meticulous planning allowed them to restore critical systems within hours, minimizing disruption to patient care. These examples highlight the importance of proactive security measures and comprehensive recovery plans in mitigating the impact of repeat ransomware attacks.
Mitigation Strategies for the Impact of Repeat Ransomware Attacks
| Impact Category | Mitigation Strategies |
|---|---|
| Financial | Cybersecurity insurance, robust incident response plan, diversification of revenue streams, financial reserves for recovery. |
| Reputational | Transparent communication with stakeholders, proactive public relations, community engagement, demonstrable commitment to security improvements. |
| Operational | Redundant systems and data backups, disaster recovery planning, robust security protocols, employee training, incident response team. |
Conclusion
So, what have we learned? Paying a ransom is no guarantee of safety; in fact, it can often increase your risk. The key takeaway here is proactive security. Investing in robust security measures, from multi-factor authentication to regular security audits, is crucial. Understanding the vulnerabilities exploited in these repeat attacks empowers us to build stronger defenses.
Don’t become a statistic – take control of your cybersecurity and protect yourself from the devastating impact of ransomware.
Quick FAQs
What types of businesses are most frequently targeted by repeat ransomware attacks?
While any business can be a target, those in healthcare, finance, and manufacturing are often hit repeatedly due to the sensitive data they hold and the potential for high ransoms.
How long is the typical timeframe between initial and subsequent attacks?
This varies widely, ranging from weeks to months or even years. Attackers often wait until security measures are relaxed or new vulnerabilities are discovered.
Are there legal consequences for paying a ransom?
While not always illegal, paying a ransom can have legal ramifications, particularly if it violates sanctions or involves organizations dealing with sensitive data. It’s crucial to consult legal counsel.
Can insurance cover the costs of repeat ransomware attacks?
Cybersecurity insurance can help cover some costs associated with ransomware attacks, but coverage details vary. It’s essential to review your policy carefully.