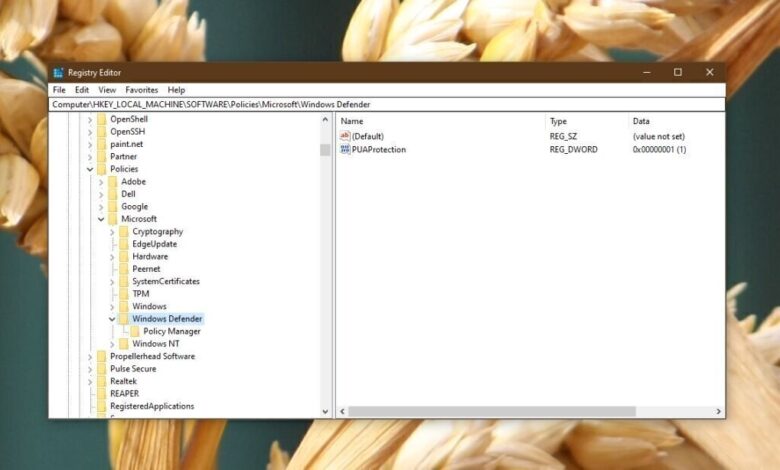
Restricting Disable Licensing Features Using Windows Group Policy Editor
Restricting disable licensing features using Windows Group Policy Editor? Sounds complicated, right? But trust me, mastering this powerful tool can be a game-changer for managing software licenses across your network. This isn’t just about ticking boxes; it’s about gaining control, improving security, and ultimately saving your organization money. We’ll dive into the nitty-gritty of using Group Policy Objects (GPOs) to restrict software installations, manage activation keys, and even monitor software usage for compliance.
Get ready to unlock the potential of GPOs and streamline your software licensing!
This post will walk you through a practical, step-by-step guide on leveraging the power of Windows Group Policy Editor to control and restrict software licensing. We’ll cover everything from understanding the basics of GPOs and targeting specific users, to implementing robust monitoring and troubleshooting common issues. We’ll also explore alternative methods and best practices to ensure a secure and efficient software license management strategy.
Understanding Group Policy Objects (GPOs) and their Role in Software Restriction
Group Policy Objects (GPOs) are a powerful administrative tool within Windows Server environments, providing centralized management and control over various aspects of the operating system and applications. They are crucial for managing software licensing by enabling administrators to define rules and restrictions on software installation, execution, and access across multiple machines within a domain. This centralized approach simplifies software deployment and ensures consistent policy enforcement, enhancing security and compliance.GPOs control software installation and execution through a hierarchical structure linked to Organizational Units (OUs) within the Active Directory.
When a user logs in or a computer starts, the system evaluates the GPOs linked to the user’s or computer’s OU. These GPOs contain settings that dictate which software can be installed, run, or accessed. If a user attempts to install or run software that violates the defined GPO settings, the system will either block the action or prompt the user with a message explaining the restriction.
This mechanism allows administrators to enforce licensing agreements and prevent unauthorized software usage effectively.
GPO Settings Relevant to Software Licensing
Several GPO settings directly influence software licensing. These settings allow administrators to fine-tune control over software deployment and usage, preventing unauthorized installations and ensuring compliance with licensing agreements. For example, administrators can leverage software restriction policies to create a whitelist of approved applications, effectively blocking any software not included in this list. Similarly, they can utilize the “Software Installation” settings to deploy and manage software updates centrally.
Another key area is the use of scripts to automate software licensing processes. These scripts can be used to verify licenses, update license keys, or automatically disable software that is not properly licensed.
Creating a New GPO
Creating a new GPO involves a few straightforward steps within the Group Policy Management Console (GPMC.MSC). First, open the GPMC.MSC. Then, locate the OU where you want the GPO to apply. Right-click on the OU and select “Create a GPO in this domain, and Link it here…” A new window will appear prompting you to name the GPO.
Give it a descriptive name, such as “Software Licensing Restrictions.” After clicking “OK,” the new GPO will be created and linked to the selected OU. You can then edit the GPO by right-clicking it and selecting “Edit.” This opens the Group Policy Management Editor, where you can configure various settings to control software installation and execution based on licensing requirements.
Navigating through the editor, you’ll find various policy settings to manage software installations, including those relating to application control, script execution, and user rights assignments.
Identifying Target Users and Computers for Policy Application
Precisely targeting the application of restrictive licensing policies is crucial for effective management and avoids unintended disruptions. Misdirected policies can impact productivity and user experience, highlighting the need for careful planning and execution. This section will explore various methods to ensure your policies reach only the intended users and computers.Targeting specific user groups or organizational units (OUs) within your Active Directory structure is the most common and effective approach.
This granular control allows you to apply different policies based on roles, departments, or security levels. For instance, you might apply stringent licensing restrictions to a group of temporary contractors while allowing more flexibility for permanent employees.
Targeting with Security Groups and Organizational Units
Using Active Directory security groups and OUs provides a hierarchical and manageable method for policy application. Security groups allow you to easily add or remove users, while OUs offer a structured way to organize users and computers based on their location or function within the organization. By linking a GPO to a specific security group or OU, the policy will automatically apply to all members of that group or OU.
For example, you could create a security group called “Marketing Team” and link a GPO restricting the use of certain software to this group. All users added to the “Marketing Team” group would then inherit the licensing restrictions defined in that GPO.
Effective Filtering Criteria for Precise Policy Application
Precise policy application often requires more than just assigning a GPO to an OU or group. You can leverage advanced filtering options within Group Policy Management to further refine your targeting. This allows for highly specific application of policies based on various attributes.
- Computer Operating System: Restrict policies based on the operating system version (e.g., only apply to Windows 10 machines).
- Computer Membership: Target specific computer groups within Active Directory.
- User Account Type: Apply different policies to standard users versus domain administrators.
- Security Group Membership: This allows for nested group structures, enhancing flexibility and granularity.
For instance, a policy restricting access to specific software could be applied only to computers running Windows 10 Enterprise and members of a specific department’s security group. This layered approach ensures the policy’s impact is precisely controlled.
Comparison of Targeting Methods
Several methods exist for targeting users and computers. Choosing the right method depends on your organization’s structure and specific needs.
| Method | Advantages | Disadvantages |
|---|---|---|
| Security Groups | Easy to manage, flexible membership, allows for nested groups | Requires careful planning and maintenance, potential for group sprawl |
| Organizational Units | Provides a hierarchical structure, simplifies administration, inherits policies | Less flexible than security groups for dynamic membership changes |
| WMI Filters | Highly granular control, allows for complex filtering criteria | Requires advanced technical knowledge, can be complex to configure and maintain |
WMI filters offer the most granular control but require advanced technical skills. Security groups and OUs provide a balance between ease of use and precise targeting, making them suitable for most organizations. The best approach often involves a combination of these methods for optimal results.
Restricting Software Installation via Group Policy
Implementing software restriction policies is crucial for maintaining a secure and controlled computing environment, especially in organizations. Group Policy Objects (GPOs) provide a powerful mechanism to achieve this, allowing administrators to dictate which software can and cannot be installed on managed machines. This granular control minimizes the risk of unauthorized software installations, including potentially malicious or unlicensed applications.Software Installation Restrictions in GPOs offer a centralized approach to managing software deployment.
Instead of configuring each individual machine, administrators can create and deploy GPOs that apply to specific organizational units (OUs) or even individual users. This centralized management simplifies the process, ensuring consistency across the network. It’s particularly useful for preventing the installation of unlicensed software, a common violation of software licensing agreements that can expose the organization to legal and financial risks.
Preventing Unlicensed Software Installation
Group Policy provides several methods to prevent the installation of unlicensed software. One primary method leverages the Software Restriction Policies (SRP) feature. SRP allows administrators to define rules that control which executables can run on a computer. By creating rules that explicitly block the installation executables (.exe, .msi, etc.) of unlicensed software, you can effectively prevent their installation.
This can involve creating a list of disallowed executables or using hash-based rules to identify specific files. Another approach is to utilize AppLocker, a more advanced feature introduced in Windows 7 and later, which offers more fine-grained control over application execution. AppLocker allows for rules based on publisher, file path, and other attributes, providing a more robust and flexible way to manage application whitelisting and blacklisting.
Effective implementation requires careful planning and ongoing maintenance to ensure the rules remain relevant and up-to-date.
Software Restriction Methods Comparison
The following table compares different methods for restricting software installation using Group Policy, highlighting their applicability and limitations:
| Method | Description | Applicability | Limitations |
|---|---|---|---|
| Software Restriction Policies (SRP) | Allows administrators to create rules to block the execution of specific executables based on path, hash, or other criteria. | Windows XP and later. Relatively simple to implement for basic restrictions. | Can become complex to manage with many rules. Doesn’t inherently handle updates or variations of the same software. Less granular control compared to AppLocker. |
| AppLocker | Provides more granular control over application execution, allowing for rules based on publisher, file path, file hash, and other criteria. Supports both whitelisting and blacklisting. | Windows Vista and later. Offers more advanced features and flexibility. | More complex to configure and manage than SRP. Requires more in-depth understanding of application packaging and deployment. |
| Application Control (Third-Party Solutions) | Many third-party solutions offer advanced application control features beyond what is built into Windows, providing centralized management and detailed reporting. | Wide range of operating systems, often integrated with other security tools. | Requires purchasing and maintaining a third-party solution. May require additional integration efforts. |
| User Account Control (UAC) | While not strictly a software restriction method, UAC prompts users for administrator privileges before installing software, adding a layer of security. | Windows Vista and later. Simple to enable and provides basic protection. | Can be bypassed by users with administrator rights. Doesn’t prevent installation of software approved by the administrator. |
Managing Software Activation and Licensing through Group Policy: Restricting Disable Licensing Features Using Windows Group Policy Editor
Group Policy offers a powerful mechanism for managing software licenses across an organization, streamlining the activation process and enforcing compliance. This centralized approach can significantly reduce administrative overhead and improve security by preventing the use of unlicensed software. However, its implementation requires careful planning and understanding of its limitations.Group Policy’s capabilities extend to managing software activation keys, which are crucial for unlocking software functionalities.
Administrators can deploy activation keys through various Group Policy settings, ensuring consistent activation across multiple machines. Furthermore, Group Policy can be used to enforce software licensing agreements, ensuring that only authorized users and computers can access specific software. This is achieved by integrating licensing information with the software deployment process.
Software Activation Key Management with Group Policy, Restricting disable licensing features using windows group policy editor
While Group Policy doesn’t directly manage theactivation* process for all software (some applications use independent activation servers), it excels at deploying the necessary activation keys. This is often done via scripts or specialized software deployment tools integrated with Group Policy. For example, a script could be deployed to automatically enter the activation key during the software installation process. This ensures consistency and prevents manual key entry errors.
The success or failure of the activation process can be monitored through logging mechanisms, allowing administrators to identify and address any issues promptly. A successful implementation depends on the software vendor’s support for automated activation and the proper configuration of the deployment scripts.
Challenges in Centralized Software License Management
Centralizing software license management through Group Policy presents several challenges. One key challenge is the variety of licensing models used by different software vendors. Some vendors might require individual activation keys for each machine, while others might use volume licensing agreements. Managing these different models requires careful planning and potentially customized scripts or tools. Another challenge lies in tracking license usage and ensuring compliance.
Group Policy can enforce installation, but actively tracking whether a license is being used legitimately might require additional tools and monitoring. Finally, maintaining up-to-date license information within the Group Policy infrastructure is crucial and requires careful processes to prevent errors and ensure accuracy. Changes to licensing agreements or the addition of new software necessitates regular updates to the GPOs.
Enforcing Software Licensing Compliance with Group Policy
Enforcing compliance with software licensing terms is achievable through a combination of Group Policy settings and software deployment strategies. This can involve restricting installation of unlicensed software through Software Restriction Policies (SRP), which we’ve previously covered. Additionally, Group Policy can be used to deploy only authorized versions of software, preventing the use of cracked or unauthorized copies. Regular audits, using tools that check license compliance against the deployed software, are vital to identify any discrepancies and ensure ongoing compliance.
For example, a regular audit might compare the number of installed licenses of a specific application against the number of licenses purchased. Any discrepancies would trigger an investigation to ensure the software is being used in accordance with the license agreement. Finally, clear communication of the organization’s software licensing policy to all users is essential to foster compliance and minimize unintentional violations.
Implementing Auditing and Monitoring of Software Usage
Keeping tabs on software usage within your organization is crucial not only for license compliance but also for understanding software adoption and identifying potential security risks. Effective monitoring allows you to proactively address potential issues before they escalate into costly licensing violations or security breaches. This involves strategically leveraging Group Policy’s reporting capabilities to track software installation and activation events.Implementing a robust software usage auditing system using Group Policy offers a centralized and efficient method for tracking software deployments and license utilization across your network.
By configuring specific Group Policy settings, you can generate detailed logs that provide valuable insights into which software is installed on which machines, when it was installed, and even activation details where applicable. This data forms the basis for accurate license management and helps you identify potential compliance gaps.
Software Installation and Activation Event Logging
Configuring Group Policy to log software installation and activation events involves modifying the relevant Group Policy settings to enable detailed logging. This usually involves enabling specific event logging within the Windows Event Viewer. While the exact steps might vary slightly depending on your Windows version, the general approach remains consistent. You would navigate to the appropriate Group Policy Management Console (GPMC.MSC), locate the relevant GPO for your target computers, and then edit the settings under “Computer Configuration” -> “Policies” -> “Administrative Templates” -> “Windows Components” -> “Windows Installer”.
Within this section, you’ll find options to enable detailed logging of installation and uninstallation events. Similarly, you might need to adjust settings related to software licensing and activation within the relevant components of Group Policy. For example, you could enable logging of activation attempts and successes. This detailed logging provides a comprehensive audit trail of software changes on managed machines.
Analyzing Audit Logs for License Compliance
Analyzing the generated audit logs requires a systematic approach. The logs will contain a wealth of information, but effectively extracting meaningful data requires careful planning. One approach is to use the Windows Event Viewer to filter events based on specific criteria such as software name, installation date, or user. You can then export these filtered logs into a format suitable for analysis using tools like Microsoft Excel or dedicated log analysis software.
By comparing the logged software installations with your purchased licenses, you can identify potential discrepancies. For example, if your logs show 50 installations of “Software A” but you only have 25 licenses, you have a clear indication of a potential licensing violation. Another effective method involves scripting to automate the process of extracting and analyzing data from the event logs.
This can involve using PowerShell to query the event logs and generate reports summarizing software usage and license compliance. This automated approach enhances efficiency and allows for regular checks.
Best Practices for Audit Log Management
Effective audit log management goes beyond simply collecting data; it’s about establishing a robust system for storing, accessing, and analyzing that data. Regularly reviewing and analyzing logs is essential to proactively identify potential licensing issues. Implement a process for regularly reviewing audit logs, perhaps on a weekly or monthly basis, depending on the size of your organization and the frequency of software deployments.
Also, consider implementing retention policies to manage the size of your audit logs. Old logs can consume significant storage space and make it more challenging to find relevant information. Finally, ensure that your audit logs are secured appropriately to prevent unauthorized access or modification. This involves implementing access control lists (ACLs) and regular security audits of your log management system.
Addressing Common Challenges and Troubleshooting
Implementing software restriction policies using Group Policy can be powerful, but it’s not without its potential pitfalls. Successfully managing software licensing and restrictions requires careful planning and a proactive approach to troubleshooting. Understanding common issues and their solutions is crucial for maintaining a secure and compliant environment.Troubleshooting software restriction policies often involves deciphering cryptic error messages and navigating the complexities of GPO interactions.
This section will cover some of the most frequently encountered problems and offer practical solutions to get your policies working effectively.
Common Errors Encountered During Software Restriction Policy Configuration
Incorrectly configured software restriction policies can lead to various problems, ranging from unexpected application blocks to complete policy failures. A common error is specifying incorrect paths or file hashes, leading to unintended consequences. Another frequent mistake is applying policies at the wrong organizational unit (OU) level within the Active Directory, resulting in the policy either affecting too many or too few users and computers.
Furthermore, poorly defined rules can create conflicts, causing unpredictable behavior. For example, a rule allowing a specific application might be overridden by a more restrictive rule applied later. Finally, insufficient auditing can make diagnosing problems difficult, as it’s hard to understand what is actually happening on the client machines.
Resolving Conflicts Between Conflicting GPOs Affecting Software Licensing
Multiple GPOs targeting the same users or computers can lead to policy conflicts. These conflicts frequently arise when different administrative teams manage overlapping policies, creating inconsistencies in software license enforcement. To resolve this, you need to carefully analyze the GPOs affecting the target computers. Use the Group Policy Management Console (GPMC.MSC) to determine the order of precedence for applied GPOs.
The GPOs applied last have higher precedence and will override conflicting settings in GPOs applied earlier. Reordering the GPOs, using the GPMC, allows you to prioritize the desired policy. Another approach involves using the “Link Enabled” setting within a GPO to enable or disable the GPO without deleting it, providing a more controlled method of managing policy conflicts.
Finally, careful design of GPOs, using well-defined scopes and filters, is critical to prevent future conflicts. For example, instead of having one broadly applied GPO, create more specific GPOs targeting specific user groups or organizational units.
So, I was just wrestling with restricting disable licensing features using Windows Group Policy Editor – a real pain sometimes! It got me thinking about how much simpler app development is becoming, especially with the advancements discussed in this great article on domino app dev the low code and pro code future. Maybe I should explore low-code solutions to streamline my admin tasks! Anyway, back to battling those pesky Group Policy settings…
Troubleshooting Steps for Resolving Issues with Software License Enforcement
Before diving into specific troubleshooting, ensure you have sufficient logging and auditing enabled within your Group Policy settings. This will provide valuable insights into policy application and enforcement.
- Verify Policy Application: Use the Resultant Set of Policy (RSoP) tool (rsop.msc) to confirm that the intended software restriction policies are applied correctly to the target computers. RSoP displays the effective settings after all GPOs have been processed, highlighting any conflicts.
- Check for Policy Conflicts: Identify and resolve any conflicts between multiple GPOs that might be affecting software licensing. Use the GPMC to examine the order of applied GPOs and adjust accordingly. The higher the GPO in the list, the higher its precedence.
- Review Software Restriction Rules: Carefully examine the rules defined within your software restriction policies to ensure they accurately reflect your licensing requirements. Check for typos, incorrect paths, and overly broad or restrictive rules.
- Examine Event Logs: Check the Windows Event Logs (especially the Application and System logs) on the client computers for errors related to software restriction policies. These logs often provide detailed information about policy application failures and conflicts.
- Test with a Single Computer: To isolate the problem, test the policy on a single computer outside of a production environment. This helps in ruling out network or domain-wide issues.
- Ensure Proper Group Membership: Verify that the users and computers are correctly assigned to the security groups targeted by the software restriction policies.
- Restart the Computer: A simple restart of the affected computer can often resolve temporary glitches or inconsistencies in policy application.
- Update Group Policy: Use the `gpupdate /force` command on the client computer to force a refresh of the Group Policy settings.
Security Considerations and Best Practices
Improperly configured software restriction policies can significantly weaken your organization’s security posture, leaving it vulnerable to malware and unauthorized software installations. Securing Group Policy settings related to software licensing requires a multi-layered approach encompassing careful planning, robust implementation, and ongoing monitoring. This section details the security implications of misconfigurations and Artikels best practices to mitigate these risks.The consequences of poorly implemented software restriction policies can range from minor inconveniences to major security breaches.
For example, if a policy is too restrictive, it might block legitimate software needed for productivity, leading to workflow disruptions. Conversely, a policy that is too permissive could allow malicious software to execute, potentially compromising sensitive data or systems. Failing to properly secure Group Policy settings exposes your organization to unauthorized software installations, license key theft, and potential legal ramifications related to software compliance.
Security Implications of Improperly Configured Software Restriction Policies
A poorly configured software restriction policy can inadvertently grant access to unauthorized applications or prevent legitimate applications from running. This can result in increased vulnerability to malware infections, data breaches, and system instability. For example, a policy that fails to block executables from untrusted sources could allow malicious software to be installed and executed, potentially leading to significant damage.
Conversely, a policy that is too restrictive could prevent employees from using essential applications, impacting productivity and potentially leading to workarounds that introduce new security risks. Careful planning and testing are crucial to ensure the policy effectively balances security and usability.
Best Practices for Securing Group Policy Settings Related to Software Licensing
Implementing robust security measures around Group Policy settings is paramount to protect software licenses and prevent unauthorized access. This includes restricting administrative access to Group Policy Management Console (GPMC) to only authorized personnel, using strong passwords and multi-factor authentication, and regularly auditing changes made to GPOs. Regularly reviewing and updating the software restriction policies to reflect the latest threats and security best practices is also essential.
Implementing version control for GPOs allows for easy rollback in case of accidental or malicious changes.
Strategies for Preventing Unauthorized Modifications to Group Policy Objects
Preventing unauthorized modifications to Group Policy Objects (GPOs) is critical to maintaining a secure and stable computing environment. This can be achieved through a combination of technical and administrative controls. Technical controls include implementing access control lists (ACLs) on GPOs to restrict modification permissions to authorized users or groups, utilizing Group Policy Preferences to manage settings instead of directly modifying registry keys, and employing auditing mechanisms to track changes made to GPOs.
Administrative controls involve establishing clear procedures for making changes to GPOs, requiring multiple approvals for significant changes, and conducting regular audits to identify and address unauthorized modifications. Implementing a change management process ensures that all modifications are documented, approved, and tested before being deployed to production environments. This minimizes the risk of accidental or malicious changes impacting the organization’s security posture.
Alternative Methods for Software License Management
Managing software licenses effectively is crucial for compliance and cost control. While Group Policy offers a robust solution within a Windows environment, it’s not the only game in town. Several alternative methods exist, each with its own strengths and weaknesses, making the choice dependent on specific organizational needs and infrastructure. This section explores these alternatives and provides a framework for selecting the best approach.
Group Policy excels in managing software licenses within a homogeneous Windows domain, offering centralized control and ease of deployment for policies. However, it lacks the flexibility to manage licenses across diverse operating systems or cloud environments. Other methods provide broader compatibility and more advanced features, but may require more complex setup and management.
Comparison of Group Policy and Alternative License Management Methods
The following table compares Group Policy with other common software license management approaches. This comparison highlights key differences in functionality, scalability, and cost, helping to clarify the best fit for various scenarios.
| Method | Strengths | Weaknesses | Best Suited For |
|---|---|---|---|
| Group Policy | Centralized management, easy deployment within Windows domains, cost-effective for simple deployments. | Limited cross-platform support, complex for large, heterogeneous environments, less granular control than dedicated solutions. | Small to medium-sized organizations with primarily Windows-based infrastructure and simple licensing needs. |
| Dedicated License Management Software | Comprehensive license tracking, automated license discovery and reconciliation, cross-platform compatibility, advanced reporting and analytics. | Higher initial cost, more complex setup and administration, requires dedicated expertise. | Large organizations with complex licensing needs, multiple operating systems, and a need for detailed reporting and analysis. |
| Spreadsheet-Based Tracking | Simple, low-cost, readily available. | Manual, prone to errors, lacks automation, difficult to scale. | Very small organizations with minimal software licenses. |
| Cloud-Based License Management Services | Scalability, accessibility, automated license management, often integrated with other cloud services. | Dependency on internet connectivity, potential security concerns related to data storage in the cloud, recurring subscription costs. | Organizations utilizing cloud-based infrastructure and services, or those seeking scalability and remote management capabilities. |
Examples of Alternative Software License Management Tools
Several commercial and open-source tools provide advanced license management capabilities beyond what Group Policy offers. These tools automate many aspects of license tracking, ensuring compliance and optimizing software investments.
- ManageEngine License Manager Plus: A comprehensive solution offering automated license discovery, usage tracking, and reporting. It supports a wide range of software vendors and operating systems.
- Snow License Manager: A robust solution known for its extensive features, including license optimization, cost analysis, and compliance reporting. It is often favored by large enterprises.
- Flexera Software License Manager: This tool provides deep insights into software usage, helping organizations optimize their software portfolios and reduce licensing costs. It integrates with various IT systems.
- OpenLM: An open-source license management solution suitable for academic and research institutions, or organizations looking for a cost-effective alternative. It focuses on high-performance computing licenses.
Decision-Making Flowchart for Selecting a License Management Approach
The choice of license management method should depend on factors such as organization size, IT infrastructure, budget, and licensing complexity. The following flowchart Artikels a decision-making process to guide the selection.
(Note: A visual flowchart would be included here, depicting a decision tree based on the criteria mentioned above. The tree would branch out based on the answers to questions like: Organization size? Primarily Windows environment? Budget constraints? Need for advanced reporting and analytics?
The final branches would lead to recommendations for Group Policy, dedicated software, spreadsheet tracking, or cloud-based services.)
Ending Remarks
So, there you have it! Taming the beast that is software license management with Windows Group Policy Editor is totally achievable. By carefully crafting your GPOs, targeting the right users, and implementing a solid monitoring system, you can gain complete control over your software licenses, improve security, and ultimately, save time and resources. Remember, this isn’t a one-time setup; it’s an ongoing process that requires regular review and adjustments.
Stay vigilant, stay informed, and keep those licenses in check!
User Queries
What happens if I accidentally delete a crucial GPO setting?
Don’t panic! Group Policy usually has backups. Check your domain controller’s system state backups. If you can’t restore from a backup, you may need to manually recreate the GPO settings, potentially requiring a thorough understanding of your previous configuration.
Can I use GPO to manage licenses for all software, or are there exceptions?
While GPOs are incredibly powerful, some software may use licensing mechanisms that aren’t easily managed through Group Policy. You might need a combination of GPOs and other license management tools for comprehensive control.
How often should I review and update my GPOs related to software licensing?
Regular reviews are crucial. At a minimum, schedule monthly checks to ensure your policies are still relevant and effective. More frequent checks might be needed if you’re experiencing rapid changes in software usage or deployments.
