Safeguarding the Digital Realm Application Security Testings Rise
Safeguarding the digital realm the rising importance of application security testing – Safeguarding the digital realm: the rising importance of application security testing. In today’s hyper-connected world, where digital services are the lifeblood of businesses and individuals alike, the need for robust application security is paramount. From sophisticated AI-powered attacks to the ever-expanding Internet of Things (IoT), the threat landscape is constantly evolving, demanding a proactive and comprehensive approach to securing our applications.
This post delves into the crucial role of application security testing in mitigating these risks and building a more secure digital future.
We’ll explore the various types of application security testing, from static analysis to penetration testing, and discuss how to integrate these practices effectively into the software development lifecycle (SDLC). We’ll also look at the importance of fostering a security-conscious culture within development teams and the role of emerging technologies like AI in enhancing our defenses. Get ready to dive into the fascinating world of application security and discover how you can play your part in protecting the digital realm!
The Evolving Landscape of Application Security Threats
The digital world is a constantly shifting landscape, and with it, the threats to application security evolve at an alarming pace. What was a cutting-edge attack vector last year might be commonplace today, highlighting the need for continuous vigilance and adaptation in our security strategies. Understanding the current threat landscape is paramount to building robust and resilient applications.The most prevalent application security vulnerabilities in 2024 continue to be a mix of well-known weaknesses and newly emerging exploits.
While classic vulnerabilities like SQL injection and cross-site scripting (XSS) remain prevalent, their sophistication and the methods used to exploit them are constantly evolving. Furthermore, the rise of new technologies introduces a whole new set of vulnerabilities that require unique approaches to mitigation.
Prevalent Application Security Vulnerabilities in 2024
The OWASP Top 10 continues to provide a valuable framework for understanding the most critical risks. However, the specific vulnerabilities and their impact vary based on the application’s context and technology stack. For example, while injection flaws remain a significant threat, insecure design principles leading to vulnerabilities like broken access control are equally, if not more, damaging in their potential impact.
Improper input validation, insufficient authentication, and the lack of secure session management also remain persistent issues. The complexity of modern applications, with their interconnected components and reliance on third-party libraries, further exacerbates the challenge. A single vulnerability in a seemingly minor component can have cascading effects across the entire system.
Impact of Emerging Technologies on Application Security Risks
The integration of Artificial Intelligence (AI) and the Internet of Things (IoT) presents both opportunities and significant challenges for application security. AI-powered applications, while offering incredible benefits, can be vulnerable to adversarial attacks, including data poisoning and model manipulation. Malicious actors could exploit vulnerabilities in the AI model itself or in the data used to train it, leading to compromised results or unexpected behaviors.
Similarly, IoT devices, with their often-limited processing power and security features, represent a large attack surface. Their inherent connectivity makes them susceptible to various attacks, including denial-of-service (DoS) and data breaches. The sheer number of IoT devices further compounds the challenge, creating a complex network of potential entry points for malicious actors. Consider the potential impact of a compromised smart home system, granting attackers access to personal data and potentially even physical control of the home.
Traditional vs. Modern Application Security Threats
Traditional application security threats primarily focused on vulnerabilities within the application code itself. These included buffer overflows, SQL injection, and cross-site scripting. Modern threats, however, are far more sophisticated and often involve exploiting weaknesses in the entire application ecosystem, including third-party libraries, cloud infrastructure, and APIs. The rise of microservices architectures, while offering benefits in terms of scalability and agility, also introduces new complexities in terms of security management.
Each microservice represents a potential point of failure, requiring careful attention to secure communication and data protection across the entire distributed system. Moreover, the increasing reliance on cloud-based services shifts the security responsibility partially to the cloud provider, but also introduces new attack vectors related to cloud misconfigurations and data breaches within the cloud environment.
Financial and Reputational Consequences of Application Security Breaches
The financial and reputational consequences of application security breaches can be devastating. Data breaches can lead to significant financial losses due to regulatory fines, legal fees, remediation costs, and loss of customer trust. The cost of a data breach can easily run into millions, or even billions, of dollars, depending on the scale and sensitivity of the data compromised.
Beyond the financial implications, a security breach can severely damage an organization’s reputation, leading to loss of customers, investors, and employee morale. The negative publicity surrounding a breach can have long-lasting effects, making it difficult for the organization to regain public trust. For example, the Equifax data breach in 2017 resulted in billions of dollars in losses and a significant decline in the company’s stock price.
The reputational damage sustained by Equifax continues to this day, serving as a stark reminder of the severe consequences of inadequate application security.
The Importance of Proactive Application Security Testing
Integrating application security testing (AST) into the software development lifecycle (SDLC) is no longer a luxury; it’s a necessity. In today’s threat landscape, reactive security measures simply aren’t enough. Proactive AST allows organizations to identify and mitigate vulnerabilities early in the development process, significantly reducing the cost and risk associated with security breaches. This shift towards a “secure by design” approach is crucial for building robust and resilient applications.Proactive AST offers several key benefits.
Early detection of vulnerabilities minimizes the cost of remediation, as fixing bugs in the early stages is far cheaper than addressing them after deployment. It also improves the overall quality of the software, leading to a more reliable and user-friendly product. Furthermore, proactive AST helps organizations meet compliance requirements and build trust with customers, demonstrating a commitment to data security.
Finally, it reduces the likelihood of significant financial and reputational damage resulting from a security breach.
Application Security Testing Methodologies
Several different methodologies exist for performing AST, each with its own strengths and weaknesses. Choosing the right mix of approaches is crucial for comprehensive coverage.Static Application Security Testing (SAST) analyzes the source code without actually executing the application. This allows for the identification of vulnerabilities early in the development process, even before the application is built. Tools like SonarQube and Checkmarx are examples of popular SAST solutions.
They are effective at finding coding flaws but may miss vulnerabilities that only emerge during runtime.Dynamic Application Security Testing (DAST) involves testing the application while it’s running. This allows for the detection of vulnerabilities that might be missed by SAST, such as vulnerabilities related to the application’s interaction with external systems or the web server. OpenVAS and Burp Suite are examples of DAST tools.
While DAST is great at identifying runtime vulnerabilities, it might not pinpoint the root cause within the code itself.Interactive Application Security Testing (IAST) combines the benefits of both SAST and DAST. It involves instrumenting the application to monitor its behavior during runtime and correlate runtime activity with the source code. This allows for the precise identification of vulnerabilities and their location within the code.
Contrast Security and AppDetective are examples of IAST solutions. IAST offers a higher level of accuracy but often requires more integration effort.
Selecting Appropriate Application Security Testing Tools
Selecting the right AST tools depends heavily on the specific needs of the project. Factors to consider include the type of application (web, mobile, desktop), the programming languages used, the development methodology (Agile, Waterfall), the budget, and the level of expertise within the development team. A thorough assessment of these factors is crucial to ensure that the chosen tools are effective and efficient.
For instance, a small team working on a simple web application might find open-source tools sufficient, while a large enterprise developing a complex system might require more sophisticated commercial solutions with integrated reporting and vulnerability management capabilities. Prioritizing tools that integrate seamlessly with existing development workflows also minimizes disruption.
Application Security Testing Strategy for an E-commerce Platform
Consider a large-scale e-commerce platform. A comprehensive AST strategy would involve a multi-phased approach incorporating various testing methodologies. The following table Artikels a hypothetical strategy:
| Testing Phase | Tools | Responsible Team | Frequency |
|---|---|---|---|
| Code Review | SonarQube (SAST), Manual Code Review | Development Team, Security Engineer | Continuously during development |
| Unit Testing | JUnit, pytest (with security-focused test cases) | Development Team | Continuously during development |
| Integration Testing | OWASP ZAP (DAST), Manual Penetration Testing | QA Team, Security Engineer | Before each release |
| System Testing | Burp Suite (DAST), IAST (e.g., Contrast Security) | QA Team, Security Engineer | Before each major release |
Key Techniques in Application Security Testing
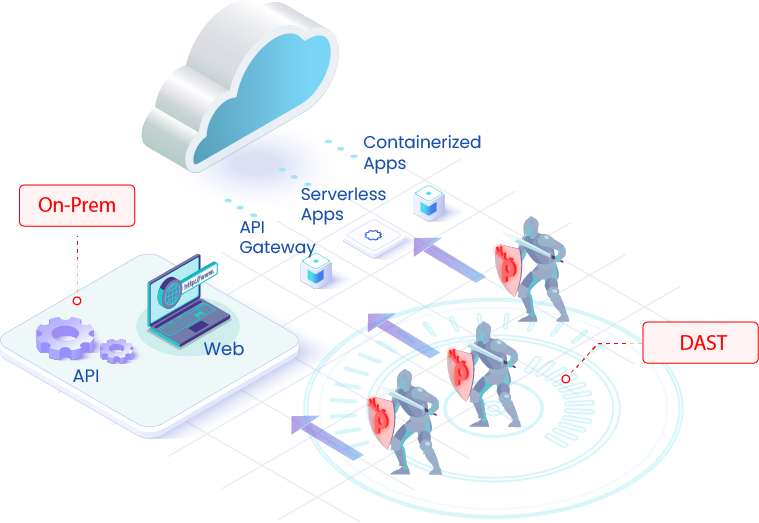
Application security testing (AST) is crucial for identifying and mitigating vulnerabilities before they can be exploited. A robust AST strategy employs a combination of techniques, each playing a vital role in ensuring the security of applications. Understanding these techniques and their strengths and weaknesses is paramount for building secure software.
Common Vulnerabilities and Mitigation Strategies
Several common vulnerabilities plague applications, each requiring a specific mitigation strategy. SQL injection, for example, allows attackers to manipulate database queries, potentially granting unauthorized access to sensitive data. This can be mitigated through parameterized queries or input validation, ensuring that user-supplied data is treated as data, not as executable code. Cross-site scripting (XSS) vulnerabilities allow attackers to inject malicious scripts into websites, stealing user information or redirecting users to phishing sites.
Mitigation involves encoding user input, using output encoding to sanitize data displayed on the page, and implementing a robust content security policy (CSP). Another example is insecure direct object references (IDORs), where attackers can manipulate URLs to access unauthorized resources. Proper authorization checks and the use of unique identifiers that are not easily guessable are key to mitigating IDORs.
Finally, insecure authentication mechanisms can be exploited by attackers using brute-force attacks or credential stuffing. Strong password policies, multi-factor authentication (MFA), and rate limiting can significantly improve security.
Automated versus Manual Application Security Testing, Safeguarding the digital realm the rising importance of application security testing
Automated and manual application security testing both play critical roles, offering complementary strengths. Automated testing, using tools like static and dynamic application security testing (SAST and DAST) tools, provides efficient and scalable coverage, particularly for identifying common vulnerabilities. Automated tools can quickly scan large codebases, pinpointing potential weaknesses that might be missed in manual reviews. However, automated tools can produce false positives, requiring manual verification.
Manual testing, such as penetration testing, provides a more in-depth analysis, focusing on exploiting vulnerabilities and assessing the impact of successful attacks. While manual testing is more time-consuming and expensive, it is invaluable for uncovering sophisticated attacks that automated tools may miss. The optimal approach typically involves a combination of both, leveraging the speed and scalability of automated tools for initial screening and the depth of manual testing for confirmation and further investigation.
Static and Dynamic Application Security Testing
Static Application Security Testing (SAST) analyzes the application’s source code without executing it. This allows SAST to identify vulnerabilities early in the development lifecycle, often before the code is even deployed. SAST tools can detect vulnerabilities like buffer overflows, SQL injection flaws, and insecure use of cryptographic libraries. Conversely, Dynamic Application Security Testing (DAST) analyzes the application while it is running, simulating real-world attacks to identify vulnerabilities in the runtime environment.
DAST tools can find vulnerabilities like cross-site scripting (XSS) and cross-site request forgery (CSRF) that might not be apparent during static analysis. While SAST is better at finding vulnerabilities in the code itself, DAST is more effective at finding vulnerabilities that emerge only when the application is running. Combining both SAST and DAST provides a more comprehensive security assessment.
Penetration Testing in Identifying and Remediating Security Weaknesses
Penetration testing simulates real-world attacks to identify vulnerabilities in an application’s security posture. This involves attempting to exploit weaknesses in the application, its infrastructure, and its surrounding environment. The process typically includes:
- Planning and scoping: Defining the target system, the types of tests to be performed, and the rules of engagement.
- Information gathering: Gathering information about the target system to identify potential vulnerabilities.
- Vulnerability analysis: Identifying and assessing the potential impact of identified vulnerabilities.
- Exploitation: Attempting to exploit vulnerabilities to demonstrate their impact.
- Reporting: Documenting the findings, including the identified vulnerabilities, their severity, and recommended remediation steps.
- Remediation: Implementing the recommended fixes to address the identified vulnerabilities.
Penetration testing provides valuable insights into an application’s security weaknesses, enabling developers to proactively address potential threats and improve the overall security posture. A well-executed penetration test can reveal vulnerabilities that might otherwise go undetected, preventing costly breaches and data loss.
Building a Secure Development Culture: Safeguarding The Digital Realm The Rising Importance Of Application Security Testing
Creating a truly secure application isn’t just about the tools and techniques; it’s about fostering a security-conscious mindset within the entire development team. A culture of security, where developers proactively consider security implications throughout the software development lifecycle (SDLC), is paramount to building robust and resilient applications. This involves a multifaceted approach encompassing training, collaboration, and a fundamental shift in how security is integrated into the development process.Building a secure development culture requires a proactive and integrated approach.
It’s not a one-time fix, but rather an ongoing process of education, collaboration, and continuous improvement. This involves embedding security practices into every stage of the software development lifecycle, from initial design to deployment and maintenance. Without this holistic view, even the most sophisticated security testing tools will only offer limited protection.
Security Training and Awareness Programs for Developers
Effective security training goes beyond simply checking a box. It needs to be engaging, relevant, and tailored to the specific skills and roles of the developers. The training should not just focus on theoretical concepts but should include hands-on exercises and real-world examples of vulnerabilities and exploits. Regular refresher courses and updates on emerging threats are crucial to maintain a high level of security awareness.
For example, a training program might include modules on common vulnerabilities like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF), as well as secure coding practices for specific programming languages. The goal is to empower developers to write secure code from the outset, rather than relying solely on post-development security checks.
Collaboration Between Development and Security Teams
Effective communication and collaboration between development and security teams are vital for a successful security program. Security shouldn’t be seen as a separate, post-development function; instead, it should be integrated throughout the SDLC. This requires establishing clear communication channels and processes, such as regular security reviews, code audits, and vulnerability assessments. A collaborative approach ensures that security considerations are addressed early in the development process, preventing vulnerabilities from being introduced in the first place.
For example, a joint security review process involving developers and security experts can identify and address potential vulnerabilities before they become major issues. This collaborative approach also fosters a shared sense of responsibility for security, making it everyone’s concern rather than solely the responsibility of the security team.
A Hypothetical Training Module for Developers on Secure Coding Practices
This module aims to provide developers with practical, hands-on experience in writing secure code. The training emphasizes learning by doing, focusing on common vulnerabilities and mitigation techniques.
The following points highlight key areas covered in the module:
- Input Validation and Sanitization: Understanding the importance of validating and sanitizing all user inputs to prevent injection attacks (SQL injection, command injection, cross-site scripting).
- Authentication and Authorization: Implementing secure authentication mechanisms (e.g., multi-factor authentication) and authorization controls to protect sensitive data and functionality.
- Session Management: Understanding the risks associated with insecure session management and implementing secure session handling techniques to prevent session hijacking.
- Data Protection: Implementing appropriate data protection measures, such as encryption and data masking, to protect sensitive data both in transit and at rest.
- Error Handling: Properly handling errors and exceptions to prevent information leakage and unexpected behavior that could be exploited by attackers.
- Secure Coding Practices for Specific Languages: Tailored training on secure coding practices for the specific programming languages used by the development team (e.g., Java, Python, C#).
- Security Testing and Vulnerability Scanning: Introducing developers to basic security testing techniques and the use of vulnerability scanners to identify and address potential security flaws.
The Future of Application Security Testing

The landscape of application security is constantly evolving, driven by the increasing complexity of software, the rise of cloud-native architectures, and the sophistication of cyberattacks. The future of application security testing will be defined by a shift towards more automated, intelligent, and integrated approaches, aiming to keep pace with these rapid changes. This means moving beyond traditional penetration testing and embracing a more holistic and proactive security posture.
Emerging Trends in Application Security Testing
Several key trends are shaping the future of application security testing. These trends reflect a move towards more efficient, effective, and adaptable security practices. The adoption of these trends will be crucial for organizations to effectively manage the growing threat landscape.
- Shift-Left Security: Integrating security testing earlier in the software development lifecycle (SDLC), even at the design and coding phases, rather than as an afterthought.
- DevSecOps: Automating security testing and integrating it seamlessly into DevOps pipelines for continuous security validation.
- Cloud-Native Security: Addressing the unique security challenges posed by cloud-based applications, including serverless functions and microservices.
- API Security Testing: Focusing on the security of APIs, which are increasingly becoming the attack vector of choice for malicious actors.
- Software Composition Analysis (SCA): Identifying and mitigating vulnerabilities in open-source and third-party components used in applications.
Challenges in Securing Complex Applications
Securing increasingly complex applications presents significant challenges. The sheer scale and interconnectedness of modern software systems make comprehensive security testing difficult and time-consuming.
- Microservices Architecture: The decentralized nature of microservices makes it challenging to maintain a holistic view of the application’s security posture.
- Third-Party Dependencies: Reliance on numerous third-party libraries and components introduces significant security risks that are difficult to manage.
- Legacy Systems: Integrating security testing into legacy systems often requires significant effort and may disrupt existing workflows.
- Rapid Development Cycles: The pressure to release software quickly can compromise security testing efforts if not carefully managed.
- Skills Gap: A shortage of skilled application security professionals makes it challenging for organizations to implement robust security practices.
The Role of AI and Machine Learning in Application Security Testing
AI and machine learning (ML) are poised to revolutionize application security testing. These technologies can automate many aspects of testing, improve accuracy, and accelerate the identification of vulnerabilities.
AI and ML algorithms can analyze vast amounts of code and data to identify patterns and anomalies indicative of vulnerabilities. This allows for more efficient and effective testing, especially in large and complex applications. Furthermore, ML can be used to prioritize vulnerabilities based on their severity and potential impact, allowing security teams to focus their efforts on the most critical issues.
For example, AI-powered tools can analyze code for common vulnerabilities and misconfigurations, significantly reducing the time and effort required for manual code reviews.
A Hypothetical Future Scenario Illustrating Advancements in Application Security Testing
Imagine a future where a developer commits code to a repository. An AI-powered application security testing platform automatically analyzes the code in real-time, identifying potential vulnerabilities before they are even deployed. The platform not only flags the vulnerabilities but also suggests automated remediation steps, providing the developer with the necessary information to fix the issues instantly. The platform continuously monitors the application in production, leveraging machine learning to detect emerging threats and anomalies, proactively alerting the security team to any potential breaches. This automated and integrated approach ensures continuous security validation throughout the entire software lifecycle, significantly reducing the risk of security breaches. This system also leverages blockchain technology to provide immutable records of security testing and remediation, fostering trust and transparency across the development lifecycle.
Final Thoughts
Ultimately, safeguarding the digital realm through robust application security testing isn’t just about preventing breaches; it’s about building trust, protecting reputations, and ensuring the continued smooth operation of our digital lives. By embracing proactive security measures, integrating security into every stage of development, and fostering a culture of collaboration between developers and security experts, we can significantly reduce our vulnerability to cyber threats.
The journey towards a more secure digital future requires continuous vigilance and adaptation, but the rewards – a safer and more reliable online experience – are well worth the effort. Let’s keep pushing the boundaries of application security and work together to build a stronger, more resilient digital world.
Detailed FAQs
What are the biggest risks of neglecting application security testing?
Ignoring application security testing significantly increases your risk of data breaches, financial losses, reputational damage, legal liabilities, and loss of customer trust. It can also lead to costly remediation efforts later in the development cycle.
How much does application security testing cost?
The cost varies greatly depending on the size and complexity of your application, the chosen testing methodologies, and the tools employed. It’s an investment that needs to be carefully planned and budgeted for, but the potential savings from preventing breaches far outweigh the initial cost.
Can I perform application security testing myself, or do I need external experts?
While some basic security checks can be done in-house, complex applications often benefit from the expertise of specialized security testing firms. They bring in-depth knowledge, advanced tools, and unbiased perspectives to identify vulnerabilities you might miss.
How often should I conduct application security testing?
The frequency depends on your risk tolerance and the nature of your application. Regular testing, integrated throughout the SDLC (e.g., during development, before release, and periodically after deployment), is crucial for maintaining a strong security posture.