
Schools Are Lucrative Targets for Cybercriminals
Schools are lucrative targets for cybercriminals. Think about it – sensitive student data, financial records, and often, outdated technology. It’s a digital goldmine for malicious actors looking to exploit vulnerabilities. This isn’t just a theoretical threat; it’s a growing reality with real-world consequences for schools and their communities. We’ll delve into the reasons why schools are so vulnerable, the types of attacks they face, and most importantly, how they can bolster their defenses.
From phishing scams targeting unsuspecting staff to sophisticated ransomware attacks crippling entire networks, the landscape of cyber threats against schools is constantly evolving. Understanding these threats is the first step in mitigating the risk and protecting our students’ data and the integrity of our educational institutions. We’ll explore real-world examples, practical strategies, and the crucial role of human awareness in this digital battleground.
Vulnerabilities in School Systems
Schools, with their increasingly interconnected networks and reliance on technology, represent a tempting target for cybercriminals. The sensitive data they hold – student records, financial information, and research data – makes them a lucrative prize. While many schools are implementing security measures, vulnerabilities remain, leaving them susceptible to various attacks. Understanding these weaknesses is crucial for effective mitigation.
Common Security Weaknesses in School Network Infrastructure
A robust network infrastructure is the foundation of a secure school system. However, many schools struggle with inadequate network segmentation, leaving critical systems vulnerable to lateral movement of attackers. Weak or default passwords, insufficient firewall protection, and a lack of intrusion detection and prevention systems are common shortcomings. Furthermore, many schools lack robust monitoring and logging capabilities, hindering the detection and response to security incidents.
Physical security of network equipment is often overlooked, creating opportunities for unauthorized access and tampering.
Software Vulnerabilities in Educational Settings
Outdated or unpatched software presents a significant vulnerability. Educational institutions often rely on legacy systems, which may lack essential security updates and patches, leaving them exposed to known exploits. The use of unapproved or unlicensed software introduces additional risks, as these applications may contain vulnerabilities or malware. Poor software configuration, such as default settings, can also create entry points for attackers.
For example, a failure to update Adobe Flash Player before its official end-of-life left many schools vulnerable to exploits. Similarly, outdated operating systems on classroom computers and servers create pathways for various attacks.
Outdated Technology and Increased Risk
The use of outdated technology significantly increases the risk of cyberattacks. Older hardware and software often lack the security features found in their modern counterparts. These systems may not support the latest security protocols, making them easier to compromise. Moreover, maintaining outdated systems can be costly and resource-intensive, diverting funds from essential security upgrades. The lack of vendor support for older technologies further exacerbates the problem, making it difficult to address vulnerabilities as they are discovered.
This is particularly true for specialized educational software that may not receive regular updates.
Comparison of Security Strengths and Weaknesses Across Different School System Types
| System Type | Infrastructure Weakness | Software Vulnerability | Mitigation Strategy |
|---|---|---|---|
| Large Public School District | Limited budget for security upgrades, complex network infrastructure | Outdated operating systems across numerous devices, reliance on legacy software | Prioritize security updates based on risk assessment, implement centralized patch management, invest in security awareness training |
| Small Private School | Lack of dedicated IT staff, reliance on external IT support | Unpatched software, weak password policies | Employ a managed security service provider (MSSP), implement multi-factor authentication, regular security audits |
| Large Private School | Over-reliance on proprietary systems, lack of network segmentation | Unpatched third-party applications, inadequate data backup and recovery | Regular penetration testing, robust data backup and recovery plan, employee training on cybersecurity best practices |
| Small Public School | Inadequate funding for cybersecurity, limited technical expertise | Outdated antivirus software, lack of endpoint protection | Collaborate with other schools for shared resources, leverage free or low-cost security tools, participate in cybersecurity awareness programs |
Types of Cyberattacks Targeting Schools
Schools, with their increasingly interconnected systems and often limited cybersecurity resources, are becoming prime targets for cybercriminals. These attacks range from relatively simple phishing attempts to sophisticated ransomware deployments, each with its own motivations and consequences. Understanding the types of attacks and the criminals’ objectives is crucial for developing effective preventative measures.Cybercriminals employ a variety of methods to breach school systems, driven by a range of motivations, from financial gain to disruption and data theft.
The impact of these attacks can be devastating, disrupting education, compromising sensitive data, and incurring significant financial losses.
Methods of Cyberattacks Against Schools
Cybercriminals use a diverse toolkit to target schools. Phishing remains a prevalent method, using deceptive emails or text messages to trick individuals into revealing login credentials or downloading malware. Ransomware attacks encrypt school data, demanding payment for its release. Malware, encompassing viruses, worms, and Trojans, can infiltrate systems, steal data, or disrupt operations. Denial-of-service (DoS) attacks overwhelm school networks, rendering them inaccessible.
Finally, social engineering, manipulating individuals to divulge information, is a common tactic. These attacks are often sophisticated and tailored to exploit vulnerabilities in specific school systems.
Motivations Behind Cyberattacks on Educational Institutions
The motivations behind these attacks are multifaceted. Financial gain is a primary driver, with ransomware attacks aiming for direct monetary payments. Data theft can target student records, employee information, or intellectual property for resale on the dark web. Disruption of school operations, such as cancelling exams or delaying academic schedules, can be a goal for politically motivated actors or cyber-extortionists.
In some cases, attacks are simply opportunistic, exploiting vulnerabilities for personal gain or as a test of skills.
Examples of Real-World Cyberattacks on Schools and Their Consequences
The consequences of cyberattacks on schools can be severe and far-reaching.
- In 2021, a ransomware attack on a school district in Texas encrypted critical systems, disrupting classes and costing hundreds of thousands of dollars in recovery efforts. The attack also resulted in a temporary halt to online learning and administrative services. The attackers demanded a substantial ransom for the decryption key.
- A 2022 incident involved a phishing campaign targeting a university in California. Successful phishing attempts led to the theft of sensitive student and faculty data, including social security numbers and financial information. The breach resulted in significant legal and reputational damage for the institution, along with the need for extensive credit monitoring services for affected individuals.
- A smaller school in Maine experienced a malware infection that compromised its student management system. This resulted in a delay in the release of report cards and transcripts, impacting students’ college applications and other crucial processes.
Impact of Different Attack Vectors on School Operations
The impact of a cyberattack varies significantly depending on the attack vector. Ransomware attacks directly disrupt operations by encrypting essential data, while phishing attacks can lead to data breaches and further compromises. Malware infections can spread rapidly, compromising multiple systems and potentially leading to significant data loss. DoS attacks temporarily disable access to online resources, hindering teaching and administrative functions.
The recovery time and financial costs also vary considerably depending on the type and severity of the attack, the preparedness of the school’s IT infrastructure, and the effectiveness of its incident response plan.
Data Breaches and Their Impact
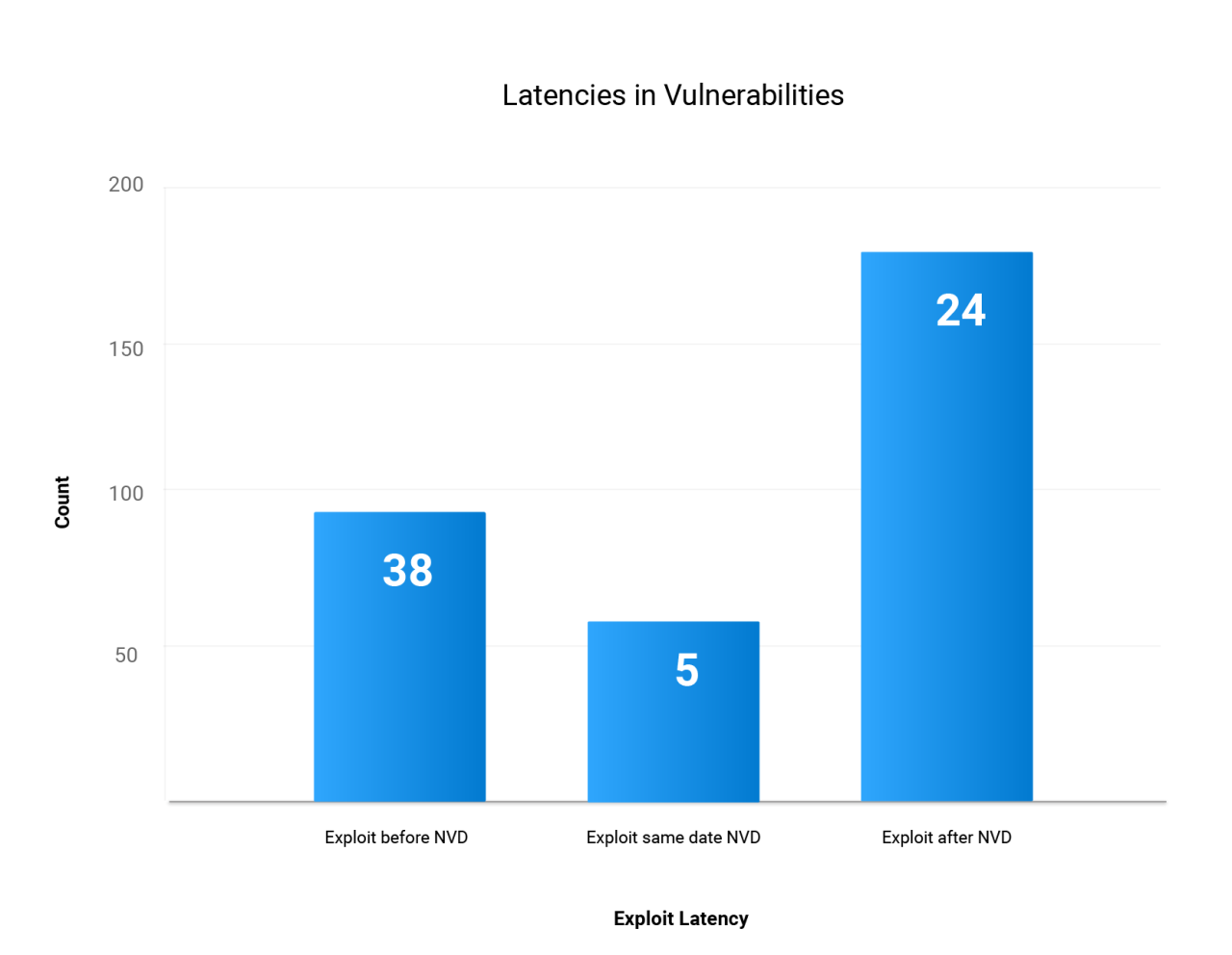
Data breaches in schools are devastating events with far-reaching consequences. The sensitive nature of the information held by educational institutions makes them prime targets for cybercriminals, and the impact of a successful attack can be financially crippling, legally damaging, and deeply damaging to the school’s reputation. Understanding the types of data involved, the potential repercussions, and effective mitigation strategies is crucial for all schools.The sensitive data stored by schools encompasses a wide range of personal and financial information.
Student records, for instance, often include names, addresses, social security numbers, grades, medical information, disciplinary records, and even photos. Financial data held by the school might involve employee payroll information, student financial aid records, and details of school fundraising activities. The unauthorized release of any of this information can have severe consequences for both the individuals affected and the institution itself.
Types of Sensitive Data and Potential Consequences
A data breach exposing student records could lead to identity theft, harassment, or discrimination. The unauthorized access to financial information can result in financial loss for the school or its employees and students, potentially leading to further complications like credit card fraud or embezzlement. The reputational damage from a data breach can be significant, impacting enrollment numbers, funding opportunities, and the overall trust placed in the institution.
For example, a well-publicized breach could lead to parents transferring their children to other schools, negatively impacting the school’s budget and future prospects.
Legal and Reputational Ramifications of Data Breaches, Schools are lucrative targets for cybercriminals
Schools face significant legal and regulatory ramifications following a data breach. Depending on the jurisdiction and the type of data compromised, schools may be subject to fines, lawsuits from affected individuals, and investigations by regulatory bodies like the Federal Trade Commission (FTC) or state attorneys general. The costs associated with legal fees, remediation efforts, and potential settlements can be substantial.
Beyond the legal ramifications, a data breach can severely damage a school’s reputation. Loss of public trust can be difficult to regain, potentially leading to a decline in enrollment, decreased funding, and difficulty attracting and retaining qualified staff. The negative publicity associated with a breach can overshadow the school’s positive achievements and create long-term damage to its image.
Strategies for Mitigating the Risk of Data Breaches
Robust cybersecurity measures are essential to mitigate the risk of data breaches. This includes implementing strong access controls, regularly updating software and systems, employing robust firewalls and intrusion detection systems, and providing regular cybersecurity training for staff and students. Data encryption is crucial to protect sensitive information, even in the event of a breach. Regular security audits and penetration testing can identify vulnerabilities before they can be exploited by malicious actors.
Furthermore, developing and implementing a comprehensive incident response plan is vital for minimizing the impact of a successful attack. This plan should include clear procedures for identifying, containing, and responding to a data breach. Finally, establishing strong data governance policies and procedures can help to ensure that sensitive data is handled appropriately and securely throughout its lifecycle.
Responding to a Data Breach: A Flowchart
The following flowchart Artikels the steps a school should take in response to a data breach:[Imagine a flowchart here. The flowchart would start with “Detection of Suspicious Activity/Breach,” leading to “Confirmation of Breach,” then branching to “Contain the Breach” (involving isolating affected systems and preventing further data loss) and “Investigate the Breach” (identifying the cause, extent, and affected data).
From the investigation, the flow would proceed to “Notify Affected Individuals” (in accordance with legal requirements), “Notify Relevant Authorities” (such as law enforcement and regulatory bodies), and “Implement Remedial Measures” (repairing vulnerabilities, enhancing security, and restoring systems). Finally, the flowchart would conclude with “Post-Incident Review and Improvement.” Each step would involve specific actions and considerations.]
The Role of Human Error
Let’s face it, even the most robust cybersecurity systems can be brought down by human error. Schools, with their diverse populations and often limited IT resources, are particularly vulnerable. Understanding and mitigating these human factors is crucial for building a truly secure learning environment. This section explores common mistakes and offers practical solutions to strengthen a school’s cyber defenses.
Human error isn’t malicious intent; it’s often unintentional negligence stemming from a lack of awareness or training. This can range from simple mistakes like using weak passwords to more serious breaches involving clicking on malicious links. The consequences, however, can be equally devastating, leading to data breaches, financial losses, and reputational damage.
Common Human Errors Increasing Cyber Vulnerability
Several common human errors significantly increase the vulnerability of school systems to cyberattacks. Addressing these requires a multi-pronged approach involving education and improved security practices.
- Weak Passwords: Using easily guessable passwords like “password123” or personal information makes systems incredibly vulnerable to brute-force attacks and credential stuffing. This is often compounded by password reuse across multiple accounts.
- Phishing Scams: Malicious emails or text messages disguised as legitimate communications from trusted sources (e.g., banks, schools) often lure users into revealing sensitive information or downloading malware. Sophisticated phishing attacks can be incredibly convincing, even to tech-savvy individuals.
- Clicking on Malicious Links: Unsuspecting clicks on links embedded in emails, social media posts, or websites can lead to malware infections, data breaches, and system compromises. This is particularly dangerous with links that appear legitimate but redirect to harmful sites.
- Ignoring Software Updates: Failing to update software regularly leaves systems vulnerable to known exploits. Many cyberattacks exploit vulnerabilities that have already been patched in updated software versions.
- Poor Physical Security: Leaving laptops or other devices unattended, failing to secure physical access to servers, or not properly disposing of sensitive documents can all create significant security risks.
The Importance of Security Awareness Training
Security awareness training is not just a good idea; it’s a necessity. Equipping staff and students with the knowledge and skills to identify and avoid cyber threats is the most effective way to reduce the risk of human error. Regular, engaging training programs can significantly improve an organization’s overall security posture.
Sample Security Awareness Training Module for School Staff
This module Artikels key topics and practical exercises for a comprehensive security awareness training program for school staff. The goal is to provide staff with the necessary knowledge and skills to proactively protect the school’s systems and data.
- Module 1: Introduction to Cybersecurity Threats: Overview of common threats, including phishing, malware, and ransomware. Discussion of the impact of cyberattacks on schools and students.
- Module 2: Password Security Best Practices: Creating strong, unique passwords; password managers; avoiding password reuse.
- Module 3: Identifying and Avoiding Phishing Attacks: Recognizing suspicious emails, links, and attachments; verifying the authenticity of communications; reporting suspicious activity.
- Module 4: Safe Social Media Practices: Understanding the risks of social media; protecting personal information online; avoiding sharing sensitive information.
- Module 5: Mobile Device Security: Protecting mobile devices from theft and malware; using strong passwords and security features; backing up data regularly.
- Practical Exercises: Simulated phishing attacks, password strength testing, and quizzes to reinforce learning.
Best Practices for Strong Passwords and Avoiding Phishing Scams
Implementing these best practices can significantly reduce the risk of successful cyberattacks stemming from human error.
- Strong Passwords: Use a password manager; create passwords that are at least 12 characters long, including uppercase and lowercase letters, numbers, and symbols; avoid using personal information or easily guessable words.
- Avoiding Phishing Scams: Be wary of unsolicited emails or messages; verify the sender’s identity before clicking on links or opening attachments; hover over links to see the actual URL; report suspicious emails.
Protecting School Systems
Protecting school systems from cyberattacks requires a multi-layered approach encompassing robust network security, regular audits, strong authentication, and employee training. Failing to prioritize cybersecurity leaves schools vulnerable to data breaches, financial losses, and reputational damage, ultimately impacting students and the educational process. A proactive and comprehensive strategy is essential for mitigating these risks.Regular security audits and penetration testing are crucial components of a robust school cybersecurity strategy.
These assessments identify vulnerabilities before malicious actors can exploit them. By proactively identifying and addressing weaknesses, schools can significantly reduce their attack surface and strengthen their overall security posture.
Network Security Best Practices
Implementing strong network security practices is paramount. This involves using firewalls to control network traffic, employing intrusion detection and prevention systems to monitor for malicious activity, and regularly updating all software and firmware to patch known vulnerabilities. Strong password policies, including password complexity requirements and regular password changes, are also essential. Schools should also consider segmenting their network to limit the impact of a potential breach.
For instance, separating student devices from administrative systems prevents a compromise in one area from affecting the other. Regular backups of critical data are also vital for disaster recovery in the event of a successful attack.
The Importance of Regular Security Audits and Penetration Testing
Security audits provide a comprehensive assessment of a school’s security posture. These audits involve reviewing security policies, procedures, and technologies to identify weaknesses and areas for improvement. Penetration testing, on the other hand, simulates real-world attacks to identify vulnerabilities that might be missed during a security audit. Regularly scheduled audits and penetration tests, ideally conducted by independent security experts, provide schools with valuable insights into their security weaknesses and allow them to address them proactively.
For example, a recent audit might reveal that a specific software application is outdated and vulnerable to exploitation, prompting immediate remediation.
Multi-Factor Authentication: Enhancing Security
Multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide multiple forms of authentication before accessing school systems. This typically involves a combination of something they know (password), something they have (security token or mobile device), and something they are (biometric authentication). MFA significantly reduces the risk of unauthorized access, even if passwords are compromised.
By requiring multiple authentication factors, MFA makes it much harder for attackers to gain access, even if they obtain usernames and passwords through phishing or other means. Consider a scenario where a teacher’s password is stolen. With MFA, the attacker would still need access to the teacher’s phone or another authentication factor to log in, significantly hindering their access.
Hypothetical Scenario: Robust Cybersecurity Implementation
Imagine a school district implementing a comprehensive cybersecurity program. This includes regular security awareness training for all staff, strong password policies enforced through multi-factor authentication, network segmentation, robust firewalls, intrusion detection systems, and regular security audits and penetration testing. The positive outcomes would be numerous. The district would experience a significant reduction in successful cyberattacks, minimized data breaches, improved data protection compliance, enhanced trust among parents and the community, and increased operational efficiency due to reduced downtime from security incidents.
Furthermore, the proactive approach to security would likely lead to lower insurance premiums and a stronger reputation for responsible data handling.
The Economic Impact of Cyberattacks on Schools

Cyberattacks against schools aren’t just a technological problem; they represent a significant and growing economic threat. The financial repercussions extend far beyond the immediate costs of system repair, impacting budgets, long-term planning, and even the school’s reputation. Understanding these economic impacts is crucial for effective preventative measures and resource allocation.The financial costs associated with recovering from a cyberattack are substantial and multifaceted.
These costs can cripple even well-funded school districts, forcing difficult choices between essential services and cybersecurity investments.
Direct Costs of Cyberattacks
Direct costs are the immediate and easily quantifiable expenses incurred during and immediately after a cyberattack. These include the expenses related to restoring systems, engaging legal counsel, and paying for incident response teams. Remediation can involve purchasing new hardware and software, rebuilding compromised systems, and restoring lost data. Legal fees can mount quickly, especially if the attack leads to legal action from affected parties like parents or students.
Hiring cybersecurity experts to investigate the breach, contain the damage, and implement preventative measures also contributes significantly to the overall direct costs. For example, a ransomware attack on a school district might involve tens of thousands of dollars in ransom payments alone, in addition to the costs of remediation and legal consultation.
Indirect Costs of Cyberattacks
Beyond the direct expenses, indirect costs represent the less tangible but equally damaging financial consequences of a cyberattack. Reputational damage is a significant concern; a data breach can erode public trust, impacting enrollment numbers and potentially leading to a loss of funding. Loss of student trust and disruption to learning are also significant factors. The time spent recovering from an attack, including the downtime of systems and the redirection of staff resources, results in lost productivity.
This lost productivity translates to lost teaching time, administrative inefficiencies, and the inability to effectively manage essential school functions. For instance, a school might lose valuable fundraising opportunities due to the disruption caused by a cyberattack, impacting their long-term financial stability.
Long-Term Impacts of Cyberattacks
The long-term financial impacts of a cyberattack can be devastating and far-reaching. The costs associated with enhanced cybersecurity measures, such as ongoing monitoring, employee training, and system upgrades, are significant. Schools may need to invest in more robust security systems, which can be expensive to implement and maintain. Furthermore, the lingering effects of reputational damage can negatively impact future fundraising efforts and limit the school’s ability to secure grants and other funding sources.
The loss of student data can lead to long-term legal battles and financial penalties, adding to the overall burden. A diminished reputation can also make it harder to attract and retain high-quality teachers and staff.
Financial Implications of Cyberattacks: A Summary
| Direct Costs | Indirect Costs | Long-Term Impacts |
|---|---|---|
| Remediation (hardware, software replacement) | Reputational damage | Increased cybersecurity spending |
| Legal fees (investigations, lawsuits) | Loss of student trust | Difficulty securing funding |
| Incident response team costs | Lost productivity (teaching time, administration) | Potential loss of enrollment |
| Ransom payments (in ransomware attacks) | Loss of fundraising opportunities | Long-term legal battles |
Wrap-Up
The vulnerability of schools to cyberattacks is a serious issue, but not an insurmountable one. By understanding the motivations behind these attacks, identifying common vulnerabilities, and implementing robust security measures – from staff training to advanced technological safeguards – we can significantly reduce the risk. Proactive measures, coupled with a culture of cybersecurity awareness, are crucial in protecting our schools and the valuable data they hold.
It’s a shared responsibility – educators, administrators, and students all have a part to play in building a safer digital learning environment.
Key Questions Answered: Schools Are Lucrative Targets For Cybercriminals
What types of data are most commonly targeted in school cyberattacks?
Student personal information (names, addresses, social security numbers), financial records, academic transcripts, and employee data are all prime targets.
What is the role of insurance in mitigating the financial impact of a cyberattack on a school?
Cybersecurity insurance can help cover costs associated with data breach response, legal fees, and system recovery, but comprehensive policies are crucial.
How can schools effectively communicate about a data breach to parents and students?
Transparency and prompt communication are key. Schools should have a pre-planned communication strategy, including templates and contact lists, to ensure timely and effective notification.
Are there any government resources available to help schools improve their cybersecurity?
Yes, many government agencies offer resources, grants, and training programs to assist schools in enhancing their cybersecurity posture. Check with your local and national education departments.





