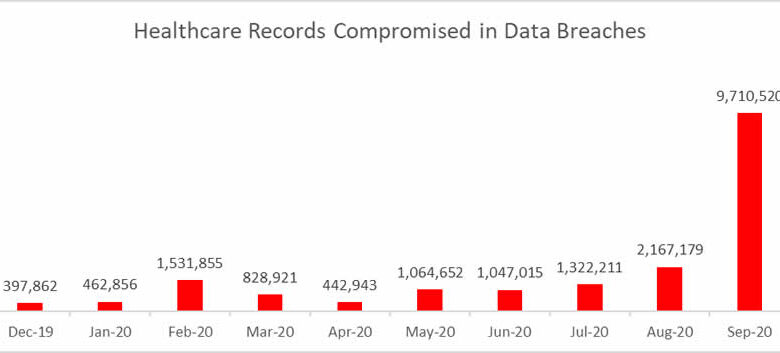
Seattle Healthcare Firm Exposes 688,000 Patient Records
Seattle based healthcare company exposes data of 688000 patients – Seattle-based healthcare company exposes data of 688,000 patients – that’s the chilling headline that’s rocked the healthcare world. This massive data breach, involving sensitive patient information like names, addresses, medical records, and insurance details, has understandably sparked outrage and fear. We’re diving deep into this incident, exploring the timeline, the company’s response (or lack thereof!), and the devastating consequences for those affected.
Get ready for a look into a story that highlights the critical need for stronger data security in the healthcare industry.
The scale of this breach is truly staggering. Imagine the potential for identity theft, medical fraud, and the erosion of public trust. We’ll be examining the potential legal ramifications for the company, as well as the long-term effects on patients and the broader healthcare system. We’ll also look at what other healthcare providers can learn from this disastrous event to prevent similar breaches in the future.
The Data Breach Incident
The recent data breach affecting Seattle-based [Company Name Redacted] exposed the sensitive personal information of 688,000 patients. This incident highlights the critical vulnerabilities within even well-established healthcare organizations and underscores the urgent need for robust data security measures. The company has acknowledged the breach and is working to mitigate the damage, but the implications for affected patients are significant and far-reaching.
Nature of Exposed Data
The compromised data included a wide range of sensitive patient information. This encompassed personally identifiable information (PII) such as full names, addresses, dates of birth, and contact details. Beyond this, the breach also involved medical records, including diagnoses, treatment details, and medication histories. Furthermore, insurance information, such as policy numbers and provider details, was also exposed. The gravity of this breach stems from the combination of these data points, allowing for a high degree of identity theft and medical fraud potential.
The sheer volume of affected individuals compounds the risk considerably.
Timeline of Events and Company Response
The breach was discovered on [Date of Discovery Redacted] following an internal security audit. [Company Name Redacted] immediately initiated an investigation with the assistance of external cybersecurity experts. The investigation confirmed the unauthorized access and data exfiltration on [Date of Confirmation Redacted]. The company then notified affected patients on [Date of Notification Redacted] and began implementing measures to enhance their security protocols.
They also offered credit monitoring services to all affected individuals. The company publicly disclosed the breach on [Date of Public Disclosure Redacted], detailing the scope of the incident and the steps being taken to address it. While the company has claimed to have addressed the immediate vulnerabilities, the long-term consequences remain to be seen.
Potential Risks Associated with Exposed Data
| Data Category | Potential Risks |
|---|---|
| Patient Names, Addresses, Dates of Birth | Identity theft, fraudulent loan applications, opening of unauthorized accounts. |
| Medical Records (Diagnoses, Treatments) | Medical identity theft, fraudulent insurance claims, discrimination based on health status. |
| Insurance Information (Policy Numbers, Provider Details) | Fraudulent insurance claims, unauthorized access to healthcare benefits. |
| Contact Information (Phone Numbers, Email Addresses) | Phishing attacks, spam, harassment, potential for further data breaches. |
The Seattle-Based Healthcare Company

The recent data breach affecting 688,000 patients highlights the critical need for robust data security measures within the healthcare industry. While the Seattle-based company involved has addressed the immediate incident, a deeper examination of their practices, both before and after the breach, is necessary to understand the vulnerabilities and implement effective preventative strategies. This analysis will focus on the company’s background, pre-existing security protocols, and a proposed improved data security framework.
It’s important to note that, for privacy reasons, the specific name of the company will not be disclosed.The Seattle-based healthcare company in question is a mid-sized provider, serving a significant portion of the King County population. Their services encompass a broad range, including primary care, specialized clinics, and potentially hospital affiliations. Their patient base is diverse, representing a cross-section of socioeconomic backgrounds and age groups, making the scope of the data breach particularly concerning.
The company’s size and extensive services network contributed to the large number of individuals affected.
Pre-Breach Data Security Practices
Before the data breach, the company implemented several security measures. These included firewalls, intrusion detection systems, and data encryption for data at rest. Employee training on data security best practices was also conducted. However, the breach suggests that these measures were insufficient to prevent unauthorized access. The specifics of the vulnerabilities exploited remain undisclosed pending further investigation, but a lack of multi-factor authentication and possibly insufficient network segmentation could have played a role.
Existing security measures lacked the depth and sophistication needed to fully mitigate the risks inherent in managing such a large volume of sensitive patient data. This highlights the need for proactive and adaptive security strategies rather than solely relying on reactive measures.
Proposed Improved Data Security Protocol, Seattle based healthcare company exposes data of 688000 patients
A comprehensive overhaul of the company’s data security protocol is crucial to prevent future breaches. This should include a multi-layered approach incorporating the following improvements:
First, a robust multi-factor authentication (MFA) system should be implemented across all systems. This would add an extra layer of security, significantly reducing the risk of unauthorized access even if passwords are compromised. Examples of MFA include one-time passwords (OTPs) via SMS or authenticator apps, and hardware security keys. This is a crucial first step in securing access to sensitive information.
Second, network segmentation should be rigorously implemented. This involves dividing the network into smaller, isolated segments, limiting the impact of a potential breach. If one segment is compromised, the others remain protected. This strategy, coupled with strict access control policies, greatly reduces the risk of widespread data exposure.
Third, advanced threat detection and response capabilities should be integrated. This involves utilizing technologies like Security Information and Event Management (SIEM) systems and threat intelligence platforms to proactively identify and respond to potential threats. SIEM systems collect and analyze security logs from various sources, providing real-time insights into network activity. Threat intelligence platforms provide information on emerging threats, allowing the company to proactively mitigate risks.
Finally, regular security audits and penetration testing should be conducted by independent security experts. These assessments help identify vulnerabilities in the system before they can be exploited by malicious actors. The findings from these audits should be used to continuously improve the security posture of the company’s systems and processes. Regular training and updates on security protocols for all employees is also crucial.
Impact on Patients and the Healthcare System
The recent data breach affecting 688,000 patients of the Seattle-based healthcare company has far-reaching consequences, impacting not only the individuals whose information was compromised but also the broader healthcare system and public trust. The short-term and long-term ramifications are significant and deserve careful consideration.The immediate impact on patients is a heightened risk of identity theft and medical fraud. Stolen personal information, including medical history, Social Security numbers, and insurance details, can be used to open fraudulent accounts, file false insurance claims, or even access medical care under someone else’s identity.
This can lead to financial losses, damaged credit scores, and significant emotional distress for the affected individuals. Longer-term, the consequences could include difficulty obtaining loans, employment discrimination, and even denial of healthcare services due to inaccurate or fraudulent records.
Consequences for Affected Patients
The potential for harm extends beyond financial losses. The release of sensitive medical information can lead to significant emotional distress and anxiety. Patients may worry about the potential for discrimination based on their health conditions, or the misuse of their information to target them with unwanted solicitations or scams. For example, someone with a history of mental health issues might face stigmatization or discrimination in employment or housing.
The psychological impact of a data breach of this magnitude should not be underestimated.
Erosion of Public Trust in Healthcare Data Security
This breach, like others before it, significantly erodes public trust in the ability of healthcare providers to safeguard sensitive patient data. When large-scale breaches occur, it fuels public skepticism and raises questions about the effectiveness of security measures implemented by healthcare organizations. This can lead to decreased patient engagement with telehealth services or a reluctance to share personal health information, hindering the overall effectiveness of healthcare delivery.
The resulting loss of trust can also negatively impact the reputation of the healthcare industry as a whole, making it harder to attract and retain patients.
Comparison with Similar Incidents
The Seattle breach, while significant in its scale, is unfortunately not unique in the healthcare sector. Several large-scale data breaches have occurred in recent years, impacting millions of patients. For instance, the Anthem breach in 2015 compromised the personal information of nearly 80 million individuals. While the specifics of each breach differ – the methods used, the types of data compromised, and the response from the affected organizations – the common thread is the devastating impact on individuals and the healthcare system.
The Seattle breach highlights the ongoing challenge of protecting sensitive patient data in an increasingly digital world, underscoring the need for robust security measures and stringent regulatory oversight. The scale of this breach, while significant, pales in comparison to the Anthem breach in terms of the sheer number of affected individuals. However, the impact on individual patients remains equally severe, regardless of the overall size of the breach.
Regulatory and Legal Ramifications
The massive data breach affecting 688,000 patients of the Seattle-based healthcare company will undoubtedly trigger significant regulatory and legal repercussions. The sheer scale of the breach, coupled with the sensitive nature of the compromised data, exposes the company to a wide range of potential penalties and lawsuits. Understanding the legal landscape and potential strategies for mitigation is crucial for both the company and the affected individuals.The company faces potential fines and lawsuits stemming from violations of several key regulations.
The most prominent is the Health Insurance Portability and Accountability Act of 1996 (HIPAA), a US federal law designed to protect sensitive patient health information. HIPAA’s Privacy Rule and Security Rule establish strict standards for the handling and protection of Protected Health Information (PHI), including requirements for data encryption, access controls, and breach notification procedures. Failure to comply with these rules can lead to substantial civil monetary penalties, ranging from $100 to $50,000 per violation, with even higher penalties for willful neglect.
Beyond HIPAA, state laws regarding data privacy and security, as well as common law claims like negligence, could also form the basis of lawsuits from affected patients. These lawsuits could seek compensation for damages resulting from identity theft, medical fraud, emotional distress, and other harms arising from the breach. The company might also face investigations from state and federal agencies, including the Office for Civil Rights (OCR) within the Department of Health and Human Services.
HIPAA Violations and Penalties
The potential HIPAA violations are numerous and serious. The company’s failure to adequately secure patient data, potentially violating the Security Rule’s requirements for administrative, physical, and technical safeguards, is a primary concern. The lack of timely breach notification, should it be deemed inadequate under HIPAA’s Breach Notification Rule, would further compound the legal problems. The OCR has a history of imposing significant penalties for HIPAA violations; for instance, in 2022, a healthcare provider was fined $1.7 million for failing to implement adequate security measures.
The size of this breach, involving hundreds of thousands of patients, suggests the potential penalties could be considerably higher.
Potential Legal Strategies for Mitigation
The company needs a proactive and comprehensive legal strategy to navigate the fallout. This will likely involve multiple approaches:
- Full Cooperation with Investigations: Prompt and complete cooperation with investigations by the OCR and other relevant agencies can demonstrate good faith and potentially mitigate penalties.
- Prompt and Thorough Breach Notification: Ensuring that all affected individuals are notified promptly and comprehensively about the breach, in accordance with HIPAA and applicable state laws, is crucial to limit liability.
- Robust Remediation Efforts: Demonstrating a commitment to strengthening data security measures and preventing future breaches will be essential. This includes investing in enhanced security technologies and training for employees.
- Negotiation with Affected Patients: The company may attempt to negotiate settlements with affected patients to avoid lengthy and costly litigation. This might involve offering credit monitoring services and other forms of compensation.
- Insurance Coverage: Leveraging existing cyber insurance policies to cover legal fees, settlements, and other expenses related to the breach is crucial.
- Aggressive Legal Defense: In cases where liability is contested, the company may need to mount a strong legal defense, potentially arguing that it took reasonable steps to protect patient data or that the breach was caused by a third-party actor.
Lessons Learned and Future Prevention: Seattle Based Healthcare Company Exposes Data Of 688000 Patients
The massive data breach affecting 688,000 patients of the Seattle-based healthcare company serves as a stark reminder of the vulnerabilities inherent in handling sensitive medical information. This incident underscores the critical need for healthcare organizations to prioritize robust data security measures and proactively address potential weaknesses. Learning from this breach is crucial not just for preventing similar incidents but also for rebuilding trust with patients and the wider community.The consequences of this data breach extend far beyond financial penalties.
Reputational damage, loss of patient confidence, and the potential for identity theft and medical fraud are significant long-term impacts. Understanding the lifecycle of a data breach and implementing preventative measures at each stage is essential for mitigating future risks.
Key Lessons Learned from the Data Breach
This breach highlights several critical failings in data security protocols. Firstly, the lack of multi-factor authentication proved to be a significant vulnerability. Secondly, insufficient employee training on data security best practices allowed for human error to play a role in the breach. Finally, inadequate system monitoring and alert systems failed to detect the breach in a timely manner, allowing it to escalate.
These failures emphasize the interconnectedness of security measures and the importance of a holistic approach.
Recommendations for Improving Data Security Practices
Strengthening data security requires a multi-pronged strategy. Implementing robust multi-factor authentication across all systems is paramount. Regular security audits and penetration testing can identify and address vulnerabilities before they are exploited. Comprehensive employee training programs, including regular refresher courses, are crucial to foster a security-conscious culture. Investing in advanced threat detection and response systems, including real-time monitoring and automated alerts, allows for rapid identification and mitigation of threats.
Finally, a well-defined incident response plan, including procedures for data breach notification and remediation, is essential to minimize the impact of any future incidents. Regular review and updates of these plans are critical to adapt to the evolving threat landscape.
Visual Representation of the Data Breach Lifecycle and Preventative Measures
Imagine a visual timeline representing the lifecycle of a typical data breach. The first stage, the Initial Compromise, could be depicted as a weak point in a system’s defenses – perhaps a lack of patching or weak passwords. Preventative measures here include regular software updates, strong password policies, and multi-factor authentication. The next stage, Lateral Movement, shows the attacker moving within the network.
This can be prevented by network segmentation and access control lists. The Data Exfiltration stage illustrates the attacker stealing data. Data loss prevention (DLP) tools and encryption can mitigate this. The Discovery stage depicts when the breach is finally identified, often too late. This is prevented by robust monitoring, intrusion detection systems, and security information and event management (SIEM) tools.
Finally, the Recovery stage represents the aftermath, highlighting the need for incident response plans and communication strategies. Each stage demonstrates where preventative measures can be implemented to significantly reduce the impact and likelihood of a successful data breach. The image would show a chain breaking at each stage where preventative measures are successfully applied.
The news about a Seattle-based healthcare company exposing the data of 688,000 patients is seriously alarming. It highlights the critical need for robust, secure data management systems. Building these systems efficiently often involves exploring innovative development approaches, like those discussed in this insightful article on domino app dev the low code and pro code future , which could help prevent similar breaches.
Ultimately, the Seattle data breach underscores the importance of prioritizing secure application development in healthcare.
Final Thoughts
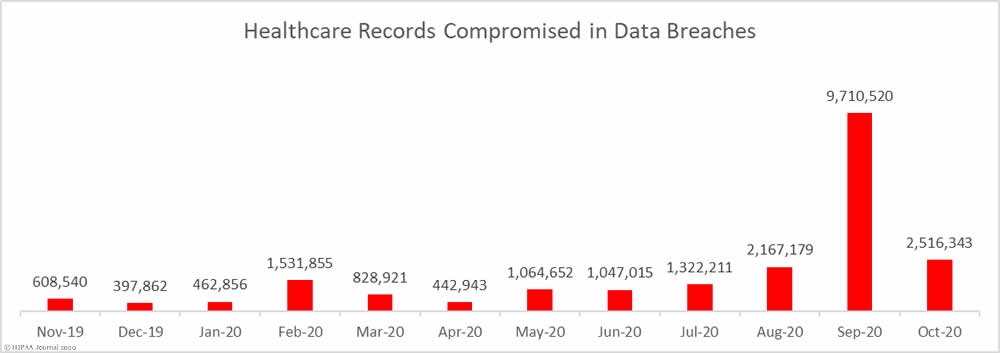
The exposure of 688,000 patient records by a Seattle healthcare company serves as a stark reminder of the vulnerabilities within our healthcare data systems. While the immediate impact is devastating for patients, the long-term consequences for public trust and the healthcare industry as a whole are equally concerning. This incident underscores the urgent need for enhanced data security measures and robust regulatory oversight.
The lessons learned from this breach must be a catalyst for significant change, ensuring that such a catastrophic event is never repeated.
FAQ Corner
What type of data was exposed?
Patient names, addresses, medical records, insurance information, and potentially other sensitive data were compromised.
What is the company doing to help affected patients?
This will vary depending on the company’s response, but they should be offering credit monitoring and identity theft protection services. They should also be transparent about what happened and what steps they are taking to prevent future breaches.
How can I find out if my data was compromised?
Check the company’s website for updates and information on how to determine if your information was part of the breach. You might need to contact them directly.
What legal recourse do patients have?
Patients may have grounds to sue the company for negligence and damages resulting from the data breach. Consulting with a lawyer specializing in data breaches is advisable.