Securing Cloud Strategies for CSPs Malware Mitigation
Securing the cloud strategies for csps to mitigate malware hosting risks – Securing cloud strategies for CSPs to mitigate malware hosting risks is crucial in today’s digital landscape. The rise of cloud computing has brought unprecedented convenience and scalability, but it’s also created new attack surfaces for malicious actors. This means CSPs face unique challenges in protecting their infrastructure and their clients’ data from sophisticated malware attacks. We’ll dive into the multifaceted strategies needed to secure cloud environments, from proactive measures like robust security architectures to reactive responses that minimize damage during incidents.
Understanding the various attack vectors, implementing multi-layered security, and leveraging cutting-edge technologies like AI and machine learning are key components of a comprehensive strategy. Equally important is maintaining regulatory compliance and fostering a strong security culture within the organization. This isn’t just about technology; it’s about people, processes, and a commitment to continuous improvement in the face of evolving threats.
Understanding Cloud Security Threats for CSPs
Cloud Service Providers (CSPs) face a unique set of security challenges unlike traditional on-premise infrastructure. Their responsibility extends to securing vast and diverse environments, often hosting data and applications for numerous clients. This shared responsibility model inherently increases the potential for malware to spread rapidly and impact multiple organizations, magnifying the consequences of a security breach.The scale and complexity of cloud environments present a significant challenge.
A single vulnerability exploited in a shared infrastructure component can cascade across multiple tenants, leading to widespread compromise. This makes the prevention and detection of malware hosting a critical concern for CSPs, impacting not only their own operations but also the security and trust of their clients.
Malware Hosting Risks for CSPs
CSPs face a heightened risk of malware hosting due to the shared nature of their infrastructure. Attackers may target vulnerabilities in the CSP’s platform, applications, or customer configurations to gain unauthorized access and deploy malware. This could involve exploiting known vulnerabilities in popular software, leveraging misconfigurations within customer environments, or employing sophisticated social engineering tactics to gain initial access.
Once inside, malware can spread rapidly, affecting multiple clients and causing significant damage. The distributed nature of cloud environments also complicates detection and remediation efforts.
Common Attack Vectors
Several attack vectors are commonly used to compromise cloud environments and facilitate malware hosting. These include exploiting vulnerabilities in cloud-based services (e.g., misconfigured storage buckets, insecure APIs), utilizing phishing and social engineering to obtain credentials, leveraging compromised user accounts, employing malicious insiders, and deploying advanced persistent threats (APTs) designed for long-term stealthy access. These attacks can result in data breaches, service disruptions, and reputational damage for the CSP.
Successful attacks often involve a combination of techniques to bypass security controls and establish a persistent presence. For example, an attacker might initially gain access through a phishing campaign, then leverage that access to move laterally within the cloud environment and deploy malware on multiple virtual machines.
Impact on Reputation and Customer Trust
The consequences of malware hosting for CSPs are far-reaching. A single major security incident involving malware can severely damage a CSP’s reputation, leading to loss of customer trust and significant financial repercussions. Customers may lose confidence in the CSP’s ability to protect their data, potentially leading to contract cancellations and legal action. Regulatory fines and penalties can also be substantial, particularly in industries with stringent compliance requirements (e.g., healthcare, finance).
Moreover, the impact extends beyond direct customers; negative publicity can deter potential clients from choosing the CSP’s services, hindering future growth and profitability. Maintaining a strong security posture and proactively addressing potential vulnerabilities are crucial for mitigating these risks.
Types of Malware and Their Impact
The following table compares different types of malware and their potential impact on CSPs:
| Malware Type | Description | Impact on CSPs | Mitigation Strategies |
|---|---|---|---|
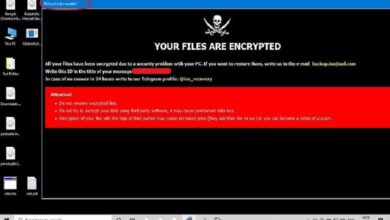
| Ransomware | Encrypts data and demands a ransom for its release. | Data loss, service disruption, reputational damage, financial losses. | Regular backups, strong access controls, security awareness training. |
| Botnets | Networks of compromised computers used for malicious activities. | Distributed denial-of-service (DDoS) attacks, data theft, spam distribution. | Intrusion detection systems (IDS), security information and event management (SIEM), vulnerability management. |
| Cryptojackers | Secretly use computing resources to mine cryptocurrency. | Performance degradation, increased operational costs, potential legal issues. | Regular security audits, monitoring of resource usage, anti-malware solutions. |
| Rootkits | Hide their presence on a system, making detection difficult. | Persistent access, data theft, system instability. | Regular system scans, advanced threat detection tools, security patching. |
Implementing Proactive Security Measures
Proactive security is paramount for CSPs aiming to prevent malware hosting. A reactive approach, focused solely on responding to breaches, is insufficient in today’s sophisticated threat landscape. A robust, multi-layered defense is crucial, combining preventative measures with robust detection and response capabilities. This section will explore key elements of a proactive security strategy.A multi-layered security architecture acts as a defense in depth, ensuring that even if one layer is compromised, others remain to protect the system.
This approach significantly reduces the likelihood of successful malware attacks and minimizes the impact of any breaches that do occur. Think of it like a castle with multiple walls, moats, and guards – each layer adds another level of protection.
Multi-Layered Security Architecture for CSPs
A robust multi-layered security architecture for CSPs should incorporate several key components. The first layer involves securing the physical infrastructure, including data centers and network equipment, with physical access controls and environmental monitoring. The second layer focuses on network security, utilizing firewalls, intrusion detection/prevention systems (IDPS), and virtual private networks (VPNs) to control network traffic and prevent unauthorized access.
The third layer centers on host security, employing endpoint detection and response (EDR) solutions, anti-malware software, and secure configuration management on all servers and virtual machines. The fourth layer addresses application security through secure coding practices, regular security testing, and vulnerability management. Finally, the fifth layer involves data security, including data encryption both in transit and at rest, access control mechanisms, and data loss prevention (DLP) tools.
This layered approach ensures comprehensive protection.
The Role of Intrusion Detection and Prevention Systems (IDPS)
IDPS systems are critical components of a proactive security strategy. They monitor network traffic and system activity for suspicious patterns indicative of malicious activity, such as unauthorized access attempts, malware infections, or denial-of-service attacks. Intrusion detection systems (IDS) passively monitor and alert on suspicious activity, while intrusion prevention systems (IPS) actively block or mitigate threats. By deploying both IDS and IPS, CSPs gain a comprehensive monitoring and response capability, significantly reducing the risk of malware hosting.
For example, an IPS could block a known malicious IP address from accessing a CSP’s network, preventing a potential malware infection before it even begins. Effective deployment requires careful configuration and ongoing monitoring to ensure optimal performance and minimize false positives.
Secure Coding Practices for Cloud Applications
Secure coding practices are fundamental to preventing vulnerabilities that could be exploited by malware. Developers must follow established security principles throughout the software development lifecycle (SDLC), including input validation, output encoding, secure authentication and authorization mechanisms, and the avoidance of known vulnerabilities. For example, developers should always validate user inputs to prevent injection attacks, such as SQL injection or cross-site scripting (XSS).
Regular security code reviews and penetration testing are also crucial to identify and address vulnerabilities before deployment. Following secure coding best practices minimizes the attack surface of cloud applications, reducing the likelihood of malware infections. Ignoring these practices can lead to severe security breaches, as seen in numerous real-world examples of applications compromised due to insecure coding.
Vulnerability Management and Patching in Cloud Environments, Securing the cloud strategies for csps to mitigate malware hosting risks
Proactive vulnerability management is crucial for mitigating malware hosting risks. This involves regularly scanning systems and applications for known vulnerabilities, prioritizing remediation efforts based on risk, and applying necessary patches promptly. In cloud environments, automated patching and vulnerability scanning tools are essential to manage the scale and complexity of the infrastructure. CSPs should establish a robust patching process, including testing patches in a staging environment before deploying them to production, to minimize disruption and ensure stability.
Failure to implement timely patching leaves systems vulnerable to exploitation, making them prime targets for malware. For instance, the timely patching of the Log4j vulnerability prevented widespread exploitation and significant damage across many organizations.
Reactive Measures and Incident Response
A robust incident response plan is crucial for CSPs facing malware infections. It’s not a matter of
- if* an incident will occur, but
- when*. A well-defined plan minimizes damage, speeds recovery, and protects the reputation of the CSP and its clients. This plan should be regularly tested and updated to reflect evolving threats and infrastructure changes.
The core of effective reactive measures lies in swift action. Delay in responding to a malware infection can exponentially increase the damage and the cost of remediation. The speed and efficiency of the response directly impacts the overall success in mitigating the impact of the attack.
Incident Response Plan Stages
A comprehensive incident response plan should encompass several key stages. These stages ensure a systematic and coordinated approach to handling the incident, from initial detection to full recovery and post-incident analysis. A well-defined process helps to maintain control and minimizes confusion during a stressful situation. This structured approach also allows for better tracking of progress and identification of areas for improvement in future iterations of the plan.
Isolating Infected Systems
Upon detecting a malware infection, immediate isolation of the affected system(s) is paramount. This prevents the malware from spreading laterally within the CSP’s network, impacting other systems and data. Isolation can involve disconnecting the infected system from the network, disabling network interfaces, or utilizing network segmentation techniques. Virtual machine snapshots, if available, provide a quick rollback point before the infection spreads further.
For example, a CSP might use virtual machine snapshots to revert an infected server to a known good state before the malware attack, significantly reducing recovery time.
Malware Identification and Analysis
Identifying the source and type of malware is crucial for effective remediation. This involves analyzing system logs, network traffic, and the malware itself (if safely contained). Advanced techniques like sandbox analysis can be employed to observe the malware’s behavior in a controlled environment without risking further damage. For instance, a security team might use a sandbox to analyze a suspicious file, observing its attempts to connect to external servers or its actions on the file system without allowing it to impact the main network.
This analysis helps determine the malware’s capabilities and its potential impact.
Data Recovery and System Restoration
Data recovery and system restoration are the final stages of the incident response process. This may involve restoring data from backups, utilizing data recovery tools, or rebuilding affected systems from scratch. The choice of method depends on the extent of the damage and the availability of reliable backups. Regular backups, ideally stored offline or in geographically separate locations, are essential for quick and effective data recovery.
For example, a CSP could use a 3-2-1 backup strategy (three copies of data, on two different media, with one copy offsite) to ensure business continuity in the event of a major malware attack. The process also involves verifying the integrity of restored data and systems to ensure the complete removal of malware.
Leveraging Security Technologies
Securing cloud environments against malware requires a multi-layered approach, and leveraging advanced security technologies is paramount. This section explores several key technologies that CSPs can implement to bolster their defenses and mitigate the risks associated with malware hosting. Understanding the strengths and weaknesses of each technology is crucial for effective deployment and management.Sandboxing technologies offer a controlled environment to analyze potentially malicious files and code without exposing the wider system to risk.
This allows for a more thorough assessment of malware behavior and capabilities, providing valuable insights for incident response and future prevention strategies.
Sandboxing Technologies: Benefits and Limitations
Sandboxing involves executing suspicious files in an isolated virtual environment. This allows security teams to observe the file’s behavior without risking infection of the main system. Benefits include early detection of malicious activity, detailed analysis of malware behavior (including network connections and registry modifications), and the ability to identify zero-day threats. However, limitations exist. Sandboxing can be computationally expensive, requiring significant processing power and storage.
Sophisticated malware can also employ evasion techniques to mask its malicious behavior within the sandboxed environment. Furthermore, some advanced malware may require interaction with external systems or specific hardware to fully realize its malicious potential, making complete analysis within a sandbox challenging. Finally, the effectiveness of sandboxing depends heavily on the quality and up-to-dateness of the sandbox’s detection engines and its ability to emulate a realistic environment.
Cloud Security Information and Event Management (SIEM) Solutions
SIEM solutions aggregate and analyze security logs from various sources within the cloud environment, providing a centralized view of security events. Different SIEM solutions offer varying capabilities and features, including log aggregation, threat detection, security information and event correlation, and reporting. Some are cloud-native, offering seamless integration with cloud environments and optimized for scalability, while others are on-premises solutions that can be integrated with cloud environments through APIs.
The choice depends on factors such as budget, existing infrastructure, and the level of sophistication required. For example, a smaller CSP might benefit from a cloud-native SIEM with basic threat detection, while a larger CSP with complex infrastructure might require a more comprehensive solution with advanced analytics and machine learning capabilities. A key difference lies in their approach to data analysis: some rely primarily on signature-based detection, while others incorporate more advanced techniques like anomaly detection and user and entity behavior analytics (UEBA).
Cloud Access Security Broker (CASB) Features for Malware Prevention
A robust CASB acts as a security intermediary between users and cloud applications, providing visibility and control over cloud traffic. Key features for malware prevention include data loss prevention (DLP) capabilities to prevent the exfiltration of sensitive data, malware scanning of files uploaded to cloud applications, and granular access control to limit the impact of a successful compromise. A strong CASB also provides real-time monitoring and alerting for suspicious activities, enabling quick response to potential threats.
CASBs can integrate with various cloud platforms and applications, offering centralized management and comprehensive visibility across the cloud environment. For example, a CASB can enforce policies that block access to malicious websites or prevent the download of infected files. The ability to integrate with other security tools, such as SIEM, enhances the overall security posture by enabling a more holistic approach to threat detection and response.
Machine Learning and AI in Advanced Malware Detection and Response
Machine learning (ML) and artificial intelligence (AI) are increasingly vital in detecting and responding to advanced malware threats. These technologies can analyze vast amounts of data to identify patterns and anomalies indicative of malicious activity, surpassing the capabilities of traditional signature-based detection methods. AI-powered solutions can learn from past attacks and adapt to new threats, providing more effective protection against evolving malware.
For example, an AI-powered system might identify a previously unseen malware variant based on its unusual network behavior or file characteristics. These systems can also automate incident response, accelerating the containment and remediation of malware infections. This reduces the manual effort required and minimizes the impact of an attack. However, it’s important to note that ML/AI models require significant amounts of training data and ongoing maintenance to remain effective.
The accuracy of these models also depends on the quality and relevance of the data used for training.
Regulatory Compliance and Best Practices

Navigating the complex landscape of cloud security requires a robust understanding and adherence to relevant regulations and best practices. For CSPs, this is paramount, not only for maintaining client trust but also for avoiding hefty fines and reputational damage. Meeting compliance standards demonstrates a commitment to security and strengthens your position in the market.The importance of regulatory compliance cannot be overstated.
Failure to comply can lead to data breaches, financial penalties, and legal repercussions. Proactive compliance, therefore, is a crucial element of a successful cloud security strategy. This involves understanding the specific regulations that apply to your operations and implementing measures to ensure ongoing adherence.
Relevant Industry Standards and Regulatory Frameworks
Several key industry standards and regulatory frameworks provide a baseline for securing cloud environments. These frameworks offer guidance on security controls, risk management, and compliance procedures. Understanding and implementing these standards is critical for CSPs. Examples include ISO 27001, which focuses on information security management systems, and the NIST Cybersecurity Framework, which provides a voluntary framework for managing cybersecurity risk.
Other relevant frameworks include HIPAA (for healthcare data), PCI DSS (for payment card data), and GDPR (for personal data in Europe). Each framework offers specific requirements that CSPs must meet depending on the type of data they handle and the jurisdictions they operate in.
Compliance Checklist for CSPs
A comprehensive compliance checklist is essential for ensuring ongoing adherence to relevant regulations. This checklist should be regularly reviewed and updated to reflect changes in regulations and best practices. The checklist should cover areas such as:
- Data security policies and procedures: Documentation of policies related to data encryption, access control, and data loss prevention.
- Risk assessments and management: Regular risk assessments to identify and mitigate potential threats.
- Incident response plan: A documented plan for handling security incidents, including data breaches.
- Vendor risk management: Assessing the security posture of third-party vendors.
- Employee training and awareness: Regular security awareness training for all employees.
- Auditing and monitoring: Regular audits and monitoring of security controls.
- Compliance certifications: Pursuing relevant certifications such as ISO 27001 or SOC 2.
This checklist provides a framework; the specific requirements will vary depending on the applicable regulations and the CSP’s specific services.
Security Awareness Training Program for CSP Staff
A well-structured security awareness training program is crucial for mitigating insider threats and fostering a security-conscious culture within the organization. This program should be tailored to the specific roles and responsibilities of employees and should include regular updates to reflect emerging threats and best practices.The program should cover topics such as:
- Phishing and social engineering: Educating employees on how to identify and avoid phishing attacks and social engineering tactics.
- Password security: Best practices for creating and managing strong passwords.
- Data security policies: Understanding and adhering to the organization’s data security policies.
- Incident reporting: Procedures for reporting security incidents.
- Physical security: Protecting company assets and data from physical threats.
The training should utilize a variety of methods, including interactive modules, simulations, and regular quizzes to ensure employee engagement and knowledge retention. Regular refresher training is also essential to keep employees up-to-date on the latest threats and best practices. For example, a scenario-based training module could simulate a phishing email, allowing employees to practice identifying and reporting suspicious emails in a safe environment.
This hands-on approach is far more effective than simply presenting information passively.
Securing the Cloud Supply Chain
The cloud isn’t an island; it’s intricately connected to a vast network of third-party vendors, each contributing components, services, and expertise. This interconnectedness, while enabling agility and innovation, introduces significant security risks. A single compromised vendor can create a domino effect, jeopardizing the entire cloud ecosystem and exposing sensitive customer data. Understanding and mitigating these risks is paramount for Cloud Service Providers (CSPs) aiming to maintain a robust and trustworthy cloud environment.The reliance on third-party vendors expands the attack surface, introducing vulnerabilities that might otherwise be absent in a purely in-house system.
These vendors could be responsible for anything from infrastructure components and software libraries to security tools and managed services. A compromised vendor could introduce malware, backdoors, or other malicious code into the CSP’s infrastructure, leading to data breaches, service disruptions, and reputational damage. The financial implications can also be severe, including legal repercussions, loss of customer trust, and significant financial penalties.
Third-Party Vendor Risk Assessment and Management
Effective third-party vendor management begins with a rigorous assessment process. CSPs should establish clear criteria for selecting vendors, including security certifications (like ISO 27001), adherence to industry best practices, and a demonstrable track record of security. Due diligence should encompass reviewing the vendor’s security policies, procedures, and incident response plans. Regular audits and penetration testing of vendor systems are also crucial to identify and address vulnerabilities proactively.
Ongoing monitoring and continuous assessment are vital to ensure that vendors maintain their security posture over time. This includes tracking their security incidents and evaluating their responsiveness to security threats. Contracts should include clear security obligations and consequences for non-compliance.
Secure Software Development Lifecycle (SDLC) Practices
A robust and secure SDLC is crucial not only for the CSP itself but also for its partners. This involves integrating security into every phase of software development, from design and coding to testing and deployment. This includes practices like code reviews, static and dynamic analysis, penetration testing, and secure coding guidelines. Collaboration with vendors on secure coding practices and the implementation of security automation tools can significantly improve the overall security posture.
Regular security training for developers and engineers is also essential to foster a security-conscious culture throughout the entire supply chain. The adoption of DevSecOps principles, integrating security into the DevOps pipeline, further streamlines this process and ensures continuous security validation.
Best Practices for Securing Cloud Infrastructure Against Supply Chain Attacks
The importance of proactive measures to protect against supply chain attacks cannot be overstated. Implementing the following best practices can significantly reduce the risk:
- Regular Vulnerability Scanning and Penetration Testing: Proactively identify and remediate vulnerabilities in both your own infrastructure and that of your third-party vendors.
- Strong Access Control and Authentication: Implement multi-factor authentication (MFA) and least privilege access controls to limit the impact of compromised credentials.
- Software Inventory Management: Maintain a comprehensive inventory of all software components and libraries used in your cloud environment, including those from third-party vendors. This allows for timely patching and updates.
- Secure Configuration Management: Ensure that all cloud infrastructure components are configured securely according to best practices and industry standards. Automate this process wherever possible.
- Incident Response Planning: Develop and regularly test a comprehensive incident response plan that includes procedures for handling supply chain attacks. This plan should cover containment, eradication, recovery, and post-incident analysis.
- Continuous Monitoring and Logging: Implement robust monitoring and logging capabilities to detect suspicious activity and potential security breaches. Utilize Security Information and Event Management (SIEM) systems to correlate events and identify threats.
- Regular Security Audits: Conduct regular security audits of your cloud infrastructure and the services provided by your third-party vendors. These audits should assess compliance with security policies and identify areas for improvement.
- Vendor Due Diligence and Contractual Agreements: Thoroughly vet all third-party vendors and include strong security clauses in your contracts. This should include requirements for security certifications, regular audits, and incident reporting.
Monitoring and Threat Intelligence
In the dynamic landscape of cloud security, continuous monitoring and leveraging threat intelligence are not just best practices—they’re essential for survival. Failing to actively monitor your cloud environment and stay informed about emerging threats leaves your CSP vulnerable to sophisticated attacks and costly breaches. This section explores the critical role of these elements in mitigating malware hosting risks.Continuous monitoring acts as the ever-watchful eye, constantly scanning for anomalies and suspicious activities within your cloud infrastructure.
By analyzing logs, network traffic, and security events in real-time, you can detect threats early, minimizing their impact. Integrating threat intelligence feeds enhances this process by providing context and predictive capabilities, allowing you to proactively defend against known vulnerabilities and emerging attack vectors before they can exploit your systems.
Continuous Monitoring for Threat Detection
Continuous monitoring is the backbone of a robust cloud security strategy. It involves the automated and ongoing collection and analysis of data from various sources within your cloud environment. This includes security information and event management (SIEM) systems, cloud access security brokers (CASBs), and other security tools. The goal is to identify deviations from established baselines and detect any unusual activity that might indicate a security breach or malware infection.
Robust cloud security strategies are crucial for CSPs to prevent becoming unwitting malware hosts. Building secure applications is key, and that’s where efficient development processes come in; check out this article on domino app dev the low code and pro code future for insights into faster, more secure app creation. Ultimately, secure development practices directly impact a CSP’s ability to mitigate malware hosting risks within their cloud infrastructure.
For example, a sudden surge in network traffic from an unexpected source, unusual login attempts from unfamiliar locations, or unauthorized access to sensitive data are all potential red flags that require immediate investigation. Effective monitoring relies on the establishment of clear baselines, the use of automated alerting systems, and a well-defined process for investigating and responding to alerts.
Integrating Threat Intelligence Feeds
Threat intelligence feeds provide invaluable context to your security monitoring efforts. These feeds, often obtained from commercial vendors, open-source intelligence (OSINT) communities, or government agencies, deliver up-to-the-minute information on emerging threats, malware campaigns, and attack techniques. By integrating these feeds into your security information and event management (SIEM) system, you can enrich your security logs with contextual information.
This allows for more accurate threat detection and faster response times. For example, if your SIEM detects a suspicious connection attempt from an IP address known to be associated with a malicious botnet (as identified by a threat intelligence feed), you can immediately block that IP address and prevent a potential attack.
Analyzing Security Logs and Identifying Suspicious Activity
Analyzing security logs is a crucial step in identifying suspicious activity. Security logs contain a wealth of information about events occurring within your cloud environment. These logs need to be meticulously examined for patterns and anomalies that could indicate malicious activity. This involves searching for s associated with malware, unusual login attempts, data exfiltration attempts, or unauthorized access to sensitive resources.
Tools such as SIEM systems can automate this process, enabling you to efficiently analyze large volumes of log data and identify potential threats. Furthermore, advanced analytics techniques like machine learning can be employed to identify subtle anomalies that might otherwise go unnoticed. For example, an unusual increase in file downloads from a specific server, particularly if those files are known malware samples, warrants immediate investigation.
Key Performance Indicators (KPIs) for Cloud Security
Measuring the effectiveness of your cloud security strategies requires establishing key performance indicators (KPIs). These KPIs provide quantifiable metrics that allow you to assess the effectiveness of your security measures and identify areas for improvement.
| KPI | Description | Target | Measurement Method |
|---|---|---|---|
| Mean Time To Detect (MTTD) | Average time taken to detect a security incident. | < 24 hours | SIEM logs, incident response reports |
| Mean Time To Respond (MTTR) | Average time taken to respond to a security incident. | < 4 hours | Incident response reports, ticketing systems |
| False Positive Rate | Percentage of alerts that are not actual security incidents. | < 10% | SIEM logs, security analyst reports |
| Number of Security Incidents | Total number of security incidents detected within a given period. | Decreasing trend | SIEM logs, incident response reports |
Final Review: Securing The Cloud Strategies For Csps To Mitigate Malware Hosting Risks
Ultimately, securing cloud strategies for CSPs against malware requires a holistic approach. It’s a continuous journey, not a destination, demanding constant vigilance, adaptation, and a proactive mindset. By combining robust security architectures, proactive threat hunting, and a well-defined incident response plan, CSPs can significantly reduce their risk exposure and maintain the trust of their clients. Investing in security isn’t just a cost; it’s an investment in the long-term health and success of your business, ensuring a secure and reliable cloud experience for everyone.
Question Bank
What are some common malware types that target CSPs?
Ransomware, cryptojackers, botnets, and data-exfiltration malware are common threats. Each presents unique challenges and requires specific mitigation strategies.
How can CSPs educate their employees about cloud security?
Regular security awareness training, phishing simulations, and clear security policies are crucial. Emphasis should be placed on recognizing and reporting suspicious activities.
What is the role of threat intelligence in cloud security?
Threat intelligence provides valuable insights into emerging threats, allowing CSPs to proactively adapt their security posture and prioritize mitigation efforts. This can involve subscribing to threat feeds and actively monitoring security news.
How frequently should security audits be performed?
Regular security audits, ideally at least annually, are necessary to identify vulnerabilities and ensure compliance. The frequency may need to increase depending on risk assessment and regulatory requirements.