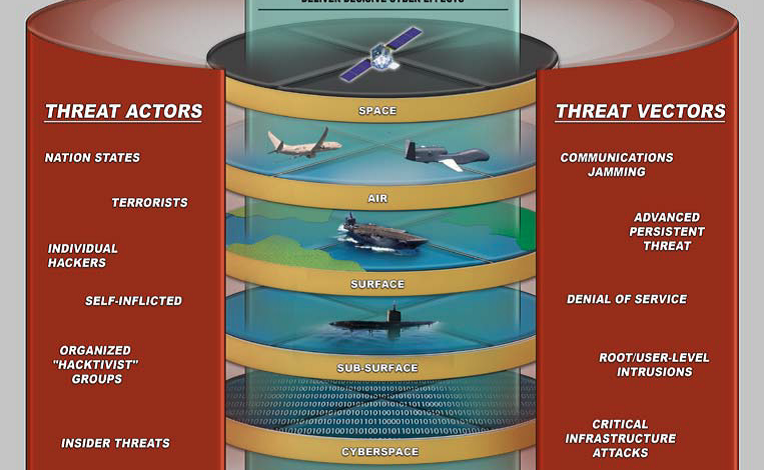
Critical US Navy Information Spilled in Cyber Attack
Critical US Navy information spilled in cyber attack: The chilling reality of a successful cyberattack against the US Navy is a scenario that keeps cybersecurity experts up at night. Imagine the potential fallout: sensitive operational data compromised, personnel records exposed, and vital navigational secrets in the wrong hands. This isn’t just a theoretical threat; it’s a stark reminder of our increasingly vulnerable digital landscape and the potential for catastrophic consequences.
This post delves into the potential nature of the spilled information, exploring the various types of data that could be compromised, from highly classified operational plans to the personal details of naval personnel. We’ll examine the potential actors behind such an attack, considering both state-sponsored adversaries and sophisticated cybercriminal groups. We’ll then analyze the immediate and long-term impact, examining the US Navy’s response mechanisms and exploring crucial preventative measures for the future.
Prepare for a deep dive into a chillingly realistic scenario.
The Nature of the Spilled Information
A hypothetical cyberattack against the US Navy could result in the compromise of a wide range of sensitive information, leading to significant operational and national security implications. The potential consequences extend beyond simple data breaches; they encompass the erosion of trust, the disruption of military operations, and the potential for significant reputational damage. Understanding the nature of this potentially compromised information is crucial for assessing the full extent of the risk.
Types of Compromised Information
The types of information potentially compromised in a hypothetical US Navy cyberattack are multifaceted and range from highly sensitive operational data to seemingly innocuous personnel details. The consequences of such a breach can be far-reaching and devastating. The severity of the impact depends heavily on the type of information exposed and the hands it falls into.
Impact of Sensitive Operational Data Loss, Critical us navy information spilled in cyber attack
The loss of sensitive operational data could severely compromise US Navy capabilities. This data might include details about ship deployments, submarine patrol routes, communication protocols, and tactical strategies. The unauthorized disclosure of such information could allow adversaries to anticipate naval movements, exploit vulnerabilities in communication systems, or even launch targeted attacks against specific vessels or personnel. For example, the revelation of a planned naval exercise could allow an adversary to position themselves for an ambush or to conduct reconnaissance operations.
The recent critical US Navy information spill, a stark reminder of our vulnerability, highlights the urgent need for robust cybersecurity. Building secure applications is key, and that’s where understanding the power of modern development comes in, like what’s discussed in this insightful article on domino app dev the low code and pro code future. Ultimately, strengthening our digital defenses requires a multi-pronged approach, including secure app development practices, to prevent future breaches of sensitive data like the Navy incident.
The impact extends beyond immediate tactical disadvantages; it could also erode the element of surprise, a critical component of naval warfare.
Consequences of Personnel Information Release
The release of personnel information, including names, addresses, family details, and medical records, poses a significant risk to US Navy personnel and their families. This information could be used for identity theft, targeted harassment, or even physical attacks. Furthermore, the disclosure of sensitive personal data could damage morale and trust within the Navy, hindering operational effectiveness. Consider the potential impact on a sailor whose family’s location is exposed, making them vulnerable to threats.
This compromises their safety and potentially their ability to perform their duties effectively.
Examples of Vulnerable Navigational Data
Sensitive navigational data, such as detailed charts of harbors, underwater topography, and precise coordinates of naval bases, could be among the most critical pieces of information compromised. This data is essential for safe navigation and effective military operations. The disclosure of such information could enable adversaries to plan attacks against US Navy vessels or bases, or to impede their ability to navigate safely in contested waters.
For instance, knowledge of precise depths in a particular harbor could allow an adversary to target a ship during transit. The precise location of sonar buoys or underwater communication cables could be equally damaging.
Classification Levels of Compromised Data
The following table illustrates the varying classification levels of potentially compromised data, ranging from unclassified to top secret:
| Classification Level | Description | Example | Potential Impact of Compromise |
|---|---|---|---|
| Top Secret | Information whose unauthorized disclosure could cause exceptionally grave damage to national security. | Detailed plans for a major naval operation. | Catastrophic operational failure, significant loss of life, severe damage to national security. |
| Secret | Information whose unauthorized disclosure could cause serious damage to national security. | Detailed specifications of a new naval weapon system. | Significant operational setbacks, potential loss of life, substantial damage to national security. |
| Confidential | Information whose unauthorized disclosure could cause damage to national security. | Personnel records containing sensitive personal information. | Compromised operational security, potential harm to personnel, damage to national security. |
| Unclassified | Information whose unauthorized disclosure would not cause damage to national security. | Publicly available information about Navy ships. | Minimal impact, potential for embarrassment or misinformation. |
Attribution and Actors Involved

Pinpointing the perpetrators behind a sophisticated cyberattack against the US Navy is a complex undertaking, requiring meticulous analysis of the attack vectors, malware used, and the overall operational security demonstrated by the attackers. The scale and nature of the data breach suggest a highly capable actor with significant resources and expertise. This points towards a few likely profiles.
Several factors need to be considered when attempting attribution. These include the technical sophistication of the attack, the specific data targeted, the geopolitical context, and the potential motivations of various actors. We’ll examine the capabilities and likely motivations of both state-sponsored and non-state actors.
Potential State-Sponsored Actors
State-sponsored actors, often operating under the guise of advanced persistent threats (APTs), possess the resources, expertise, and motivation to conduct such a large-scale operation. Countries with a history of targeting US military and intelligence infrastructure, such as Russia, China, and Iran, are prime suspects. Their intelligence agencies are known to employ highly skilled cyber warfare units capable of penetrating deeply entrenched defense systems.
For instance, the Russian GRU is known for its involvement in disruptive cyber operations targeting critical infrastructure worldwide, while the Chinese Ministry of State Security (MSS) has a long history of intellectual property theft and strategic espionage. Iran’s Islamic Revolutionary Guard Corps (IRGC) has also demonstrated capabilities in conducting cyberattacks against Western targets. The level of sophistication required to successfully breach US Navy systems suggests an actor with a dedicated cyber warfare program and significant financial backing, aligning with the capabilities of these state-sponsored groups.
Potential Non-State Actors
While less likely to possess the same level of resources as state-sponsored actors, highly skilled non-state actors, such as sophisticated cybercriminal groups, also cannot be ruled out. Groups like APT29 (Cozy Bear) and APT32 (OceanLotus), although sometimes linked to state actors, have demonstrated the capacity to carry out complex attacks targeting sensitive information. These groups often operate for financial gain, but their capabilities could be leveraged by state actors for geopolitical objectives.
The financial incentive for such a data breach could be immense, especially if the stolen information can be sold on the dark web or used for blackmail. However, the specificity of the stolen data suggests a higher likelihood of state-sponsored involvement, given the limited financial gain compared to the resources required for such a sophisticated attack.
Methods of Infiltration
The attackers likely employed a multi-stage infiltration strategy, exploiting vulnerabilities in US Navy systems and leveraging social engineering techniques. This might have involved phishing campaigns targeting personnel with privileged access, exploiting zero-day vulnerabilities in software, or using malware to gain persistent access to the network. Advanced techniques like supply chain attacks, where malicious code is introduced into legitimate software, are also a strong possibility.
Once inside the network, lateral movement would be employed to gain access to the specific databases containing the sensitive information. The attackers likely used sophisticated tools and techniques to mask their activity and evade detection.
Motivations for Targeting the US Navy
The motivations behind the attack could be multifaceted. For state-sponsored actors, the primary goal might be espionage, seeking to gain insights into US Navy operations, capabilities, and strategies. This intelligence could be used to inform military planning, develop countermeasures, or even compromise future operations. Alternatively, the goal could be sabotage or disruption, aiming to degrade the operational readiness of the US Navy.
For non-state actors, the motivation might be primarily financial, aiming to sell the stolen data to the highest bidder, or to use it for blackmail or extortion. However, the scale and sophistication of the attack strongly suggest that espionage and strategic advantage are more likely primary motivators.
Comparison of Threat Actor Capabilities
State-sponsored actors generally possess superior capabilities compared to non-state actors. They have access to more advanced tools, more extensive resources, and a higher degree of operational security. Their attacks tend to be more sophisticated, persistent, and targeted. Non-state actors may have the technical skills to carry out complex attacks, but they often lack the resources and organizational structure to execute such a large-scale operation with the same level of stealth and sophistication as a state-sponsored group.
This disparity in capabilities makes a state-sponsored actor a more likely candidate for the US Navy cyberattack.
Impact and Response
The cyberattack against the US Navy, resulting in the leak of critical information, carries profound and multifaceted consequences, impacting immediate operational readiness and long-term strategic planning. The severity of the breach necessitates a swift and comprehensive response, involving a multi-layered approach encompassing immediate damage control, long-term security enhancements, and potential retaliatory measures. The ripple effects of this incident will be felt across various levels of naval operations for years to come.
The recent cyber attack resulting in the spill of critical US Navy information is a stark reminder of how vulnerable even the most secure organizations can be. This incident highlights the urgent need for robust security measures, and understanding solutions like those offered by bitglass and the rise of cloud security posture management becomes crucial. Strengthening cloud security is no longer optional; it’s essential to prevent future breaches and protect sensitive data from falling into the wrong hands.
Immediate Operational Consequences
The immediate impact of the data breach includes compromised operational security. The leaked information, depending on its nature (e.g., deployment schedules, communication protocols, technological vulnerabilities), could directly affect ongoing naval operations. This could range from the need to immediately alter deployment plans to mitigate potential threats, to the scrambling of communication systems to prevent further exploitation. For example, the exposure of a new sonar technology’s specifications might necessitate its immediate decommissioning or redesign, causing significant disruption and resource expenditure.
The compromised information could also provide adversaries with crucial intelligence, enabling them to better target US naval assets and personnel. This might lead to a period of heightened alert and defensive measures, impacting training schedules and resource allocation.
Long-Term Strategic Implications for US Naval Operations
The long-term implications extend beyond immediate operational disruptions. The loss of trust in existing security protocols, the potential for further exploitation of vulnerabilities, and the erosion of strategic advantage will require significant investment in both technological and human resources. The incident will likely prompt a reassessment of cybersecurity protocols and investment in more robust defensive systems. This could lead to delays in new technology deployments as security audits and risk assessments become more stringent.
Furthermore, the damage to the US Navy’s reputation as a technologically superior force could have broader geopolitical consequences, potentially influencing the strategic calculations of allies and adversaries alike. For instance, a loss of confidence in US naval capabilities might embolden potential adversaries to engage in more aggressive actions.
US Navy Response Mechanisms
The US Navy’s response to such a cyberattack would involve a coordinated effort across various departments. This would include immediate containment of the breach to prevent further data exfiltration, forensic investigation to identify the extent and nature of the compromise, and the implementation of enhanced security measures. This also involves working closely with cybersecurity firms, intelligence agencies, and international partners to identify the perpetrators and coordinate a response.
Furthermore, the Navy would need to conduct a thorough review of its security protocols, identify vulnerabilities, and implement corrective measures to prevent future attacks. This could involve upgrading existing systems, retraining personnel, and implementing new security technologies. Finally, the Navy may consider retaliatory measures, depending on the attribution of the attack and the severity of the damage.
Hypothetical Response Protocol
A hypothetical response protocol could unfold as follows:
1. Incident Detection and Containment
Immediate detection of the breach triggers an emergency response team. The affected systems are isolated to prevent further data exfiltration.
2. Forensic Investigation
A dedicated team conducts a forensic analysis to determine the extent of the breach, the type of data compromised, and the attack vector.
3. Damage Assessment
The severity of the impact on operations and national security is assessed.
4. Vulnerability Remediation
System vulnerabilities are identified and patched, and security protocols are strengthened.
5. Attribution and Response
Efforts are made to identify the perpetrators. Depending on attribution, legal and potentially retaliatory actions are considered.
6. Public Communication
A carefully crafted public statement is released, balancing transparency with the need to protect sensitive information.
7. Long-Term Security Enhancement
A comprehensive review of security protocols is undertaken, leading to significant investments in cybersecurity infrastructure and training.
Decision-Making Process Flowchart
[Imagine a flowchart here. The flowchart would begin with “Incident Detection,” branching into “Containment,” “Forensic Investigation,” and “Initial Damage Assessment.” Each of these would lead to further branches, such as “Attribution,” “Vulnerability Remediation,” “Response Strategy (Defensive/Offensive),” and “Public Communication.” The flowchart would illustrate the iterative and interdependent nature of the decision-making process, showing feedback loops and decision points based on the evolving situation.] The flowchart would visually represent the dynamic interplay between immediate responses and long-term strategic considerations, highlighting the crucial role of information sharing and collaboration across various agencies and departments.
Preventive Measures and Future Security
The recent cyberattack highlighting the vulnerability of US Navy information systems underscores the urgent need for comprehensive improvements in cybersecurity infrastructure and practices. Strengthening defenses requires a multi-pronged approach encompassing technological advancements, enhanced intelligence gathering, rigorous personnel training, and the adoption of robust security best practices. Failing to address these vulnerabilities leaves the Navy susceptible to further attacks, potentially compromising national security and operational capabilities.
Strengthening Cybersecurity Infrastructure
The US Navy must invest heavily in modernizing its IT infrastructure. This includes transitioning to zero-trust security architectures, which assume no user or device is inherently trustworthy and verifies every access request. Implementing robust intrusion detection and prevention systems, coupled with advanced threat intelligence platforms, is crucial for identifying and mitigating cyber threats in real-time. Regular security audits and penetration testing can identify vulnerabilities before malicious actors exploit them.
Furthermore, a move towards cloud-based solutions, when appropriately secured, can offer scalability and enhanced security features compared to legacy systems. The successful implementation of these measures requires significant funding and collaboration between various naval departments.
The Role of Enhanced Intelligence Gathering
Proactive intelligence gathering is vital in preventing future attacks. This involves actively monitoring online forums, dark web marketplaces, and other digital spaces frequented by cybercriminals to identify potential threats before they materialize. Collaboration with domestic and international intelligence agencies is crucial in sharing threat information and coordinating responses. Advanced techniques like threat modeling, which involves identifying potential vulnerabilities in systems and processes, should be employed to anticipate attack vectors and develop countermeasures.
Real-time analysis of network traffic and system logs can also provide early warnings of suspicious activity. The success of these efforts relies on the integration of human intelligence with advanced analytical tools.
Technological Advancements in Naval Cybersecurity
Several technological advancements can significantly bolster naval cybersecurity. Artificial intelligence (AI) and machine learning (ML) can automate threat detection and response, identifying anomalies and malicious activities that might escape human detection. Blockchain technology can enhance data security and integrity by creating immutable records of sensitive information. Quantum-resistant cryptography is crucial in preparing for the potential threat of quantum computers breaking current encryption methods.
Implementing multi-factor authentication (MFA) across all systems, coupled with robust access control measures, reduces the risk of unauthorized access. The effective deployment of these technologies requires skilled personnel capable of managing and maintaining these complex systems.
Personnel Training and Awareness Programs
Human error remains a significant vulnerability in any cybersecurity system. Comprehensive training programs for all naval personnel are essential to raise awareness of cyber threats and best practices. This includes regular security awareness training, phishing simulations to educate users about social engineering tactics, and hands-on training in secure coding practices. Emphasis should be placed on fostering a security-conscious culture where personnel understand their roles in protecting sensitive information.
Regular updates and refresher courses are vital to keep personnel abreast of evolving threats and technologies. Investing in robust cybersecurity training is not just cost-effective but is essential for building a resilient workforce.
Best Practices for Securing Sensitive Naval Information
The effective protection of sensitive naval information relies on the consistent application of several key best practices:
- Implement strong password policies and encourage the use of password managers.
- Regularly update software and operating systems to patch known vulnerabilities.
- Segment networks to limit the impact of breaches.
- Employ data loss prevention (DLP) tools to monitor and prevent sensitive data from leaving the network.
- Conduct regular security audits and penetration testing to identify vulnerabilities.
- Establish clear incident response plans to effectively manage and mitigate cyberattacks.
- Encrypt all sensitive data both in transit and at rest.
- Develop and enforce strict access control policies based on the principle of least privilege.
- Implement robust monitoring and logging capabilities to track system activity and detect anomalies.
- Foster a culture of security awareness and responsibility among all personnel.
Illustrative Scenarios
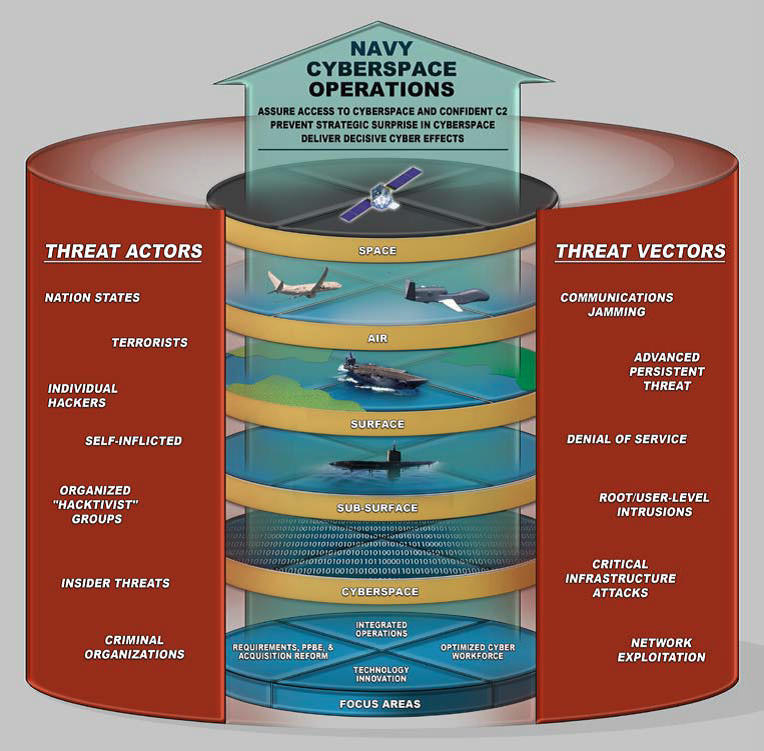
This section details hypothetical scenarios illustrating the ramifications of a successful cyberattack against US Navy systems, focusing on the visual aspects of a compromised infrastructure. These scenarios are not based on any specific real-world incident but rather serve to highlight the potential consequences of such attacks.
Successful Cyberattack and Ramifications
Imagine a sophisticated phishing campaign targeting high-ranking Navy personnel. The attackers, a state-sponsored group with advanced capabilities, craft emails mimicking official Navy communications, containing malware disguised as legitimate attachments. Several officers fall victim, unknowingly installing the malware onto their secure workstations. This malware grants the attackers initial access, which they then leverage to move laterally across the network, gaining control of sensitive databases and communication systems.
The consequences include the theft of highly classified information pertaining to naval operations, strategic deployments, and technological advancements. This breach could compromise national security, expose sensitive intelligence, and significantly disrupt naval operations. Furthermore, the attackers could use the stolen information to conduct further attacks, such as launching targeted ransomware attacks or manipulating critical systems. The resulting damage could cost billions in financial losses and severely damage national security and international relations.
Visual Depiction of a Compromised Server Room Under Attack
The server room is dimly lit, emergency lights flickering erratically. Rows of servers hum with an unnatural intensity, their cooling fans working overtime. Red and amber warning lights flash incessantly on the front panels of numerous machines. On the main console, lines of cryptic code scroll rapidly, interspersed with error messages in various colors. The air is thick with the smell of ozone and overheating electronics.
Several technicians frantically work at consoles, their faces illuminated by the harsh glow of the screens. A low, rhythmic beeping sound emanates from one particular server rack, growing louder and more insistent. On the floor, discarded cables and tools lie scattered amidst spilled coffee and the remnants of hastily eaten snacks. The scene conveys a palpable sense of urgency and chaos, reflecting the intense struggle to contain the cyberattack.
Visual Depiction of a Successful Infiltration of a Secure Network
Imagine a network map displayed on a large screen. Each node represents a server, workstation, or other network device, connected by lines depicting data flow. Initially, the map shows a calm, orderly network, with data flowing smoothly between nodes. As the attack progresses, certain nodes begin to glow red, indicating compromised systems. These red nodes start to spread across the network map, like a virus, rapidly infecting adjacent nodes.
The lines connecting the nodes begin to flicker and change color, representing disrupted communication channels. Data flow becomes erratic, with some connections completely severed. The overall image is one of escalating chaos and uncontrolled spread, visually representing the attackers’ successful infiltration and their ability to move laterally within the Navy’s network.
Visual Depiction of a Compromised Communication System
Picture a bustling communication center. Operators usually sit at their consoles, monitoring various communication channels. However, in this scenario, the screens display a chaotic jumble of static, garbled messages, and nonsensical data streams. Warning lights flash erratically, and the usual calm efficiency is replaced with confusion and frantic activity. Some communication channels are completely dead, while others are flooded with nonsensical messages or deliberate misinformation.
Operators are frantically trying to regain control, but their efforts are hampered by the overwhelming nature of the attack. The visual representation highlights the disruption and chaos caused by the compromised communication system, emphasizing the vulnerability of critical naval communication infrastructure to sophisticated cyberattacks.
Summary
The potential for a successful cyberattack against the US Navy to compromise critical information is a serious threat with far-reaching consequences. From the immediate disruption of naval operations to the long-term erosion of strategic advantage, the stakes are incredibly high. While the US Navy undoubtedly possesses robust cybersecurity measures, the constant evolution of cyber threats necessitates ongoing vigilance, technological advancements, and a commitment to robust personnel training.
The narrative presented here, while hypothetical, serves as a crucial wake-up call, highlighting the need for continuous improvement and proactive defense against the ever-present danger of sophisticated cyberattacks.
Key Questions Answered: Critical Us Navy Information Spilled In Cyber Attack
What types of data are most vulnerable in a US Navy cyberattack?
Highly sensitive data like operational plans, ship locations, personnel identities, communication codes, and advanced weapons systems information are all prime targets.
How could a cyberattack impact US Navy morale?
A breach could severely damage morale, especially if personnel data is leaked or if the attack reveals vulnerabilities in security protocols, leading to distrust and anxiety.
What role does human error play in these attacks?
Phishing scams, weak passwords, and a lack of security awareness among personnel are common entry points for attackers, highlighting the crucial role of training and education.
What international treaties or agreements address this kind of cyber warfare?
While no single treaty specifically addresses all aspects, various international agreements touch upon aspects of cyber warfare, data protection, and state responsibility, but enforcement and interpretation remain challenging.