Software Bill of Materials Managing Build Tools
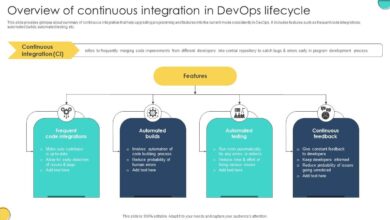
Software Bill of Materials managing build tools: It sounds technical, right? But trust me, understanding how SBOMs work with your build process is crucial, especially in today’s complex software landscape. Think of an SBOM as a detailed ingredient list for your software – it tells you exactly what components went into building your application, from libraries and frameworks to even the tiniest dependencies.
This transparency is key for security, compliance, and even just good old-fashioned maintainability. We’ll dive into how different build tools handle SBOMs, the challenges you might face, and how to integrate them seamlessly into your workflow.
This post will walk you through everything from defining an SBOM and exploring popular build tools like Maven, Gradle, and npm, to managing SBOMs throughout your entire software development lifecycle (SDLC). We’ll examine the security implications, explore future trends, and even work through a practical example to solidify your understanding. Get ready to level up your software development game!
Defining Software Bill of Materials (SBOM) in the Context of Build Tools
Software Bill of Materials (SBOMs) are becoming increasingly crucial in software development, especially when dealing with the complexities introduced by modern build tools. An SBOM, in essence, provides a comprehensive inventory of all the software components used in a project, detailing their versions, licenses, and relationships. This detailed inventory is critical for security, compliance, and maintainability. Understanding SBOMs in the context of build tools allows for better management of dependencies and improved software supply chain security.An SBOM’s core components include a formal description of the software, a list of its constituent parts (including libraries, frameworks, and other dependencies), and information about each component, such as its version, source, license, and checksum.
The SBOM also often includes relationships between these components, showing how they interact within the final software product. This detailed breakdown is crucial for traceability and vulnerability management.
SBOM and Build Reproducibility
A key aspect of leveraging SBOMs is their direct contribution to build reproducibility. A well-defined SBOM, generated during the build process, acts as a blueprint for recreating the exact software build. By specifying the exact versions of all components, including the build tool itself, an SBOM ensures that anyone can rebuild the software to an identical state. This is vital for ensuring consistent behavior across different environments and preventing discrepancies between development, testing, and production deployments.
The reproducibility enabled by an SBOM significantly reduces the risk of unexpected behavior caused by variations in dependencies. For instance, if a security vulnerability is discovered in a specific version of a library, the SBOM immediately allows you to identify if that vulnerable version is used in your project and take appropriate action.
SBOM Formats
Several standardized formats exist for representing SBOMs, each with its own strengths and weaknesses. Two prominent examples are SPDX (Software Package Data Exchange) and CycloneDX. SPDX is a widely adopted standard that uses a flexible schema to describe software packages and their relationships. It supports various data representations, including XML, JSON, and tag-value lists. CycloneDX, on the other hand, is a lightweight and machine-readable format designed for ease of use and automation.
It’s often preferred for its simpler structure and better support for automated analysis tools. The choice of format often depends on the specific tools and workflows used within an organization.
Example SBOM using a Hypothetical Build Tool
Let’s imagine a simple Python project built using `buildozer`, a hypothetical build tool. The project uses the `requests` library (version 2.28.1) and the `beautifulsoup4` library (version 4.11.1). The `buildozer` tool itself is version 1.0.
0. A simplified SBOM in CycloneDX format might look like this (note
this is a simplified representation and a real SBOM would contain more metadata):“`xml
Popular Build Tools and Their SBOM Integration Capabilities: Software Bill Of Materials Managing Build Tools
Generating accurate and comprehensive Software Bills of Materials (SBOMs) is crucial for software supply chain security. Different build tools offer varying levels of support for SBOM generation, impacting the ease and effectiveness of this critical process. This post will explore the SBOM capabilities of three popular build tools: Maven, Gradle, and npm, highlighting their strengths and weaknesses.
Maven’s SBOM Generation Capabilities
Maven, a widely used Java build tool, has seen increasing integration with SBOM generation. While not directly built-in, plugins like the CycloneDX Maven Plugin provide seamless SBOM creation within the Maven build lifecycle. This plugin leverages the CycloneDX standard, a popular format for SBOMs, allowing for easy integration with various security tools and vulnerability databases. The plugin’s configuration is generally straightforward, allowing developers to specify the output format and location of the SBOM.
However, accurately capturing all transitive dependencies can sometimes be challenging, particularly with complex project structures. The effectiveness of the SBOM depends heavily on the accuracy of dependency information within the project’s `pom.xml` file.
Gradle’s SBOM Generation Capabilities
Similar to Maven, Gradle doesn’t natively support SBOM generation but relies on plugins. The CycloneDX Gradle Plugin offers comparable functionality to its Maven counterpart, allowing developers to generate SBOMs in the CycloneDX format. Gradle’s flexible plugin ecosystem and robust dependency management system can potentially lead to more comprehensive SBOMs, especially when dealing with multi-module projects or projects with complex dependency graphs.
However, proper configuration of the plugin is crucial for accurate SBOM generation. Misconfigurations or inconsistencies in the project’s dependency declarations can result in inaccurate or incomplete SBOMs.
npm’s SBOM Generation Capabilities
npm, the Node.js package manager, also lacks native SBOM generation. However, tools like `sbom-generator` can be integrated into the npm workflow to generate SBOMs. These tools typically leverage the package.json file and the npm registry to gather dependency information. The challenge with npm lies in the sheer volume and dynamic nature of its package ecosystem. Maintaining accurate and up-to-date dependency information, especially for packages with numerous nested dependencies, is critical for generating a comprehensive SBOM.
The lack of standardized metadata within npm packages can also lead to inaccuracies in the generated SBOM.
Best Practices for Integrating SBOM Generation into a Gradle CI/CD Pipeline
Integrating SBOM generation into a CI/CD pipeline ensures that SBOMs are created automatically with each build. Using Gradle, this can be achieved by adding the CycloneDX Gradle plugin to the project’s build script and configuring it to generate the SBOM as part of the build process. The generated SBOM can then be stored in an artifact repository or integrated with vulnerability scanning tools.
Automated SBOM generation in the CI/CD pipeline improves the speed and consistency of security analysis, reducing the risk of vulnerabilities making their way into production. For example, the SBOM could be automatically uploaded to a vulnerability scanning service like Snyk or Anchore, triggering a scan for known vulnerabilities.
Challenges in Generating Accurate and Comprehensive SBOMs
Generating accurate and comprehensive SBOMs across different build tools presents several challenges. These include: inconsistent dependency management practices across projects, the presence of indirect or transitive dependencies that are difficult to track, and the complexities of dealing with dynamically linked libraries or runtime dependencies. Furthermore, the lack of standardization across different SBOM formats can make it difficult to share and analyze SBOMs generated by different tools.
The accuracy of an SBOM is directly tied to the completeness and accuracy of the dependency information provided by the build tool and the project’s configuration. For instance, a missing or outdated dependency entry in a `pom.xml` or `build.gradle` file will result in an incomplete SBOM.
Impact of Dependency Management on SBOM Accuracy
Dependency management plays a pivotal role in SBOM accuracy. Robust dependency management ensures that all direct and transitive dependencies are accurately identified and included in the SBOM. However, issues such as shadowing, where multiple versions of the same dependency exist in the dependency tree, can complicate this process and lead to inaccuracies. Furthermore, the use of private or internal repositories can also pose challenges, as these repositories may not always provide the necessary metadata for SBOM generation.
Effective dependency management practices, including the use of dependency locking mechanisms and regular dependency audits, are crucial for generating accurate and reliable SBOMs. For example, utilizing tools that create a dependency graph visualization can help identify conflicts and inconsistencies in the dependency tree, which can then be addressed to improve SBOM accuracy.
Managing SBOMs Throughout the Software Development Lifecycle
Integrating Software Bills of Materials (SBOMs) into your software development lifecycle (SDLC) isn’t just a good idea; it’s becoming a necessity for security and compliance. This involves proactively generating and managing SBOMs at each stage, allowing for continuous tracking of components and their associated vulnerabilities. This proactive approach minimizes risks and ensures a more secure and compliant software delivery pipeline.
SBOM Generation and Integration Across SDLC Phases
A step-by-step guide to incorporating SBOM generation throughout the SDLC is crucial for effective vulnerability management and compliance. By integrating SBOM generation early and consistently, you build a comprehensive record of your software’s composition, enabling rapid response to security threats.
- Requirements Gathering and Design: While SBOM generation happens later, this initial phase sets the stage. Defining dependencies and outlining third-party libraries early aids in accurate SBOM creation. Understanding licensing requirements here prevents later compliance issues.
- Development and Implementation: As developers integrate libraries and dependencies, the build system should automatically generate an SBOM. This should be done frequently, perhaps with every commit or at least daily, to provide an up-to-date record.
- Testing and Quality Assurance: The SBOM is used during testing to identify vulnerabilities within components. Automated vulnerability scanning tools can leverage the SBOM to pinpoint weaknesses. This enables proactive patching and remediation.
- Deployment and Release: The SBOM should be included as part of the software release package. This allows downstream consumers (e.g., security teams, operations teams) to assess the security profile of the software before deployment.
- Maintenance and Updates: Ongoing monitoring and updates to the SBOM are vital. As new vulnerabilities are discovered or components are updated, the SBOM should reflect these changes. This ensures the SBOM remains a current and accurate representation of the software’s composition.
SBOM Management Tasks Across SDLC Stages
This table summarizes the key SBOM management tasks at each stage of the SDLC.
| SDLC Stage | SBOM Generation | Vulnerability Analysis | Compliance Checks |
|---|---|---|---|
| Requirements | Dependency identification and initial planning | Preliminary risk assessment based on chosen components | License review of planned components |
| Development | Automated SBOM generation with each build | Automated vulnerability scanning of dependencies | Automated license compliance checks |
| Testing | SBOM validation against test results | Targeted vulnerability testing based on SBOM findings | Verification of license compliance in the test environment |
| Deployment | SBOM inclusion in the release artifact | Final vulnerability scan before release | Final compliance check before release |
| Maintenance | SBOM updates with component changes | Continuous monitoring for new vulnerabilities | Regular license compliance audits |
Tracking Vulnerabilities Using SBOMs
An SBOM acts as a central repository of information about all components within a software system. When a vulnerability is discovered in a component listed in the SBOM, the impact can be immediately assessed. For example, if a vulnerability is reported in a specific version of a widely used library, and that version is listed in the SBOM, the development team can immediately determine if their software is affected.
This allows for rapid remediation and reduces the window of vulnerability exposure.
SBOMs and Software License Compliance
SBOMs play a crucial role in software license compliance. By clearly listing all components and their associated licenses, organizations can easily verify compliance with various open-source and commercial license agreements. This avoids potential legal issues and financial penalties associated with non-compliance. For instance, an SBOM clearly indicating the use of a GPL-licensed library will ensure the organization understands its obligations regarding open-sourcing any modifications or derivative works.
Security Implications and Vulnerability Management with SBOMs
Software Bill of Materials (SBOMs) are rapidly becoming essential for managing software security. They provide a comprehensive inventory of all components within a software system, allowing organizations to understand their software’s composition and identify potential vulnerabilities more effectively. This detailed understanding significantly improves the ability to proactively address security risks and enhance the overall security posture.SBOMs offer a powerful mechanism for identifying and mitigating security vulnerabilities.
By providing a clear picture of the components used, including their versions and licenses, SBOMs enable organizations to quickly identify components with known vulnerabilities. This contrasts sharply with the often opaque and time-consuming process of manually tracking dependencies. The speed and accuracy offered by SBOMs are crucial in today’s fast-paced threat landscape.
SBOM Usage for Improved Software Security Posture
Using an SBOM allows for proactive vulnerability identification. Organizations can leverage the SBOM to query known vulnerability databases (like the National Vulnerability Database – NVD) to check if any of their components have known security flaws. This allows for timely patching and mitigation before an exploit is even attempted. For instance, an SBOM might reveal that a specific version of a logging library used in the application has a critical vulnerability allowing for remote code execution.
This information enables immediate action to upgrade the library to a patched version, thus eliminating the vulnerability.
Integrating SBOM Data with Vulnerability Scanning Tools
Many vulnerability scanning tools now support integration with SBOM data. This integration streamlines the vulnerability assessment process. Instead of relying solely on black-box scanning techniques which can miss vulnerabilities, the SBOM provides a “white-box” view, allowing the scanner to focus its efforts on the specific components listed. This often leads to more accurate and efficient vulnerability detection, reducing false positives and improving the overall effectiveness of the security testing.
A typical integration might involve importing the SBOM into the scanner, which then cross-references the component information with its vulnerability database. The output would be a report detailing any vulnerabilities found within the identified components.
Facilitating Rapid Identification and Remediation of Security Flaws
The use of SBOMs significantly accelerates the identification and remediation of security flaws. When a new vulnerability is disclosed affecting a component listed in the SBOM, the affected software can be quickly identified. This allows for immediate patching or mitigation efforts. This rapid response significantly reduces the window of vulnerability, minimizing the risk of exploitation. For example, if a critical vulnerability is found in a widely used open-source library, organizations using that library can quickly determine if they are affected by checking their SBOMs.
Those affected can then prioritize updating the library to a secure version. This process, facilitated by SBOMs, reduces the response time from days or weeks to hours, significantly minimizing the risk.
Future Trends and Challenges in SBOM Management for Build Tools
The landscape of software development is rapidly evolving, driven by the increasing complexity of applications and the growing emphasis on security. This evolution presents both exciting opportunities and significant challenges for SBOM management within build tools. As we move forward, we’ll see a convergence of advanced technologies and refined practices aimed at streamlining SBOM creation, management, and utilization.
However, hurdles remain, particularly in handling the intricate nature of modern software architectures.
Emerging Trends in SBOM Management and Their Impact on Build Tools
Several key trends are shaping the future of SBOM management. The increasing adoption of automated SBOM generation directly within the CI/CD pipeline is a significant development. This automation reduces manual effort, improves accuracy, and ensures SBOMs are consistently generated for every build. Furthermore, the standardization of SBOM formats, particularly SPDX and CycloneDX, is facilitating interoperability between different tools and systems.
This interoperability is crucial for efficient SBOM sharing and analysis across the software supply chain. Another notable trend is the integration of SBOMs with vulnerability databases, enabling automated vulnerability detection and risk assessment. This proactive approach helps developers quickly identify and address security weaknesses in their software. Finally, the growing use of SBOMs for compliance purposes, driven by regulatory mandates like the EU’s Cybersecurity Act, is further solidifying their importance.
Challenges in Managing SBOMs for Complex, Microservice-Based Architectures
Managing SBOMs for complex systems, especially those based on microservices, poses unique challenges. The decentralized nature of microservices architectures, where multiple teams develop and deploy independent services, makes it difficult to maintain a comprehensive and accurate view of the entire software composition. Tracking dependencies across numerous microservices, each with its own set of libraries and components, requires robust mechanisms for aggregation and correlation of individual SBOMs.
The dynamic nature of microservice deployments, with frequent updates and deployments, also adds to the complexity. Maintaining up-to-date SBOMs for constantly evolving systems necessitates efficient mechanisms for automated updates and version control. The sheer volume of data generated by numerous microservices can also overwhelm existing SBOM management systems, requiring scalable and efficient solutions for storage and analysis.
For example, a large e-commerce platform with hundreds of microservices would struggle with manual SBOM aggregation, highlighting the need for automated solutions.
The Role of Automation in Simplifying SBOM Management
Automation plays a pivotal role in simplifying SBOM management. Automated SBOM generation, as previously mentioned, eliminates manual processes and reduces errors. Automated vulnerability scanning, integrated with SBOMs, enables proactive identification and remediation of security vulnerabilities. Automated SBOM updating, triggered by changes in the software composition, ensures SBOMs remain current and relevant. Furthermore, automated SBOM analysis and reporting tools can provide valuable insights into the software supply chain, facilitating risk management and compliance efforts.
Tools that integrate directly with CI/CD pipelines, automatically generating and updating SBOMs with each build, are crucial for achieving this level of automation. This reduces the manual intervention required and ensures consistency in the process.
Potential Future Improvements for SBOM Integration Within Build Tools
The integration of SBOMs within build tools can be significantly enhanced in several ways.
- Improved Accuracy and Completeness: Enhancements to algorithms and data sources to improve the accuracy and completeness of SBOMs, especially for complex dependencies and transitive dependencies. This would involve improved handling of dynamically linked libraries and other nuanced dependencies.
- Enhanced Support for Diverse Package Managers: Broader support for a wider range of package managers and build systems, ensuring compatibility across different development environments and languages.
- Integration with Vulnerability Databases and Threat Intelligence Feeds: Direct integration with up-to-date vulnerability databases and threat intelligence feeds to automatically assess the security risks associated with identified components.
- Improved SBOM Versioning and Management: Robust mechanisms for managing SBOM versions and tracking changes over time, ensuring traceability and accountability.
- Simplified SBOM Sharing and Collaboration: Streamlined mechanisms for sharing SBOMs securely and efficiently across teams and organizations, facilitating collaborative security analysis.
Illustrative Example: SBOM Generation and Analysis for a Simple Project
This example demonstrates SBOM generation and analysis for a small Node.js project using the `npm` package manager. We’ll walk through the process, highlighting key steps and potential vulnerabilities identified. This illustrative project will be a simple web server that uses a single external library for logging.
Imagine a visual representation of the SBOM generation process. The illustration starts with a central box labeled “Simple Node.js Project,” containing the project’s source code files (e.g., `server.js`, `index.html`). Arrows emanate from this box, pointing to two other boxes. One box is labeled “npm Package Manager,” representing the tool used to manage project dependencies. The other box is labeled “External Libraries,” containing a smaller box for each dependency (in this case, just one: a logging library like `winston`).
Lines connect each library box to the “npm Package Manager” box, illustrating the dependency relationships. Finally, an arrow leads from the “npm Package Manager” box to a final box labeled “SBOM (Software Bill of Materials),” which displays a structured representation of the project and its dependencies, including version numbers and other metadata.
SBOM Generation using npm
The process begins by installing the necessary logging library using npm: `npm install winston`. Once installed, we can generate the SBOM using a tool that integrates with npm. Many tools offer this functionality, either directly or via plugins. For this example, let’s assume a hypothetical tool called “SBOM-Generator” that integrates with npm. Running `sbom-generator –npm` would then analyze the `package.json` and `package-lock.json` files to create the SBOM in SPDX format (or another format, depending on the tool).
The resulting SBOM would be a structured file containing information about the project, its dependencies (winston), and the versions of each component. This structured data will be essential for the next phase of vulnerability analysis.
SBOM Analysis and Vulnerability Identification, Software bill of materials managing build tools
After generating the SBOM, we utilize a vulnerability scanning tool. This tool will take the SBOM as input and cross-reference the component versions listed within the SBOM against known vulnerability databases (like the National Vulnerability Database (NVD) or similar). This comparison identifies any vulnerabilities associated with the specific versions used in the project. For instance, if the `winston` version used in our project has a known vulnerability (e.g., a remotely exploitable security flaw), the vulnerability scanner will flag it, providing details such as the vulnerability ID (CVE ID), severity level (critical, high, medium, low), and a description of the vulnerability.
SBOM Analysis Results
| Component | Version | Vulnerability ID (CVE) | Severity |
|---|---|---|---|
| winston | 3.8.2 | CVE-2023-XXXX | High |
| Node.js | 18.16.1 | None | N/A |
Insights from the Example
This simple example highlights the importance of incorporating SBOM generation and analysis into the software development lifecycle. The ability to quickly identify vulnerabilities, even in a small project, allows for proactive remediation, reducing the risk of exploitation. Further, consistent use of SBOMs facilitates better supply chain security management and improved traceability of components. The choice of SBOM generation tool and vulnerability scanner will greatly influence the efficiency and accuracy of the process.
Regular updates to the project’s dependencies and proactive monitoring of known vulnerabilities are critical for maintaining a secure software environment.
Last Recap
So, there you have it – a whirlwind tour of software bill of materials and their crucial role in managing build tools. While the process might seem initially daunting, the benefits of increased security, improved compliance, and easier troubleshooting far outweigh the effort. By embracing SBOMs and integrating them into your CI/CD pipeline, you’re not just building software; you’re building a more secure and maintainable future.
Remember, transparency is key, and SBOMs are your passport to a more robust and responsible software development journey. Happy building!
Essential Questionnaire
What happens if my SBOM is inaccurate?
An inaccurate SBOM can lead to missed vulnerabilities, compliance issues, and difficulties in troubleshooting. It’s crucial to use reliable tools and processes to ensure accuracy.
How often should I update my SBOM?
Ideally, your SBOM should be updated with each build, especially if you’re working with frequently updated dependencies. Automated processes can help manage this efficiently.
Are there any free tools for SBOM generation?
Yes, several open-source tools are available, and many build tools offer built-in SBOM generation capabilities. Research options based on your chosen build tool and project needs.
Can SBOMs help with open-source license compliance?
Absolutely! SBOMs provide a clear list of dependencies, including their licenses, making it easier to ensure compliance with open-source licensing requirements.