Software Supply Chain Attacks Are Escalating at an Alarming Rate
Software supply chain attacks are escalating at an alarming rate, and it’s a seriously scary situation. We’re seeing more sophisticated attacks targeting everything from small businesses to critical infrastructure. Hackers are getting incredibly creative in how they exploit vulnerabilities, sneaking malicious code into seemingly innocuous software components. The consequences? Massive financial losses, reputational damage, and even national security risks.
This isn’t just a tech problem; it’s a problem for everyone.
Think about it: the software we use daily – from the apps on our phones to the systems running our hospitals – is increasingly reliant on interconnected networks and third-party components. A single compromised piece of software can create a domino effect, impacting millions. This post dives deep into the current threat landscape, explores the vulnerabilities being exploited, and Artikels strategies to protect ourselves and our organizations from these increasingly prevalent attacks.
The Rising Threat Landscape
Software supply chain attacks are no longer a theoretical threat; they’re a stark reality, escalating at an alarming pace and posing a significant risk to businesses and individuals alike. The interconnected nature of modern software development and deployment creates a vast attack surface, making even seemingly minor vulnerabilities exploitable on a massive scale. This necessitates a comprehensive understanding of the current threat landscape to effectively mitigate the risks.The current state of software supply chain attacks reveals a worrying trend of increasing sophistication and frequency.
Attackers are constantly developing new techniques to exploit vulnerabilities within the intricate web of dependencies that underpin modern software. These attacks are not limited to large corporations; even small businesses and open-source projects are increasingly becoming targets. The sheer scale of potential damage, coupled with the difficulty in attribution and remediation, makes this a critical security concern.
Attack Vectors
Several attack vectors are commonly employed in software supply chain attacks. These include compromised developer accounts, malicious code injected into open-source libraries or dependencies, typosquatting (registering domain names or package names that closely resemble legitimate ones), and supply chain manipulation targeting software distribution channels. The success of these attacks often hinges on exploiting human error, inadequate security practices, or vulnerabilities in the software development lifecycle.
Motivations Behind Attacks
The motivations behind software supply chain attacks are diverse. Financial gain is a primary driver, with attackers seeking to steal intellectual property, extort money through ransomware, or deploy malware to conduct cryptojacking or other illicit activities. Espionage is another significant motivator, with nation-state actors targeting critical infrastructure or sensitive data. In some cases, attacks may be driven by activism or disruption, aiming to damage a company’s reputation or disrupt its operations.
High-Profile Software Supply Chain Attacks
Several high-profile attacks have highlighted the devastating impact of compromised software supply chains. These incidents underscore the need for robust security measures throughout the entire software development lifecycle, from code development to deployment and maintenance. The following table provides a summary of some notable examples:
| Attack Name | Target | Impact | Year |
|---|---|---|---|
| SolarWinds Orion breach | Numerous US government agencies and private companies | Data breaches, espionage, disruption of operations | 2020 |
| Codecov breach | Thousands of Codecov customers | Exposure of sensitive environment variables and credentials | 2021 |
| NotPetya | Global businesses | Widespread disruption, billions of dollars in damages | 2017 |
| Log4j vulnerability (Log4Shell) | Numerous applications and services | Remote code execution, widespread exploitation | 2021 |
Vulnerabilities and Exploits
Software supply chain attacks are thriving due to a confluence of vulnerabilities and sophisticated exploitation techniques. Understanding these weaknesses is crucial for building robust defenses. This section delves into the common vulnerabilities targeted, the methods used to compromise development processes, and illustrative examples of malicious code injection.
The core of many attacks lies in exploiting weaknesses in the software development lifecycle (SDLC). Attackers often target areas with lax security practices or vulnerabilities in open-source components, leveraging them to infiltrate the supply chain and compromise the integrity of software. This can range from simple typosquatting to highly sophisticated attacks targeting the build process itself.
Common Vulnerabilities Exploited
Many vulnerabilities can be exploited in software supply chain attacks. These range from well-known vulnerabilities in widely used libraries to weaknesses in the security practices of developers and organizations. For instance, outdated or unpatched dependencies are a frequent target. Compromised developer accounts also provide a direct path to injecting malicious code into the software. Finally, insecure configuration management practices, allowing attackers to gain control over build systems or repositories, are a common attack vector.
Techniques to Compromise Software Development Processes
Attackers employ various techniques to infiltrate the SDLC. One common method is to compromise a developer’s machine through phishing or malware, gaining access to their credentials and code repositories. Another tactic involves targeting the build system itself. This could involve modifying the build process to inject malicious code into the final software product. Alternatively, attackers might gain access to a software repository, replacing legitimate code with malicious versions.
This can also be achieved by creating a malicious package that looks legitimate and is downloaded by the victim’s build process.
Malicious Code Injection Methods
Malicious code injection can take many forms. One common method is to insert malicious code directly into the source code of a software project. This can be done by modifying the code directly in a repository or by injecting it during the build process. Another approach is to use typosquatting, where attackers create packages with names similar to legitimate packages.
Unsuspecting developers might install these malicious packages, inadvertently introducing vulnerabilities into their projects. Finally, supply chain attacks might leverage tainted open-source components, modifying them before they are integrated into larger projects. A sophisticated attacker might use a technique like code obfuscation to hide the malicious code, making detection more difficult.
The Role of Open-Source Components
Open-source components play a significant role in modern software development. While they offer numerous benefits, they also introduce significant security risks. Attackers can compromise open-source projects by submitting malicious code as contributions. This malicious code might lie dormant for a long time before being activated. Alternatively, attackers might create fake open-source projects that mimic legitimate ones, waiting for developers to integrate them into their software.
The widespread use of open-source components makes them attractive targets for supply chain attacks, as a single compromised component can impact a vast number of applications.
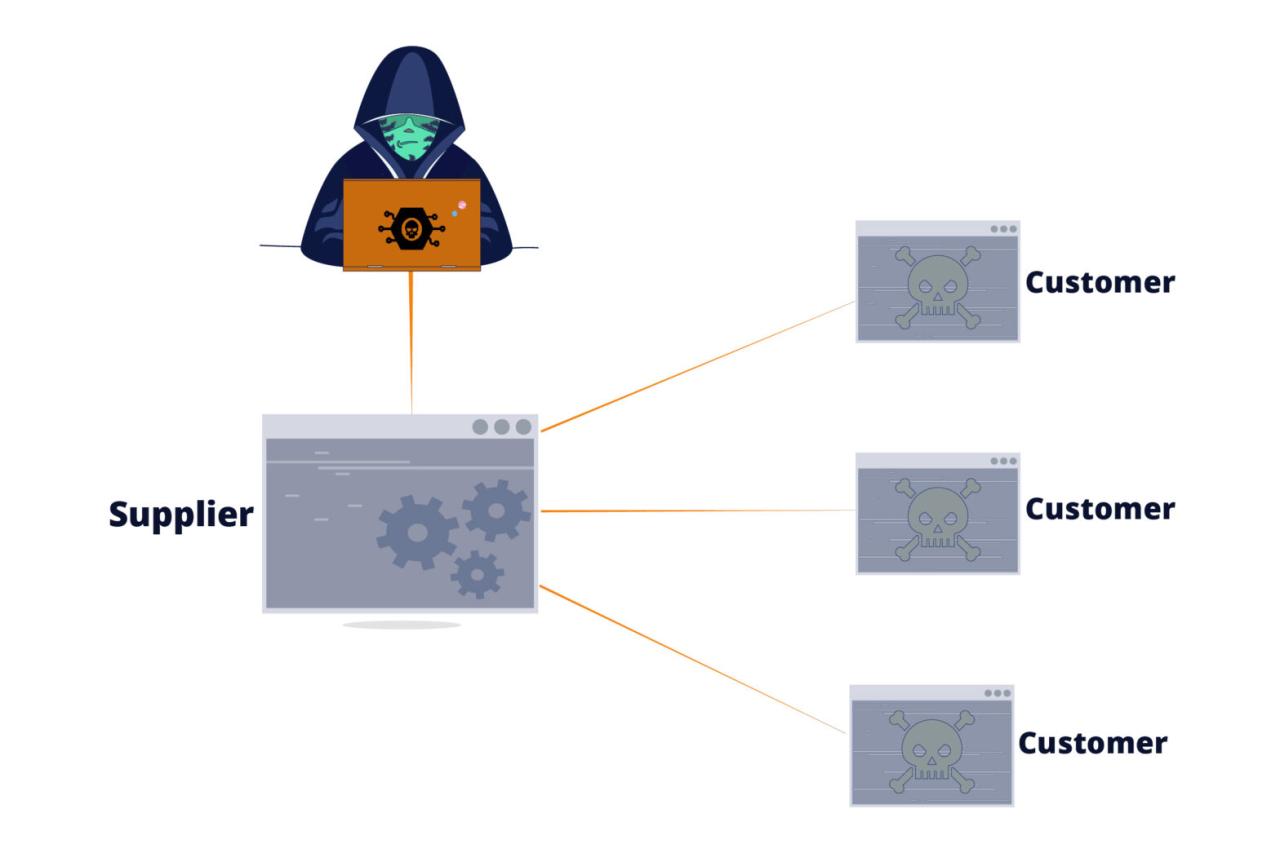
Hypothetical Supply Chain Attack Scenario
Imagine a scenario involving a popular open-source logging library, “LogLib.” An attacker compromises the project’s main repository, subtly introducing a backdoor into a seemingly innocuous function. This backdoor allows remote code execution, activated only when a specific environment variable is set. Numerous companies rely on “LogLib” in their applications. When these companies deploy their applications to a cloud environment where that specific environment variable is set (perhaps due to a misconfiguration), the backdoor is triggered, giving the attacker access to their systems.
This scenario highlights the cascading effect of a single vulnerability in a widely used open-source component. The attacker gains access to numerous systems without directly targeting each individual organization.
Impact and Consequences
Software supply chain attacks don’t just cause immediate disruption; they trigger a cascade of negative effects that can cripple organizations for years. The financial losses, reputational damage, and legal ramifications are significant, often extending far beyond the initial breach. Understanding these consequences is crucial for proactive security planning.The economic impact of a successful software supply chain attack can be devastating.
Direct costs include remediation efforts, incident response, legal fees, and potential fines. Indirect costs are equally substantial and often harder to quantify. These include lost revenue due to business disruption, decreased customer trust leading to lost sales, and the cost of rebuilding damaged brand reputation. A single compromised component can lead to millions, even billions, of dollars in losses, depending on the scale of the attack and the affected organization.
For example, the NotPetya ransomware attack in 2017, which exploited a vulnerability in Ukrainian accounting software, caused billions of dollars in damages globally.
Economic Impact
Successful attacks translate into substantial financial losses for affected organizations. These costs encompass immediate expenses like incident response, legal fees, and system recovery, as well as longer-term losses from decreased productivity, damaged reputation, and lost business opportunities. The scale of these losses can vary drastically, ranging from thousands to billions of dollars, depending on the size and scope of the organization and the nature of the attack.
The longer the breach goes undetected, the more extensive the financial repercussions.
Reputational Damage
The reputational harm inflicted by a supply chain attack can be long-lasting and far-reaching. Customers lose trust in compromised organizations, leading to decreased sales and market share. Investors may withdraw support, impacting stock prices and overall financial stability. The negative publicity associated with a data breach or service disruption can significantly harm an organization’s image and brand value, making it difficult to attract new customers and partners.
The SolarWinds attack, for example, severely damaged the reputation of SolarWinds and impacted the trust in many organizations that relied on their software.
Legal and Regulatory Implications
Organizations facing supply chain attacks face significant legal and regulatory challenges. Depending on the nature of the attack and the data involved, companies might face lawsuits from affected customers, penalties from regulatory bodies like the FTC or GDPR, and investigations from law enforcement agencies. Non-compliance with data protection regulations can result in hefty fines, further exacerbating the financial burden.
Furthermore, the legal complexities of determining liability across the supply chain can lead to protracted and expensive legal battles.
Disruption of Critical Infrastructure
Software supply chain attacks pose a significant threat to critical infrastructure, including power grids, healthcare systems, and transportation networks. Compromised software components within these systems can lead to widespread outages, service disruptions, and even physical damage. The consequences can be catastrophic, affecting public safety, economic stability, and national security. Imagine a scenario where a compromised component in a power grid’s control system leads to a widespread blackout, impacting millions of people.
Long-Term Consequences for Victims
The long-term consequences for victims of software supply chain attacks are multifaceted and often severe.
- Sustained loss of revenue and market share.
- Erosion of customer trust and brand reputation.
- Increased cybersecurity insurance premiums and costs.
- Heightened regulatory scrutiny and potential fines.
- Ongoing legal battles and reputational damage.
- Difficulty attracting and retaining talent.
- Increased operational costs associated with enhanced security measures.
Mitigation Strategies and Best Practices: Software Supply Chain Attacks Are Escalating At An Alarming Rate
Securing the software supply chain is no longer a luxury; it’s a necessity. The escalating frequency and sophistication of supply chain attacks demand a proactive and multi-layered approach encompassing robust security practices throughout the entire software development lifecycle. This section details crucial mitigation strategies and best practices to strengthen your organization’s defenses.
Effective mitigation requires a holistic strategy that integrates security into every stage of the software development process, from initial design to deployment and beyond. This includes rigorous vetting of third-party components, proactive vulnerability management, and continuous monitoring for suspicious activity.
Secure Software Development Lifecycle Practices
Implementing a secure software development lifecycle (SDLC) is paramount. This involves integrating security considerations into each phase, starting with secure coding practices and extending to rigorous testing and vulnerability management. A robust SDLC minimizes the introduction of vulnerabilities and strengthens the overall resilience of the software against attacks. This includes utilizing secure coding guidelines, performing regular code reviews, and integrating automated security testing throughout the development process.
For example, implementing static and dynamic application security testing (SAST and DAST) can help identify vulnerabilities early in the development cycle, significantly reducing the cost and effort required to fix them later.
Malicious Code Injection Prevention Methods, Software supply chain attacks are escalating at an alarming rate
Preventing malicious code injection requires a combination of techniques. This includes rigorously validating all inputs, using parameterized queries to prevent SQL injection, and employing robust input sanitization techniques. Regular security audits and penetration testing are crucial to identify potential vulnerabilities. Furthermore, implementing code signing and verification mechanisms helps ensure the authenticity and integrity of software components. For instance, using a trusted code signing certificate to digitally sign software packages allows recipients to verify the origin and integrity of the code, preventing malicious code from being substituted.
Software Composition Analysis (SCA) Tool Usage
Software composition analysis (SCA) tools play a critical role in identifying and mitigating vulnerabilities in open-source and third-party components. These tools automatically scan codebases to detect known vulnerabilities, licensing issues, and security risks within the software’s dependencies. By integrating SCA tools into the SDLC, organizations can proactively address vulnerabilities before they are exploited. For example, an SCA tool might identify a known vulnerability in a widely used open-source library, allowing developers to update to a patched version and prevent a potential attack.
The use of SCA tools significantly reduces the attack surface by identifying and mitigating risks early in the development process.
Multi-Layered Security Approach
A multi-layered security approach provides comprehensive protection against supply chain attacks. This involves implementing a combination of security controls across different layers, including network security, application security, and data security. Network segmentation, firewalls, and intrusion detection systems protect the network perimeter. Secure coding practices, input validation, and regular security testing enhance application security. Data encryption and access control mechanisms protect sensitive data.
A layered approach ensures that even if one layer is compromised, other layers provide additional protection. This layered approach, encompassing preventative, detective, and responsive measures, ensures a robust and resilient security posture. For example, a breach at the network level might be detected by an intrusion detection system, while vulnerabilities in the application code are identified through regular penetration testing.
This layered approach provides multiple opportunities to detect and respond to threats.
Future Trends and Predictions
The software supply chain is a dynamic ecosystem, constantly evolving with new technologies and attack surfaces. Predicting the future of its security requires considering emerging threats, the influence of AI, and the likely evolution of attack vectors. While precise forecasting is impossible, analyzing current trends allows us to anticipate the likely challenges ahead.Emerging threats and vulnerabilities will continue to proliferate.
The increasing complexity of software, coupled with the rise of open-source components and the adoption of cloud-native architectures, expands the attack surface exponentially. We’ll see more sophisticated attacks leveraging zero-day exploits targeting lesser-known dependencies and obscure components within the software supply chain. The reliance on third-party libraries and services, while offering efficiency, introduces significant risks if those providers themselves are compromised.
Furthermore, the rise of supply chain attacks targeting the development pipeline itself (DevSecOps) through compromised build systems or code repositories represents a major concern.
The Impact of AI and Automation on Supply Chain Security
AI and automation are transforming software development and deployment, but this technological advancement also introduces new security challenges. AI-powered tools can be used to automate security testing and vulnerability detection, improving overall security posture. However, these same tools can also be weaponized by attackers. For example, AI can be used to generate highly effective and targeted phishing campaigns or to automate the discovery of zero-day vulnerabilities, making attacks more efficient and difficult to defend against.
The increasing use of AI in automated software development processes, while speeding up delivery, increases the potential for injecting malicious code into the software supply chain undetected. Imagine an AI-powered code generation tool being compromised, subtly inserting backdoors into thousands of applications across various industries. This scenario highlights the critical need for robust security controls within the AI-driven development pipeline.
Evolution of Attack Vectors
Attack vectors will become increasingly sophisticated and harder to detect. We can expect to see a rise in attacks that combine multiple techniques to bypass multiple layers of security. For example, a combination of social engineering to compromise a developer’s account, followed by the injection of malicious code into the build system, and finally, the use of polymorphic malware to evade detection.
Supply chain attacks will likely move beyond simple code injection and focus on manipulating the entire development and deployment process, aiming to create a long-lasting, covert presence within the target organization’s infrastructure. The use of living-off-the-land binaries and techniques to blend into normal system activity will become more prevalent, making detection more challenging.
Potential for More Sophisticated and Widespread Attacks
The potential for large-scale, devastating attacks on the software supply chain is increasing. A successful attack on a major software vendor or open-source project could compromise millions of applications and systems worldwide. The cascading effect of such an attack could cripple critical infrastructure, disrupt global economies, and cause widespread chaos. Imagine a compromised component used in critical medical devices, leading to malfunctions with potentially fatal consequences.
This highlights the systemic risk posed by vulnerabilities in the software supply chain. These attacks will also be more financially motivated, targeting organizations holding valuable intellectual property or financial data.
Predicted Evolution of Software Supply Chain Attacks (Next Five Years)
Imagine a graph depicting the evolution of software supply chain attacks over the next five years. The X-axis represents time (years), and the Y-axis represents the sophistication and scale of attacks. The graph begins in 2024 with relatively simple attacks, such as code injection into open-source libraries, represented by small, scattered data points. As we move towards 2025, the data points increase in both size and density, reflecting the rise of more sophisticated attacks targeting the build process and using AI-powered tools.
Software supply chain attacks are escalating at an alarming rate, making secure development practices more critical than ever. To combat this, exploring innovative approaches like those discussed in this article on domino app dev, the low-code and pro-code future , could offer a path towards more resilient applications. Ultimately, strengthening our software development lifecycles is key to mitigating the growing threat of supply chain attacks.
By 2027, the data points coalesce into larger clusters, representing coordinated attacks targeting multiple points in the supply chain, utilizing advanced evasion techniques. In 2028, we see the emergence of massive, systemic attacks impacting critical infrastructure, with the data points forming a large, concentrated mass at the high end of the Y-axis. Finally, in 2029, the graph shows a plateauing of attack frequency but with a continued increase in sophistication, reflecting the adaptation of defensive strategies and the continuous evolution of attack methods.
This visual representation illustrates a steady increase in both the scale and complexity of attacks over the next five years, necessitating proactive and adaptive security measures.
Final Conclusion
The escalating threat of software supply chain attacks demands immediate and decisive action. While the sophistication of these attacks continues to grow, so too must our defenses. By understanding the vulnerabilities, adopting robust security practices, and fostering collaboration across the industry, we can significantly mitigate the risks and build a more resilient software ecosystem. Staying informed, proactive, and vigilant is crucial in this ever-evolving landscape of cybersecurity threats.
Let’s work together to make the digital world a safer place.
Question Bank
What is a software supply chain attack?
A software supply chain attack targets the process of developing and distributing software. Attackers compromise a component of the software supply chain (e.g., a library, a tool, or a developer’s machine) to inject malicious code into the final product.
How can I protect my organization from these attacks?
Implement robust security practices throughout your software development lifecycle, use software composition analysis tools, and regularly update and patch your software. Employee training on security best practices is also crucial.
Are open-source components more vulnerable?
Open-source components can be more vulnerable due to their widespread use and sometimes less rigorous security auditing. However, many open-source projects have strong security practices and communities that help identify and fix vulnerabilities quickly.
What is the role of AI in these attacks?
AI can be used by both attackers (to automate attacks and identify vulnerabilities) and defenders (to detect and respond to attacks more effectively). This makes the fight against supply chain attacks even more complex.