Software Supply Chain Exposures Whitepaper A Deep Dive
Software Supply Chain Exposures Whitepaper: Have you ever stopped to think about the hidden vulnerabilities lurking within the software you use every day? This isn’t just about a single line of buggy code; it’s about the entire network of developers, libraries, and components that contribute to the applications we rely on. This whitepaper delves into the increasingly complex world of software supply chain security, exploring the threats, vulnerabilities, and strategies needed to protect ourselves from the potentially devastating consequences of a compromised system.
Get ready for a thrilling ride as we uncover the secrets and risks hidden within the digital supply chain.
We’ll explore real-world examples of attacks, examine common vulnerabilities in open-source components, and discuss practical mitigation strategies. We’ll also look at the legal and regulatory landscape, considering the implications of non-compliance and the importance of proactive security measures. Finally, we’ll peer into the future, anticipating emerging threats and the role of AI in safeguarding our digital infrastructure. It’s a journey into the heart of cybersecurity, and it’s more crucial than ever.
Introduction to Software Supply Chain Exposures
Software supply chain exposures represent vulnerabilities within the process of developing, building, and deploying software. These vulnerabilities can be exploited by malicious actors to compromise the integrity, confidentiality, or availability of the software itself, and potentially the systems it runs on. This goes beyond simply targeting the final product; it encompasses the entire chain of tools, libraries, components, and individuals involved in its creation.
Understanding these exposures is critical for securing modern software systems.Software supply chain security threats are rapidly evolving, mirroring the increasing complexity and interconnectedness of modern software development. The shift towards cloud-native architectures, microservices, and open-source components has expanded the attack surface significantly. Malicious actors are constantly developing new techniques to exploit vulnerabilities at various stages of the supply chain, from compromising developer accounts to injecting malware into seemingly benign packages.
This evolution necessitates a proactive and multi-faceted approach to security.
Real-World Examples of Software Supply Chain Attacks
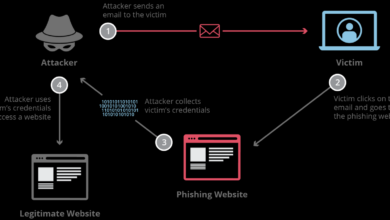
Several high-profile incidents have underscored the devastating consequences of supply chain vulnerabilities. The SolarWinds attack, where malicious code was inserted into updates for the SolarWinds Orion platform, compromised thousands of organizations worldwide. This attack highlighted the potential for widespread damage when vulnerabilities are introduced at a high level within the supply chain. Similarly, the NotPetya ransomware attack, while not strictly a software supply chain attack in the purest sense, leveraged a vulnerability in a widely used accounting software to spread rapidly and cause billions of dollars in damage.
These events demonstrate the systemic risk posed by supply chain vulnerabilities and the need for robust security measures throughout the entire software development lifecycle.
Types of Software Supply Chain Attacks
The following table summarizes different types of software supply chain attacks, their descriptions, impacts, and potential mitigation strategies.
| Attack Type | Description | Impact | Mitigation Strategies |
|---|---|---|---|
| Compromised Dependencies | Malicious code is introduced into open-source libraries or third-party components used in the software. | Data breaches, system compromise, malware infections, service disruptions. | Employ rigorous dependency checks, utilize software composition analysis (SCA) tools, implement strong access controls for repositories. |
| Supply Chain Tampering | Physical or digital tampering with the software build process, potentially modifying source code or binaries. | Malware distribution, backdoors, intellectual property theft. | Secure development environments, use secure build systems, implement code signing and verification. |
| Developer Account Compromise | Malicious actors gain access to developer accounts to introduce malicious code or deploy malicious software. | Data breaches, malware infections, unauthorized code deployments. | Implement multi-factor authentication (MFA), enforce strong password policies, regularly audit developer accounts. |
| Malicious Insider Threats | An insider with access to the software development process intentionally introduces malicious code or vulnerabilities. | Data breaches, sabotage, intellectual property theft, service disruptions. | Implement strong access controls, conduct background checks, implement robust monitoring and auditing systems. |
Identifying Vulnerabilities in the Software Supply Chain
The software supply chain, a complex network of developers, libraries, and dependencies, presents numerous opportunities for vulnerabilities to be introduced. Understanding these vulnerabilities is crucial for building secure and resilient software systems. This section will delve into common vulnerabilities, the challenges of verification, and key vulnerable areas within the software development lifecycle, ultimately outlining a process for effective auditing.
Common Vulnerabilities in Open-Source Components
Open-source components, while offering significant benefits like cost savings and community support, also introduce inherent risks. Many open-source projects lack the rigorous security testing and auditing found in commercial software. This can lead to the inclusion of known vulnerabilities or the introduction of new ones through malicious contributions. Examples include outdated libraries containing known exploits, insufficient input validation leading to injection attacks, and insecure coding practices resulting in buffer overflows or memory leaks.
The sheer volume of open-source components used in modern software makes thorough vetting a significant challenge. A well-known example is the widespread use of Log4j, where a single vulnerability had cascading effects across countless applications.
Challenges of Verifying Authenticity and Integrity of Software Components
Ensuring the authenticity and integrity of software components is paramount. Malicious actors can tamper with components, either by directly modifying the source code or injecting malicious code into the build process. This can lead to supply chain attacks where compromised components are unknowingly integrated into applications, allowing attackers to gain unauthorized access or control. Verifying authenticity often relies on digital signatures and cryptographic checksums, but these mechanisms can be bypassed if the attacker compromises the signing keys or the build process itself.
Furthermore, the complexity of modern software development, with numerous dependencies and sub-dependencies, makes complete verification a computationally intensive and often impractical task.
Vulnerable Areas in the Software Development Lifecycle
Several stages within the software development lifecycle (SDLC) are particularly vulnerable to attacks. These include the requirements gathering phase, where insecure design choices can be made, the coding phase where vulnerabilities can be introduced directly into the code, and the testing phase where vulnerabilities may be missed due to incomplete or inadequate testing. The deployment phase is also critical, as improperly configured servers or insecure deployment processes can expose vulnerabilities.
Finally, the maintenance phase presents ongoing risks as outdated components and unpatched vulnerabilities linger in production systems. A robust SDLC with security built-in at each stage is essential to mitigate these risks.
Process for Regularly Auditing Third-Party Libraries and Dependencies
A structured process for regularly auditing third-party libraries and dependencies is crucial for maintaining software security. This process should involve: (1) Regularly scanning dependencies for known vulnerabilities using automated tools. (2) Manually reviewing the code of critical components to identify potential vulnerabilities not detected by automated tools. (3) Maintaining an up-to-date inventory of all third-party libraries and dependencies.
(4) Implementing a robust vulnerability management process to quickly address identified vulnerabilities. (5) Using a secure software composition analysis (SCA) tool to identify and assess the risks associated with open-source and commercial components. This multi-faceted approach, combined with a commitment to proactive security measures, significantly reduces the risk of supply chain attacks.
Mitigation Strategies and Best Practices: Software Supply Chain Exposures Whitepaper
Securing your software supply chain requires a multi-faceted approach encompassing proactive measures, robust security tools, and a commitment to secure development practices. Ignoring these aspects leaves your organization vulnerable to costly breaches and reputational damage. This section details key strategies and best practices to fortify your software supply chain against threats.
Effective mitigation hinges on a layered defense strategy, addressing vulnerabilities at every stage of the software development lifecycle (SDLC). This includes careful vendor selection, rigorous code review, automated vulnerability scanning, and ongoing monitoring for suspicious activity.
Software Bill of Materials (SBOM) Generation and Analysis
SBOMs provide a comprehensive inventory of all components within a software product. They are crucial for identifying and tracking vulnerabilities throughout the supply chain. Generating and regularly updating SBOMs allows for efficient vulnerability detection and facilitates quicker response times to security incidents. Tools like CycloneDX and SPDX provide standardized formats for SBOM creation and analysis. Analyzing SBOMs allows for identifying outdated or vulnerable components, facilitating timely remediation.
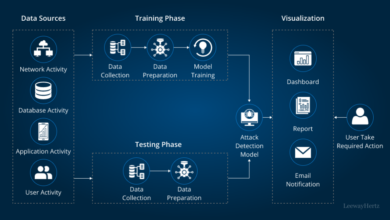
Vulnerability Detection and Remediation
Implementing automated vulnerability scanning throughout the SDLC is paramount. Static Application Security Testing (SAST) tools analyze code without execution, identifying vulnerabilities early in the development process. Dynamic Application Security Testing (DAST) tools test running applications, identifying vulnerabilities that might be missed by SAST. Software Composition Analysis (SCA) tools scan dependencies for known vulnerabilities, providing crucial insights into the security posture of third-party components.
Examples of effective tools include SonarQube (SAST), Burp Suite (DAST), and Snyk or Black Duck (SCA). A well-defined vulnerability remediation process, including prioritization based on severity and risk, is crucial for efficient patching and mitigation.
Secure Coding Practices and Development Methodologies
Secure coding practices should be ingrained throughout the development process. This includes adhering to coding standards, conducting regular code reviews, and utilizing secure coding libraries and frameworks. Adopting secure development methodologies like DevSecOps, which integrates security into every stage of the SDLC, is essential. Training developers on secure coding principles and best practices is a vital component of this strategy.
Regular security awareness training for all personnel involved in the software supply chain enhances overall security posture.
Vulnerability Management Approaches
Different vulnerability management approaches exist, each with its own strengths and weaknesses. A centralized vulnerability management system offers a single point of control for tracking and managing vulnerabilities across the entire software ecosystem. This system facilitates prioritization based on risk, streamlining remediation efforts. In contrast, a decentralized approach might be more suitable for organizations with highly independent teams.
Regardless of the approach, clear communication and collaboration across teams are essential for effective vulnerability management. Regular vulnerability assessments and penetration testing help identify weaknesses and validate the effectiveness of implemented security controls.
Legal and Regulatory Compliance
Navigating the complex legal landscape surrounding software supply chain security is crucial for organizations of all sizes. Failure to comply with relevant regulations can lead to significant financial penalties, reputational damage, and even legal action. This section Artikels key legal frameworks, their implications, and best practices for ensuring compliance.The increasing interconnectedness of software systems and the growing reliance on third-party components have brought software supply chain security to the forefront of regulatory attention.
Governments worldwide are recognizing the critical need for robust security measures to protect against vulnerabilities that can have far-reaching consequences.
Relevant Legal Frameworks and Regulations
Several legal frameworks and regulations address aspects of software supply chain security, although a universally harmonized approach is still developing. These regulations often overlap and are jurisdiction-specific, requiring careful attention to detail. For example, the European Union’s General Data Protection Regulation (GDPR) indirectly impacts software supply chain security by imposing strict data protection requirements on organizations processing personal data.
A breach stemming from a vulnerable software component could lead to GDPR non-compliance and hefty fines. Similarly, the California Consumer Privacy Act (CCPA) and other state-level privacy laws in the US place obligations on companies to protect consumer data, making software supply chain security a key element of compliance. Beyond privacy regulations, sector-specific regulations like those in finance (e.g., PCI DSS) or healthcare (e.g., HIPAA) often have explicit or implicit requirements for securing software and its supply chain.
Finally, national security concerns are increasingly driving legislation focused on software provenance and security, particularly for critical infrastructure.
Implications of Non-Compliance
Non-compliance with relevant regulations can result in a range of serious consequences. Financial penalties can be substantial, potentially reaching millions of dollars depending on the severity of the violation and the jurisdiction. Reputational damage can be equally devastating, leading to loss of customer trust, decreased market share, and difficulty attracting investors. In some cases, non-compliance can lead to legal action, including lawsuits from affected parties, government investigations, and even criminal charges.
The impact on an organization’s operations can also be significant, with potential disruptions to services, increased operational costs, and the need for costly remediation efforts. For instance, a data breach caused by a vulnerability in a third-party component could trigger investigations, legal action, and significant financial losses from remediation, regulatory fines, and potential litigation.
Industry Standards and Best Practices for Compliance
Several industry standards and best practices provide guidance on achieving software supply chain security and regulatory compliance. The National Institute of Standards and Technology (NIST) offers valuable resources, including the NIST Cybersecurity Framework, which provides a voluntary framework for managing cybersecurity risk. The Center for Internet Security (CIS) also publishes benchmarks and best practices that can help organizations improve their software supply chain security posture.
ISO 27001, an internationally recognized standard for information security management systems, provides a framework for establishing, implementing, maintaining, and continually improving an information security management system. Adherence to these standards demonstrates a commitment to security and can assist in demonstrating compliance with regulatory requirements. Furthermore, implementing secure software development lifecycle (SDLC) practices, such as regular security testing, vulnerability scanning, and code reviews, are crucial for preventing vulnerabilities from entering the software supply chain in the first place.
Key Legal Considerations for Software Vendors and Users
Software vendors and users face distinct but interconnected legal considerations. Vendors have a responsibility to ensure the security of their products and to provide adequate disclosure of known vulnerabilities. Users, on the other hand, have a responsibility to implement appropriate security measures to protect their systems and data. Key considerations include: contractual obligations related to security, data privacy regulations, intellectual property rights, liability for security breaches, and compliance with relevant industry standards.
For example, a software vendor might be held liable for damages resulting from a security vulnerability in their product, particularly if they failed to disclose or address the vulnerability in a timely manner. Similarly, a user might be held liable for a data breach if they failed to implement reasonable security measures to protect their systems and data, even if the vulnerability originated in a third-party component.
Understanding these legal responsibilities is crucial for mitigating risk and ensuring compliance.
Future Trends and Emerging Threats
The software supply chain, once a relatively straightforward process, is now a complex web of interconnected components, making it increasingly vulnerable to a diverse range of threats. Understanding the evolving landscape of these threats is crucial for building resilient and secure software systems. This section explores emerging threats, the impact of AI, and future trends in securing the software supply chain.The software supply chain faces an ever-growing number of sophisticated attacks, fueled by the increasing complexity of software development and the rise of open-source components.
These attacks range from traditional vulnerabilities like malware injection to more subtle attacks exploiting dependencies and misconfigurations. The sheer volume and velocity of these threats pose significant challenges for organizations striving to maintain secure software.
AI and Machine Learning’s Impact on Software Supply Chain Security
The integration of AI and machine learning (ML) is transforming various aspects of software development, including security. AI-powered tools can automate vulnerability detection, identify malicious code, and even predict potential security breaches. However, this technology is a double-edged sword. Sophisticated attackers can also leverage AI to create more evasive and difficult-to-detect attacks, developing highly targeted malware and exploiting vulnerabilities more effectively.
For example, AI could be used to generate realistic-looking phishing emails or to automate the process of finding and exploiting zero-day vulnerabilities at scale. This arms race necessitates a continuous evolution of security measures to stay ahead of the curve.
Future Trends in Software Supply Chain Security Practices
Several key trends are shaping the future of software supply chain security. Increased adoption of Software Bill of Materials (SBOMs) is expected, providing better transparency and traceability of components. This improved visibility will facilitate quicker identification of vulnerabilities and assist in risk assessment. Furthermore, we will see greater emphasis on secure software development practices, including DevSecOps, shifting security considerations left in the development lifecycle.
This approach aims to integrate security practices throughout the entire software development process rather than treating security as an afterthought. Blockchain technology also holds potential for enhancing the security and transparency of the software supply chain, offering tamper-proof records of software components and their origins. Finally, the rise of automated security testing and continuous integration/continuous delivery (CI/CD) pipelines will help organizations detect and respond to threats more quickly.
Visual Representation of Evolving Software Supply Chain Threats
Imagine a graph charting the evolution of software supply chain threats over time. The X-axis represents time, starting from the early days of software development and extending to the present and beyond. The Y-axis represents the complexity and sophistication of threats. Initially, the graph shows a relatively low and steady line, representing simpler threats like individual vulnerabilities in proprietary code.
As time progresses and open-source components become more prevalent, the line begins to rise, reflecting the increasing complexity of the software ecosystem and the emergence of attacks targeting dependencies. The line sharply increases with the advent of AI-driven attacks, demonstrating the ability of attackers to leverage automation and sophisticated techniques. The graph then shows a fluctuating line representing the ongoing arms race between attackers and defenders, with peaks and valleys signifying periods of intense threat activity followed by periods of improved security measures.
The future projection shows a continued upward trend, indicating the ongoing need for robust and adaptable security practices to combat increasingly sophisticated threats.
Case Studies and Real-World Examples

Understanding the impact of software supply chain vulnerabilities requires examining real-world incidents. Analyzing both successful and unsuccessful responses allows us to learn valuable lessons and improve our security posture. The following case studies illustrate the diverse nature of these attacks, their consequences, and the strategies employed to mitigate them.
SolarWinds Orion Supply Chain Attack
The SolarWinds attack, discovered in late 2020, remains a landmark event in software supply chain security. The attackers compromised the SolarWinds Orion software update process, inserting malicious code into updates distributed to thousands of organizations. This allowed them to gain access to numerous victim networks, including government agencies and private companies. The impact was significant, leading to widespread data breaches and espionage.
SolarWinds’ response involved patching the vulnerable software, notifying affected customers, and collaborating with security agencies. However, the incident highlighted the challenges of securing the entire supply chain, even for large, established companies. The long-term impact involved significant reputational damage and substantial costs associated with remediation and investigation.
NotPetya Ransomware Attack, Software supply chain exposures whitepaper
While not strictly a software supply chain attack in the same vein as SolarWinds, the NotPetya ransomware attack of 2017 effectively demonstrated the cascading effects of compromised software. The attack leveraged a vulnerability in the Ukrainian accounting software M.E.Doc, which spread rapidly through networks, encrypting data and causing significant disruption. Although the initial vector was a software update, the rapid propagation highlighted the interconnectedness of systems and the potential for seemingly localized vulnerabilities to cause widespread damage.
The response from various organizations varied, but many faced substantial downtime and financial losses due to the attack’s destructive nature. The lesson learned here underscores the importance of robust patching and incident response plans, extending beyond direct software dependencies.
Successful Mitigation: Improved Vulnerability Disclosure Programs
Many organizations have proactively improved their vulnerability disclosure programs (VDPs) as a direct response to increasing supply chain threats. These programs encourage ethical hackers to report vulnerabilities before they can be exploited. A successful VDP provides a structured channel for reporting, prioritization, and remediation, reducing the window of vulnerability. Companies like Google and Microsoft have established robust VDPs, fostering a collaborative approach to security.
These programs, while not foolproof, demonstrate a proactive approach to mitigating risk before vulnerabilities can be weaponized by malicious actors.
| Organization | Attack Type | Impact | Response |
|---|---|---|---|
| SolarWinds | Supply Chain Compromise (malicious code in software update) | Widespread data breaches, espionage, reputational damage, significant financial losses | Patching, customer notification, collaboration with security agencies, internal security improvements |
| Various Organizations (NotPetya) | Ransomware spread via compromised accounting software | Widespread data encryption, significant downtime, substantial financial losses | Varied responses, focusing on data recovery, system restoration, and improved security practices |
| (Example: Hypothetical Company X) | Third-party library vulnerability exploited | Limited data breach, minor service disruption | Rapid patching of the vulnerable library, security awareness training for developers |
End of Discussion
Securing the software supply chain isn’t just a technical challenge; it’s a fundamental shift in how we think about software development and deployment. This whitepaper has illuminated the critical vulnerabilities and the potential for catastrophic consequences. But it also offers a path forward, outlining best practices, security tools, and a framework for building more resilient and secure systems.
By understanding the risks and implementing effective mitigation strategies, we can collectively work towards a more secure digital future. The journey to secure software supply chains is ongoing, and constant vigilance and adaptation are key to staying ahead of the ever-evolving threat landscape. Let’s build a more secure digital world, together.
General Inquiries
What is the difference between a software supply chain attack and a traditional software vulnerability?
A traditional vulnerability is a flaw within a specific piece of software. A supply chain attack targets the process of building and delivering that software, compromising components or the entire development pipeline.
How can I identify if my organization is vulnerable to software supply chain attacks?
Conduct regular security audits of your dependencies, implement strong access controls, and use vulnerability scanning tools. A thorough risk assessment focusing on your software’s components and their origins is crucial.
What is the role of AI in mitigating software supply chain risks?
AI can automate vulnerability detection, predict potential attacks, and enhance threat intelligence, enabling faster response times and more effective mitigation strategies.
Are there any industry certifications related to software supply chain security?
While there isn’t one single overarching certification, various organizations offer certifications related to cybersecurity and secure software development practices that are relevant to supply chain security.