Standalone Service Mesh Which Option Is Right?
Standalone service mesh solution or lightweight option which is right for you? That’s the million-dollar question many developers grapple with. Choosing the right service mesh architecture is crucial for the performance, scalability, and security of your microservices. This post dives deep into the differences between standalone and lightweight service meshes, helping you determine which best fits your specific needs and project goals.
We’ll explore their strengths and weaknesses, comparing key features and offering practical advice to guide your decision.
We’ll cover everything from architecture and deployment to cost considerations and future trends. Whether you’re a seasoned pro or just starting with microservices, this guide will equip you with the knowledge to make an informed choice. Get ready to navigate the world of service meshes and find the perfect solution for your application!
Introduction: Standalone vs. Lightweight Service Mesh
Service meshes are increasingly crucial for managing the complexities of microservices architectures. They provide a dedicated infrastructure layer that handles service-to-service communication, enhancing reliability, security, and observability. But choosing the right service mesh can be challenging, given the range of options available. This post clarifies the differences between standalone and lightweight service mesh solutions, helping you make an informed decision.A service mesh’s core functionalities include service discovery (locating services), traffic management (routing, load balancing), security (authentication, authorization), observability (monitoring, tracing), and resilience (retry mechanisms, circuit breaking).
Essentially, it abstracts away the complexities of inter-service communication, allowing developers to focus on building applications rather than infrastructure.
Standalone vs. Lightweight Service Meshes
Standalone service meshes are typically full-featured platforms deployed as independent components in your infrastructure. They offer a comprehensive suite of features, but require more resources and expertise to manage. Lightweight service meshes, on the other hand, are often integrated directly into the application or runtime environment, providing a more streamlined approach with reduced overhead.
Use Cases for Standalone Service Meshes, Standalone service mesh solution or lightweight option which is right for you
Standalone service meshes excel in large, complex microservices environments with stringent security and observability requirements. For example, a large financial institution managing thousands of microservices might choose a standalone solution like Istio or Linkerd to ensure robust security, fine-grained traffic control, and comprehensive monitoring. The extensive features justify the increased operational complexity.
Use Cases for Lightweight Service Meshes
Lightweight meshes are ideal for smaller deployments, simpler microservices architectures, or situations where minimal overhead is critical. A startup with a few dozen microservices might opt for a lightweight solution like Consul Connect or Kuma, focusing on essential features like service discovery and basic security without the complexity of a full-fledged standalone mesh. The reduced operational burden and resource consumption are key advantages.
Comparison of Standalone and Lightweight Service Meshes
The choice between a standalone and lightweight service mesh depends heavily on your specific needs and context. The following table summarizes key differences:
| Feature | Standalone Service Mesh | Lightweight Service Mesh |
|---|---|---|
| Complexity | High | Low |
| Performance | Can be lower due to added overhead | Generally higher due to less overhead |
| Scalability | High | Moderate to High (depending on implementation) |
| Cost | Potentially higher due to infrastructure and management needs | Potentially lower due to reduced infrastructure and simpler management |
Standalone Service Mesh Solutions
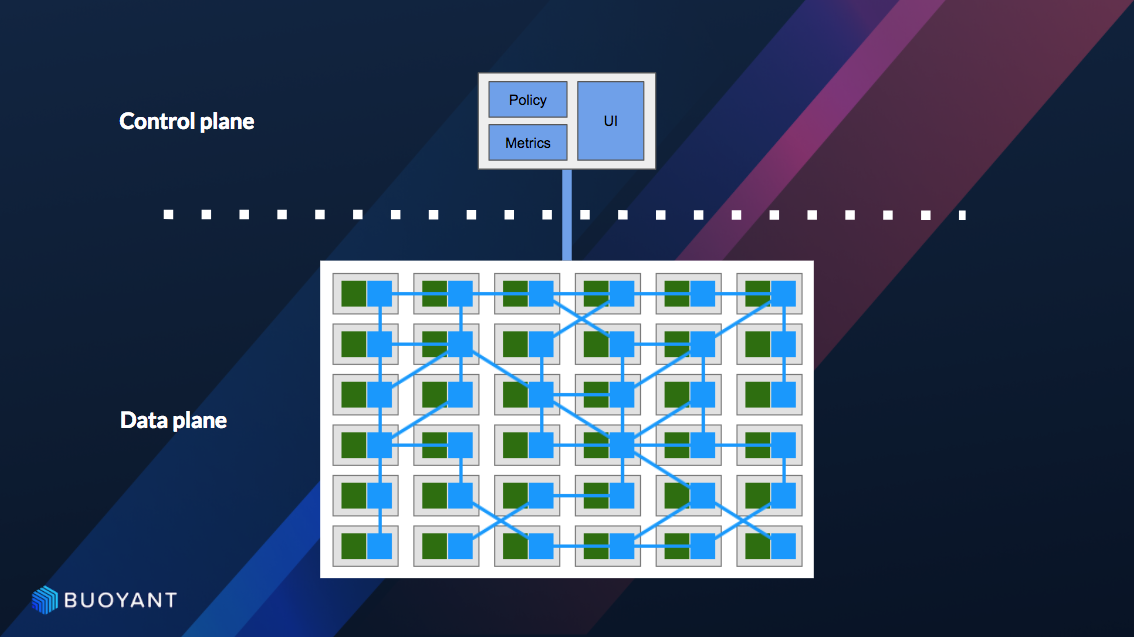
Standalone service meshes offer a complete, self-contained solution for managing microservices within a single application or a tightly coupled set of applications. Unlike lightweight options integrated into existing infrastructure, they provide a dedicated control plane and data plane, offering a higher degree of isolation and control. This approach is particularly well-suited for organizations that prioritize strong security and require fine-grained management of service interactions.
Standalone Service Mesh Architecture
A typical standalone service mesh comprises a control plane and a data plane. The control plane manages the overall configuration and behavior of the mesh, including service discovery, traffic routing, and policy enforcement. It often consists of several components working in concert, such as a control server, a configuration store, and a policy engine. The data plane, on the other hand, consists of proxies (often Envoy) deployed alongside each microservice instance.
These proxies intercept and manage all network traffic, enforcing policies defined by the control plane. Communication between the control plane and the data plane is crucial for dynamic configuration updates and real-time monitoring. Imagine a central command center (control plane) directing individual traffic controllers (data plane proxies) at each intersection (microservice).
Advantages of Standalone Service Meshes
Standalone service meshes offer several key advantages. Their dedicated architecture allows for robust security features, such as mutual TLS authentication and authorization, providing a high level of protection against unauthorized access. They also facilitate advanced traffic management capabilities, including A/B testing, canary deployments, and fault injection, enabling more controlled and reliable deployments. Furthermore, the dedicated control plane provides centralized observability and monitoring, offering comprehensive insights into service performance and behavior.
This detailed insight enables proactive identification and resolution of issues.
Challenges and Drawbacks of Standalone Service Meshes
While offering significant benefits, standalone service meshes also present challenges. Their complexity can lead to increased operational overhead, requiring specialized expertise to manage and maintain the mesh effectively. The added layer of indirection introduced by the proxies can increase latency, although modern proxies are optimized to minimize this impact. Furthermore, integrating a standalone mesh into an existing infrastructure can be complex and potentially disruptive, requiring careful planning and execution.
Finally, the cost of licensing and maintaining a standalone solution can be significant, especially for larger deployments.
Optimal Scenario for a Standalone Service Mesh
A standalone service mesh is the optimal choice when strong security and fine-grained control over service interactions are paramount. Consider a financial institution deploying a new microservices-based application handling sensitive customer data. A standalone service mesh, with its robust security features like mutual TLS and advanced authorization policies, would be crucial to protect against unauthorized access and data breaches.
The centralized observability features would also enable the institution to closely monitor application performance and quickly identify and respond to potential security threats. The added complexity and operational overhead would be justifiable given the high stakes involved in protecting sensitive financial data.
Lightweight Service Mesh Options

Lightweight service meshes offer a compelling alternative to their heavyweight counterparts, particularly for smaller deployments or those prioritizing simplicity and performance. They provide many of the benefits of a full-fledged service mesh—like service discovery, routing, and resilience—but with a significantly reduced operational overhead. This makes them ideal for teams who want the advantages of a service mesh without the complexity of managing a large, distributed control plane.Lightweight service meshes typically focus on a smaller set of features, often integrating directly into the application code or leveraging sidecar proxies with minimal functionality.
This streamlined approach results in lower resource consumption and improved performance compared to standalone solutions. This often means faster deployments, less operational overhead, and potentially lower infrastructure costs.
Key Characteristics of Lightweight Service Meshes
Lightweight service meshes are defined by their minimal footprint and focus on essential features. They prioritize ease of deployment and management, often foregoing advanced features like sophisticated traffic management policies or extensive observability capabilities found in standalone solutions. Instead, they concentrate on providing core functionality such as service discovery, basic routing, and resilience patterns like retries and circuit breaking.
This reduced scope translates to faster startup times, lower resource utilization (CPU, memory, network), and simplified operations. A lightweight mesh might rely on simple configuration files or environment variables, rather than a complex control plane.
Performance Comparison: Lightweight vs. Standalone Service Meshes
In terms of performance, lightweight service meshes generally outperform standalone solutions. This advantage stems from their reduced complexity and smaller attack surface. The overhead introduced by a lightweight mesh is significantly less than that of a standalone mesh, leading to improved latency and higher throughput. For example, a standalone service mesh might introduce several milliseconds of latency per request due to its complex routing and policy enforcement mechanisms.
A lightweight mesh, on the other hand, might add only a fraction of a millisecond, making it virtually imperceptible in many applications. This performance difference becomes especially critical in high-throughput environments where even small latency increases can significantly impact overall performance.
Best Practices for Deploying and Managing a Lightweight Service Mesh
Successful deployment and management of a lightweight service mesh hinge on a few key practices. First, choosing the right mesh for your specific needs is crucial. Consider factors like the size of your application, the complexity of your microservices architecture, and your team’s expertise. Next, thorough testing is essential to ensure the mesh integrates seamlessly with your existing infrastructure and doesn’t introduce unexpected performance bottlenecks.
Regular monitoring of key metrics such as latency, throughput, and error rates is also crucial for identifying and resolving potential issues. Finally, adopting a robust CI/CD pipeline for automated deployment and updates is essential for efficient management and continuous improvement.
Integrating a Lightweight Service Mesh into an Existing Microservices Architecture: A Step-by-Step Guide
Integrating a lightweight service mesh into an existing microservices architecture can be achieved through a phased approach.
- Assessment: Begin by evaluating your current architecture, identifying potential bottlenecks, and defining your requirements for service discovery, routing, and resilience. This assessment helps in selecting the most suitable lightweight service mesh.
- Pilot Project: Choose a small subset of your microservices for a pilot implementation. This allows you to test the mesh’s functionality and performance in a controlled environment before deploying it across the entire system. This minimizes risk and allows for iterative refinement.
- Gradual Rollout: Once the pilot project is successful, gradually roll out the mesh to other microservices. This phased approach reduces the impact of any potential issues and allows for continuous monitoring and adjustments.
- Monitoring and Optimization: Continuously monitor the mesh’s performance and adjust configurations as needed. This iterative process ensures optimal performance and stability.
- Documentation and Training: Maintain comprehensive documentation and provide training to your team on the mesh’s functionalities and operational procedures. This ensures smooth operation and facilitates troubleshooting.
Choosing the Right Solution
Picking the perfect service mesh—standalone or lightweight—depends heavily on your specific needs. It’s not a one-size-fits-all situation, and making the wrong choice can lead to performance bottlenecks, security vulnerabilities, or increased operational complexity. This section will help you navigate the decision-making process by considering key factors.Application size and complexity significantly impact service mesh selection. Smaller, simpler microservice architectures might find a lightweight solution perfectly adequate.
The overhead of a full-blown standalone mesh might be unnecessary and even detrimental to performance. Conversely, large, complex applications with stringent security and observability requirements often benefit from the advanced features and robust capabilities of a standalone service mesh. For example, a small startup with a handful of microservices might thrive with a lightweight solution like Linkerd, while a large e-commerce platform handling millions of transactions daily would likely need the power and control of Istio.
Infrastructure and Deployment Environment Influence
The infrastructure and deployment environment play a crucial role. A cloud-native environment with Kubernetes often pairs well with standalone meshes designed for seamless integration. These meshes leverage Kubernetes features for service discovery, configuration management, and other functionalities. On the other hand, if you’re operating in a less dynamic environment, perhaps with virtual machines or bare metal servers, a lightweight mesh might be easier to deploy and manage, minimizing the complexity of integrating with your existing infrastructure.
Consider the level of automation and orchestration already in place; a standalone mesh will generally require more sophisticated infrastructure management.
Security Requirements Impact on Mesh Selection
Security is paramount. Standalone service meshes typically offer more comprehensive security features, including advanced authentication, authorization, and encryption capabilities. They often provide robust policy enforcement mechanisms and fine-grained control over traffic flow. Lightweight options may offer basic security features, but they often lack the sophisticated functionalities of their standalone counterparts. For applications handling sensitive data or requiring stringent security compliance, a standalone mesh is usually the safer choice.
For example, a financial institution processing transactions would prioritize the robust security features of a standalone mesh like Istio over the simpler features of a lightweight mesh.
Decision Tree for Service Mesh Selection
Choosing between a standalone and lightweight service mesh involves careful consideration of several factors. The following decision tree provides a structured approach:
- Application Size and Complexity:
- Small, simple application: Proceed to Lightweight Mesh Evaluation.
- Large, complex application: Proceed to Standalone Mesh Evaluation.
- Infrastructure and Deployment Environment:
- Cloud-native (Kubernetes): Favor Standalone Mesh (better integration).
- Non-cloud-native (VM, bare metal): Consider Lightweight Mesh (simpler deployment).
- Security Requirements:
- High security needs (sensitive data, strict compliance): Choose Standalone Mesh (robust security features).
- Moderate security needs: Evaluate both options based on specific requirements.
Illustrative Examples
Let’s explore concrete scenarios to understand when a standalone service mesh shines and when a lightweight alternative is more appropriate. We’ll examine the architecture, benefits, and trade-offs of each approach in the context of a hypothetical microservices application.This section provides two contrasting examples: a high-transaction volume e-commerce platform and a smaller, internal application for managing employee data. These examples highlight the different needs and considerations involved in choosing between a standalone and a lightweight service mesh.
Standalone Service Mesh: E-commerce Platform
Imagine a large-scale e-commerce platform with hundreds of microservices handling various aspects like product catalog, shopping cart, payment processing, order management, and inventory. This system experiences extremely high traffic, demanding robust traffic management, advanced security features, and fine-grained observability. A standalone service mesh like Istio or Linkerd would be ideal here. Its comprehensive feature set allows for advanced traffic routing, sophisticated security policies (like mutual TLS authentication), and detailed monitoring capabilities crucial for maintaining uptime and performance under heavy load.The network topology would look something like this:“` +——–+ | API | +——–+ | +———————–+———————–+ | | | +——-+——-+ +——-+——-+ +——-+——-+ | Catalog Service | | Cart Service | | Payment Service | +——-+——-+ +——-+——-+ +——-+——-+ | | | +———————–+———————–+ | +——–+ | DB | +——–+Istio/Linkerd Control Plane – ————————
Manages all service communication
Enforces security policies
Monitors and reports on traffic
“`The standalone service mesh acts as a central control plane, managing all communication between services, ensuring security, and providing comprehensive observability. This centralized approach offers the best control and scalability for high-traffic, mission-critical applications.
Lightweight Service Mesh: Employee Data Management
Consider a smaller, internal application for managing employee data within a company. This application consists of a handful of microservices responsible for tasks like user authentication, data storage, and reporting. The traffic volume is significantly lower compared to the e-commerce platform, and the need for advanced features is less critical. A lightweight service mesh like Consul Connect or Kuma would be a more suitable choice.
These solutions provide basic service discovery, routing, and security features without the overhead of a full-fledged standalone mesh.The network topology in this case is simpler:“` +——-+——-+ +——-+——-+ +——-+——-+ | Auth Service | | Data Service| | Reporting Service| +——-+——-+ +——-+——-+ +——-+——-+ | | | +———————–+———————–+ | +——–+ | DB | +——–+Consul Connect/Kuma Control Plane – —————————–
Provides service discovery
Enables secure communication between services
Offers basic monitoring capabilities
“`The lightweight service mesh provides essential capabilities without adding excessive complexity or overhead. This is ideal for smaller applications where the benefits of a full-fledged service mesh may not outweigh the added operational burden.
Future Trends and Considerations

The landscape of service mesh technologies is dynamic, constantly evolving to meet the demands of increasingly complex and distributed applications. Standalone and lightweight solutions will continue to adapt, driven by advancements in cloud-native architectures and the emergence of new paradigms like serverless computing. Understanding these trends is crucial for making informed decisions about deploying and managing service meshes effectively.The next few years will likely witness a convergence of features between standalone and lightweight service meshes.
Lightweight solutions may incorporate more advanced functionalities currently associated with standalone meshes, while standalone offerings may become more streamlined and resource-efficient. This will blur the lines somewhat, potentially offering more choice in selecting the right fit for a given application’s needs.
Impact of Serverless Computing
Serverless computing’s rise significantly impacts service mesh design. Traditional service meshes assume a relatively stable pool of microservices running continuously. However, serverless functions are ephemeral, invoked only when needed. This necessitates service mesh architectures that can dynamically manage the lifecycle of these short-lived functions, efficiently routing traffic and applying security policies without incurring unnecessary overhead. We’re already seeing the development of service mesh extensions specifically designed for serverless environments, capable of handling the unique challenges posed by function-as-a-service (FaaS) platforms like AWS Lambda or Google Cloud Functions.
These extensions often leverage features like automatic sidecar injection and dynamic configuration to seamlessly integrate with serverless deployments. For example, a serverless function might automatically receive a sidecar upon invocation, ensuring consistent observability and security policies are applied. This dynamic approach contrasts sharply with the more static configuration typically found in traditional service mesh deployments targeting long-running microservices.
Choosing between a standalone service mesh solution and a lightweight option depends heavily on your application’s complexity and scalability needs. If you’re building modern apps, understanding the development landscape is key, and that’s where learning about domino app dev, the low-code and pro-code future , comes in handy. This knowledge helps you make informed decisions about your architecture, ultimately influencing whether a full-blown mesh or a simpler approach is the right fit for your project.
Evolution of Operational Overhead
Operational overhead is a key concern for both standalone and lightweight service meshes. Standalone solutions, with their richer feature sets, inherently require more management. However, advancements in automation and orchestration, such as improved control planes and automated policy management, are reducing this burden. Machine learning (ML) is also beginning to play a role, enabling predictive scaling and automated troubleshooting, potentially mitigating the complexity associated with managing a large-scale standalone service mesh.
Lightweight meshes, while simpler to operate, may see increased overhead as they integrate more advanced features. For instance, adding features like advanced traffic management or sophisticated security policies will inevitably increase resource consumption and management requirements. The balance between functionality and operational simplicity will remain a critical factor in choosing the appropriate solution. Consider, for example, a large enterprise adopting a standalone mesh.
The initial operational overhead might be significant, but the investment in automation and ML-driven tools could dramatically reduce this burden over time, making it more manageable than initially anticipated. Conversely, a smaller company starting with a lightweight mesh might find that adding advanced features later significantly increases their operational burden, potentially necessitating a shift to a more robust solution.
Wrap-Up
Ultimately, the choice between a standalone and lightweight service mesh hinges on your application’s specific requirements. Consider the complexity of your microservices architecture, your infrastructure capabilities, and your security needs. By carefully weighing the pros and cons of each approach and using the decision tree Artikeld in this post, you can confidently select the service mesh solution that best supports your current and future goals.
Remember, the right choice ensures optimal performance, scalability, and security for your applications.
Expert Answers: Standalone Service Mesh Solution Or Lightweight Option Which Is Right For You
What are the typical costs associated with each type of service mesh?
Costs vary widely depending on the specific solution, vendor, and your infrastructure. Standalone meshes often involve higher upfront investment in infrastructure and management, while lightweight options might have lower initial costs but potentially higher operational costs over time.
How do I choose between Istio and Linkerd?
Istio and Linkerd are both popular service mesh solutions, but they differ in their complexity and features. Istio is a more feature-rich and complex solution, while Linkerd is simpler and more lightweight. The best choice depends on your needs and technical expertise.
Can I migrate from a lightweight to a standalone service mesh later?
Yes, it’s generally possible to migrate, although it might require significant effort and planning. The complexity of the migration will depend on the size and complexity of your application and the specific service mesh solutions involved.
What about security considerations for each option?
Both standalone and lightweight service meshes offer robust security features, but their implementation and management differ. Standalone meshes often provide more comprehensive security features out-of-the-box, but require more complex configuration and management. Lightweight meshes may require additional tools and integrations to achieve comparable security levels.