Application Security
-
Cybersecurity
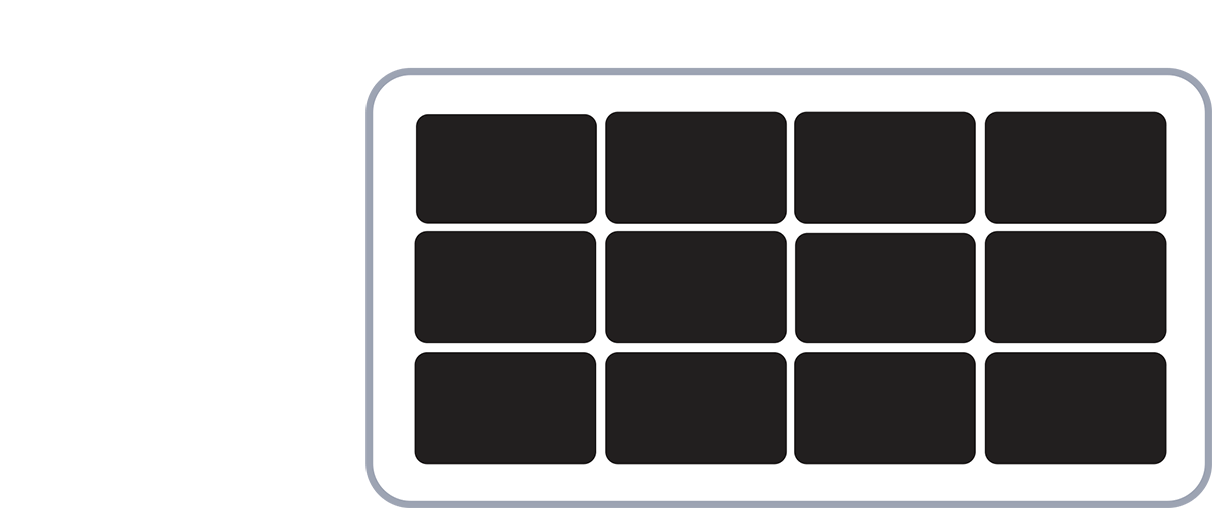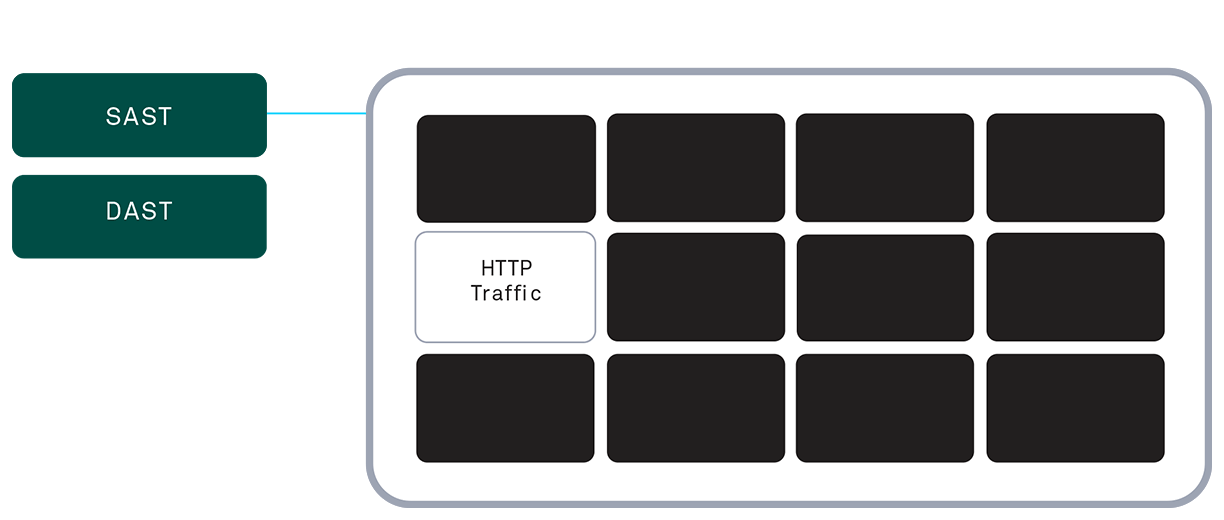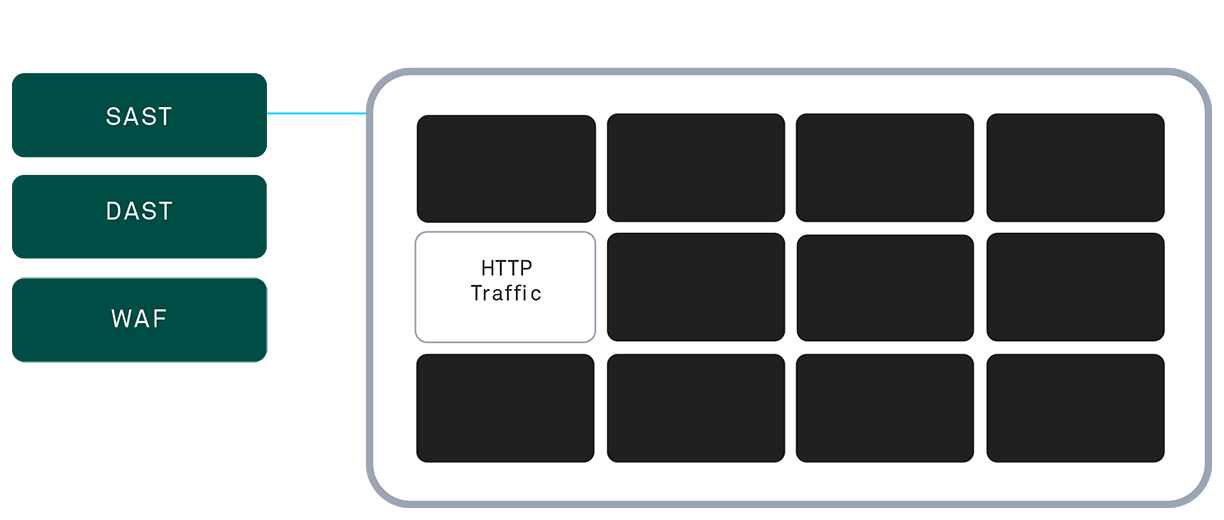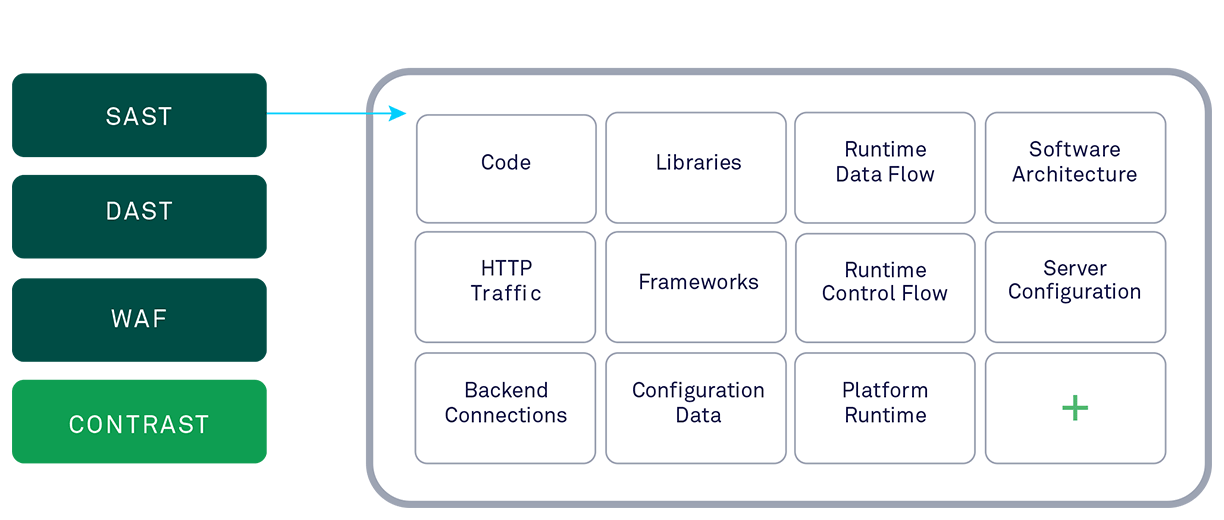
IAST, RASP, and Runtime Instrumentation Securing Apps
Iast rasp and runtime instrumentation – IAST, RASP, and runtime instrumentation are crucial for securing applications. This exploration delves into…
Read More » -
Technology

Zero Trust CIO & CTO Advantage in Corporate Environments
How zero trust helps CIOs and CTOs in corporate environments is a critical issue. Zero trust security is rapidly reshaping…
Read More » -
Cybersecurity
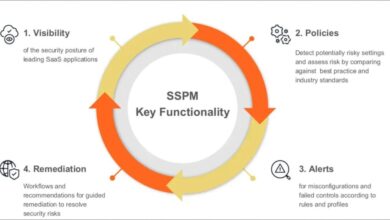
How to Secure Your Apps with SaaS Security Posture Management (SSPM)
How to secure your apps with saas security posture management sspm – How to secure your apps with SaaS security…
Read More » -
Cybersecurity

ASPM Saving Costs & Filling CSPM Gaps
How financial services firms can use application security posture management aspm to save costs and fill cloud security posture management…
Read More » -
Tech Acquisitions
F5 to Acquire Volterra Cloud Securitys Next Chapter
F5 to acquire cloud based application security provider volterra – F5’s acquisition of Volterra, a cloud-based application security provider, is…
Read More » -
Cybersecurity

Exploring Different Types of Cybersecurity Protecting the Digital Realm
Exploring different types of cybersecurity protecting the digital realm is more crucial than ever. Our increasingly digital lives leave us…
Read More » -
Cybersecurity

Exploring Cybersecurity Research Topics for Masters Studies
Exploring cybersecurity research topics for masters degree studies is more than just picking a subject; it’s about diving headfirst into…
Read More » -
Software Development

Build Smarter, More Secure Applications with PulseVADC Community Edition
Build smarter more secure applications with pulse vadc community edition – Build smarter, more secure applications with PulseVADC Community Edition!…
Read More » -
Cybersecurity

Aqua Security CNAPP Frictionless Cloud Workload Protection
Aqua security cnapp is first to combine frictionless cloud workload visibility with active protection across the application lifecycle 2 –…
Read More » -
Software Development

7 Steps to Secure Design Patterns A Robust Software Security Foundation
7 Steps to implement secure design patterns a robust foundation for software security – that’s what we’re diving into today!…
Read More »
