cloud security
-
Cloud Security

How to Secure Virtual Machines VMs in Cloud Computing Environments
How to secure virtual machines VMs in cloud computing environments is a crucial topic for anyone working with cloud infrastructure.…
Read More » -
Cloud Security
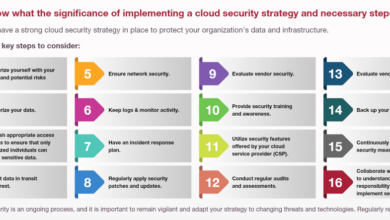
Securing Cloud Strategies for CSPs Malware Mitigation
Securing the cloud strategies for csps to mitigate malware hosting risks – Securing cloud strategies for CSPs to mitigate malware…
Read More » -
Cybersecurity

Is Microsoft Grappling With a DDoS Cyber Attack?
Is microsoft chatgpt grappling with ddos cyber attack – Is Microsoft grappling with a DDoS cyber attack? That’s the question…
Read More » -
Cloud Security

Cloud Security Right Preparation is Key
Cloud security is best achieved with the right preparation. Think of it like building a house – you wouldn’t start…
Read More » -
Cybersecurity

Enhancing Visibility with Bitglass and Splunk 2
Enhancing visibility with Bitglass and Splunk 2 is a game-changer for security. This powerful duo offers unparalleled insight into your…
Read More » -
Cloud Security

Cloud Security That Performs A Deep Dive
Cloud security that performs isn’t just about ticking boxes; it’s about building a robust, responsive system that proactively protects your…
Read More » -
Cybersecurity

Hackers Breach Verkadas Cloud Camera Systems
Hackers breach systems of cloud based security camera company Verkada – a chilling headline that highlights the vulnerability of even…
Read More » -
Cybersecurity

Ransomware Attack on Cloud Company NetGain
Ransomware attack on cloud company NetGain – sounds scary, right? It was. This wasn’t just another small-scale incident; we’re talking…
Read More » -
Cloud Computing

Embrace Hyper Automation for Seamless Cloud Migration
Embrace hyper automation for seamless cloud migration: It sounds futuristic, right? But the truth is, smoothly transitioning your systems to…
Read More » -
DevOps

Heres What Secure DevOps Looks Like in Action
Heres what secure devops looks like in action – Here’s what Secure DevOps looks like in action: Forget the image…
Read More »
