cloud security
-
Technology Acquisitions

HPE Acquires Scytale Cloud Security Boost
HPE acquires cloud security startup Scytale, marking a significant move in the rapidly evolving cloud security landscape. This acquisition promises…
Read More » -
Cybersecurity
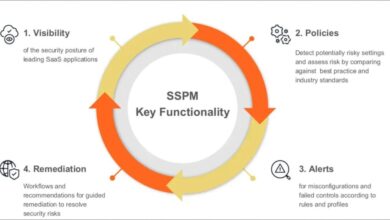
How to Secure Your Apps with SaaS Security Posture Management (SSPM)
How to secure your apps with saas security posture management sspm – How to secure your apps with SaaS security…
Read More » -
Business

Securing Customer Data in the AI Cloud Age
How to secure customer data in the age of AI and cloud computing sets the stage for this enthralling narrative,…
Read More » -
Cybersecurity
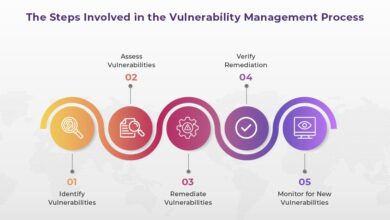
Future-Proofing Vulnerability Management
How to prepare for the future of vulnerability management is crucial in today’s rapidly evolving threat landscape. Cybersecurity threats are…
Read More » -
Cloud Security

Multi-Cloud Security How-to Guide
How to maintain security across multi cloud environments – How to maintain security across multi-cloud environments is crucial in today’s…
Read More » -
Data Security
How to Achieve Maximum Security in Virtualized Data Centers
How to achieve maximum security in virtualized data centers is a critical concern for organizations today. Virtualization offers agility and…
Read More » -
Network Security

How Security Service Edge Revolutionizes Network Security
How security service edge is revolutionizing network security by fundamentally shifting the way we approach network security. It’s moving beyond…
Read More » -
Cybersecurity

ASPM Saving Costs & Filling CSPM Gaps
How financial services firms can use application security posture management aspm to save costs and fill cloud security posture management…
Read More » -
Data Management
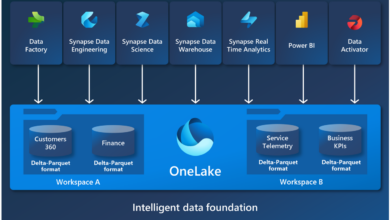
How Data Fabric Boosts Security Governance
How data fabric architecture helps enhance security governance is crucial in today’s data-driven world. Data fabric provides a flexible and…
Read More » -
Small Business

How Cloud Boosts SMB Security
How cloud can help SMBs overcome IT security concerns is a crucial topic. Small and medium-sized businesses often face unique…
Read More »
