Cybersecurity
-
Cybersecurity
Intel Zombieload Hacker Target
Intel Zombieload vulnerability might expose sensitive data like passwords to hackers. This sophisticated attack leverages a previously unknown flaw in…
Read More » -
Technology

Intel Processors Recognizing Ransomware at Hardware Level
Intel processors to recognize ransomware attacks at hardware level sets the stage for a fascinating new approach to cybersecurity. This…
Read More » -
Cybersecurity
Intel & Check Point Ransomware Defense Partnership
Intel and Check Point software extend partnership for ransomware protection, forging a powerful alliance to combat the escalating threat of…
Read More » -
Risk Management
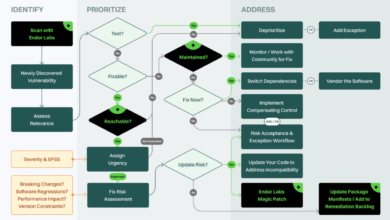
Lightspeed Remediation Integrated Risk Prioritization
Integrated risk prioritization for lightspeed remediation is crucial for navigating the complexities of fast-paced risk mitigation. This approach allows organizations…
Read More » -
Business & Finance

Cyber Insurance A Failing Safety Net
Insurance cover becoming impossible for cyber attacks is a growing concern. Businesses are facing an escalating threat landscape, with increasingly…
Read More » -
Government & Politics

State-Funded Cyber Attacks Insurance Withdrawal
Insurance company says it will no longer cover state funded cyber attacks – Insurance company says it will no longer…
Read More » -
Business Insurance

Insurance Companies Now Cover Ransomware Cyber Attacks
Insurance companies are now covering ransomware cyber attacks, signaling a significant shift in how businesses approach digital security risks. This…
Read More » -
Cybersecurity

Insurance Companies Paying Ransom A Growing Trend
Insurance companies are insisting to pay ransom for ransomware attacks, a disturbing new development in the ongoing cybercrime crisis. This…
Read More » -
Business Management

Insufficient Mobile Security Business Enterprises at Risk
Insufficient mobile security business enterprises at risk face significant vulnerabilities in today’s digital landscape. From financial losses and reputational damage…
Read More » -
Cybersecurity

Insider Threats Detect, Remediate, Prevent Attacks – Live Webinar
Insider threats detect remediate prevent insider attacks live webinar. This webinar dives deep into the insidious world of insider threats,…
Read More »
