Cybersecurity
-
Politics

Googles Election Security Initiative
Google decides to offer cyber security for countries hosting elections, a bold move that promises significant changes to how elections…
Read More » -
Cloud Computing

Google Clouds Advanced Security Alliance
Google cloud partners with mcafee palo alto networks and deloitte for advanced security – Google Cloud partners with McAfee, Palo…
Read More » -
Technology

Google Cloud Completes Mandiant Acquisition for $5.4 Billion
Google cloud completes mandiant acquisition for 5 4 billion – Google Cloud completes Mandiant acquisition for $5.4 billion – a…
Read More » -
Cloud Computing
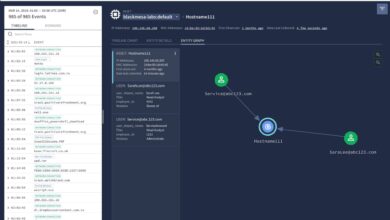
Google Cloud Launches Chronicle CyberShield Enhanced Security
Google Cloud launched Chronicle CyberShield, a game-changer in security monitoring. This new offering promises a more robust and comprehensive approach…
Read More » -
Cybersecurity

Google Blocks Worlds Largest DDoS Cyber Attacks
Google blocks worlds largest ddos cyber attacks – Google blocks world’s largest DDoS cyber attacks – that’s a headline that…
Read More » -
Cybersecurity

Google Bans JavaScript Attachments Due to Rising Cybersecurity Concerns
Google bans javascript attachments due to rising cyber security concerns – Google bans JavaScript attachments due to rising cybersecurity concerns…
Read More » -
Technology
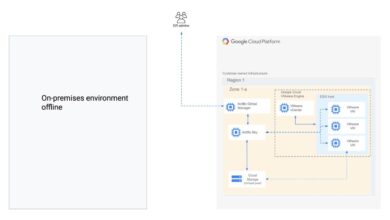
Google Acquires Actifio for Cloud Security
Google acquires Actifio for cloud security—a move that’s sent ripples through the tech world! This acquisition isn’t just another corporate…
Read More » -
Cybersecurity

GoDaddy Data Breach Could Lead to Phishing Attacks
GoDaddy data breach could lead to phishing attacks – that’s the chilling reality facing millions. This massive security lapse exposed…
Read More » -
Technology

Global Internet Shutdown to Avoid Future Cyber Attacks
Global Internet Shutdown to Avoid Future Cyber Attacks: Imagine a world plunged into digital darkness, a drastic measure taken to…
Read More » -
Cybersecurity

Getting Real About Ransomware
Getting real about ransomware means facing the harsh reality of this ever-evolving threat. It’s not just a tech problem; it’s…
Read More »
