Data Breaches
-
Cybersecurity News

A Synopsis of This Weeks Cyber Attack News
A synopsis of this weeks cyber attack news – A synopsis of this week’s cyber attack news reveals a disturbing…
Read More » -
Cybersecurity

A Surge in Ransomware Attacks Against Universities
A surge in ransomware attacks against universities is alarmingly escalating, targeting vital research data, student records, and operational systems. These…
Read More » -
Online Security

A New Age of Threats in Online Shopping Cybersecurity Tips
A new age of threats in online shopping cybersecurity tips is crucial now more than ever! Online shopping has become…
Read More » -
Cybersecurity

A Briefing on What We Know Now on Insider Threats
A briefing on what we know now on insider threats sets the stage for a fascinating exploration of a critical…
Read More » -
Education Technology

UK NCSC Issues Cybersecurity Warning to Schools & Universities
Uk ncsc issues cybersecurity warning to schools n universities – UK NCSC Issues Cybersecurity Warning to Schools & Universities –…
Read More » -
Cybersecurity

12 Common Concerns of the Permeable IoT Attack Surface
12 Common Concerns of the Permeable IoT Attack Surface: Ever felt that nagging unease when your smart devices are “too”…
Read More » -
Cybersecurity

Hacktivists Turning to Ransomware Spread
Hacktivists turning to ransomware spread is a chilling trend reshaping the digital landscape. It’s no longer just about making a…
Read More » -
Cybersecurity

Vulnerable US States A Cyberattack Risk List
List of vulnerable states in america that are vulnerable to cyber attacks – Vulnerable US States: A Cyberattack Risk List…
Read More » -
Cybersecurity

Russian Ransomware Criminals Earn $500 Million
Russian ransomware criminals earn 500 million – that’s the staggering figure that has sent shockwaves through the cybersecurity world. This…
Read More » -
Cybersecurity
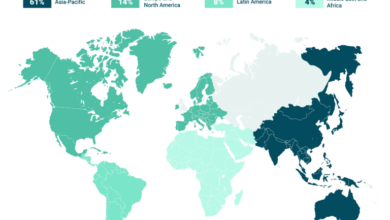
Top 10 Industries Most Vulnerable to Cyber Attacks
Top 10 industries most vulnerable to cyber attacks – it’s a headline that grabs your attention, right? We live in…
Read More »
