data security
-
Cybersecurity

DSPM Essential for Gen AI & Copilot Tool Deployment
Data security posture management dspm is an important first step in deploying gen ai and copilot tools – Data security…
Read More » -
Science & Technology

Russian Scientists Develop New Communication Through Quantum Teleportation
Russian scientists develop new communication medium through quantum teleportation – a groundbreaking achievement that could revolutionize secure communication and data…
Read More » -
Data Security & Privacy

The Risks of Sharing Business Data with AI
The risks of sharing business data with AI are far-reaching and often underestimated. While AI offers incredible potential for streamlining…
Read More » -
Cybersecurity

Ransomware Gangs Doxing Victims Families
Ransomware gangs doxing family members of victims is a terrifying new escalation in cybercrime. It’s no longer just about encrypting…
Read More » -
Cybersecurity

Top 5 PCI Compliance Mistakes and How to Avoid Them
Top 5 PCI Compliance Mistakes and How to Avoid Them: Navigating the complex world of PCI compliance can feel like…
Read More » -
Cybersecurity
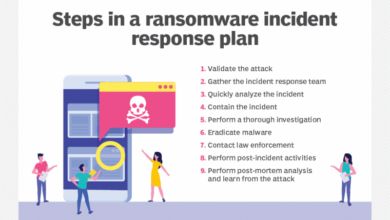
Harnessing AI to Thwart Ransomware Threats A Strategic Approach
Harnessing ai to thwart ransomware threats a strategic approach – Harnessing AI to thwart ransomware threats: a strategic approach. That’s…
Read More » -
Cybersecurity
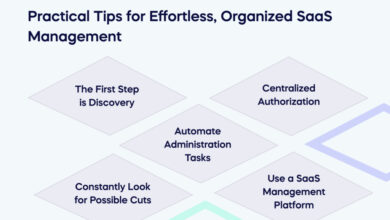
8 Tips to Protect Your Organization in the Evolving SaaS Landscape
8 Tips to Protect Your Organization in the Evolving SaaS Landscape: The world of Software as a Service (SaaS) is…
Read More » -
Cybersecurity

Future-Proofing Cybersecurity A Deep Dive into WithSecure
Future proofing cybersecurity a deep dive into withsecures innovative mid market security solutions – Future-proofing cybersecurity: a deep dive into…
Read More » -
Cybersecurity

Eight Ways to Bolster Your Cybersecurity Resources Without Blowing Your Budget
Eight Ways to Bolster Your Cybersecurity Resources Without Blowing Your Budget – that’s the dream, right? We all want rock-solid…
Read More » -
Cybersecurity

Encryptionless Ransomware Desais Defense Strategies
Encryptionless ransomware attacks and defense strategies an interview with zscalers deepen desai – Encryptionless ransomware attacks and defense strategies an…
Read More »
