data security
-
Cybersecurity
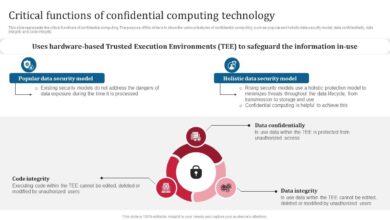
Exploring the Essence of Confidential Computing
Exploring the essence of confidential computing, we delve into a fascinating world where data security reaches unprecedented levels. Imagine a…
Read More » -
Cybersecurity

Exploring Different Types of Cybersecurity Protecting the Digital Realm
Exploring different types of cybersecurity protecting the digital realm is more crucial than ever. Our increasingly digital lives leave us…
Read More » -
Cybersecurity
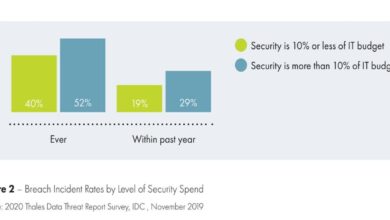
Expert Comments on Five Guys Data Breach
Expert comments on Five Guys data breach are all over the internet, and for good reason! This massive security incident…
Read More » -
European Union Politics

EU Proposes Joint Cyber Unit for Large-Scale Attacks
European Union proposes joint cyber unit for large scale cyber attacks – a bold move in the face of increasingly…
Read More » -
Cybersecurity News

Europe Witnesses Simulated Cyberattack on Retail
Europe witnesses a simulated cyber attack on retail sector – a chilling scenario that highlighted the vulnerability of European retailers…
Read More » -
Cybersecurity

Essential Data Protection Starts With Least Privilege
Essential data protection starts with least privilege: That’s the core message I want to hammer home today. We’re all bombarded…
Read More » -
Cybersecurity

Equifax Data Breach Settlement $20,000 Per Victim?
Equifax data breach settlement of 20000 per victim – Equifax data breach settlement of $20,000 per victim? It sounds too…
Read More » -
IT Security
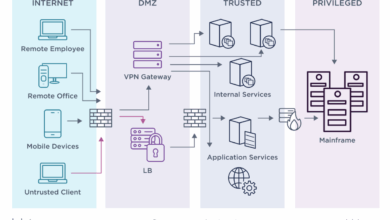
Enterprise Information Networks and the Threat Environment
Enterprise information networks and the threat environment are more intertwined than ever. Think about it – your company’s entire digital…
Read More » -
Cybersecurity

Ensuring Data Security with Remote Workers
Ensuring data security with remote workers is more critical than ever. The rise of remote work has dramatically expanded the…
Read More » -
IT Security

Ensuring Data Security in Slack
Ensuring data security in Slack isn’t just about ticking boxes; it’s about building a robust, secure environment for your team’s…
Read More »
