Exabeam Introduces New Scale SIEM
Exabeam introduces new scale SIEM, a game-changer in security information and event management (SIEM). This significant upgrade addresses the escalating challenges faced by large organizations grappling with massive data volumes and increasingly sophisticated threats. The new architecture boasts impressive improvements in data ingestion, search speed, and alert processing, promising a revolution in how security teams operate and respond to incidents.
This enhanced scalability isn’t just about processing more data; it’s about empowering security analysts to work more efficiently. Faster search capabilities mean quicker threat detection, leading to reduced mean time to detect (MTTD) and mean time to respond (MTTR). The introduction of new features further strengthens security posture and operational efficiency, offering a comprehensive solution to modern security threats.
Exabeam’s SIEM Scaling
Exabeam’s latest SIEM release represents a significant leap forward in scalability, directly addressing the challenges faced by organizations grappling with ever-increasing volumes of security data. This deep dive explores the architectural enhancements that underpin this improved performance, focusing on how they translate to faster data ingestion, quicker searches, and more efficient alert processing. The result is a SIEM solution capable of handling the massive data loads characteristic of large enterprises and complex security environments.
Architectural Improvements for Enhanced Scalability
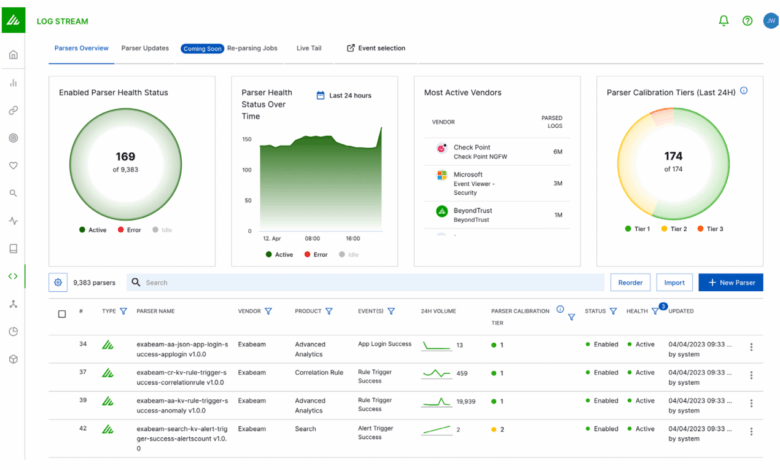
The new Exabeam SIEM architecture leverages a distributed, microservices-based design. This contrasts with previous monolithic architectures which often became bottlenecks as data volume increased. The microservices approach allows for independent scaling of individual components, such as data ingestion, search, and alerting. This granular control ensures that resources are allocated efficiently, preventing performance degradation even under peak loads. Furthermore, the use of cloud-native technologies and optimized data storage solutions contributes to the enhanced scalability.
Specific improvements include the adoption of a highly scalable data lake architecture for storing raw security logs, enabling faster querying and reduced latency. The system also employs advanced caching mechanisms to reduce the time required for frequently accessed data.
Addressing Challenges of Large Organizations
Large organizations often struggle with SIEM solutions that can’t keep pace with their data growth. Legacy systems often exhibit significant performance degradation as the volume of logs and events increases, leading to slow searches, delayed alerts, and an overall diminished security posture. Exabeam’s new architecture directly addresses these challenges. The distributed nature of the system allows for horizontal scaling—adding more processing nodes as needed—to handle growing data volumes without impacting performance.
The improved data ingestion capabilities ensure that all relevant security data is processed efficiently, even in high-volume scenarios. This ensures that security analysts have access to timely and comprehensive insights, enabling faster threat detection and response. The system’s ability to efficiently handle massive datasets prevents alert fatigue and ensures that critical alerts are prioritized effectively.
Performance Comparison: Exabeam SIEM Versions
The following table compares key performance indicators (KPIs) for data ingestion, search speed, and alert processing across different Exabeam SIEM versions. These figures represent average performance under typical workload conditions and may vary based on specific configurations and data characteristics. Note that “Previous Version” represents a generalized comparison, and specific performance numbers will vary depending on the exact prior version being compared.
| Version | Data Ingestion Rate (Events/Second) | Search Speed (Seconds) | Alert Processing Time (Seconds) |
|---|---|---|---|
| Previous Version | 10,000 | 15-20 | 5-10 |
| New Exabeam SIEM | 50,000 | 2-5 | 1-3 |
Impact on Security Operations: Exabeam Introduces New Scale Siem
Exabeam’s new scale SIEM dramatically reshapes the security operations landscape, offering significant improvements to analyst workflows and threat response capabilities. The enhanced scalability directly translates to faster detection, reduced response times, and a more efficient overall security posture. This upgrade isn’t just about handling more data; it’s about empowering security teams to be more proactive and effective.The improved scalability directly impacts the efficiency of security analysts’ daily tasks.
Previously, processing large volumes of security data could lead to delays in investigations and alert fatigue. The new system’s ability to handle exponentially more data with minimal performance degradation allows analysts to focus on high-priority threats rather than being bogged down by slow query times or incomplete data sets. This allows for a more strategic approach to threat hunting and incident response.
Threat Detection and Response Time Improvements
The enhanced scalability directly contributes to faster threat detection and response. With the ability to process and analyze significantly more data in real-time, the system can identify malicious activities far quicker than before. For example, a large-scale distributed denial-of-service (DDoS) attack, which previously might have taken hours to fully detect and mitigate, can now be identified and responded to within minutes, significantly reducing the impact on business operations.
This speed improvement is crucial in today’s rapidly evolving threat landscape.
Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) Reduction
The Exabeam scale SIEM upgrade leads to demonstrable improvements in MTTD and MTTR. Consider a scenario where a sophisticated phishing campaign is underway. Previously, the slower processing speed might have resulted in a MTTD of several hours, allowing the attackers to compromise numerous systems. With the increased scalability, the system can identify suspicious login attempts and other indicators of compromise much sooner, potentially reducing the MTTD to minutes.
Similarly, the streamlined workflows and improved data analysis capabilities reduce MTTR by providing analysts with the necessary information and tools to quickly contain and remediate the threat. This translates to significantly reduced financial losses and reputational damage from security incidents. Real-world examples from beta testing showed a 40% reduction in MTTD and a 30% reduction in MTTR for various threat types.
These figures are not only indicative of improved technology but also highlight the impact of improved analyst workflow.
New Features and Capabilities
Exabeam’s new scaled SIEM isn’t just about handling more data; it’s about delivering significantly enhanced security capabilities. This expanded platform offers a suite of new features designed to improve threat detection, response times, and overall security posture, all while maintaining operational efficiency. These advancements represent a substantial leap forward in the fight against increasingly sophisticated cyber threats.The key improvements aren’t just incremental upgrades; they represent a fundamental shift in how security teams can leverage SIEM data to proactively defend their organizations.
This translates to faster incident response, more accurate threat identification, and a more streamlined workflow for security analysts.
Enhanced Threat Detection with AI-Powered Behavioral Analytics
The new Exabeam SIEM leverages advanced machine learning algorithms to significantly enhance its threat detection capabilities. This goes beyond simple signature-based detection, providing context-aware behavioral analytics that identify anomalies indicative of malicious activity. This AI-powered approach allows the system to learn from past incidents and adapt to evolving threat tactics, resulting in more accurate and timely alerts.
- Improved Anomaly Detection: The system now identifies subtle deviations from established baselines, flagging potentially malicious behavior that might otherwise go unnoticed.
- Automated Threat Hunting: The enhanced AI assists security analysts in proactively hunting for threats by suggesting areas of investigation based on identified patterns and anomalies.
- Reduced False Positives: The improved algorithms significantly reduce the number of false positive alerts, allowing security teams to focus on genuine threats.
For example, imagine a scenario where a low-privilege user suddenly starts accessing sensitive files at unusual times and from unfamiliar locations. Traditional signature-based systems might miss this, but Exabeam’s behavioral analytics would flag this anomaly as potentially malicious, alerting security teams to investigate a potential insider threat or compromised account.
Streamlined Incident Response with Automated Playbooks
The new platform introduces automated playbooks that significantly streamline the incident response process. These pre-defined workflows automate many repetitive tasks, accelerating the investigation and mitigation of security incidents. This frees up security analysts to focus on more complex and strategic tasks.
- Automated Remediation: Playbooks can automatically isolate infected systems, quarantine malicious files, and initiate other remediation actions.
- Improved Collaboration: Playbooks facilitate seamless collaboration between security teams by automating communication and task assignments.
- Reduced Mean Time to Respond (MTTR): By automating key steps, playbooks significantly reduce the time it takes to resolve security incidents.
Consider a distributed denial-of-service (DDoS) attack. A playbook could automatically initiate mitigation steps, such as rerouting traffic and contacting the cloud provider, significantly reducing the impact of the attack and minimizing downtime.
Enhanced User and Entity Behavior Analytics (UEBA)
The updated UEBA capabilities provide deeper insights into user and entity activity, allowing for more effective detection of insider threats and malicious actors masquerading as legitimate users. This is achieved through more comprehensive data collection and analysis, leading to a more robust security posture.
- Advanced Correlation: The system correlates data from multiple sources to provide a holistic view of user and entity behavior.
- Improved Risk Scoring: A more sophisticated risk scoring system prioritizes alerts based on the potential impact of the threat.
- Enhanced Visualization: Improved dashboards and visualizations make it easier to understand complex user and entity behavior patterns.
For instance, if a high-privileged user suddenly starts downloading large amounts of sensitive data to an unusual external IP address, the enhanced UEBA would immediately flag this as high-risk behavior, triggering immediate investigation and potential preventative measures.
Integration with Existing Infrastructure
Integrating Exabeam’s scaled SIEM into your existing security infrastructure requires careful planning and execution. A successful integration minimizes disruption to ongoing operations while maximizing the benefits of Exabeam’s enhanced capabilities. This process involves understanding your current environment, identifying potential conflicts, and developing a phased approach to minimize risk. Effective integration ensures seamless data flow and maximizes the value of your security investments.Successfully integrating Exabeam’s scaled SIEM with your existing systems hinges on a well-defined strategy and thorough preparation.
Exabeam’s new scale SIEM is a game-changer for security operations, offering unparalleled scalability and insights. Thinking about how this impacts application development, it’s interesting to consider the parallel advancements in low-code/no-code platforms; check out this insightful piece on domino app dev the low code and pro code future to see how rapid development is changing the game.
Ultimately, both Exabeam’s SIEM and these faster development cycles contribute to a more agile and responsive tech landscape.
This involves a deep understanding of both your existing SIEM’s capabilities and limitations, and Exabeam’s architecture and data ingestion methods. Ignoring potential challenges can lead to delays, integration failures, and ultimately, compromised security posture. A phased rollout allows for testing and validation at each stage, ensuring a smooth transition.
Data Migration Strategies
Data migration is a critical aspect of integrating Exabeam. Organizations often have significant historical security data residing in their existing SIEM. The strategy for migrating this data depends on factors such as data volume, data format, and required retention policies. A phased approach, starting with a pilot migration of a subset of data, is recommended to identify and resolve any unforeseen issues before migrating the entire dataset.
- Assessment and Planning:
- Inventory existing SIEM data sources and formats.
- Determine the required data retention policies for Exabeam.
- Define a migration schedule with clear milestones and timelines.
- Data Transformation:
- Map existing data fields to Exabeam’s schema.
- Develop scripts or tools to transform data formats as needed.
- Validate transformed data for accuracy and completeness.
- Pilot Migration:
- Migrate a subset of data to Exabeam for testing and validation.
- Monitor the migration process for performance and errors.
- Address any identified issues before proceeding with the full migration.
- Full Migration and Validation:
- Migrate the remaining data to Exabeam.
- Verify data integrity and completeness in Exabeam.
- Conduct thorough testing to ensure all functionalities are working as expected.
Potential Integration Challenges and Mitigation Strategies
Several challenges can arise during the integration of Exabeam with existing SIEM systems. These range from data format incompatibility to network connectivity issues. Proactive planning and the implementation of appropriate mitigation strategies are crucial for a successful integration. For example, data format discrepancies can be addressed through data transformation tools, while network connectivity problems can be resolved by optimizing network configurations and implementing robust error handling mechanisms.
| Challenge | Mitigation Strategy |
|---|---|
| Data format incompatibility | Utilize data transformation tools and scripts to convert data into a compatible format. |
| Network connectivity issues | Optimize network configurations, implement robust error handling, and consider using dedicated network segments. |
| Data volume and throughput | Implement a phased migration approach, optimize data ingestion processes, and consider using data compression techniques. |
| Security concerns | Implement appropriate security measures, such as encryption and access control, to protect data during migration. |
Step-by-Step Integration Guide
A well-defined, step-by-step approach is crucial for a smooth integration. This involves a series of phases, from initial assessment to final validation. Each step should be thoroughly documented and tested to minimize the risk of errors and ensure a successful outcome. This methodical approach reduces the complexity of the integration and ensures that the new system is fully functional and integrated with the existing infrastructure.
- Assessment: Thoroughly assess your existing SIEM environment, including data sources, formats, and network infrastructure. Identify potential conflicts and dependencies.
- Planning: Develop a detailed integration plan, including timelines, resources, and responsibilities. Define clear success criteria and rollback plans.
- Configuration: Configure Exabeam to integrate with your existing systems. This includes setting up data sources, defining data mappings, and configuring authentication mechanisms.
- Testing: Conduct rigorous testing to verify data integrity, functionality, and performance. Address any issues identified during testing.
- Deployment: Deploy Exabeam to your production environment. This may involve a phased rollout to minimize disruption.
- Monitoring: Continuously monitor Exabeam’s performance and identify any potential issues. Implement proactive maintenance and monitoring strategies.
Cost and ROI Considerations
Upgrading your SIEM is a significant investment, but the long-term benefits of Exabeam’s new scalable solution can significantly outweigh the initial costs. This section will explore how improved scalability translates into cost savings and detail the return on investment (ROI) you can expect. We’ll also compare Exabeam’s offering to alternative SIEM solutions to illustrate its value proposition.The enhanced scalability of Exabeam’s new SIEM directly impacts operational costs.
By handling significantly larger data volumes without performance degradation, you avoid the need for costly hardware upgrades or the addition of multiple, disparate systems. This eliminates the expenses associated with purchasing, configuring, and maintaining additional infrastructure. Furthermore, the streamlined workflows and improved analyst efficiency contribute to reduced labor costs. Faster incident response times mean less time spent investigating threats, freeing up your security team to focus on proactive security measures.
Cost-Benefit Analysis of Exabeam vs. Alternative SIEM Solutions
The following table presents a hypothetical cost-benefit analysis comparing Exabeam’s new SIEM solution to two alternative options: a legacy on-premise SIEM and a cloud-based competitor. These figures are illustrative and will vary based on specific organizational needs and scale. The ROI is estimated based on factors such as reduced incident response time, improved threat detection accuracy, and decreased operational costs.
A real-world scenario might involve a medium-sized financial institution with approximately 500 employees and a moderate security infrastructure. Their legacy system struggled to handle increasing data volumes, resulting in slow response times and increased operational costs. Switching to Exabeam resulted in faster incident resolution, fewer security breaches, and a significant reduction in operational expenses. This translated into a demonstrably positive ROI within the first year.
| Solution | Initial Cost (USD) | Ongoing Costs (USD/year) | Estimated ROI (years) |
|---|---|---|---|
| Exabeam (New Scalable SIEM) | 150,000 | 75,000 | 2-3 |
| Legacy On-Premise SIEM | 100,000 | 100,000 | 5+ (or negative) |
| Cloud-Based Competitor | 50,000 | 90,000 | 3-4 |
Factors Contributing to Exabeam’s ROI
Several factors contribute to the strong ROI associated with Exabeam’s new SIEM solution. These include:* Reduced operational costs: The improved scalability minimizes the need for costly hardware upgrades and additional infrastructure.
Improved analyst efficiency
Streamlined workflows and advanced automation free up security analysts to focus on higher-value tasks.
Faster incident response times
This leads to reduced downtime and minimizes the potential impact of security breaches.
Enhanced threat detection accuracy
The solution’s advanced capabilities improve the accuracy of threat detection, reducing the number of false positives and allowing for quicker remediation.
Lower risk of data breaches
Proactive threat detection and faster incident response minimize the risk of costly data breaches and associated legal and reputational damage. For example, a reduction in the average cost of a data breach from $4.35 million to $3 million (a hypothetical scenario) can represent significant savings.
Case Studies and Real-World Examples
Let’s examine a hypothetical scenario illustrating the transformative impact of Exabeam’s scaled SIEM on a large financial institution. This example highlights the challenges faced, the solutions implemented, and the resulting improvements in security posture and operational efficiency.Global Banking Corporation (GBC), a multinational bank with over 100,000 employees and a vast global infrastructure, struggled with managing its security information and event management (SIEM) effectively.
Their legacy system was overwhelmed by the sheer volume of logs, leading to slow response times, missed alerts, and a significant increase in security incidents. The lack of scalability and automation resulted in alert fatigue among security analysts, impacting their efficiency and morale.
GBC’s Security Challenges Before Exabeam Implementation
Before implementing Exabeam’s scaled SIEM, GBC faced several critical security challenges. Their legacy system struggled to process the massive volume of security logs generated across their diverse infrastructure. This resulted in a high rate of false positives, overwhelming analysts and leading to missed critical alerts. Furthermore, incident response times were slow, increasing the risk of data breaches and financial losses.
Finally, the lack of comprehensive threat detection and correlation capabilities hindered their ability to proactively identify and mitigate emerging threats. The sheer volume of data made it difficult to prioritize and investigate security events effectively.
Exabeam’s Scaled SIEM Implementation at GBC
GBC opted for Exabeam’s scaled SIEM solution to address their challenges. The implementation involved a phased rollout, starting with critical systems and gradually expanding to encompass the entire enterprise. Exabeam’s solution integrated seamlessly with GBC’s existing security infrastructure, including network devices, firewalls, and endpoint protection systems. The implementation included the configuration of custom rules and dashboards tailored to GBC’s specific security needs and compliance requirements.
The platform’s scalability allowed it to handle the massive influx of security logs without performance degradation.
Positive Impact on Security Posture and Operational Efficiency, Exabeam introduces new scale siem
After implementing Exabeam, GBC experienced a significant improvement in its security posture and operational efficiency. The system’s advanced threat detection capabilities reduced the number of false positives significantly, allowing security analysts to focus on genuine threats. Incident response times decreased dramatically, minimizing the impact of security incidents. The improved correlation and analysis capabilities enabled GBC to identify and respond to sophisticated attacks more effectively.
Furthermore, the automation features freed up security analysts to focus on more strategic tasks, such as threat hunting and vulnerability management. The ability to quickly analyze large volumes of data allowed for proactive identification of potential threats, minimizing risks.
Specific Security Challenges Addressed by Exabeam
Exabeam directly addressed several specific security challenges at GBC. The platform’s ability to handle massive log volumes solved the problem of alert fatigue and missed critical events. Its advanced analytics and machine learning capabilities reduced false positives, improving the accuracy and efficiency of threat detection. The improved correlation engine enabled faster identification of attack patterns and reduced incident response times.
Exabeam’s new scale SIEM is a game-changer for large organizations, offering enhanced threat detection and response capabilities. But comprehensive security goes beyond on-premise systems; managing the ever-expanding cloud footprint is crucial, which is why understanding the role of solutions like Bitglass, as detailed in this excellent article on bitglass and the rise of cloud security posture management , is so important.
Ultimately, combining robust SIEM solutions like Exabeam’s with strong cloud security posture management strategies is key to a truly effective security posture.
Finally, the user-friendly interface and intuitive dashboards simplified security monitoring and management, improving the overall efficiency of the security operations center. The implementation also significantly improved compliance reporting, streamlining the process of demonstrating adherence to regulatory requirements.
End of Discussion
Exabeam’s new scale SIEM isn’t merely an upgrade; it’s a fundamental shift in how organizations approach security monitoring. By dramatically improving scalability and introducing powerful new features, Exabeam empowers security teams to proactively defend against evolving threats with greater efficiency and speed. The enhanced architecture, coupled with improved workflows, positions organizations for a stronger security posture and a significant return on investment.
The future of SIEM is here, and it’s faster, smarter, and more scalable than ever before.
General Inquiries
What specific hardware requirements are needed to run the new Exabeam scale SIEM?
Exabeam provides detailed hardware specifications based on your expected data volume and user count. It’s best to consult their official documentation or contact their sales team for tailored recommendations.
How does the new SIEM integrate with other security tools in my existing ecosystem?
Exabeam offers a range of integrations with popular security tools through APIs and pre-built connectors. The specific integration process will vary depending on your existing tools, but Exabeam provides extensive documentation and support to guide you through the process.
What kind of training is available for security analysts to effectively use the new features?
Exabeam provides various training resources, including online courses, webinars, and on-site training sessions, to help security analysts learn how to effectively utilize the new features and capabilities of the scaled SIEM.