IT Security
-
Technology

Zero Trust CIO & CTO Advantage in Corporate Environments
How zero trust helps CIOs and CTOs in corporate environments is a critical issue. Zero trust security is rapidly reshaping…
Read More » -
Business Management

How to Plan for Data Recovery A Comprehensive Guide
How to plan for data recovery is crucial for any organization. Data loss can cripple operations, leading to financial setbacks…
Read More » -
Small Business

How Cloud Boosts SMB Security
How cloud can help SMBs overcome IT security concerns is a crucial topic. Small and medium-sized businesses often face unique…
Read More » -
Cybersecurity

Four Steps to Improving Your Organizations Cyber Resilience
Four steps to improving your organizations cyber resilience – Four Steps to Improving Your Organization’s Cyber Resilience: In today’s digital…
Read More » -
Cybersecurity

China Cyber Attacks Targeting UK IT Firms
China cyber attacks it companies operating in britain – China cyber attacks targeting IT companies operating in Britain are escalating,…
Read More » -
Education

Best Schools for Globally Recognized Cybersecurity Degrees
Best schools which offer cybersecurity degrees recognized across the world are more crucial than ever. The digital landscape is constantly…
Read More » -
Cybersecurity
Attackers Are Targeting IT Service Providers 2
Attackers Are Targeting IT Service Providers 2: The cybersecurity landscape is shifting, and IT service providers are increasingly becoming prime…
Read More » -
Cybersecurity News

Ascension Suffers Cyber Attack
Ascension suffers cyber attack – that’s the headline that’s been making waves, and frankly, it’s terrifying. We’re talking about a…
Read More » -
Cybersecurity
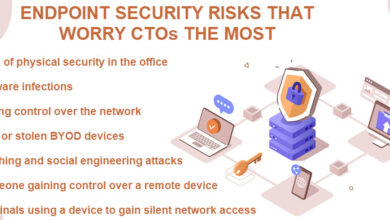
Are You Making Basic Endpoint Protection Mistakes?
Are you making some basic endpoint protection mistakes – Are You Making Basic Endpoint Protection Mistakes? This is a question…
Read More » -
Cybersecurity
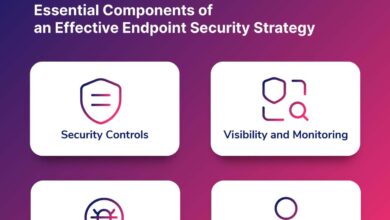
A Simple Guidance on Obtaining Effective Endpoint Security
A simple guidance on obtaining effective endpoint security is more crucial than ever in today’s hyper-connected world. We’re constantly bombarded…
Read More »
