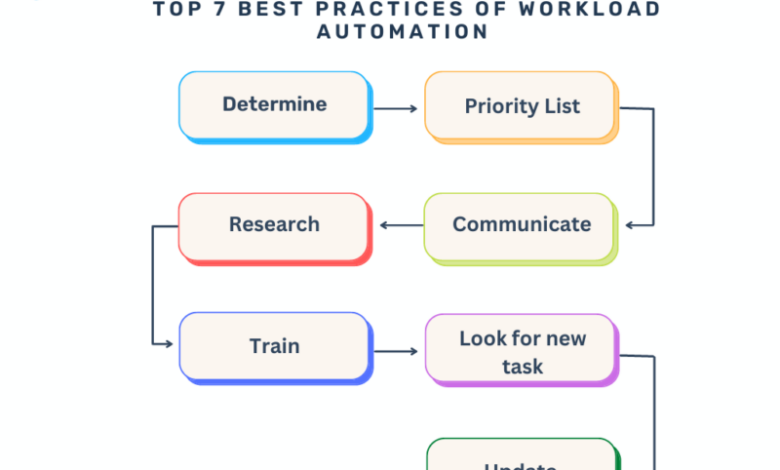
Workload Automation Investment Management
Workload automation investment management: It sounds technical, right? But think about it – this is about streamlining the often-complex processes in the investment world, freeing up valuable time and resources. Imagine a future where repetitive tasks are handled efficiently by technology, allowing human experts to focus on strategy and high-level decision-making. This isn’t just about saving money; it’s about unlocking growth potential and gaining a competitive edge in a fast-paced industry.
This post dives deep into the world of workload automation in investment management, exploring its benefits, challenges, implementation strategies, and the future trends shaping this exciting field. We’ll examine various automation tools, analyze successful case studies, and provide practical advice for anyone looking to optimize their investment processes. Get ready to discover how automation can transform your firm’s efficiency and profitability.
Defining Workload Automation in Investment Management

Workload automation in investment management refers to the use of technology to automate repetitive, manual tasks involved in investment processes. This frees up human capital for higher-value activities, improves efficiency, and reduces operational risks. Think of it as streamlining the back-office functions that support the core investment strategies.
Key Benefits of Workload Automation in Investment Management
Implementing workload automation offers significant advantages. Reduced operational costs are a major draw, as automation minimizes the need for manual labor and reduces human error. Increased efficiency is another key benefit; automated systems can process vast amounts of data and execute trades much faster than humans. Improved accuracy is also crucial; automation eliminates human error, leading to more reliable and consistent results.
Finally, enhanced regulatory compliance is a significant advantage; automated systems can help firms meet stringent regulatory requirements more easily. The improved speed and accuracy of automated processes reduce the likelihood of errors that could lead to regulatory penalties.
Challenges of a Lack of Workload Automation in Investment Management
The absence of workload automation presents considerable challenges. Manual processes are inherently slower, leading to delays in decision-making and missed opportunities in volatile markets. The high risk of human error in manual processes can lead to significant financial losses and reputational damage. Scalability becomes a major issue; manual processes struggle to keep pace with increasing data volumes and transaction frequencies.
Finally, a lack of automation often translates into higher operational costs and reduced profitability. The time spent on manual tasks could be redirected to more strategic activities, improving overall efficiency.
Comparison of Manual vs. Automated Processes
The following table highlights the key differences between manual and automated processes in investment management:
| Task | Time Required (Manual) | Time Required (Automated) | Cost (Manual) | Cost (Automated) | Error Rate (Manual) | Error Rate (Automated) |
|---|---|---|---|---|---|---|
| Portfolio Reconciliation | Days | Hours | High (salaries, overhead) | Lower (software license, maintenance) | High | Low |
| Trade Confirmation Matching | Hours | Minutes | Medium | Low | Medium | Very Low |
| Regulatory Reporting | Weeks | Days | Very High | Medium | High | Low |
| Data Entry | Days | Minutes | Medium | Low | Medium | Very Low |
Types of Workloads Suitable for Automation

Automating workloads in investment management isn’t just about saving time; it’s about improving accuracy, reducing risk, and ultimately boosting profitability. By strategically identifying and automating key processes, firms can gain a significant competitive edge. This section will explore five common workloads ripe for automation, detailing the appropriate technologies and potential ROI.
Portfolio Rebalancing
Portfolio rebalancing, the process of adjusting asset allocations to maintain a target portfolio composition, is a repetitive and time-consuming task. Automation significantly streamlines this process, minimizing human error and freeing up analysts for higher-value activities. The best-suited technology is Robotic Process Automation (RPA), coupled with sophisticated algorithms that analyze market data and execute trades automatically based on predefined parameters.
The ROI comes from reduced operational costs, improved accuracy in rebalancing, and the potential for better portfolio performance due to timely adjustments. For example, a large asset manager could see a reduction in rebalancing costs by 30% and a potential improvement in portfolio returns by 1-2% annually through automation.
Trade Reconciliation
Reconciling trades involves comparing trade data from multiple sources to identify discrepancies. This manual process is prone to errors and requires significant time and resources. Automation using RPA and machine learning (ML) can significantly improve the accuracy and efficiency of this process. ML algorithms can identify patterns and anomalies in trade data, flagging potential discrepancies for review. The ROI from automation includes a reduction in operational costs, faster turnaround times for reconciliation, and reduced risk of errors leading to financial losses.
A hypothetical scenario might show a 40% reduction in reconciliation time and a 20% decrease in reconciliation errors for a mid-sized investment firm.
Regulatory Reporting
Regulatory reporting is a compliance-intensive process requiring meticulous data gathering and reporting. Automating this workload using ETL (Extract, Transform, Load) tools, coupled with RPA, can ensure timely and accurate submission of reports, reducing the risk of penalties. The ROI is primarily realized through reduced compliance costs, avoided penalties, and improved operational efficiency. A conservative estimate might suggest a 25% reduction in reporting time and a significant reduction in the risk of regulatory fines.
Performance Reporting
Generating performance reports involves collecting data from multiple sources, calculating key performance indicators (KPIs), and formatting the results into reports. Automation using Business Intelligence (BI) tools and data visualization platforms can significantly improve the efficiency and accuracy of this process. The ROI comes from reduced time spent on report generation, improved data quality, and the ability to generate more insightful reports faster.
For instance, an investment firm could reduce the time to generate monthly performance reports by 50%, allowing analysts to focus on more strategic analysis.
Client Onboarding
The client onboarding process, involving KYC (Know Your Customer) checks, account setup, and initial investment allocation, is often manual and inefficient. Automation using RPA and workflow management systems can streamline this process, reducing processing time and improving the client experience. The ROI is realized through improved operational efficiency, reduced onboarding costs, and faster time-to-revenue. Automating this process could reduce onboarding time by 40% and decrease associated costs by 20% for a wealth management firm.
Flowchart: Automating Trade Reconciliation
A simplified flowchart for automating trade reconciliation might look like this:Start –> Data Extraction (from multiple sources) –> Data Cleaning & Transformation –> Data Matching & Comparison –> Discrepancy Identification –> Manual Review (for flagged discrepancies) –> Reconciliation Report Generation –> End
Selecting Automation Tools and Technologies
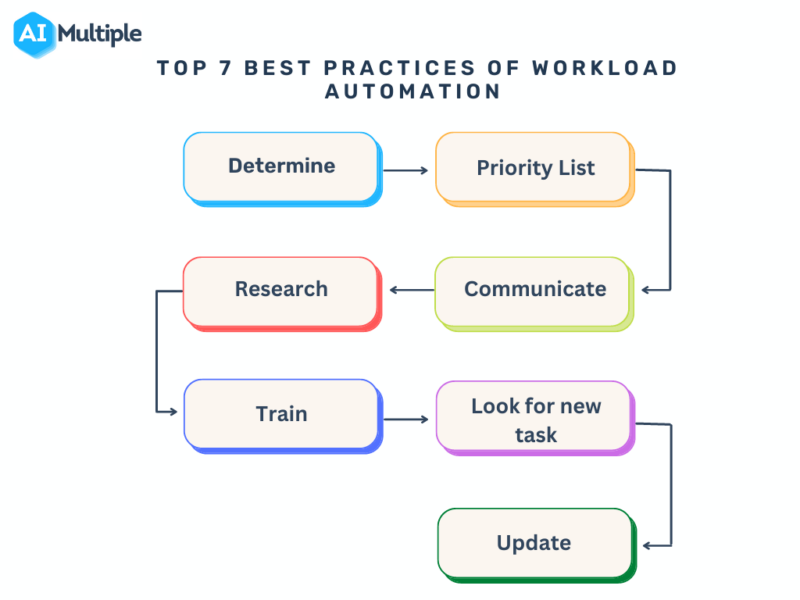
Choosing the right workload automation platform is crucial for investment firms looking to streamline operations and improve efficiency. The market offers a range of solutions, each with its strengths and weaknesses. Careful consideration of your specific needs and future scalability is paramount to a successful implementation.
Comparison of Workload Automation Platforms
Three prominent workload automation platforms frequently used in investment management are UiPath, Automation Anywhere, and Blue Prism. UiPath excels in its robust Robotic Process Automation (RPA) capabilities, offering a wide range of pre-built integrations and a user-friendly interface. Automation Anywhere provides a strong focus on AI-powered automation, enabling more complex and intelligent processes. Blue Prism emphasizes security and governance, making it a popular choice for firms with stringent regulatory requirements.
While UiPath might be favored for its ease of use and extensive library of pre-built components, Automation Anywhere’s AI capabilities could be more beneficial for organizations needing sophisticated decision-making within their automated workflows. Blue Prism’s strength lies in its robust security features, making it ideal for highly regulated environments. The best choice depends on the specific needs and priorities of the investment firm.
Successful Implementations of Workload Automation Tools
Several investment firms have successfully leveraged workload automation to optimize their operations. For example, a large asset management company used UiPath to automate its trade reconciliation process, reducing processing time by 70% and significantly decreasing manual errors. Another firm employed Automation Anywhere to automate its client onboarding process, leading to faster client acquisition and improved customer satisfaction. A hedge fund utilized Blue Prism to automate its regulatory reporting, ensuring compliance with stringent regulations while significantly reducing the risk of human error.
These examples demonstrate the potential of workload automation to deliver substantial improvements in efficiency, accuracy, and compliance within the investment management sector.
Key Factors to Consider When Selecting an Automation Solution
Selecting the right automation solution requires careful consideration of several key factors. Scalability is paramount, ensuring the chosen platform can adapt to growing data volumes and increasing automation needs. Seamless integration with existing systems is also crucial, minimizing disruption and maximizing efficiency. Robust security features are essential to protect sensitive financial data and comply with regulatory requirements. Finally, the platform’s user-friendliness and the availability of adequate training and support should be carefully evaluated.
A platform that is difficult to use or lacks sufficient support can hinder adoption and ultimately limit the benefits of automation.
Essential Features of Workload Automation Software
A comprehensive list of essential features to look for when evaluating workload automation software includes:
- Intuitive user interface and ease of use
- Robust RPA capabilities with support for various applications and systems
- Strong integration capabilities with existing IT infrastructure
- Advanced security features, including encryption and access control
- Scalability to accommodate growing data volumes and automation needs
- Comprehensive monitoring and reporting capabilities
- AI-powered capabilities for enhanced decision-making and process optimization
- Excellent vendor support and training resources
These features ensure a smooth implementation and maximize the return on investment in workload automation.
Implementation and Integration Strategies
Successfully implementing workload automation in investment management requires a well-defined strategy that considers the firm’s unique infrastructure, existing systems, and risk tolerance. A phased approach minimizes disruption and allows for iterative improvements, ensuring a smoother transition and maximizing the return on investment. Careful planning and execution are crucial for a successful deployment.A phased approach to implementation allows for controlled rollout and minimizes risk.
This is particularly important in the highly regulated environment of investment management where even small errors can have significant consequences. By starting small and scaling gradually, firms can identify and address issues early on, preventing larger problems down the line.
Phased Implementation Approach
A typical phased approach might involve three stages: a pilot project focusing on a specific, low-risk workload; a staged rollout expanding automation to other similar workloads; and finally, full-scale implementation across the organization. The pilot phase allows the firm to test the chosen automation tools and processes, refine workflows, and train staff before a wider deployment. The staged rollout allows for incremental improvements and adjustments based on feedback from the pilot phase.
For example, a firm might start by automating the daily reconciliation of a single portfolio before expanding to other portfolios and eventually encompassing all reconciliation processes.
Change Management During Automation Implementation
Change management is critical to the success of any automation initiative. Resistance to change from employees is a common hurdle. A comprehensive change management plan should address employee concerns, provide adequate training, and clearly communicate the benefits of automation. This involves actively engaging staff throughout the process, addressing their concerns, and providing ongoing support. Successful change management fosters a culture of acceptance and collaboration, increasing the likelihood of a smooth transition.
For instance, training programs should focus not just on the technical aspects of the new tools but also on how they improve workflow efficiency and reduce errors.
Integration Challenges and Solutions
Integrating automation tools with existing investment management systems can present significant challenges. Data silos, legacy systems, and differing data formats can create integration bottlenecks. Overcoming these challenges requires careful planning and the use of appropriate integration technologies such as APIs or ETL (Extract, Transform, Load) processes. For example, a firm might need to develop custom ETL processes to transform data from a legacy system into a format compatible with the new automation tool.
Careful data mapping and validation are essential to ensure data integrity throughout the integration process.
Step-by-Step Integration Guide
Integrating a new automation tool with an existing investment management system is a multi-step process.
- Needs Assessment and Tool Selection: Clearly define the specific workloads to be automated and select an automation tool that meets the firm’s needs and integrates well with existing systems.
- Data Mapping and Transformation: Identify the data sources, target systems, and necessary data transformations. This often involves creating ETL processes to ensure data compatibility.
- API Development or Configuration: Develop or configure APIs to facilitate seamless data exchange between the automation tool and existing systems. This might involve working with third-party vendors or internal IT teams.
- Testing and Validation: Thoroughly test the integrated system to ensure accuracy, reliability, and compliance with regulatory requirements. This should include both unit and integration testing.
- Deployment and Monitoring: Deploy the automated workflows to the production environment and continuously monitor performance, identifying and addressing any issues promptly.
Measuring the Success of Automation Initiatives
Successfully implementing workload automation in investment management requires a robust framework for measuring its impact. Without clear metrics, it’s impossible to demonstrate ROI or identify areas for improvement. This section Artikels key performance indicators (KPIs), tracking methods, reporting best practices, and a sample report illustrating a successful automation implementation.
Key Performance Indicators (KPIs) for Workload Automation
Three crucial KPIs provide a comprehensive view of automation success: Reduced Processing Time, Increased Throughput, and Cost Savings. These metrics offer a balanced perspective, encompassing efficiency gains, capacity improvements, and financial benefits. Tracking these KPIs over time allows for identifying trends and evaluating the long-term effectiveness of the automation strategy.
Tracking and Measuring KPIs Over Time
Tracking these KPIs involves establishing baselines before automation implementation. For example, measure the average processing time for a specific task manually. After implementing automation, continuously monitor the processing time, throughput (number of tasks completed per unit of time), and cost savings (reduction in labor, infrastructure, or error costs). Data should be collected regularly, ideally daily or weekly, and visualized in charts and graphs to easily identify trends and patterns.
This data should be compared against the baseline to demonstrate the improvement achieved through automation.
Reporting on the Impact of Workload Automation
Effective reporting requires clear and concise communication of the results. Reports should highlight the improvement in KPIs compared to pre-automation baselines. Visualizations such as charts and graphs are essential for effective communication. Furthermore, the report should include a cost-benefit analysis, demonstrating the return on investment (ROI) of the automation project. Qualitative data, such as employee feedback on improved work-life balance or reduced stress, can also be included to paint a holistic picture of the automation’s success.
Sample Report: Successful Workload Automation Implementation, Workload automation investment management
Let’s consider a hypothetical scenario where a large investment firm automated its trade reconciliation process.A report summarizing the results might include: Executive Summary: This section would briefly state the project’s goals, the automation solution implemented, and the key results achieved. Pre-Automation Baseline: This section would detail the average processing time (e.g., 24 hours), throughput (e.g., 100 trades per day), and associated costs (e.g., $5000 per month in labor costs and error correction).
A bar chart could visually represent these baseline metrics. The bar chart would show three separate bars for processing time, throughput, and cost, each labelled with its respective value. Post-Automation Results: This section would present the results after automation implementation. For instance, processing time reduced to 2 hours, throughput increased to 500 trades per day, and costs decreased to $1500 per month.
A second bar chart, identical in structure to the baseline chart, would display the post-automation values. The difference between the two charts would clearly highlight the improvement. ROI Calculation: This section would detail the cost savings and the return on investment. A simple calculation, showing the difference in monthly costs multiplied by 12 months, would provide the annual savings.
This could be further illustrated with a pie chart showing the proportion of costs before and after automation. The pie chart would visually demonstrate the significant reduction in costs post-automation. Qualitative Feedback: This section could include positive feedback from employees regarding reduced workload and improved accuracy, which would strengthen the overall impact of the automation project.
Future Trends in Workload Automation for Investment Management
The investment management industry is undergoing a rapid transformation, driven by technological advancements and evolving client expectations. Workload automation, already playing a significant role, is poised for even greater impact in the coming years, fueled by innovations in artificial intelligence and other emerging technologies. This evolution promises to reshape operational efficiency, risk management, and the overall client experience.
The Impact of AI and Machine Learning
AI and machine learning (ML) are set to revolutionize workload automation in investment management. AI-powered systems can analyze vast datasets, identify patterns and anomalies, and make predictions with greater accuracy than traditional methods. This capability translates to more efficient portfolio management, improved risk assessment, and enhanced fraud detection. For instance, ML algorithms can be trained to identify market trends and predict price movements, allowing for more proactive portfolio adjustments.
Similarly, AI can automate compliance checks, reducing the risk of regulatory violations and freeing up human resources for higher-value tasks. The integration of AI and ML is not merely about automating existing tasks; it’s about creating entirely new capabilities and optimizing decision-making processes.
Emerging Technologies Shaping the Future
Beyond AI and ML, several other technologies are poised to significantly impact workload automation. Robotic Process Automation (RPA) will continue its expansion, handling repetitive, rule-based tasks with increased efficiency. Cloud computing will provide the scalability and flexibility needed to support increasingly complex automation workflows. Blockchain technology offers potential for enhanced security and transparency in data management and transaction processing.
Finally, the rise of low-code/no-code platforms will empower business users to design and implement automation solutions without extensive coding expertise, further accelerating adoption. Imagine a scenario where a portfolio manager can use a simple, user-friendly interface to create an automated workflow for rebalancing their portfolio based on predefined parameters, eliminating the need for manual intervention.
Challenges and Opportunities
The adoption of these advanced technologies presents both challenges and opportunities. One key challenge is the need for robust data security and privacy measures to protect sensitive client information. Another is the potential for algorithmic bias, which can lead to unfair or discriminatory outcomes. However, the opportunities are substantial. Automated processes can significantly reduce operational costs, improve accuracy, and enhance the speed of decision-making.
Furthermore, freed-up human capital can be redirected to more strategic and client-facing activities, leading to improved client service and satisfaction. Successful implementation requires a strategic approach, including careful planning, investment in skilled personnel, and a focus on change management.
Potential Future Developments and Implications
The future of workload automation in investment management will likely see several key developments. We can anticipate the widespread adoption of intelligent automation, combining RPA, AI, and ML to create sophisticated, self-learning systems. Hyperautomation, encompassing the automation of entire business processes, will become increasingly prevalent. The integration of these technologies with other areas, such as customer relationship management (CRM) and compliance systems, will create a more holistic and efficient operational environment.
These developments will lead to significant improvements in efficiency, reduced costs, and enhanced risk management, ultimately contributing to a more competitive and client-centric investment management industry. For example, imagine a fully automated system that monitors market conditions, adjusts portfolio allocations, generates compliance reports, and communicates with clients, all without human intervention. This represents a future where technology handles routine tasks, allowing human professionals to focus on higher-level strategic decisions and client relationships.
Ending Remarks: Workload Automation Investment Management
Ultimately, workload automation in investment management isn’t just about technology; it’s about strategic transformation. By embracing automation, firms can not only improve efficiency and reduce costs but also foster a more data-driven and insightful approach to investment decision-making. The journey may present some challenges, but the rewards – increased profitability, reduced risk, and a more agile organization – are well worth the effort.
The future of investment management is automated, and those who adapt will thrive.
Expert Answers
What are the biggest risks associated with implementing workload automation?
The biggest risks include inadequate planning, poor integration with existing systems, insufficient training for staff, and the potential for security breaches if not properly addressed.
How long does it typically take to implement a workload automation solution?
Implementation timelines vary greatly depending on the complexity of the system and the firm’s specific needs. It can range from a few months to over a year.
What is the average ROI for workload automation in investment management?
ROI varies depending on the specific applications and scale of implementation. However, many firms report significant cost savings and efficiency gains within the first year.
Can smaller investment firms benefit from workload automation?
Absolutely! Even smaller firms can benefit from automating specific tasks, improving efficiency, and freeing up staff for higher-value activities. Cloud-based solutions offer scalable and cost-effective options.
