Malware
-
Cybersecurity
Classifying Malware Using Deep Learning A Deep Dive
Classifying malware using deep learning is revolutionizing cybersecurity. Traditional methods struggle with the ever-evolving nature of malicious software. Deep learning,…
Read More » -
Cybersecurity
How to Track Ransomware Attacks A Guide
How to track ransomware attacks a comprehensive guide sets the stage for this detailed exploration of a critical cybersecurity concern.…
Read More » -
Cybersecurity

Multi-Vector Security Defeating Evasive Malware
How multi vector security solutions neutralize evasive malware is a crucial topic in today’s digital landscape. Malware constantly evolves, finding…
Read More » -
Cybersecurity
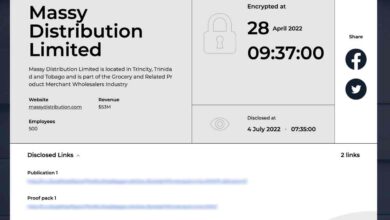
Hive Ransomware A Deep Dive
Hive ransomware lets learn all about it, a critical topic in the ever-evolving cybersecurity landscape. This exploration delves into the…
Read More » -
Cybersecurity
Gmail Hacks Cyber Attacks Explained
Hackers launch cyber attacks on gmail accounts, targeting individuals and organizations for various reasons. These attacks often involve sophisticated methods,…
Read More » -
Technology

WhatsApp Malware A Hidden Threat
Hackers install surveillance malware on WhatsApp installed smartphones, a growing concern for users worldwide. This malicious software, often hidden within…
Read More » -
Cybersecurity Threats
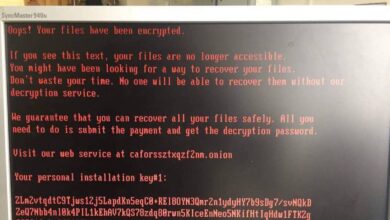
Hackers Distribute Gibon Ransomware via Malspam
Hackers distribute Gibon ransomware via malspam, a sophisticated and concerning threat. Malspam, using deceptive emails disguised as legitimate communications, often…
Read More » -
Cybersecurity

Hackers Cyberattack US Power Firms New Malware Threat
Hackers cyber attack us power firms with a new malware, raising serious concerns about the resilience of our critical infrastructure.…
Read More » -
Cybersecurity

Hackers Are Launching Fileless Cyber Attacks
Hackers are launching fileless cyber attacks, a sophisticated and insidious threat that bypasses traditional security measures. This new form of…
Read More » -
Technology

Google Malware Exploit Passwordless Account Access
Google malware exploit allows hackers to access accounts without passwords, presenting a terrifying new threat to online security. This sophisticated…
Read More »
