MFA
-
Cybersecurity
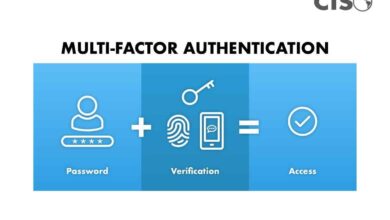
How MFA Stops Healthcare Phishing
How MFA identity security can help prevent phishing scams targeting healthcare companies is crucial in today’s digital landscape. Phishing attacks…
Read More » -
G Suite Administration

Glass Class Securing G Suite A Deep Dive
Glass Class Securing G Suite: Ever felt like your G Suite data is a little too…transparent? This isn’t about literal…
Read More » -
Cybersecurity

Follow these 3 mobile security measures to protect your enterprise networks
Follow these 3 mobile security measures to protect your enterprise networks – Follow these 3 mobile security measures to protect…
Read More » -
Cybersecurity

Five Ways to Improve Enterprise Email Security
Five ways to improve enterprise email security: It’s a topic that keeps IT managers up at night, right? We’re bombarded…
Read More » -
Cybersecurity

Ensuring Data Security with Remote Workers
Ensuring data security with remote workers is more critical than ever. The rise of remote work has dramatically expanded the…
Read More » -
Cybersecurity

Cyber Attack on OneLogin Data Compromised
Cyber attack on password manager OneLogin makes data compromised – that’s the chilling reality we face. This massive breach exposed…
Read More » -
Tech Acquisitions

Cisco Systems to Acquire Duo Security for $2.35 Billion
Cisco systems to acquire duo security for 2 35 billion – Cisco Systems to Acquire Duo Security for $2.35 Billion…
Read More » -
Technology

California Passes a Bill to Ban Traditional Passwords
California passes a bill to ban traditional passwords – can you believe it? This groundbreaking legislation is poised to reshape…
Read More » -
WordPress Security
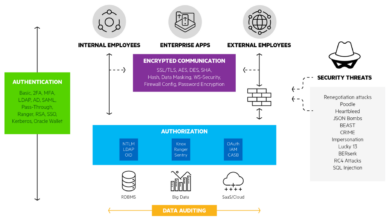
Bringing Authentication Security Out of the Dark Ages Enzoic
Bringing authentication security out of the dark ages enzoic – Bringing authentication security out of the dark ages with Enzoic…
Read More » -
AWS Security
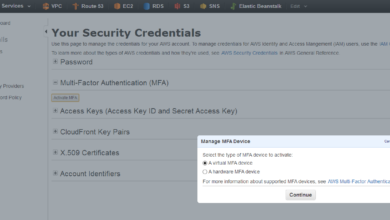
Amazon Web Services Mandates MFA Security
Amazon Web Services Mandates MFA Security: Let’s face it, keeping your AWS environment secure is a big deal. And lately,…
Read More »
