network security
-
Network Security
Hunting for Network Share Recon A Deep Dive
Hunting for network share recon sets the stage for a comprehensive exploration of identifying and analyzing network shares. This in-depth…
Read More » -
Technology

Huawei 5G Security Risks UKs Management Strategy
Huawei 5G mobile security risks can be managed says the UK, offering a nuanced perspective on a complex issue. The…
Read More » -
Technology

Zero Trust CIO & CTO Advantage in Corporate Environments
How zero trust helps CIOs and CTOs in corporate environments is a critical issue. Zero trust security is rapidly reshaping…
Read More » -
Networking & Security

How to Quickly Integrate Your SD-WAN with Bitglass
How to quickly integrate your sd wan with bitglass – How to quickly integrate your SD-WAN with Bitglass? This guide…
Read More » -
Network Security

How Security Service Edge Revolutionizes Network Security
How security service edge is revolutionizing network security by fundamentally shifting the way we approach network security. It’s moving beyond…
Read More » -
Information Security

How Many Types of Network Security Protocols Exist?
How many types of network security protocols exist? This question delves into the intricate world of digital safeguards, exploring the…
Read More » -
Cybersecurity
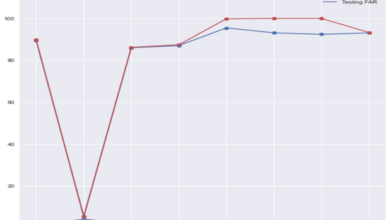
How DPI Sensors Improve Network Forensics
How DPI sensors improve network forensics is a crucial aspect of modern cybersecurity. DPI, or Deep Packet Inspection, sensors delve…
Read More » -
Business

How Can Businesses Lower Cyber Attack Risks?
How can businesses lower the risks of cyber attacks? This is a critical question for organizations in today’s digital landscape.…
Read More » -
Technology
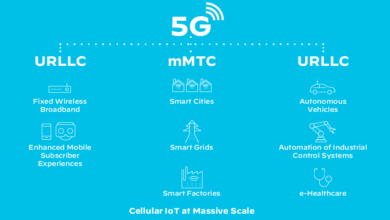
How 5G Technology Offers a Secure Network
How 5G technology offers a secure network is a critical aspect of its development. 5G’s advanced architecture introduces a new…
Read More » -
Technology

How 5G Technology Accelerates Cybersecurity
How 5G technology accelerates cybersecurity is a crucial discussion in today’s digital landscape. 5G’s increased speed and capacity bring unprecedented…
Read More »
