network security
-
Cybersecurity
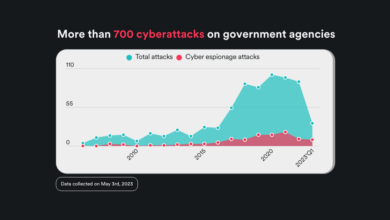
Bad Cybersecurity Practices in 8 Government Agencies
Bad cyber security practices in 8 government agencies – Bad cybersecurity practices in 8 government agencies? Yikes! That sounds serious,…
Read More » -
Cybersecurity

Amazon Defends 2.3 Tbps DDoS Attack
Amazon defends 2 3 tbps high volume ddos cyber attack in the history – Amazon Defends 2.3 Tbps high volume…
Read More » -
Cybersecurity

WPA2 Vulnerability All WiFi Devices at Risk
All WiFi enabled devices on WPA2 security protocol are vulnerable to cyber attacks. That’s a pretty scary thought, right? We…
Read More » -
Cybersecurity

All Cyberattacks Have This in Common
All cyberattacks have this in common: they all require some level of human interaction or exploitation of human error. Whether…
Read More » -
Cybersecurity

Akamai Blocks Worlds Largest DDoS Attacks in Europe
Akamai blocks worlds las largest ddos attacks in europe – Akamai Blocks World’s Largest DDoS Attacks in Europe – that…
Read More » -
Cybersecurity

AI in Cybersecurity Friend or Foe?
Ai in cybersecurity friend or foe – AI in cybersecurity: friend or foe? It’s a question that’s increasingly relevant as…
Read More » -
Cybersecurity
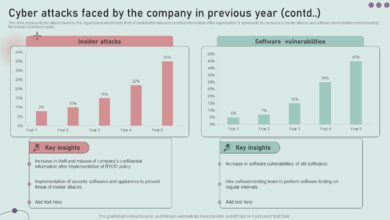
A 50% Increase in Cyber Attacks Year on Year
A 50 increase in cyber attacks year on year – A 50% increase in cyber attacks year on year? Whoa.…
Read More » -
Cybersecurity
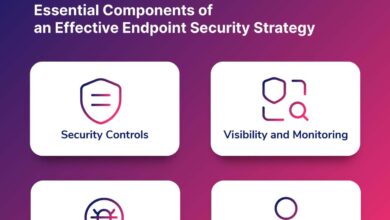
A Simple Guidance on Obtaining Effective Endpoint Security
A simple guidance on obtaining effective endpoint security is more crucial than ever in today’s hyper-connected world. We’re constantly bombarded…
Read More » -
Cybersecurity

A Cybersecurity Conversation with Vince Moore, Senior Network Engineer at Opswat
A cybersecurity conversation with vince moore senior network engineer at opswat – A cybersecurity conversation with Vince Moore, Senior Network…
Read More » -
IT Security

8 Key Tips for Data Center Security
8 Key Tips for Data Center Security: In today’s hyper-connected world, data centers are the beating heart of countless businesses.…
Read More »
