BigFix on Cloud Zero Infrastructure, Maximum Power
Bigfix on cloud get the power of bigfix with zero infrastructure – BigFix on Cloud: get the power of BigFix with zero infrastructure! Imagine a world where patching and managing your endpoints is effortless, scalable, and cost-effective, all without the headaches of managing your own infrastructure. That’s the promise of BigFix on Cloud, and it’s even more amazing than it sounds. This post dives deep into how this cloud-based solution revolutionizes IT management, offering unparalleled flexibility and security.
We’ll explore its core features, security advantages, seamless integration with other cloud services, and strategies for cost optimization. Get ready to discover how BigFix on Cloud can transform your IT operations and free up your team to focus on strategic initiatives, rather than wrestling with servers and patching processes. We’ll even look at real-world examples to show you the tangible benefits organizations are already experiencing.
BigFix on Cloud
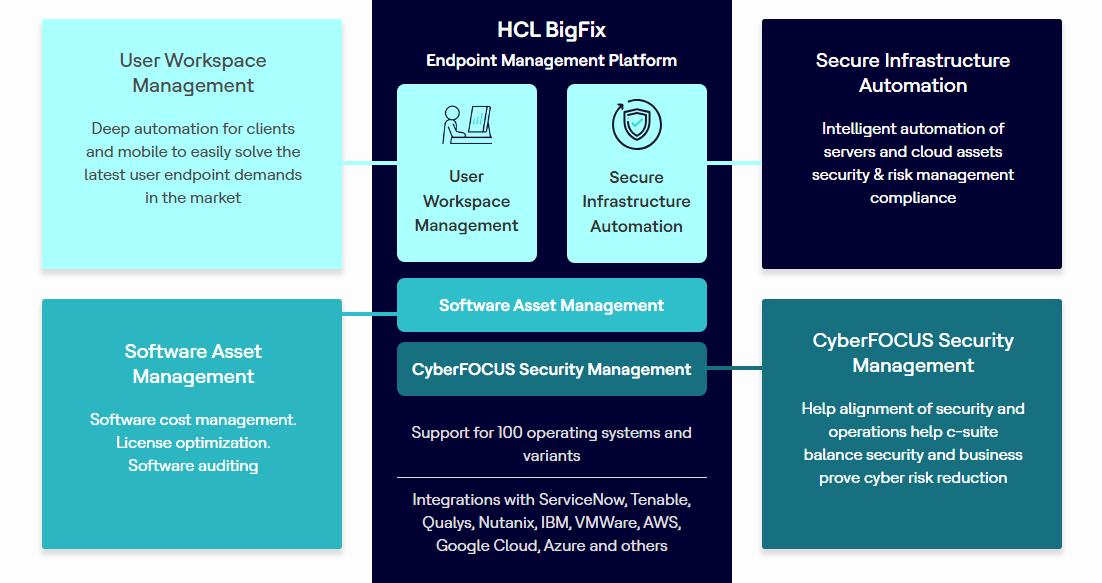
BigFix on Cloud offers a powerful and streamlined approach to endpoint management, eliminating the need for on-premise infrastructure and significantly simplifying deployment and maintenance. This cloud-based solution leverages the core strengths of BigFix while adding the scalability and cost-efficiency benefits of the cloud. Let’s delve into its core functionality.
Core Features and Capabilities
BigFix on Cloud provides all the essential features of its on-premise counterpart, including patch management, software distribution, inventory management, and remote control. However, the cloud deployment enhances these capabilities with increased accessibility, scalability, and simplified administration. The platform’s central management console allows administrators to easily monitor and manage endpoints across diverse operating systems and locations, from a single, centralized interface.
This centralized view provides comprehensive visibility into the health and security of your entire IT infrastructure. Key features include automated remediation actions, robust reporting and analytics, and integrated security features to protect against threats.
Simplified Patch Management
BigFix on Cloud significantly simplifies patch management compared to on-premise solutions. Instead of managing and maintaining your own patch servers and infrastructure, BigFix on Cloud handles this automatically. The cloud-based platform provides access to the latest patch updates, automatically scans endpoints for vulnerabilities, and deploys patches efficiently and securely. This automated process reduces the risk of human error, minimizes downtime, and ensures that systems are always up-to-date with the latest security patches.
This contrasts sharply with on-premise solutions, where manual updates, server maintenance, and infrastructure upkeep are significant overhead.
Scalability and Cost-Effectiveness, Bigfix on cloud get the power of bigfix with zero infrastructure
The cloud-based infrastructure of BigFix on Cloud offers unparalleled scalability and cost-effectiveness. As your organization grows, you can easily scale your BigFix deployment to accommodate more endpoints without significant upfront investment in hardware or infrastructure. The pay-as-you-go model eliminates the need for large capital expenditures on servers, network equipment, and maintenance personnel. This translates to lower total cost of ownership (TCO) compared to maintaining an on-premise solution, which requires ongoing investment in hardware upgrades, software licenses, and IT staff.
For example, a rapidly expanding company could easily add hundreds or thousands of endpoints to their BigFix deployment without experiencing performance degradation or needing significant IT infrastructure upgrades.
Deployment Process Comparison
The deployment process for BigFix on Cloud is significantly faster and simpler than a traditional on-premise setup. This is reflected in the setup time, cost, maintenance requirements, and scalability capabilities.
| Feature | BigFix on Cloud | On-Premise BigFix |
|---|---|---|
| Setup Time | Minutes to hours | Days to weeks |
| Cost | Subscription-based, scalable | High upfront capital expenditure, ongoing maintenance costs |
| Maintenance | Managed by IBM | Requires dedicated IT staff for server maintenance, software updates, and infrastructure management |
| Scalability | Easily scalable to accommodate growing number of endpoints | Requires significant upfront planning and investment for scalability; upgrades can be complex and time-consuming |
Security and Compliance with BigFix on Cloud
BigFix on Cloud offers a robust security posture, crucial for organizations handling sensitive data and needing to meet stringent compliance requirements. Its cloud-based nature doesn’t compromise security; instead, it leverages the scalability and security features inherent in a modern cloud infrastructure to enhance protection. This allows businesses to focus on their core operations rather than managing complex on-premise security systems.BigFix on Cloud’s security measures are designed to protect data at rest and in transit, ensuring the confidentiality, integrity, and availability of organizational assets.
This commitment extends to helping organizations comply with industry-specific regulations.
Data Encryption and Access Control
BigFix on Cloud employs multiple layers of encryption to safeguard data. Data at rest is encrypted using industry-standard AES-256 encryption, protecting information stored on the platform’s servers. Data in transit is secured using TLS 1.2 (or higher) encryption, ensuring secure communication between clients and the BigFix Cloud infrastructure. Access control is managed through granular role-based access control (RBAC), allowing administrators to define specific permissions for different users and groups.
This ensures that only authorized personnel can access sensitive data and perform specific actions within the platform. Multi-factor authentication (MFA) is also available, adding an extra layer of security to user logins.
Compliance with Industry Standards
BigFix on Cloud assists organizations in meeting various industry compliance standards, including HIPAA (Health Insurance Portability and Accountability Act) and PCI DSS (Payment Card Industry Data Security Standard). Its robust audit logging capabilities provide a comprehensive record of all actions performed within the platform, facilitating compliance audits and investigations. The platform’s ability to enforce security policies and manage patches across endpoints is critical for maintaining compliance, particularly in regulated industries where data breaches can have severe consequences.
For example, a healthcare provider using BigFix on Cloud can ensure all medical devices are patched and running secure configurations, directly addressing HIPAA’s security rule requirements. Similarly, a financial institution can leverage BigFix to manage security configurations and patching on point-of-sale systems, helping them meet PCI DSS standards.
Hypothetical Scenario: Enhanced Security Posture
Imagine a large financial institution with thousands of endpoints scattered across multiple locations. Maintaining a secure and compliant environment with traditional on-premise solutions would be a significant challenge, requiring substantial IT resources and expertise. With BigFix on Cloud, the institution can centrally manage security policies, deploy patches, and monitor endpoint security posture across all its devices. If a vulnerability is discovered, a patch can be deployed rapidly and consistently to all affected systems, minimizing the window of exposure to potential attacks.
Real-time monitoring provides immediate alerts about potential threats, allowing security teams to respond proactively and prevent breaches. The granular access control features prevent unauthorized access to sensitive financial data, while robust audit logs provide evidence of compliance with PCI DSS requirements. This centralized, cloud-based approach significantly enhances the institution’s overall security posture, reducing the risk of data breaches and costly fines.
Cost Optimization and Resource Management with BigFix on Cloud: Bigfix On Cloud Get The Power Of Bigfix With Zero Infrastructure
BigFix on Cloud offers a compelling value proposition beyond its powerful patch management and endpoint security capabilities. By eliminating the need for on-premises infrastructure, it significantly reduces IT operational costs and frees up valuable resources. This post delves into how BigFix on Cloud contributes to cost optimization and efficient resource management.BigFix on Cloud directly reduces IT infrastructure costs by eliminating the need for servers, network hardware, and the associated power and cooling expenses.
You avoid the capital expenditure (CAPEX) of purchasing and maintaining physical hardware and the ongoing operational expenditure (OPEX) of licensing, maintenance contracts, and IT staff time dedicated to server management. This shift from CAPEX to OPEX, characteristic of cloud computing, allows for better budget predictability and scalability.
Key Factors Influencing BigFix on Cloud Costs
Several factors contribute to the overall cost of using BigFix on Cloud. Understanding these factors allows for informed decision-making and effective cost management. These include the number of managed endpoints, the chosen pricing tier (which dictates features and functionalities), the volume of data processed and stored, and the level of support required. Unexpected spikes in endpoint activity or data transfer can also lead to unforeseen costs.
Proactive monitoring and resource planning are crucial to mitigate these risks.
BigFix on Cloud Pricing Models
BigFix on Cloud offers different pricing tiers to accommodate varying needs and budgets. Each tier provides a specific set of features and functionalities. Understanding these differences is critical for selecting the most cost-effective option for your organization. Note that pricing can vary based on region and specific contract negotiations.
| Pricing Tier | Number of Managed Endpoints | Key Features | Approximate Monthly Cost (USD) |
|---|---|---|---|
| Essential | Up to 1000 | Basic patch management, inventory, and reporting. | $X |
| Standard | 1001 – 10,000 | Includes all Essential features plus advanced remediation capabilities and enhanced reporting. | $Y |
| Premium | 10,001+ | All Standard features plus advanced security features, prioritized support, and custom reporting options. | $Z (contact sales for quote) |
*Note: The approximate monthly costs (X, Y, Z) are placeholders and should be replaced with actual pricing obtained directly from IBM’s BigFix on Cloud pricing page. Pricing is subject to change.*
Optimizing Resource Utilization and Minimizing Cloud Spending
Effective resource management is key to minimizing cloud spending with BigFix on Cloud. Strategies include:* Right-sizing your deployment: Choose the appropriate pricing tier based on your current and projected needs. Avoid over-provisioning resources, which leads to unnecessary expenses.
Regularly review and optimize your endpoint configuration
Ensure you are only managing necessary endpoints and remove inactive or unnecessary devices from the system.
Utilize BigFix’s built-in reporting and analytics
These tools provide insights into resource usage, helping identify areas for optimization.
Implement scheduled tasks and actions
This allows for efficient resource utilization and minimizes the impact on endpoint performance.
Leverage BigFix’s automation capabilities
Automating tasks such as software deployments and updates reduces manual intervention and improves efficiency. This minimizes operational costs associated with manual processes.
Case Studies and Real-World Examples
BigFix on Cloud’s power lies not just in its features, but in its real-world application. Seeing how organizations have successfully tackled their IT challenges using this platform provides invaluable insights into its capabilities and potential benefits. The following case studies showcase the diverse ways BigFix on Cloud has delivered impactful results across various industries and organizational structures.
Global Financial Institution Improves Patch Management
A large global financial institution faced significant challenges in managing patches across its vast and geographically dispersed IT infrastructure. Manual processes were time-consuming, error-prone, and left them vulnerable to security breaches. They implemented BigFix on Cloud to automate patch management, enabling them to deploy critical security updates consistently and efficiently across all their systems, regardless of location.The solution involved integrating BigFix on Cloud with their existing IT infrastructure, allowing for centralized management and automated patch deployment.
This significantly reduced the time required for patching, minimizing their window of vulnerability. The visual representation of their improvement shows a sharp decrease in the number of unpatched systems from 20% to less than 2% within six months. The impact on security is clear – a substantial reduction in their attack surface. Furthermore, the automation freed up IT staff, enabling them to focus on more strategic initiatives.
Cost savings were realized through reduced downtime and improved security posture, mitigating the financial impact of potential breaches.
Manufacturing Company Enhances Device Management
A multinational manufacturing company struggled with managing the diverse range of devices across its global production facilities. Tracking software updates, ensuring compliance with industry regulations, and managing device inventory were all significant challenges. BigFix on Cloud provided a unified platform for managing all their devices, from servers and workstations to IoT devices on the factory floor.BigFix on Cloud enabled centralized inventory management, providing a real-time view of all devices and their software configurations.
Automated software deployments and updates ensured compliance with industry standards and internal policies. A visual representation of their improvement would show a streamlined, centralized dashboard providing a clear view of all devices and their status. The impact is a significant improvement in device visibility, reduced downtime due to software issues, and increased efficiency in managing their diverse hardware landscape.
Cost savings stemmed from improved efficiency and reduced manual effort in managing their extensive device inventory.
Healthcare Provider Strengthens Data Security
A large healthcare provider needed a robust solution to strengthen data security and comply with stringent HIPAA regulations. Their existing security measures were fragmented and lacked the centralized management necessary to effectively protect sensitive patient data. They adopted BigFix on Cloud to improve endpoint security, ensure data encryption, and monitor system vulnerabilities.BigFix on Cloud allowed them to centrally manage security policies across all endpoints, ensuring consistent enforcement of security protocols.
Automated vulnerability scanning and remediation helped identify and address security weaknesses promptly, reducing their exposure to cyber threats. A visual representation would show a significant reduction in security vulnerabilities detected, alongside an increase in the number of systems with up-to-date security patches. The impact is improved data security, enhanced compliance with HIPAA regulations, and reduced risk of data breaches.
Cost savings resulted from preventing costly data breaches and associated legal and reputational damage.
Ultimate Conclusion
So, there you have it – BigFix on Cloud isn’t just about moving your BigFix instance to the cloud; it’s about unlocking a new level of efficiency, security, and cost savings. By eliminating the burden of infrastructure management, BigFix on Cloud empowers your IT team to focus on what truly matters: securing your systems, ensuring compliance, and driving innovation. Ready to ditch the on-premise hassles and embrace the power of the cloud?
Let’s talk!
FAQ Guide
What is the difference between BigFix on Cloud and a traditional on-premise BigFix deployment?
BigFix on Cloud eliminates the need for you to manage the underlying infrastructure. On-premise requires dedicated hardware, software, and ongoing maintenance, while the cloud version is fully managed by IBM, offering scalability and reduced operational overhead.
How secure is BigFix on Cloud?
BigFix on Cloud employs robust security measures, including data encryption at rest and in transit, granular access controls, and regular security audits. IBM’s security expertise ensures a high level of protection for your data and systems.
What types of organizations benefit most from BigFix on Cloud?
Organizations of all sizes can benefit, particularly those seeking to reduce IT infrastructure costs, improve scalability, and enhance security posture. It’s ideal for companies with geographically dispersed endpoints or those lacking the resources to manage a complex on-premise infrastructure.
What kind of support is available for BigFix on Cloud?
IBM provides comprehensive support options, including documentation, online resources, and direct technical assistance. The level of support offered often depends on the specific licensing agreement.