Risk Management
-
Business

How Can Businesses Lower Cyber Attack Risks?
How can businesses lower the risks of cyber attacks? This is a critical question for organizations in today’s digital landscape.…
Read More » -
IT Security

Glass Class Mitigating Risk Before Shadow It
Glass class mitigating risk before shadow it – Glass Class: Mitigating Risk Before Shadow It – sounds like a sci-fi…
Read More » -
Cybersecurity

Four Steps to Improving Your Organizations Cyber Resilience
Four steps to improving your organizations cyber resilience – Four Steps to Improving Your Organization’s Cyber Resilience: In today’s digital…
Read More » -
IT Security & Compliance
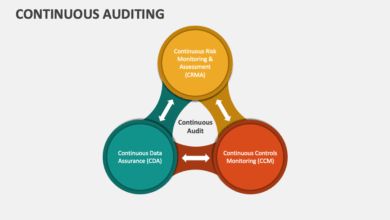
Forging the Path to Continuous Audit Readiness
Forging the path to continuous audit readiness isn’t just about ticking boxes; it’s about fundamentally shifting how organizations approach risk…
Read More » -
Cybersecurity

Dont get caught in the noise focus security on what you can control
Dont get caught in the noise focus security on what you can control – Dont get caught in the noise:…
Read More » -
Cybersecurity

Does That Data Make Your Company a Cyber Attack Target?
Does that data make your company a cyber attack target? It’s a question every business owner should be asking themselves,…
Read More » -
Cybersecurity

Data & Cyber Resilience Definition and Attainment
Definition of data resilience and cyber resilience and their attainment – Data & Cyber Resilience: Definition and Attainment – sounds…
Read More » -
Cybersecurity

Cybersecurity Regulations How Laws Apply to Your Business
Cybersecurity regulations how do laws apply to your business – Cybersecurity regulations: how do laws apply to your business? It’s…
Read More » -
Cybersecurity
Cyber Insurance Paradigm Shift Protecting Business Without Hail Marys
Cyber insurance paradigm shift protecting the business without the hail mary remedy – Cyber Insurance Paradigm Shift: Protecting Business Without…
Read More » -
Cybersecurity

Companies Taking Cyber Insurance Are Vulnerable to Ransomware Attacks
Companies taking cyber insurance are vulnerable to ransomware attacks – a seemingly paradoxical statement, yet one supported by unsettling evidence.…
Read More »
